A PKI certificate, an x.509 certificate issued by a Public Key Infrastructure (PKI), are critical in maintaining the trustworthiness and security of digital interactions. These certificates allow applications and services to create secure connections and authenticate users or devices, making them essential to the entire PKI ecosystem. SCEP (Simple Certificate Enrollment Protocol) plays a crucial role in automating digital certificate enrollment by reducing the manual dependency on network admins in any network infrastructure. Addigy, a mobile device management (MDM) platform built specifically for Apple settings in the cloud, provides efficient device management by letting IT departments remotely adjust settings, handle app administration, and impose security standards on Apple gadgets.
This guide explores the practical configuration aspects of deploying SCEP certificates utilizing the combined power of Addigy and SecureW2’s JoinNow Connector PKI. By combining the capabilities of Addigy with those of SecureW2’s robust public key infrastructure, organizations can expedite the deployment of SCEP certificates with precision and simplicity.
Join us as we break down the complexities of this configuration and show you how to deploy SCEP certificates smoothly using our JoinNow Connector PKI and Managed Device Gateway, enabling you to enhance the security of your network through a streamlined and well-managed certificate deployment process.
TECH OVERVIEW
- Set Up the Managed Device Gateway API in the JoinNow Connector Public Key Infrastructure (PKI)
- You can easily set up SCEP gateway APIs using our Getting Started Wizard.
- Establish a trusted Intermediate Certificate Authority to configure the payload to include certificate enrollment policies.
- Configure the SCEP Profile
- Create a SCEP URL by generating a shared secret and access token using SecureW2’s Token wizard.
- Configure the Wi-Fi Profile
- Configure the Wi-Fi settings to allow stored certificates to connect to the correct server.
- Configure the profile for EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) authentication, the most secure authentication protocol.
- Push the Payloads to Managed Devices
- Add the SCEP URL to the Addigy portal so you can push out configuration profiles to all Addigy devices and
- have them authenticated to the network.
- After authentication, you can also push out a payload, allowing devices to enroll for a certificate with digital signatures.
Create an Apple Push Digital Certificate
You’ll need to create Apple push digital certificates to establish secure communications between your managed Apple devices and your certificate management system. You can create an Apple Push Certificate by downloading an Addigy Certificate Signing Request (CSR) file and uploading in Apple.
- On the Addigy Portal, go to Accounts.
- Click MDM Settings.
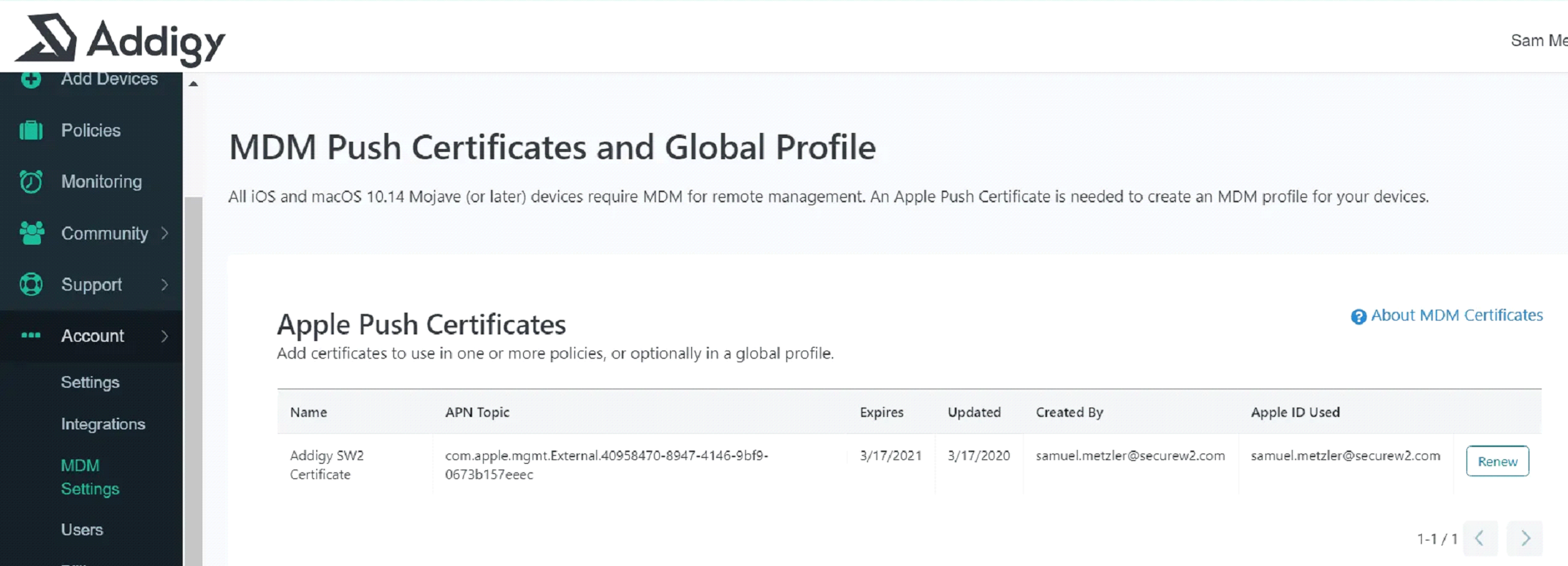
- Click MDM Settings.
Download CSR File.
- Click Add Certificate under Apple Push Certificates.
- Download Addigy CSR.
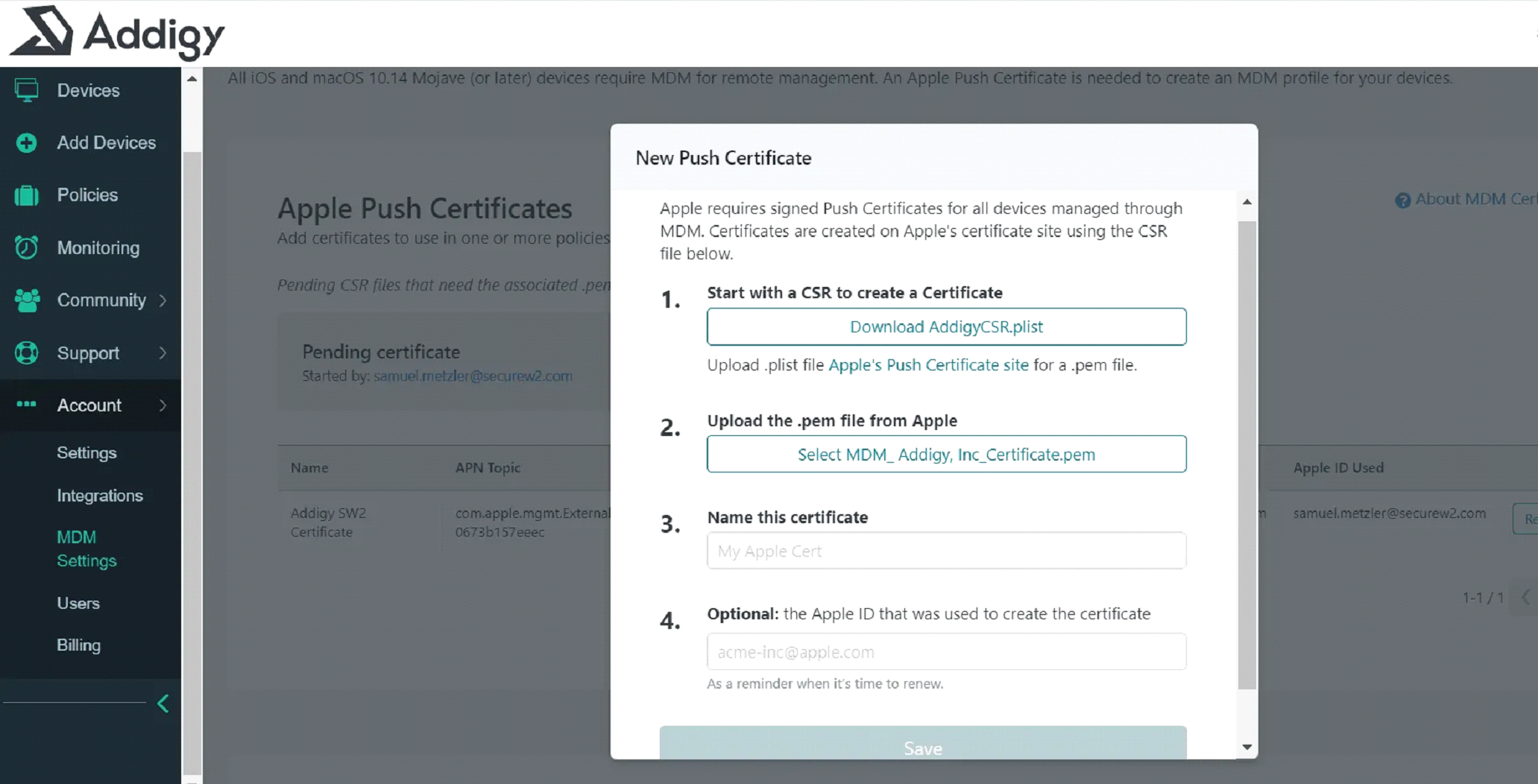
Go to this link.
- Click Create a Certificate.
- Upload your Addigy CSR
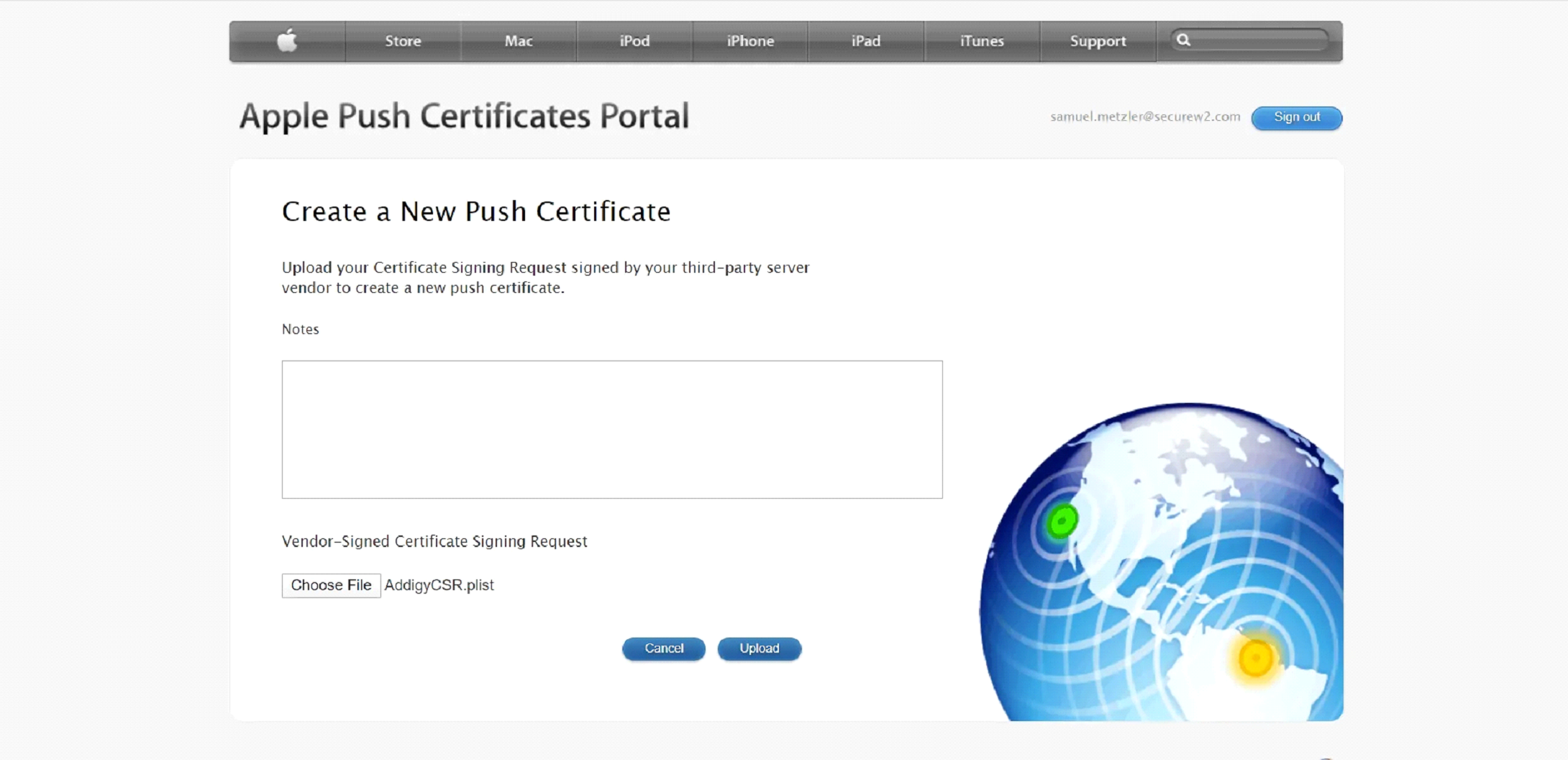
An Apple Push Certificate will be generated and a .pem file will be available for download.
Upload the .pem file.
- Go back to MDM Settings in Addigy.
- Click on Add Certificate.
- Upload the .pem file.
Click Save.
You have created an Apple Push Certificate with digital signatures for your managed devices. You must establish a secure connection so your managed devices can enroll for the certificate.
Building a .mobileconfig with the JoinNow Public Key Infrastructure
For most platforms, you can create custom Certificate Authorities and generate a SCEP URL with SecureW2’s Management Portal. These can be imported into your platform’s UI and deliver digital certificates.
Including a Certificate Authority (CA) in the mobile configuration file is critical for establishing confidence between the RADIUS server we connect to and the CA that provides our client certificates. In essence, anyone may use the public part of a certificate to validate its validity by proving ownership of the private keys used for its signing. Trust in the CA becomes critical since it validates the certificates’ authenticity. As a result, when we trust the CA, we may be certain that any data delivered to the certificate holder reaches its intended destination and that the individual or device approves everything signed with the certificate holder’s private key.
Addigy has no option, so you must build a custom mobileconfig with the SCEP URL and Shared Key. This can all be done in SecureW2’s Management Portal. After you’ve done this, reach out to the SecureW2 Support team. They can assist you in generating a custom .mobileconfig file to upload to Addigy.
Creating a SCEP URL and Shared Secret
To use an SCEP gateway for managed devices to enroll for digital certificates, generate an SCEP URL to communicate with SecureW2’s Public Key Infrastructure.
- Log in to the JoinNow Management Portal.
- Navigate to Identity Management > API Tokens.
- Click Add API Token.
- Enter a name and description for the API token on the displayed screen in the corresponding fields.
- Select as Type as SCEP Enrollment Token.
- From the SCEP Vendor drop-down list, select Addigy.
- From the Certificate Authority drop-down list, select a CA certificate Authority.
- Click Save. A .csv file containing the API secret and Enrollment URL is downloaded. In addition, the Enrollment URL is displayed on the screen.
Upload a .mobileconfig file to Addigy
Now that you’ve created a mobileconfig, you can plug it into the Addigy portal and will be able to push the payload to every managed device.
- Create a Profile in Addigy.
- Go to Policies.
- Click Catalog towards the top.
- Click on Custom Profile and Add Profile.
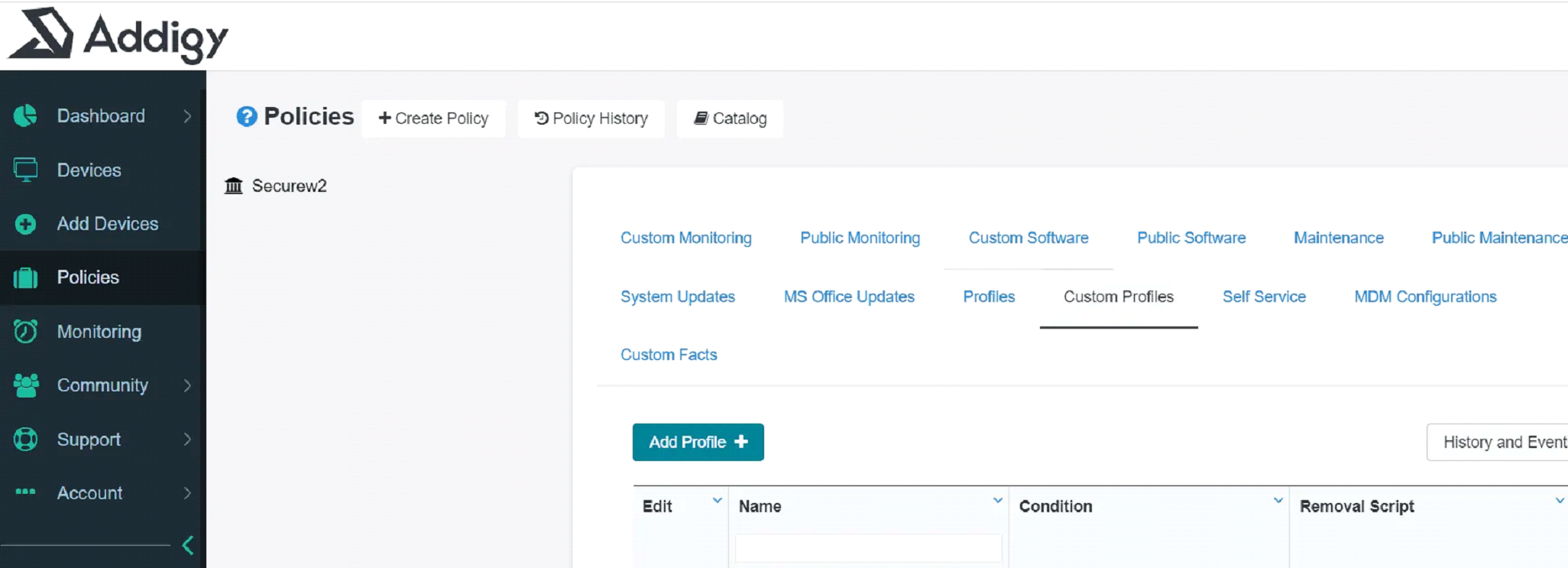
Upload your .mobileconfig file.
- Enter your profile name.
- Under Installation Files, click Select File(s) to upload your .mobileconfig file.
- Under Installation Script, the output will be shown after uploading your file.
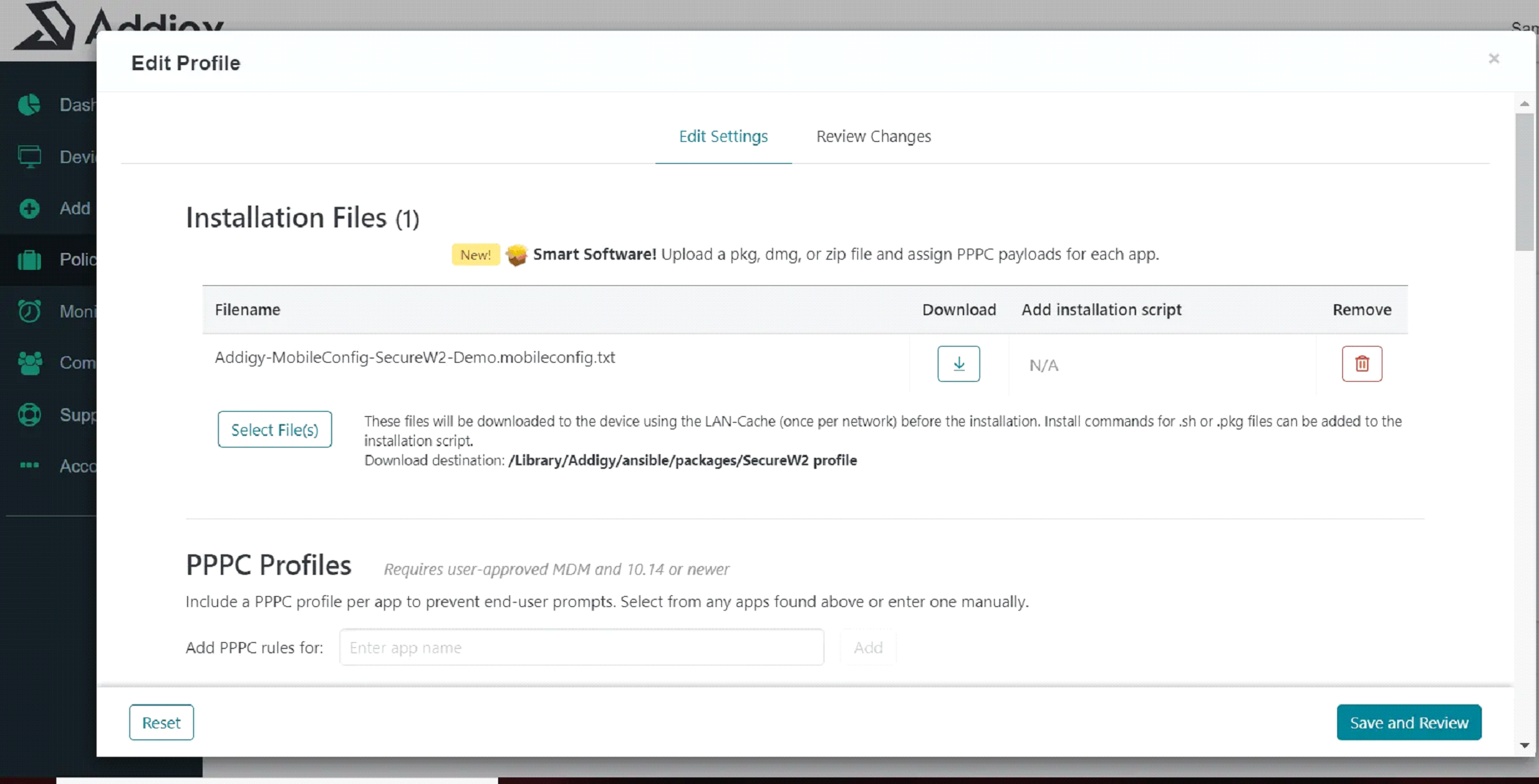
Click confirm.
Now that you’ve created a custom profile in Addigy, you can start deploying that profile to your managed devices.
Do We Need to Create a SCEP Profile?
No, we do not. At the time of updating this documentation, Tuesday, October 3rd, 2023, Addigy does not have SCEP Profiles available. For this reason, we are creating a custom .mobileconfig to distribute our SCEP URL and Secret.
Adding an iOS Device to Addigy Management
Incorporating iOS devices into your Addigy management portal is a smooth process. Here, we will explain how to get the configuration profiles on an iOS device.
- Log in to the Addigy management portal.
- Navigate to Policies.
- Find your device on the portal and click GoLive.
- Switch your device from the ‘Onboarding’ to the ‘Production’ policy.
- This will deploy the Wi-Fi profile and SCEP payload.
- Navigate to MDM Configuration.
- Check that the Addigy SCEP profile is uploaded.
- Click on the Addigy SCEP profile to view the payloads and digital certificate.
- Hover over Production.
- Click Confirm Production policy deployment.
- Click on “View Details” to see the SCEP profile connecting to your iOS device.
- The profile will take a few minutes to appear on your device.
- To find your profile, go to the Settings app and find Device Management under the General section.
- You can also view device certificates here.
- Once the profile is on your device, go to Settings > Wi-Fi and connect to the Addigy SCEP network.
- The device will connect to the network without any prompts.
- Your connected device should now be added to the Addigy management portal.
Removing the iOS Device from Addigy Management
If you want to remove the configuration profiles from an iOS device, here is how to do that within Addigy.
- To remove the device from the network, navigate to Policies > Production.
- Click on your device and change the policy from “Production” to “Onboarding”.
- Click on Onboarding and confirm the configuration.
- The profile will be pulled off the device, removing it from the network.
- The Wi-Fi profile and SCEP payload will no longer appear under Device Management.
- The device will connect to the setup Wi-Fi and be removed from “Policy Devices” on Addigy.
Verifying the SCEP Certificate on the iOS Device
If you need to verify that a SCEP certificate is on a network device, here’s how to do it.
- Log in to the SecureW2 management portal.
- Navigate to PKI → Certificate Authorities → and click Certificates on your Issuing Certificate Authority.
- Copy either the serial number or the common name.
- Paste the ID into Addigy under the Devices tab.
- You will be able to find the device attached to that digital certificate.
Revoking a SCEP Certificate from an iOS Device
If you want to revoke digital certificates, you can do so easily in SecureW2’s JoinNow Connector Public Key Infrastructure. Each Certificate Authority (CA) you build in the JoinNow PKI comes built with a Certificate Revocation List (CRL). When you revoke certificates in the platform, the PKI certificates are automatically added to the CRL.
- Go back to Certificates in the SecureW2 Management Portal.
- Click “Revoke” on the certificate.
- If you try to connect to the SCEP Wi-Fi network, it will not automatically connect you to the network.
- Instead, you’ll see a login credentials prompt.
Automated SCEP Certificate Deployment with Addigy and SecureW2
In this thorough guide, we’ve eased the process of issuing digital certificates and building a solid certificate policy for increased network security and a smooth user experience. Administrators may now easily assure the automated distribution of SCEP certificates across all managed Apple devices by seamlessly connecting Addigy and SecureW2. This potent combo uses Addigy’s cloud-based MDM platform and SecureW2’s advanced Public Key Infrastructure (PKI) to improve network security while reducing administrative constraints.
With SCEP certificate deployment, MDM can automatically issue digital certificates, which enhances network security and reduces administrative burdens. The combination of Addigy and SecureW2 provides your organization with a cost-effective and efficient certificate management solution, simplifying maintaining a secure network environment.
As you embark on this journey towards enhanced network security, look into some of our innovative products, such as Cloud RADIUS, which adds an extra layer of security to your network as it is compatible with almost all Cloud Identity providers such as Azure, Google, and Okta.
Contact us to learn how Addigy and SecureW2 can transform your organization’s network security and authentication processes.