Introduction
This guide demonstrates the authentication process of devices based on their respective physical MAC addresses using Media Access Control (MAC). Once the source MAC address is identified, the switch generates an access-request message, with the user/machine’s MAC address as the identity, and sends it to the RADIUS server. The RADIUS server performs MAC authentication after getting the access-request message.
The RADIUS authentication server determines whether to grant access to the user/device and specifies the level of access the client should receive. After making this decision, the RADIUS server transmits the access-accept, allowing the user/machine to access the network.
If you are interested in setting up EAP-TLS Authentication, you can find the relevant instructions and resources at the following link: Integrating EAP-TLS Authentication with Aruba Access Points
Follow the below steps to create a VLAN in Aruba IAP and then configure Aruba IAP with SecureW2.
Creating an Core Platform in SecureW2
Follow the below steps to create an Identity Provider in JoinNow Management Portal and configure it for MAC Authentication:
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to Integrations Hub > Core Platform.
- Click Add.
- In the Name field, enter a name for your MAC IdP.
- In the Description field, enter a suitable description for your MAC IdP.
- From the Type drop-down, select MAC Authentication.
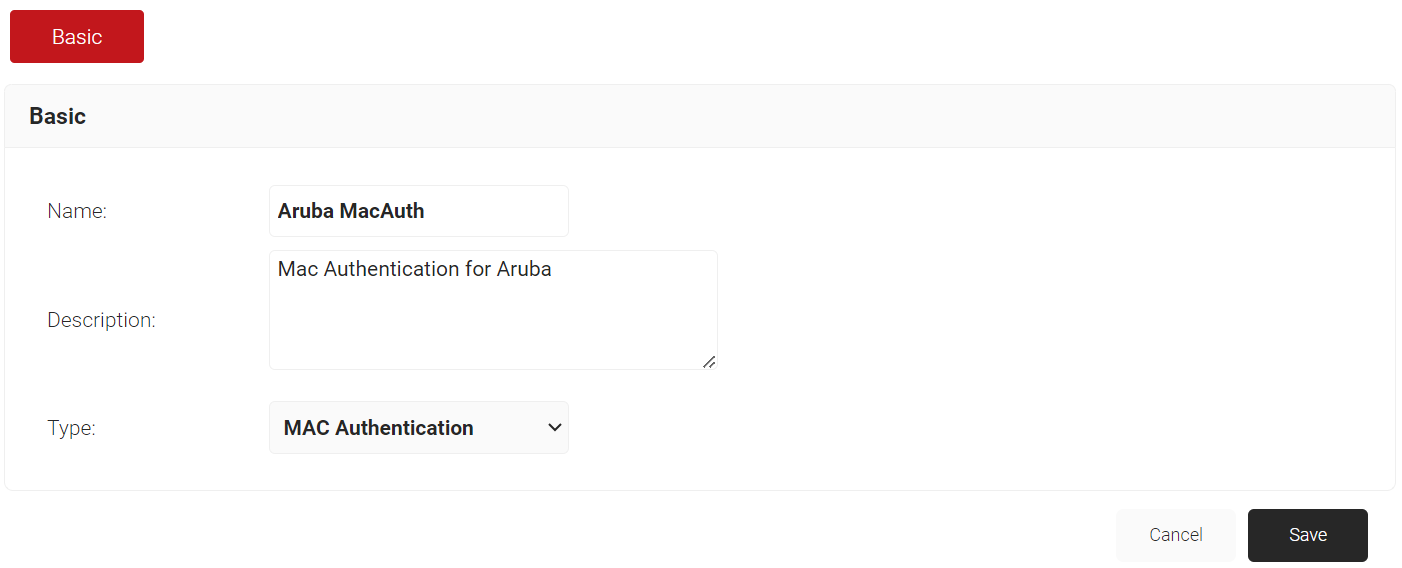
- Click Save.
- The page refreshes and displays the Configuration and Groups tabs.
- Select the Groups tab.
- Click Add group.
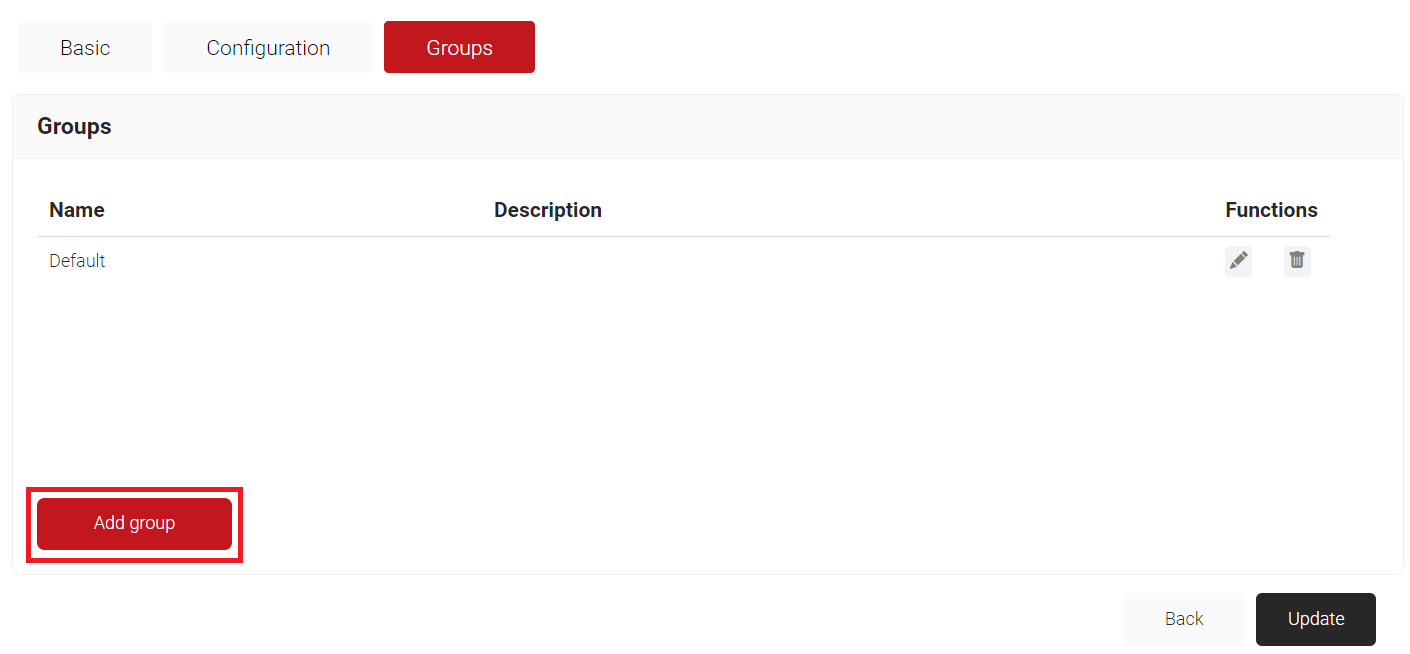
- On the displayed pop-up window, in the Name field, enter a name for your group.
- In the Description field, enter a suitable description for your group.
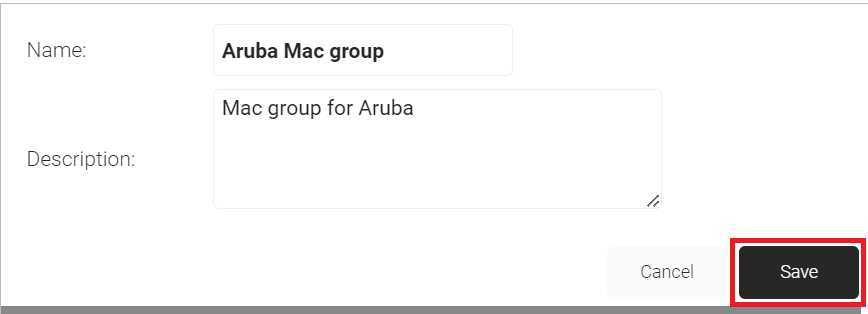
- Click Save.
- Select the Configuration tab.
- Click Add Device.
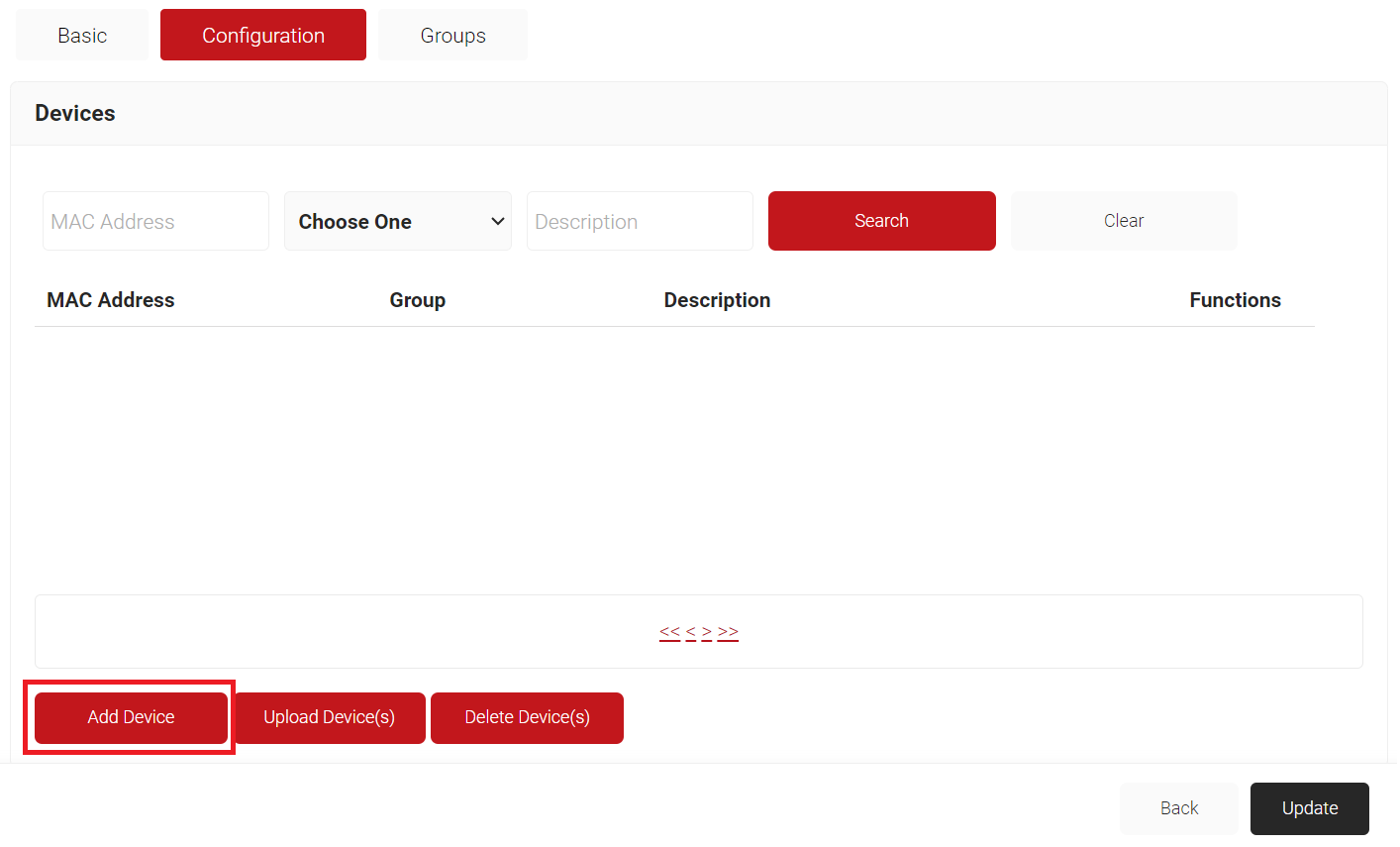
- On the displayed pop-up window, in the MAC Address field, enter the MAC address of the device that you want to authenticate.
- From the Group Name drop-down list, select the group name you created earlier.
- In the Description field, enter a suitable description for your device.
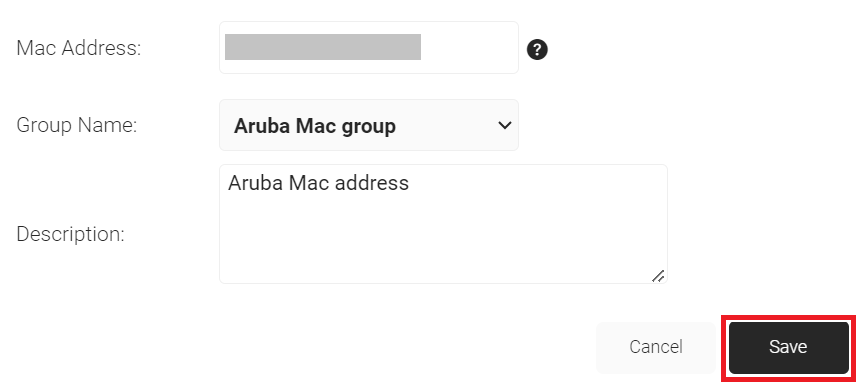
- Click Save.
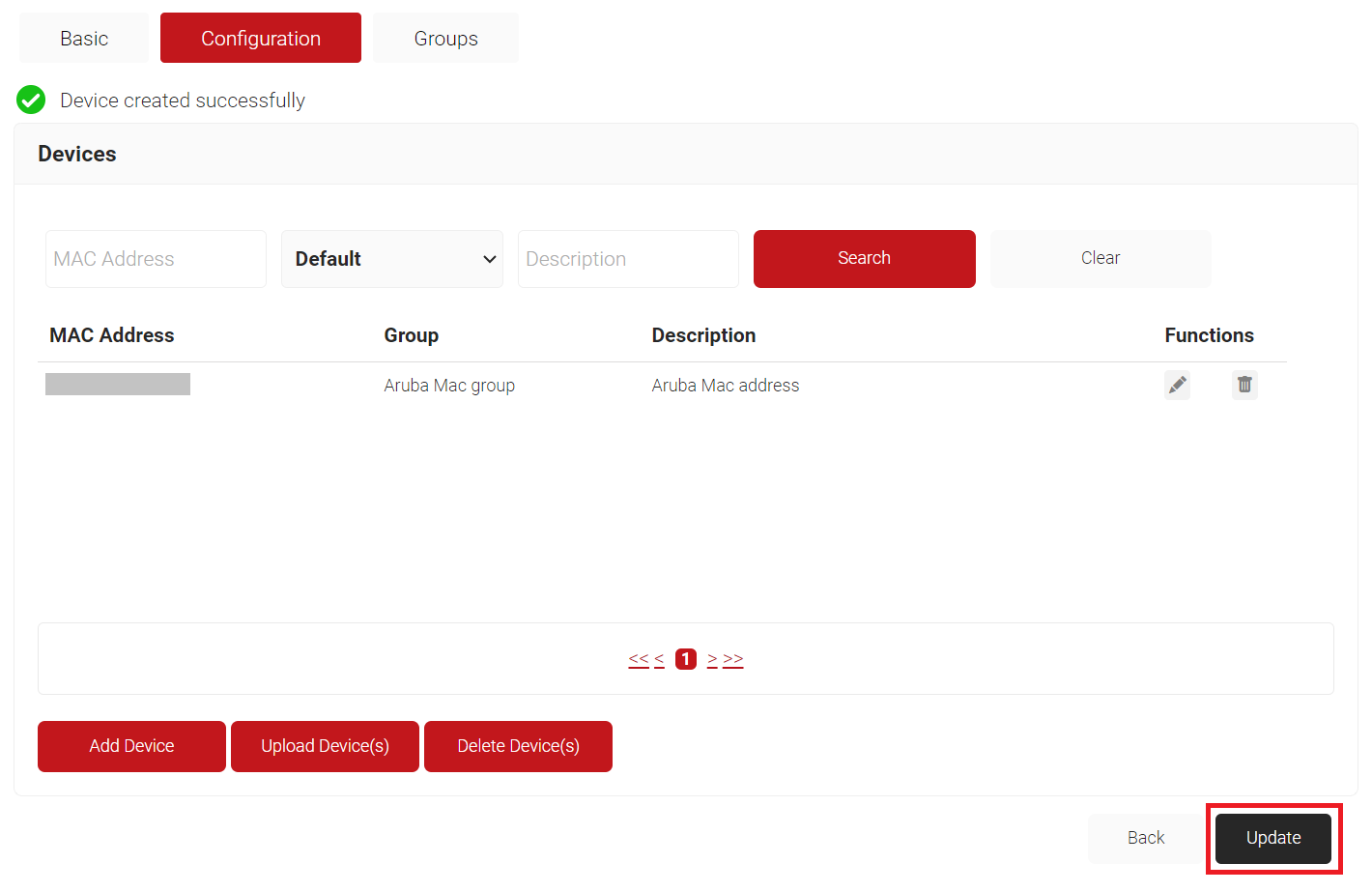
- Click Update.
Set up Policy Workflows and Network
JoinNow Management offers policy-based management to facilitate VLAN-based segmentation. The policies to be configured are:
Creating a Policy Workflows
A policy workflow grants a user access to defined resources. To add a Role policy, perform the following steps:
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to Policy Management > Policy Workflows.
- Click Add Policy Workflow.
- In the Name field, enter a name for your role policy.
- In the Display Description field, enter a suitable description for your role policy.
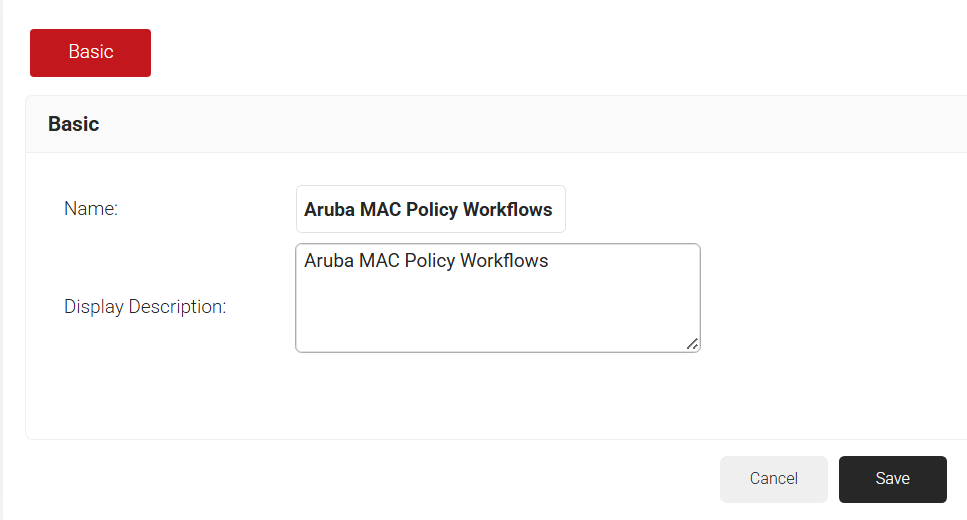
- Click Save.
- The page refreshes and the Conditions tab is displayed.
- Select the Conditions tab.
- In the Conditions section, from the Core Provider drop-down list, select the IdP you created with the MAC Authentication type.
- In the Groups field, select the group you created earlier (refer to the Creating a Core Provider in SecureW2 section).
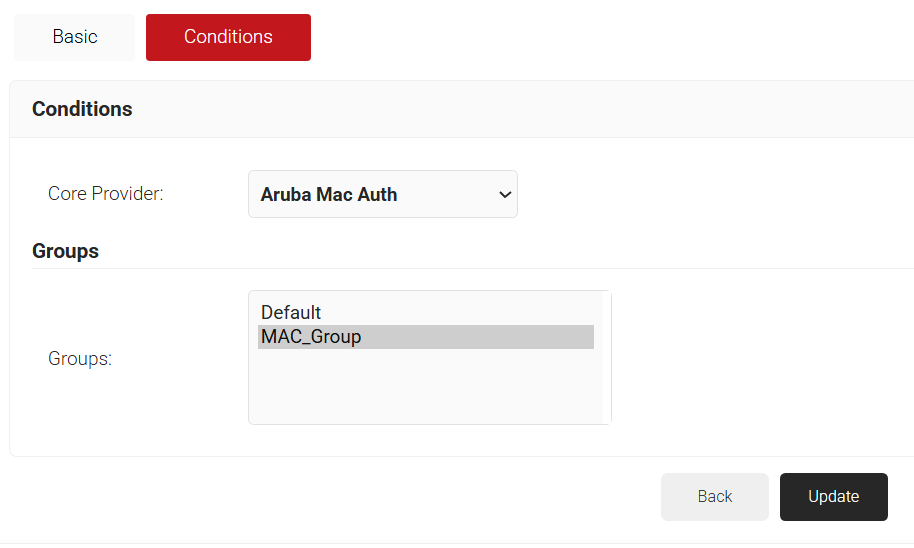
- Click Update.
Network
The purpose of a network policy is to specify how Cloud RADIUS will authorize access to a particular user role. To create and configure the Network policy, perform the following steps:
- Navigate to Policy Management > Network.
- Click Add Network Policy.
- In the Name field, enter a name for your network policy.
- In the Display Description field, enter a suitable description for your network policy.
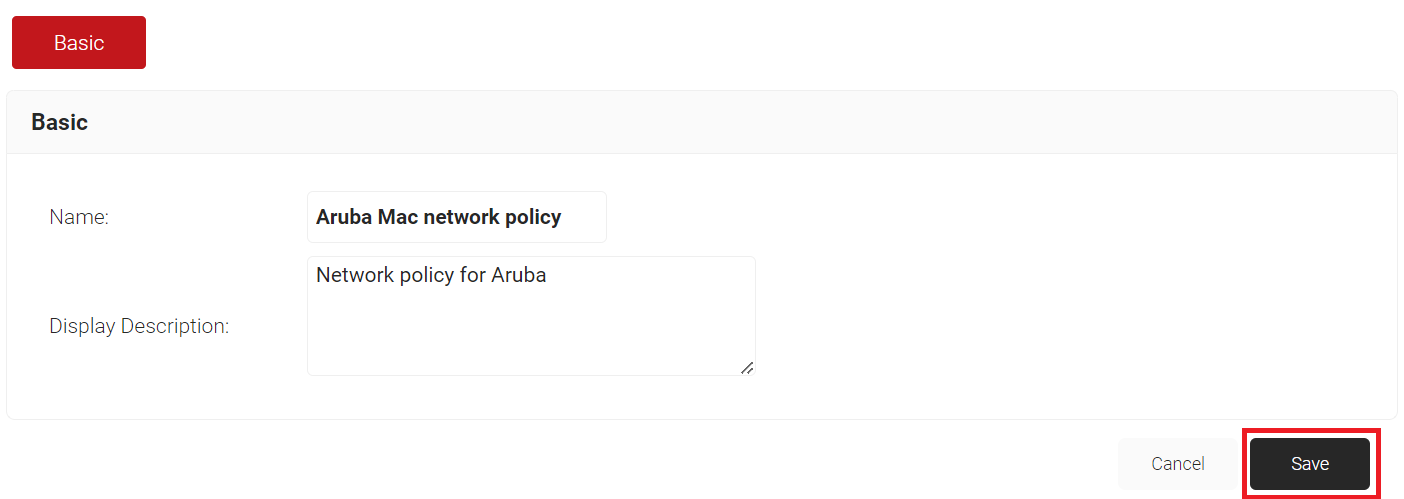
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
- Select the Conditions tab.
- In the Conditions section, select Match All or Match Any based on your requirement to set authentication criteria.
- In the case explained here, we are selecting Match All.
- Click Add rule.
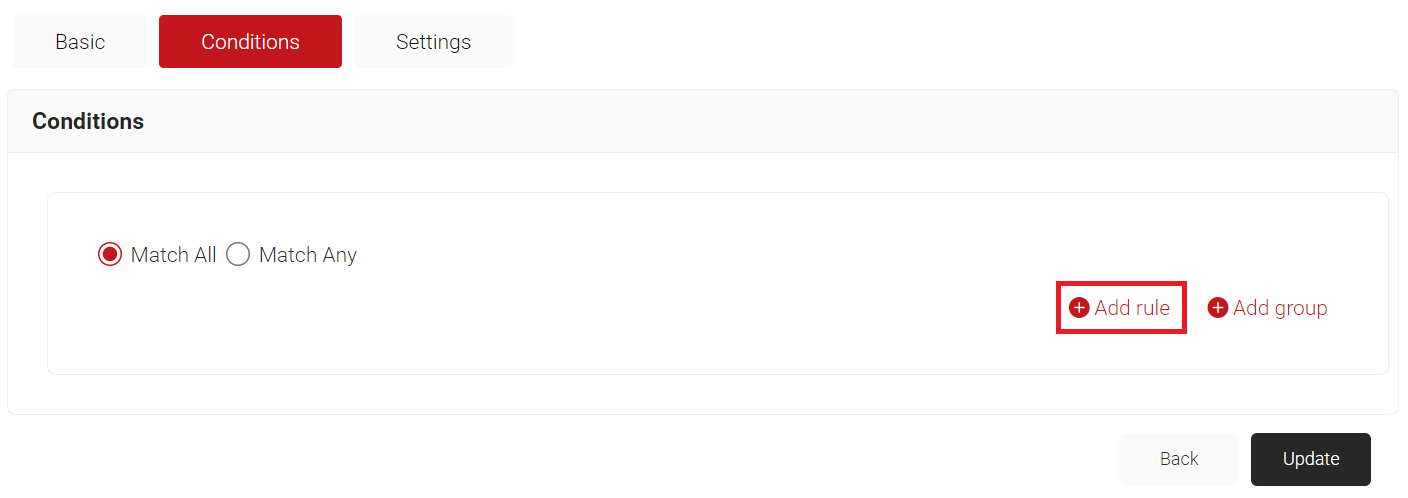
- Expand Identity and select the Role option.
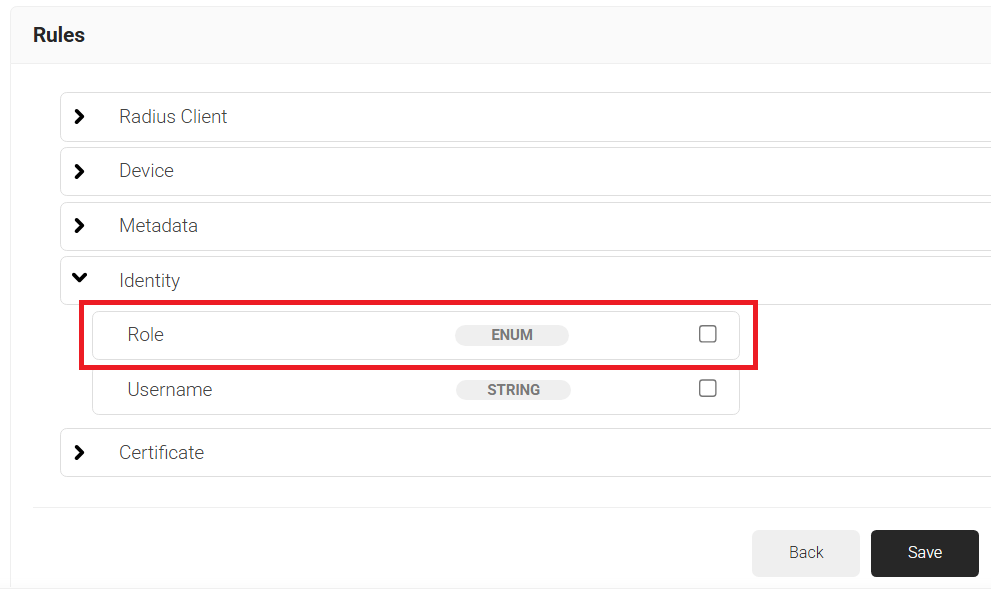
- Click Save.
- The Role option appears under the Conditions tab.
- From the Role Equals drop-down list, select the role policy you created earlier (refer to the Creating a Policy Workflow section).
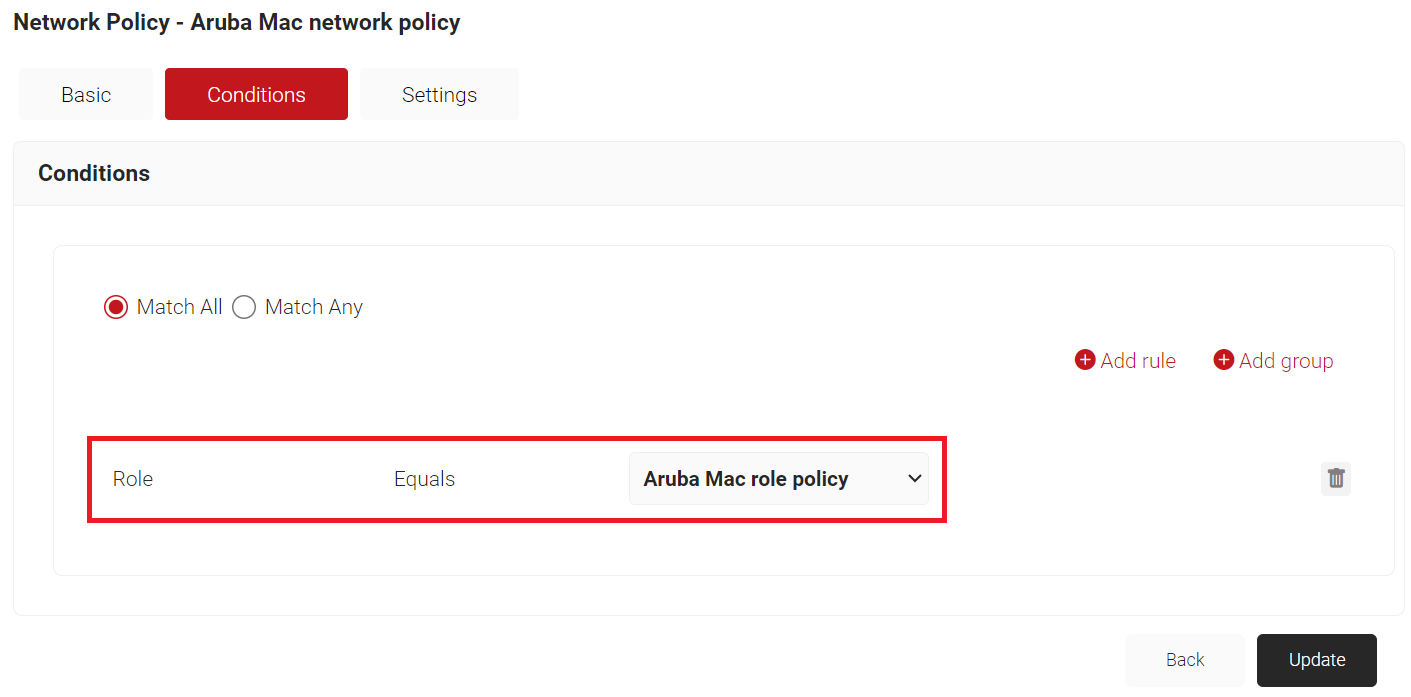
- Select the Settings tab.
- Click Add Attribute.
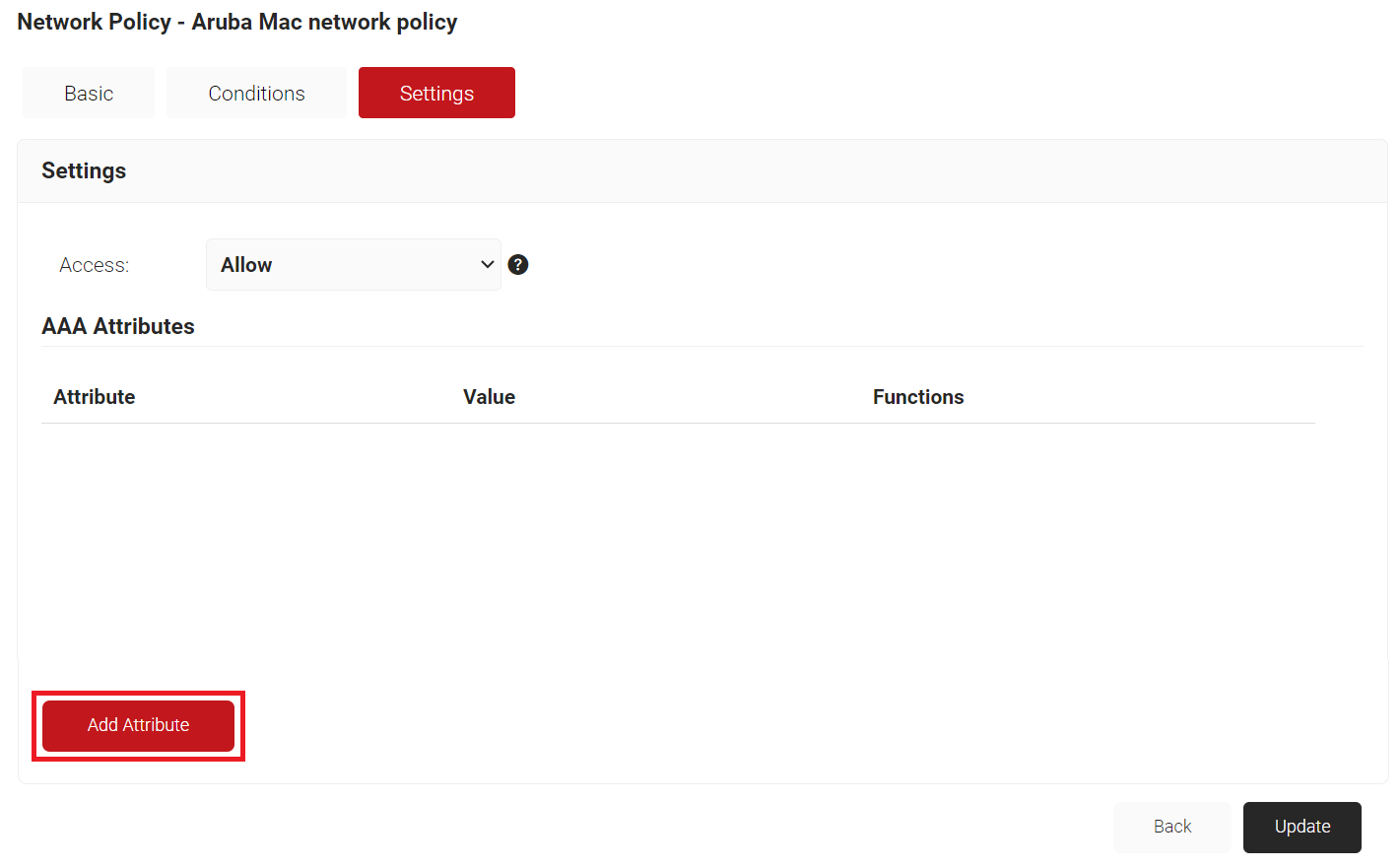
- From the Dictionary drop-down list, select an option: Radius:IETF or Custom.
- From the Attribute drop-down, select Filter-Id.
NOTE: Filter-Id is created on your access point to form a VLAN range.
- In the Value field, enter the VLAN filter-ID you wish to connect to.
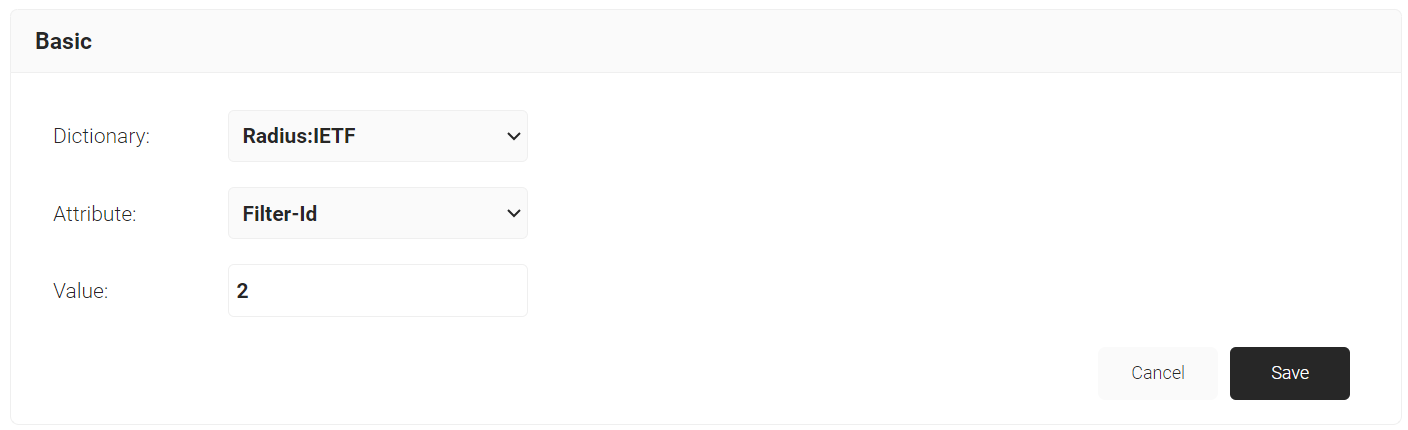
- Click Save.
Aruba IAP Configuration for VLAN
This section describes the steps to create a VLAN in Aruba IAP and then configure Aruba IAP with SecureW2.
Configuring Aruba IAP for MAC Authentication
This section describes the steps to configure a MAC authentication profile in Aruba IAP.
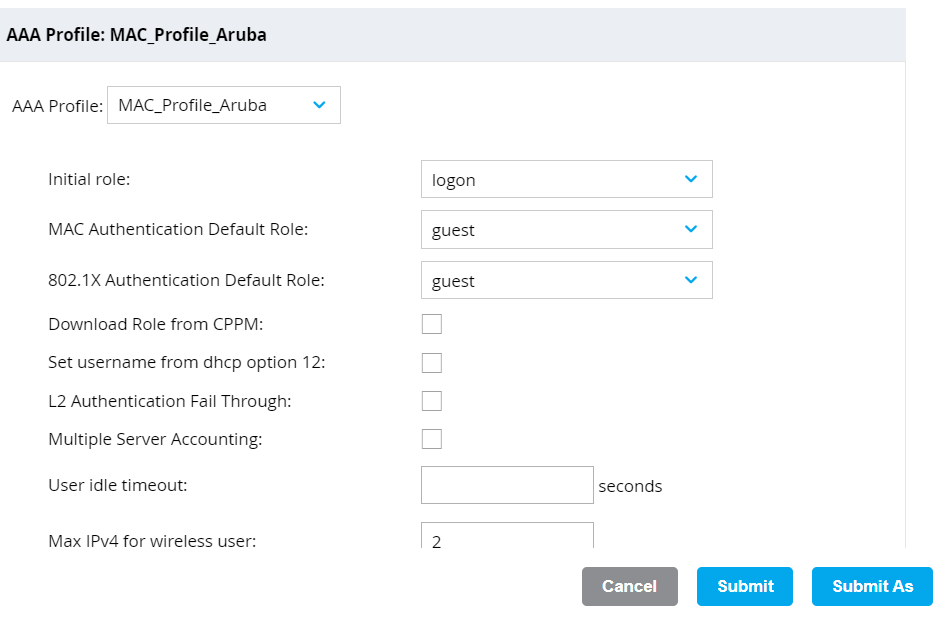
- On the left pane, navigate to Configuration > Authentication > L2 Authentication.
- Click MAC Authentication.
- In the MAC Authentication Profile: New Profile section, click + to create a MAC profile.
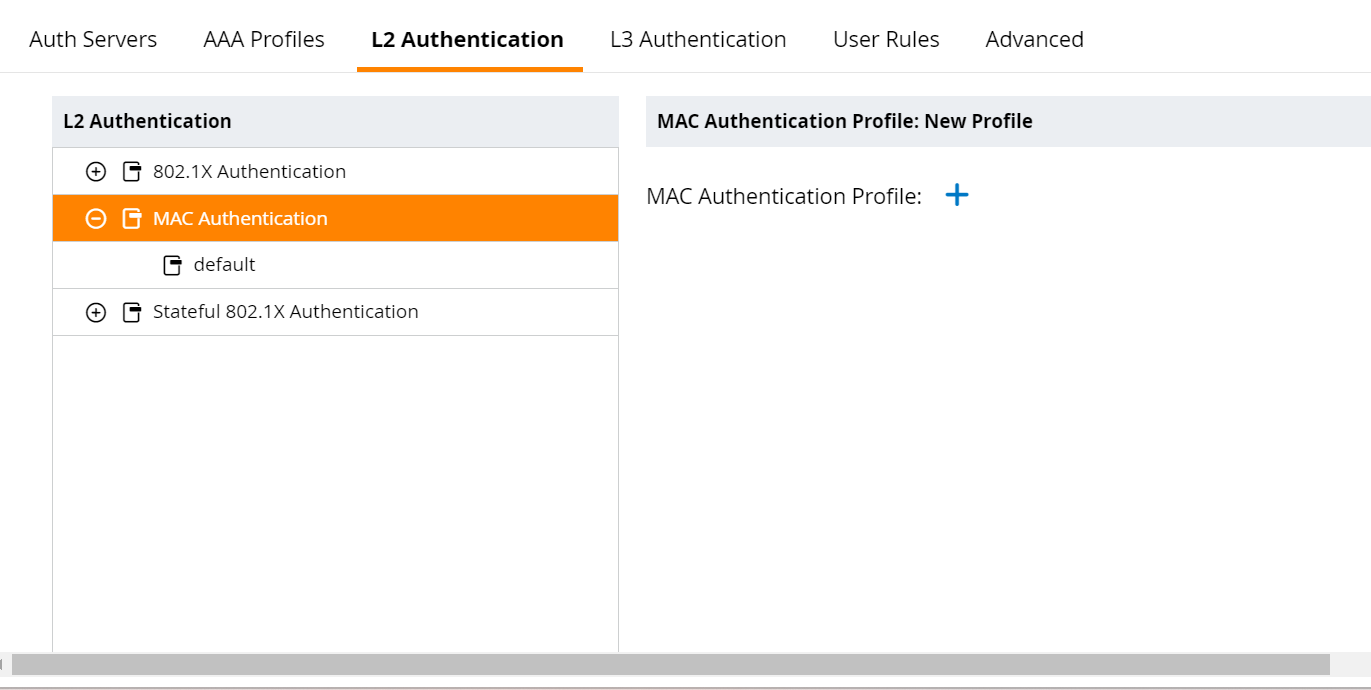
- In the Profile name field, enter a name for the profile.
- Click Submit.
- Select the AAA Profiles tab.
- Expand AAA and in the AAA Profile: New Profile section, click + to create a new profile.
- In the Profile name field, enter a name for the profile.
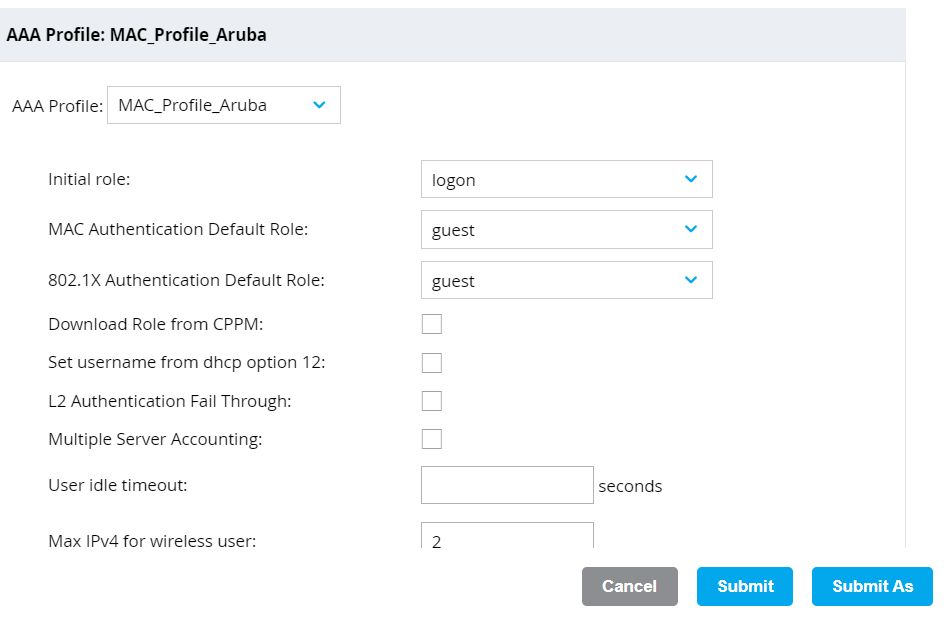
- Click Submit.
Configuring the RADIUS server with Aruba IAP
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to RADIUS > RADIUS Configuration.
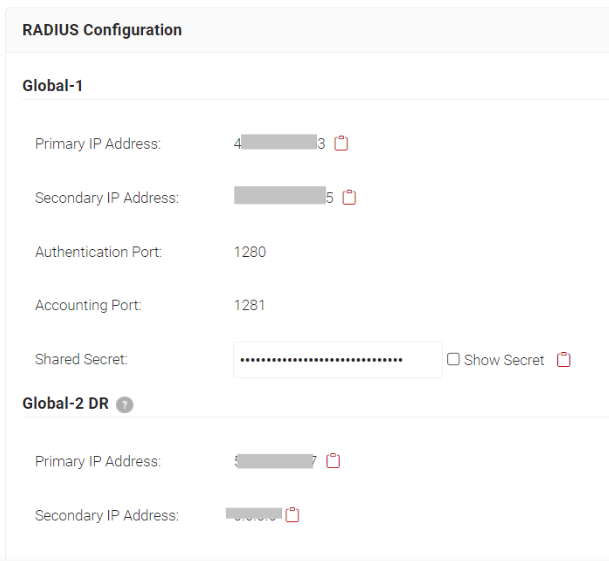
- Copy the Primary IP address on your console.
To configure Aruba IAP and the RADIUS server, follow the given steps.
- In the Aruba portal, on the left pane, navigate to Configuration > Authentication.
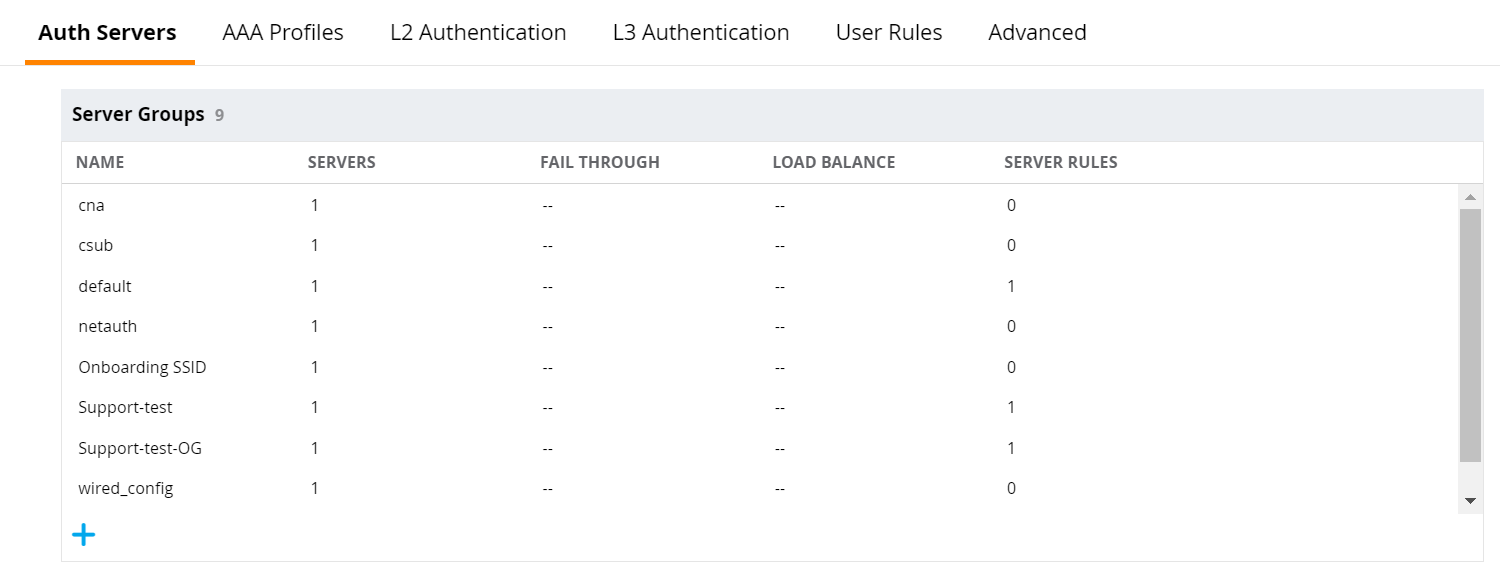
- Select the Auth Servers tab and click +.
- On the displayed page, in the Name field, enter a name.
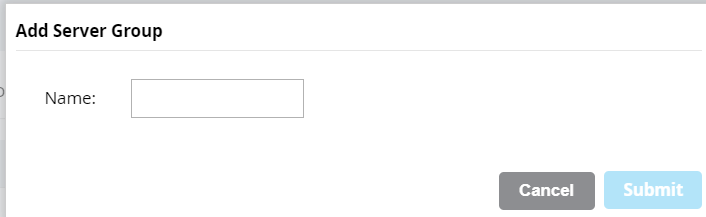
- Click Submit.
- In the Server Groups section, click the group you just created.
- Below the Server Group section, click the + sign to add server details.
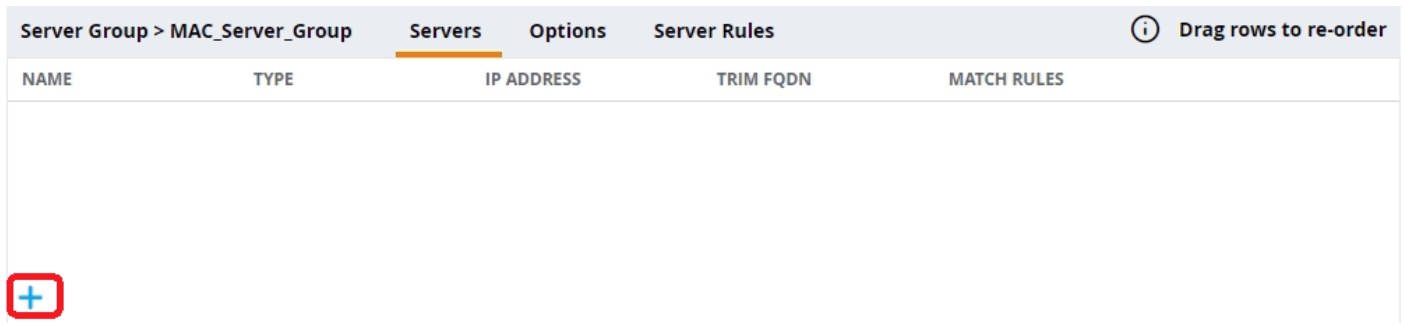
- On the displayed page, select the Add new server option.
- In the Name field, enter a name for your server.
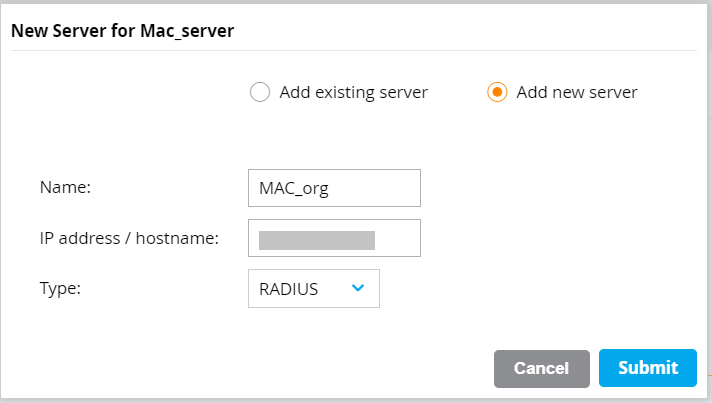
- In the IP address / hostname field, enter the RADIUS IP address that you obtain from the JoinNow MultiOS Management Portal.
- From the Type drop-down list, select RADIUS.
- Click Submit.
- Navigate back to the AAA Profiles tab.
- Click the AAA profile you created earlier (refer to the Configuring Aruba IAP for MAC Authentication section).
- Under the selected AAA Profile, click MAC Authentication Server Group.
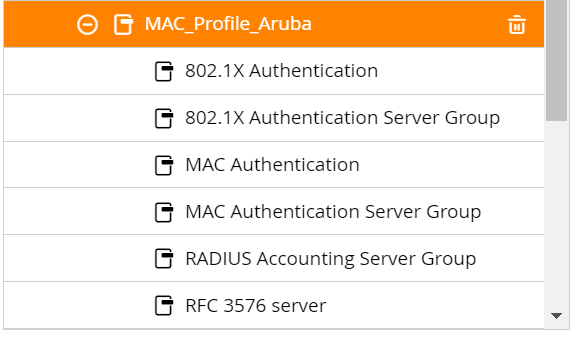
- From the Server Group drop-down list, select the server group you created.
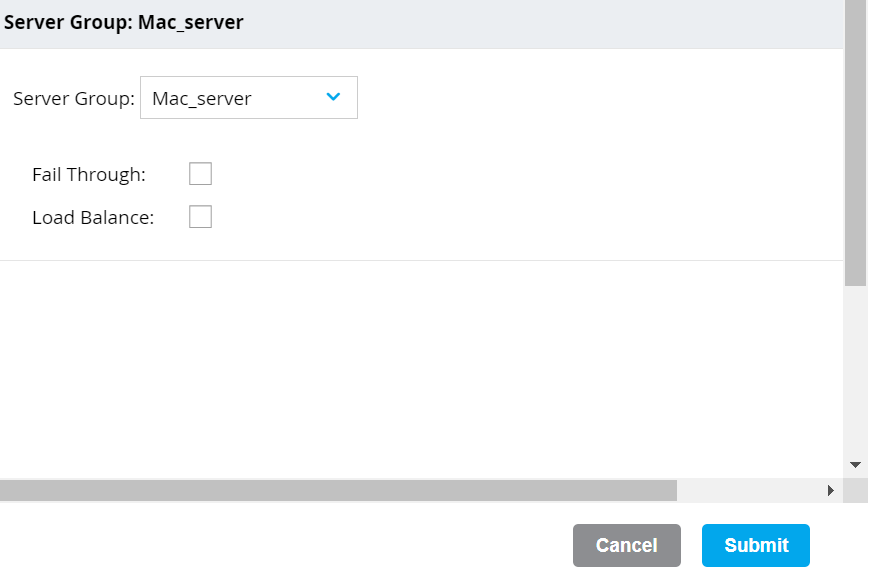
- Click Submit.
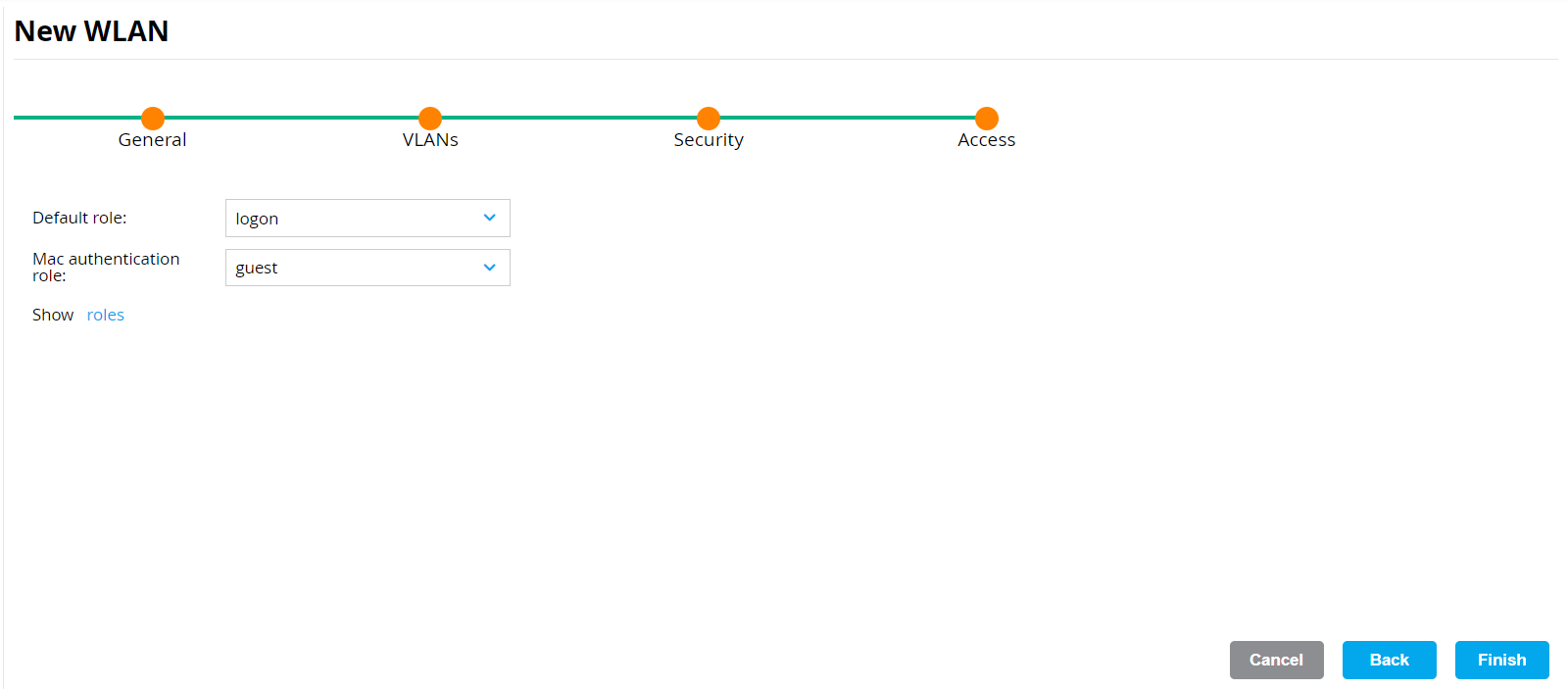
- Navigate to Configuration > WLANs.
- In the WLANs section, click +.
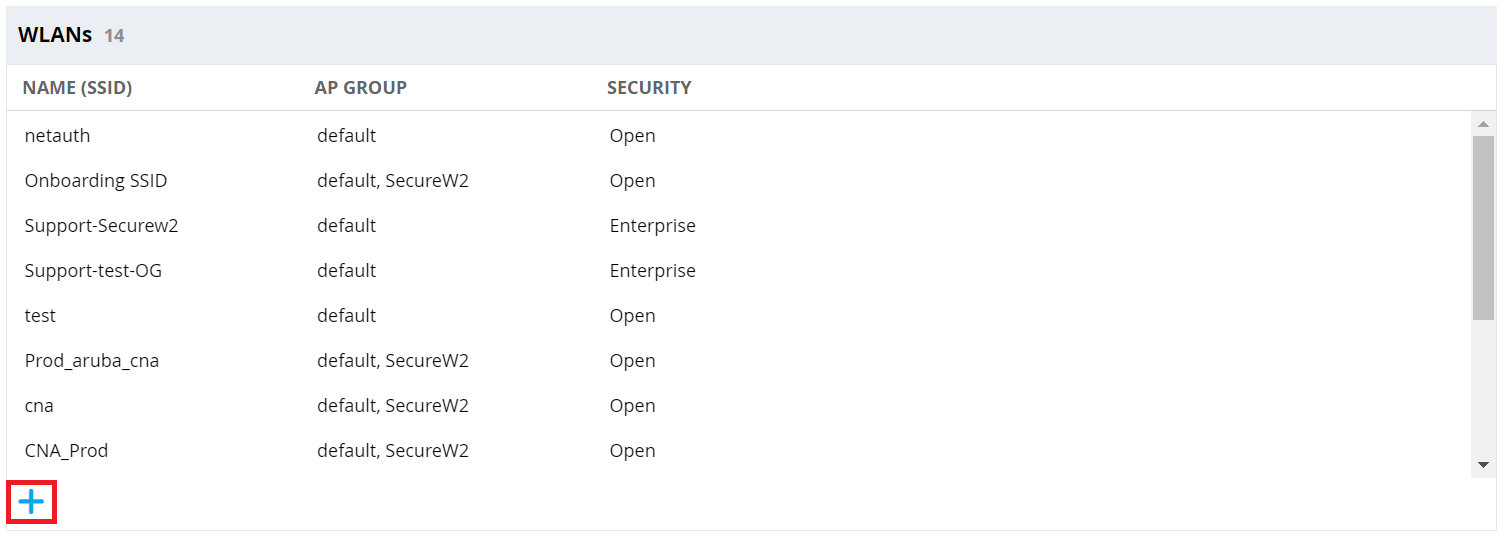
- On the General tab:
- In the Name (ssid) field, enter a name for the SSID.
- For Primary usage, select the Employee option.
- From the Select AP Groups drop-down list, select an option. According to the option, the Broadcast on field is displayed. Select the default option.
- From the Forwarding Mode drop-down list, select an option.
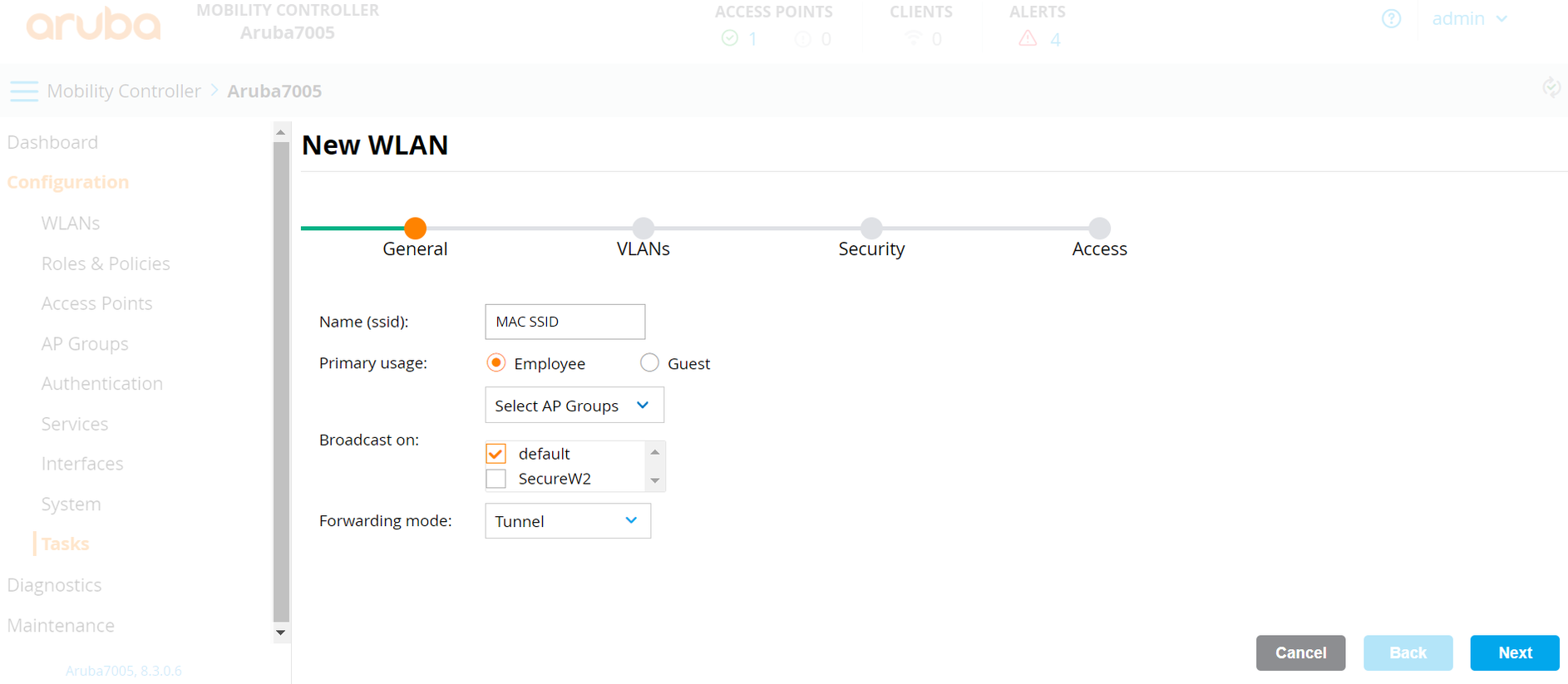
- Click Next.
- On the VLANs tab, select your VLAN ID.
- Click Next.
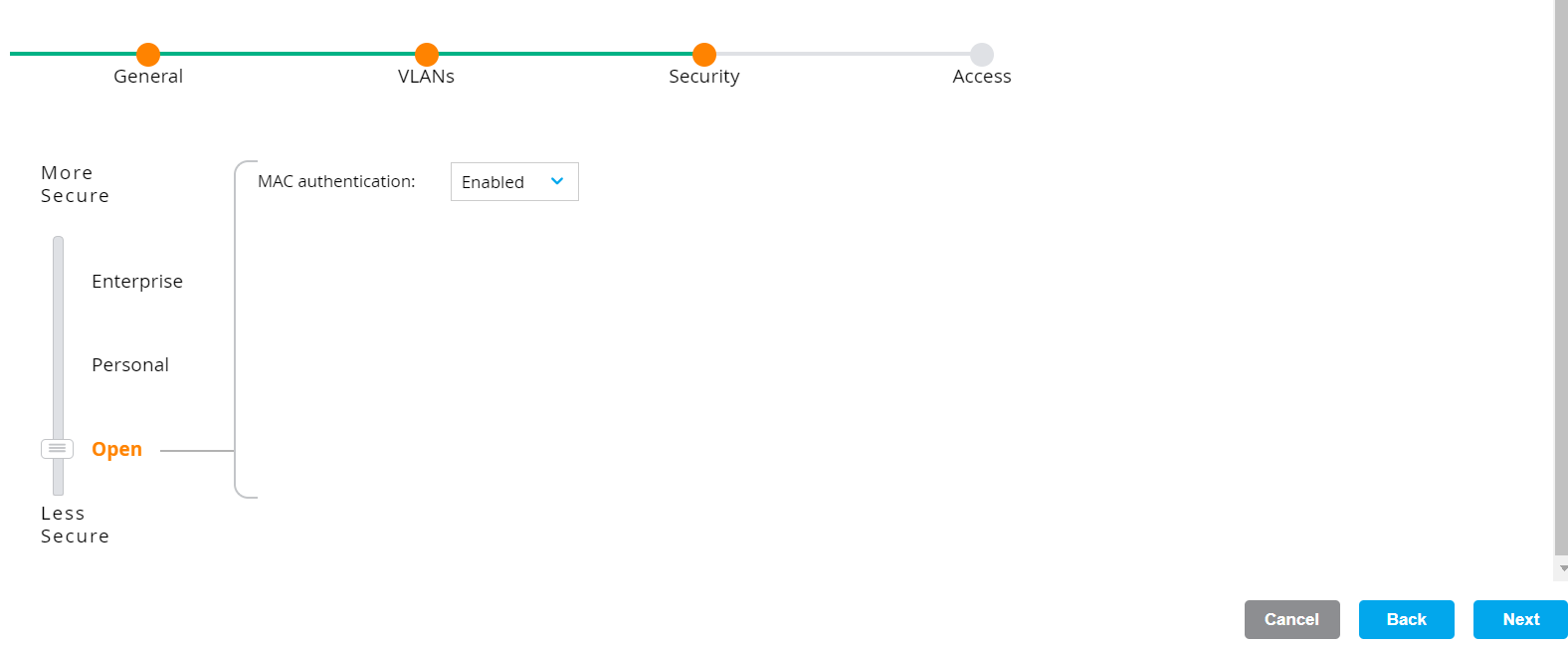
- On the Security tab:
- Move the dial to Open.
- From the MAC authentication drop-down list, select Enabled.
- Click Next.
- In the Access section, select the required roles.
- Click Finish.
- Click the WLAN you created.
- Click Profiles.
- Navigate as shown below.
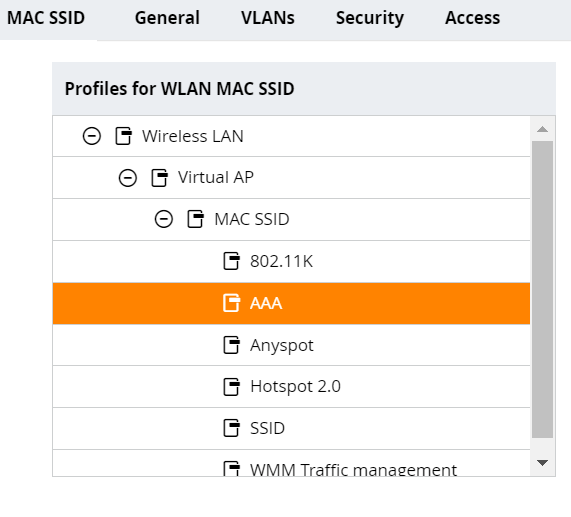
- An AAA Profile opens on the right side. From the AAA Profile drop-down list, select the AAA profile you created earlier (refer to the Configuring Aruba IAP for MAC Authentication section).
- Click Submit.