Introduction
SSL is vital to the health of the Internet as a whole, but when it comes to protecting your network and devices, additional measures are required. Malicious actors can use SSL to smuggle malware through firewalls and antivirus software, a technique sometimes referred to as exploiting “the blind spot”.
Setting up SSL Inspection (also known as SSLI or SSL Decryption) allows you to keep the benefits of SSL while browsing the web, but gives the network operator (you) a peek into their traffic. That confers a few key benefits:
- Your organization’s firewall can function effectively
- Ensures compliance with privacy and security standards
- Allows administrators total access to network usage information
When you invest in a PKI, it improves security across the network. SecureW2’s PKI Services allow SSL Inspection certificates to be installed, while a client certificate can simultaneously be enrolled and configured for VPN or Web-Application Authentication. This guide shows you how to generate and push your SSLI Root CA when enrolling end users for a client certificate.
Tech Overview
- Configure SecureW2 for SSLI on Palo Alto
- Generate a .p12 file to upload later to the Firewall for SSLI. Be sure to save it somewhere safe since you only get one.
- Set up the onboarding device profile that will be pushed to all devices so they can easily self-enroll themselves for VPN certificates.
- Create and download the Root CAs for the devices and Intermediate CAs to later upload to Palo Alto for VPN authentication.
- Configure Palo Alto for SSL Inspection
- Import the intermediate CA for SSL Decryption to Palo Alto.
- Set up necessary policies.
- Configure Palo Alto to allow SSL Decryption while using a VPN
- Import the VPN Intermediate and Root CAs to Palo Alto.
- Setup SecureW2 Cloud RADIUS for Authentication
Configure SecureW2 for SSL Decryption on Palo Alto
Navigate to Device Onboarding and, underneath that section, select Getting Started.
Here you will see our Getting Started Wizard, which configures everything you need to start your SSL Inspection deployment. Configure the wizard settings as shown in the screenshot below.
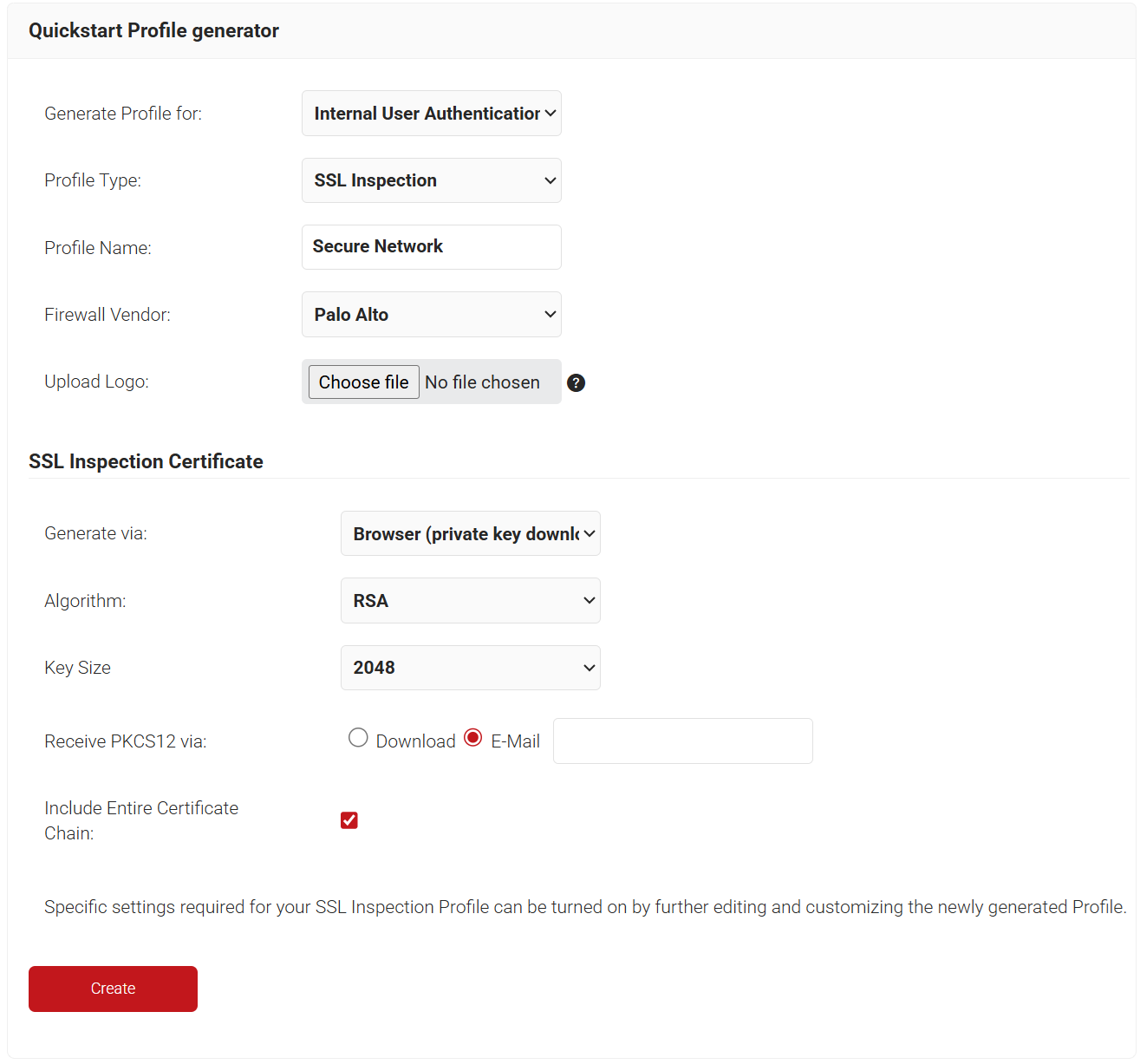
After clicking create, two things will happen.
- A .p12 file will be generated
- Before it is generated, you will be prompted to create a password, which will be used to password lock the .p12 file.
- This .p12 file is what will be uploaded to your SSL Inspection configuration.
- This .p12 file is only generated once. Make sure it’s saved in a safe place.
- A landing page will be generated
- This landing page can be used to install SSL Inspection certificates on end-user devices
- This landing page automatically detects the device’s operating system and deploys the appropriate client to install the certificate.
- However, we won’t use the landing page generated with this network profile. We will only use it to create the Root CA we need for SSL Inspection and to import that CA into the Network Profile we will create in the next step.
Now we need to generate the Root CA from this Network Profile and download it so it can be installed at the same time our VPN Certificate is configured on the device.
- Navigate to Dynamic PKI and select Certificate Authorities.
- Locate the Root CA that is associated with the Network Profile you just created.
- It should be named “Name of Network Profile” Root CA.
- Click Download.
While we’re here, we also need to download our Intermediate CA so that we can upload it to our Firewall later.
- Locate the Intermediate CA that is associated with the Network Profile you just created.
- It should be named “Name of Network Profile” Intermediate CA
- Click Download.
Configure SecureW2 for VPN
We need to run our Getting Started Wizard one more time, but this time to configure a Network Profile that will be used for enrolling our end users for a certificate that can be used for VPN, web applications, and many other things.
Navigate to the Getting Started Wizard like you did in the previous section, but this time, configure your settings as follows: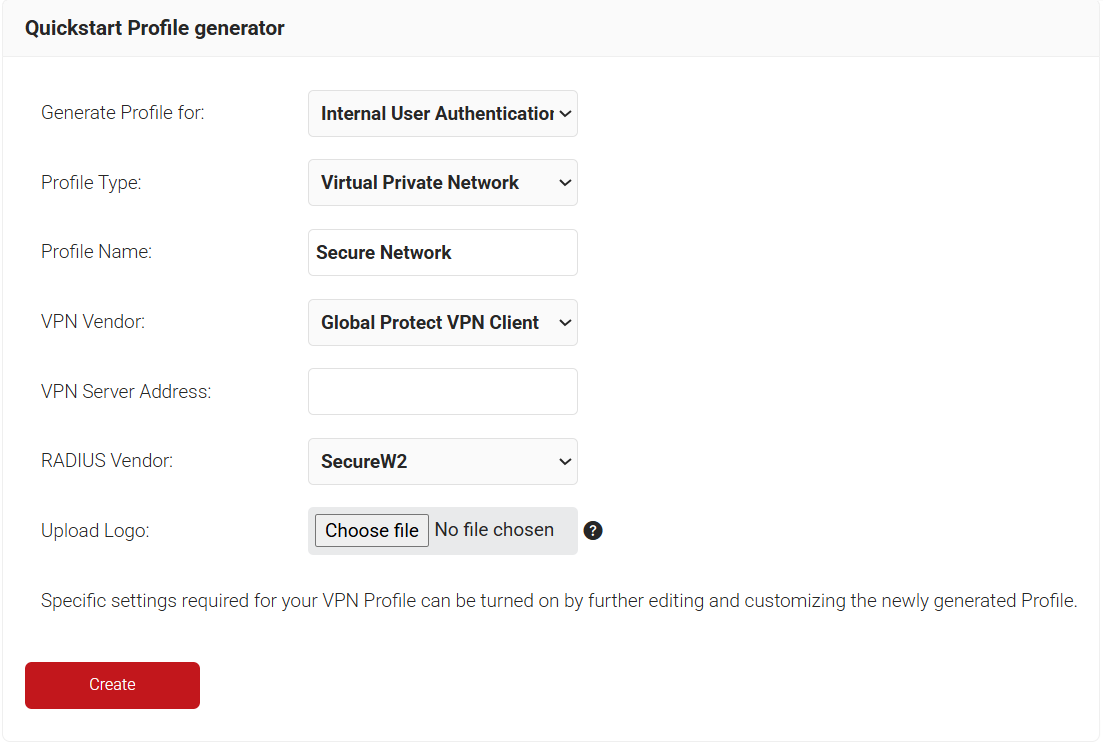
After the Wizard has finished, you will have a second Network Profile. We need to upload our SSL Inspection Root CA to our new Network Profile.
- Click Edit on our new network profile.
- Under the Certificates section, click Add/Remove Certificate.
- Under Private Certificate, click Choose File and select the Root CA we downloaded in the previous section.
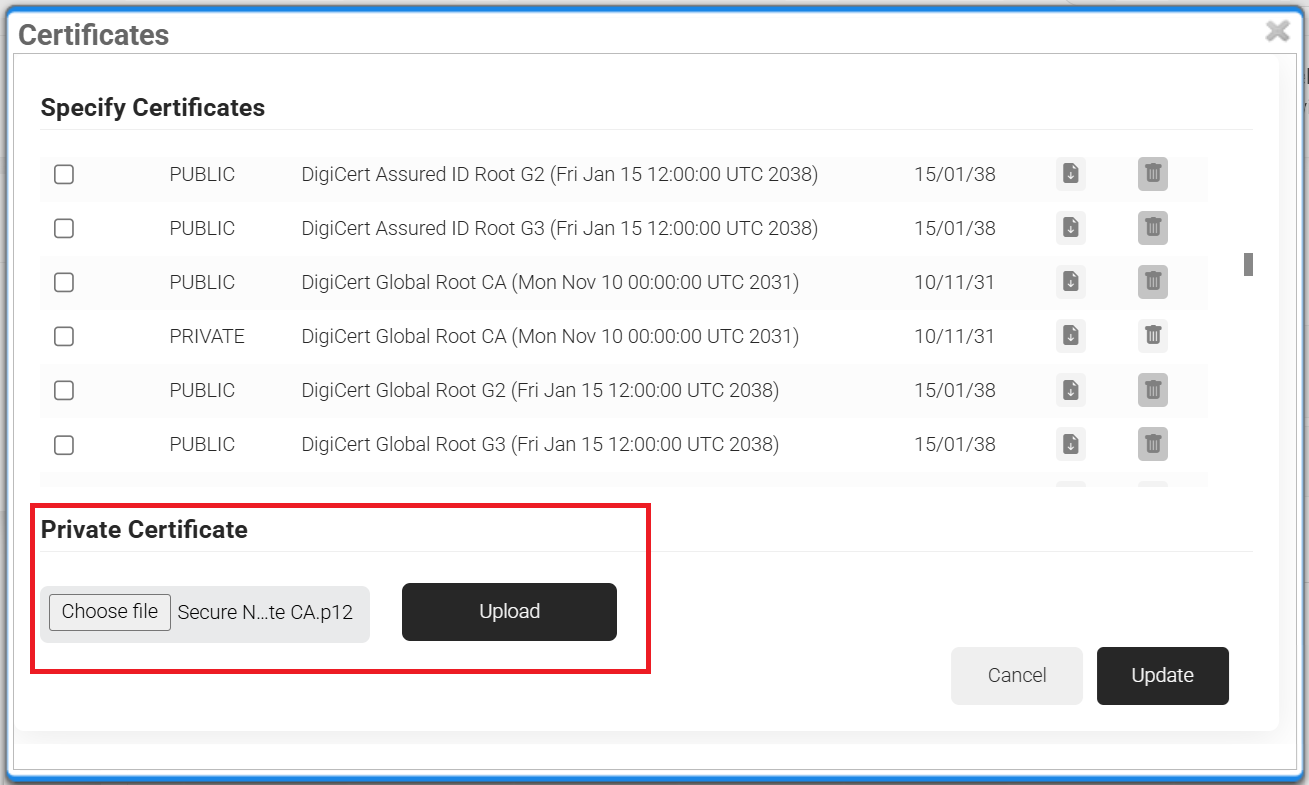
- Click Upload.
- Now, locate the Certificate we just uploaded in the Specify Certificate section, and check Install.
- Click Update.
- The new certificate now appears in the Certificates section, and you click Edit.
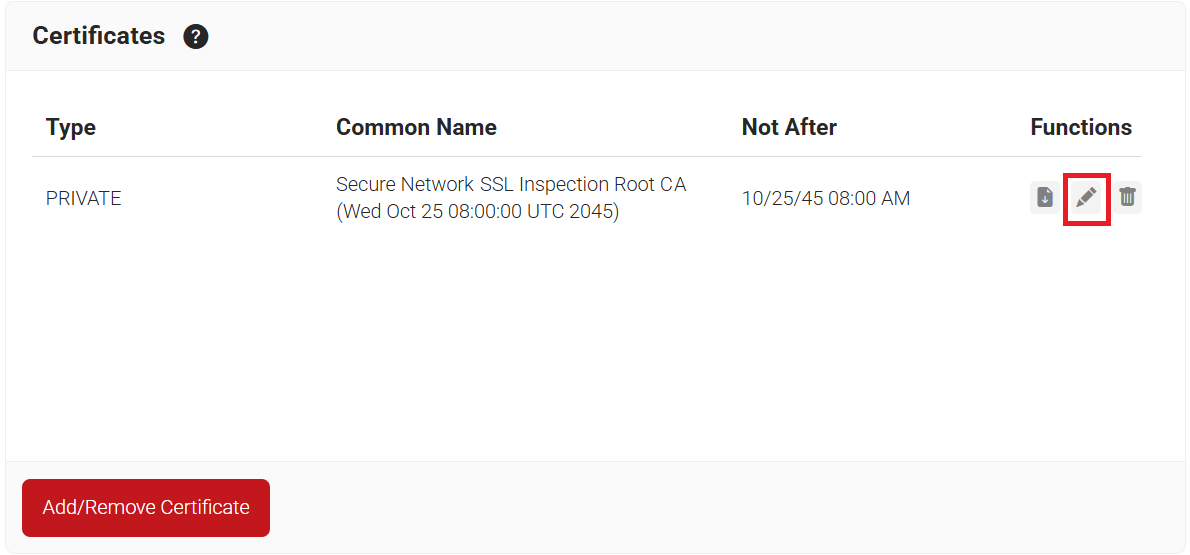
- In the Additional Certificate Operations section, select the Use Certificate for SSL Inspection and Install in Firefox Certificate Store checkboxes.
- Click Update.
- Scroll to the bottom of the Profile edit screen and click Update.
- Click Re-publish on the network profile that you just edited to push your recent changes.
Lastly, we need to download our Root and Intermediate CAs that have been generated with this Network Profile, so we can upload them to Palo Alto for VPN Authentication.
- Navigate to the Dynamic PKI section and select Certificate Authorities.
- Locate the Root CA that is associated with the Network Profile you just created.
- It should be named “Name of Network Profile” Root CA.
- Click Download.
- Locate the Intermediate CA that is associated with the Network Profile you just created.
- It should be named “Name of Network Profile” Intermediate CA
- Click Download.
Distribute Certificates to End Users
One of the reasons that the SecureW2 solution has been adopted so widely for network authentication is that it offers a platform that can easily enroll and configure both BYOD and Managed Devices. Below highlights the solutions we provide to enroll each set of devices.
BYOD Self-Service Enrollment and Configuration
The most common way we see this done is by getting the landing page URL generated for SSL Inspection and sending it to end users via email. The SecureW2 landing page takes only a few clicks for end users and includes instructions, so all MSP/Admin needs to do is send them the URL.
To get the URL:
- Navigate to Device Onboarding > Profiles.
- Click Open landing page on the Network Profile we just created using the Getting Started Wizard (From Getting Started section with Wi-Fi and VPN), and it will take you to the landing page.
- Take this URL and distribute it to your users.
- Most customers ask their users to do this at home or where they have existing network access.
- You can also do this by creating an Open SSID and redirecting users to the landing page. You can learn more about this by reading some of our integration guides on our Wi-Fi Solutions Page.
Managed Devices Certificate Auto-Enrollment and Configuration
The best way to configure your Managed Devices for certificate-based network authentication is a combination of:
- Using SecureW2’s SCEP/WSTEP Managed Device Gateway APIs so our devices can automatically enroll themselves for certificates.
- Pushing network settings configurations offered natively in your MDM so our devices are configured to use the certificates for VPN and SSLI.
To learn more, visit our Managed Devices page.
Configuring Palo Alto for SSL Decryption
Now that we’ve configured everything on the SecureW2 side, we need to configure our Palo Alto Firewall to use the SecureW2 certificates for SSL Inspection and VPN Authentication.
Import Intermediate CA for SSL Decryption on Palo Alto
- Navigate to Device > Certificate Management > Certificates.
- Click Import to select the certificate and private key to be used for SSL decryption.
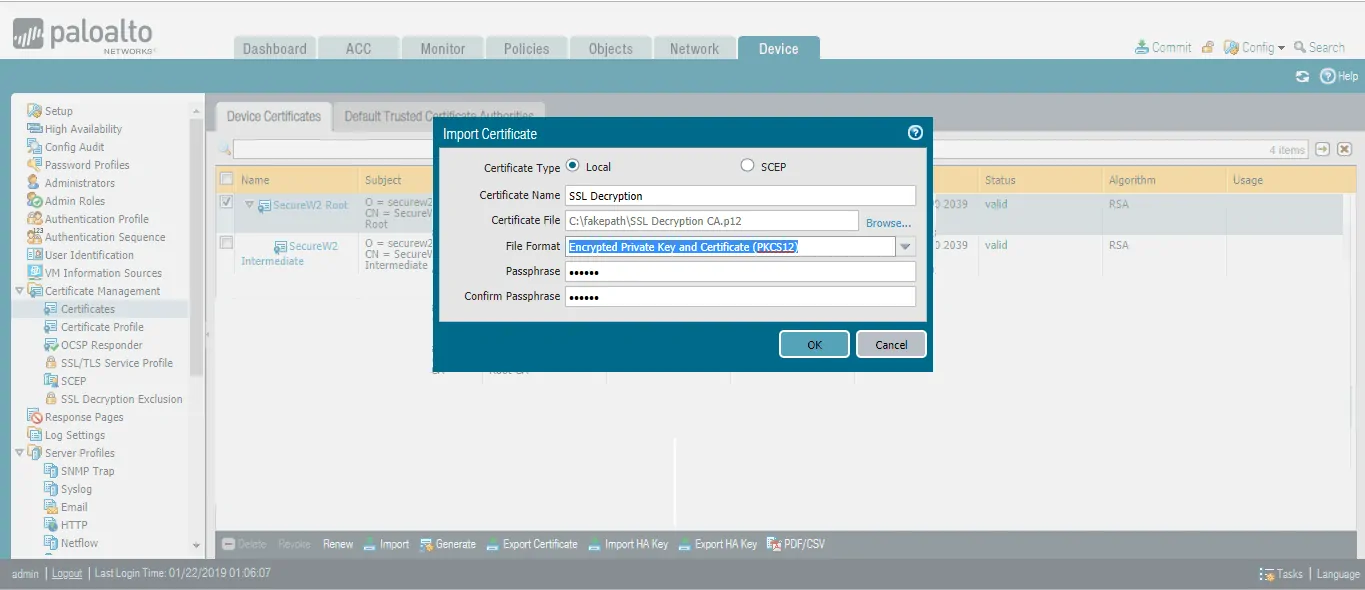
- Click OK to import the CA.
- Click on the imported CA.
- Select the Forward Trust Certificate and Forward Untrust Certificate options.
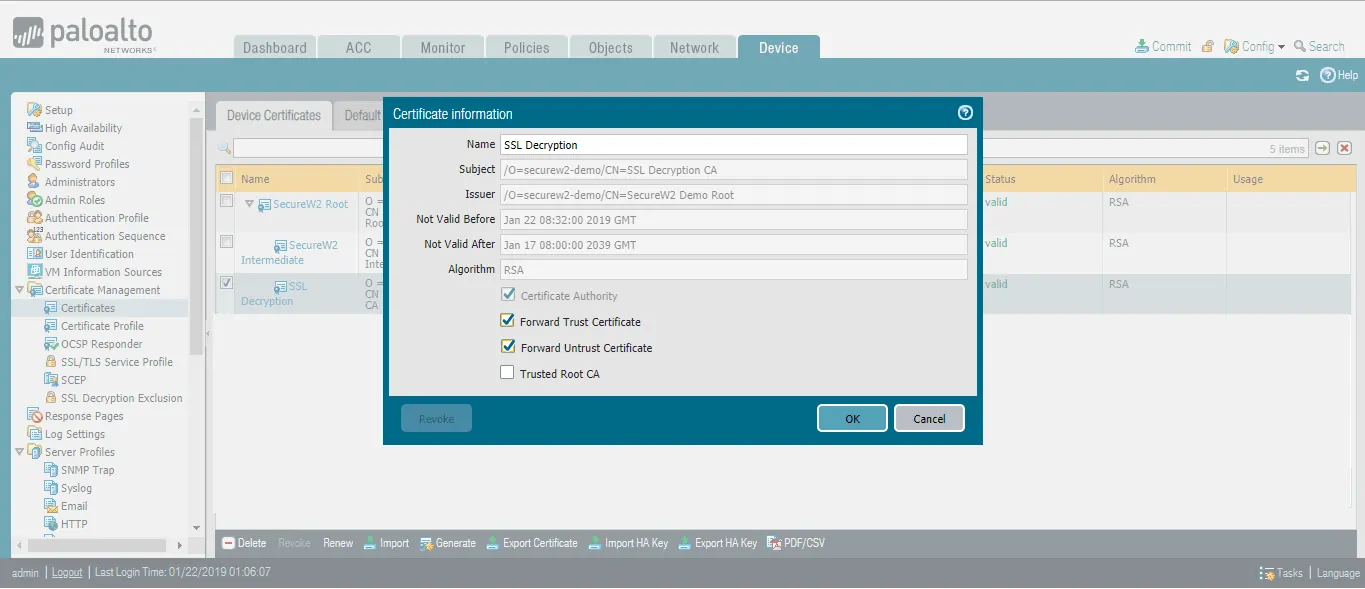
- Click Commit to commit the changes.
Creating Policies for SSL Decryption in Palo Alto
- Navigate to Policies > Decryption.
- Click Add to create a new SSL Decryption Policy.
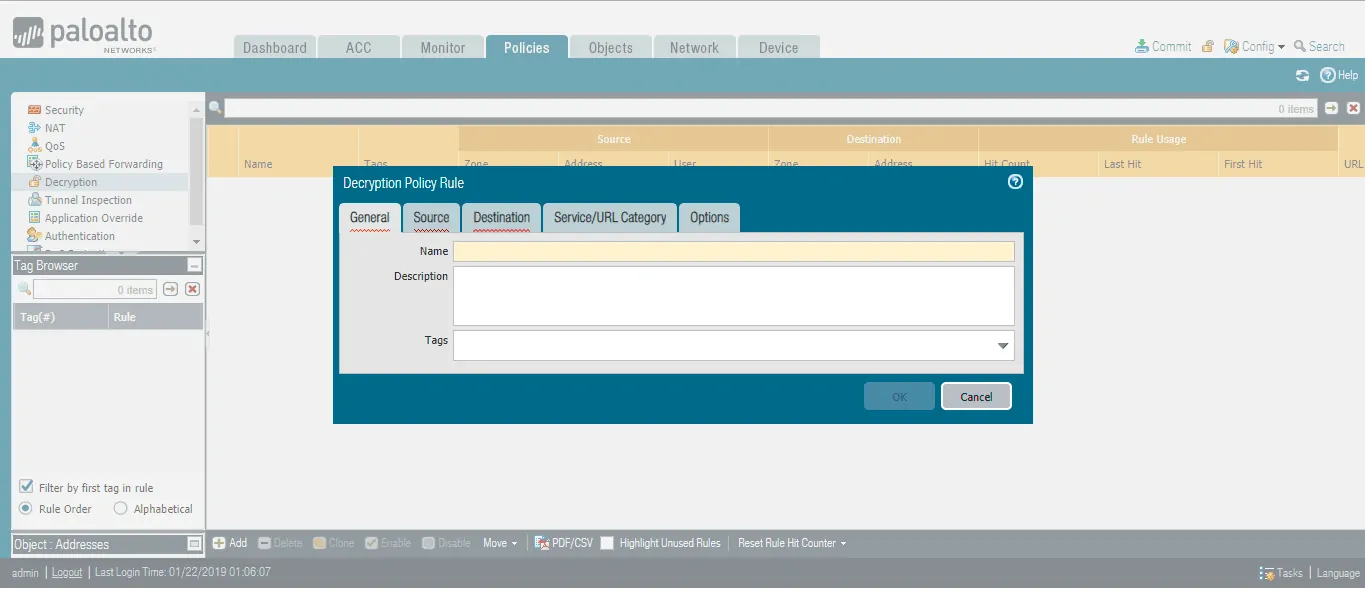
- In the General tab, provide the Name of the Policy.
- Click the Source tab.
- Specify the source zone/address to which this policy is applied.
- Click the Destination tab.
- Specify the source zone/address to which this policy is applied.
- Click the Options tab.
- Select Action as Decrypt.
- Select Type as SSL Forward Proxy.
- Optional (Create Decryption Profile)
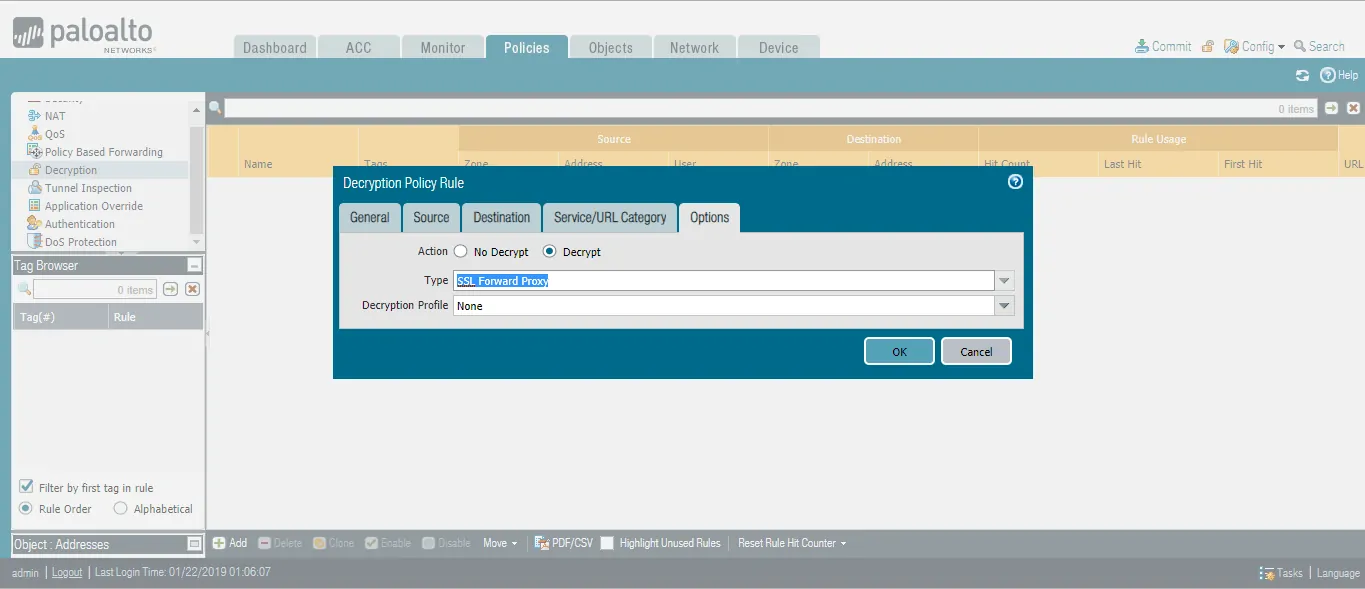
- Click OK to save the changes.
- Click Commit to commit the changes.
Using Enrolled Certificates for VPN Authentication on Palo Alto
Now we need to configure our Firewall to use our SecureW2 certificates for client authentication for an IPSEC VPN.
Prerequisites
- Tunnel and Physical Interfaces have been configured on the Palo Alto Firewall.
- The Server Certificate for the Palo Alto VPN server has been created and updated on the Firewall.
Import VPN Intermediate and Root CAs to Palo Alto
- Navigate to Device > Certificate Management -> Certificates.
- Click Import.
- Upload both the Root and Intermediate CAs that we generated and downloaded in the Getting Started for Wi-Fi and VPN Section.
- Navigate to Devices > Certificate Management > Certificate Profile.
- Enter the name of the Certificate Profile.
- Click the Username Field drop-down list to select the certificate attribute to fetch the username.
- Under CA Certificates
- Click Add and select both Root and Intermediate CA certificates imported.
- Click CRL to set up the Firewall to download CRL files.
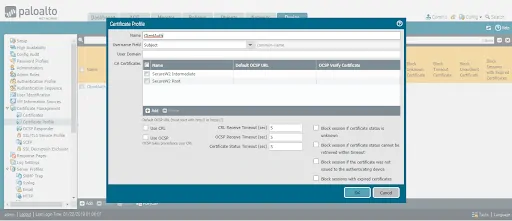
- Click OK to save the changes.
- Click Commit to commit the changes.
Set Up GlobalProtect Gateway for Remote Clients
- Navigate to Network > GlobalProtect >Gateways.
- Click Add to create a new Gateway.
- Under the General tab, provide the name and configure the Network Settings.
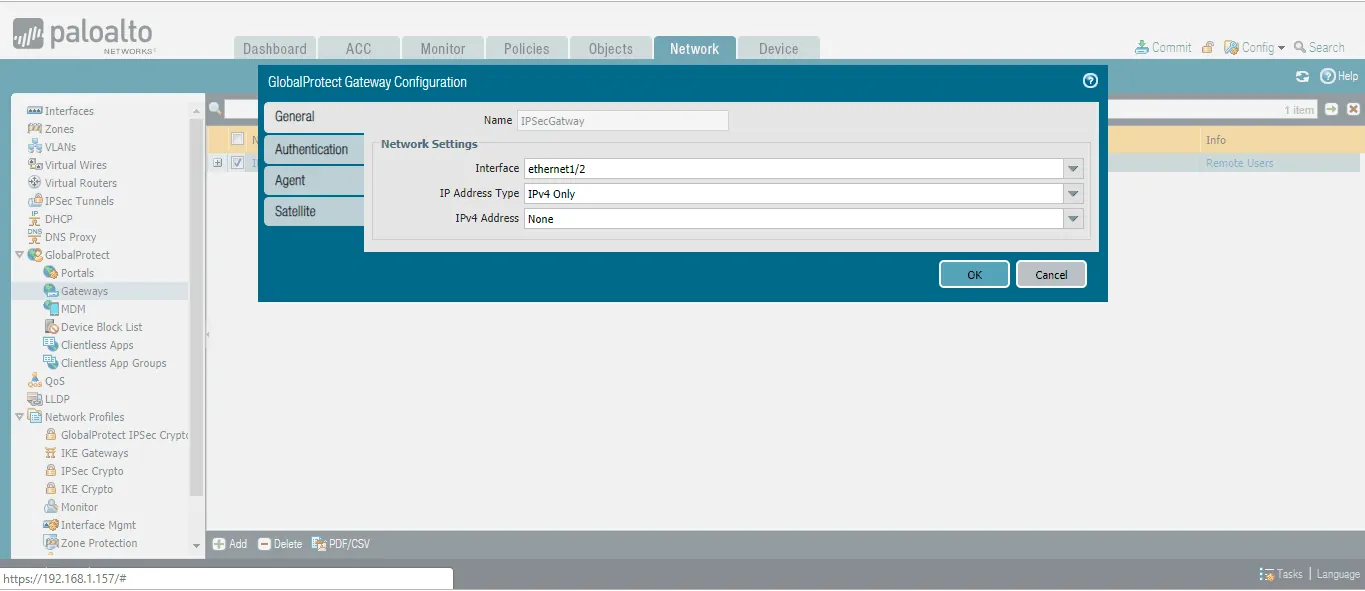
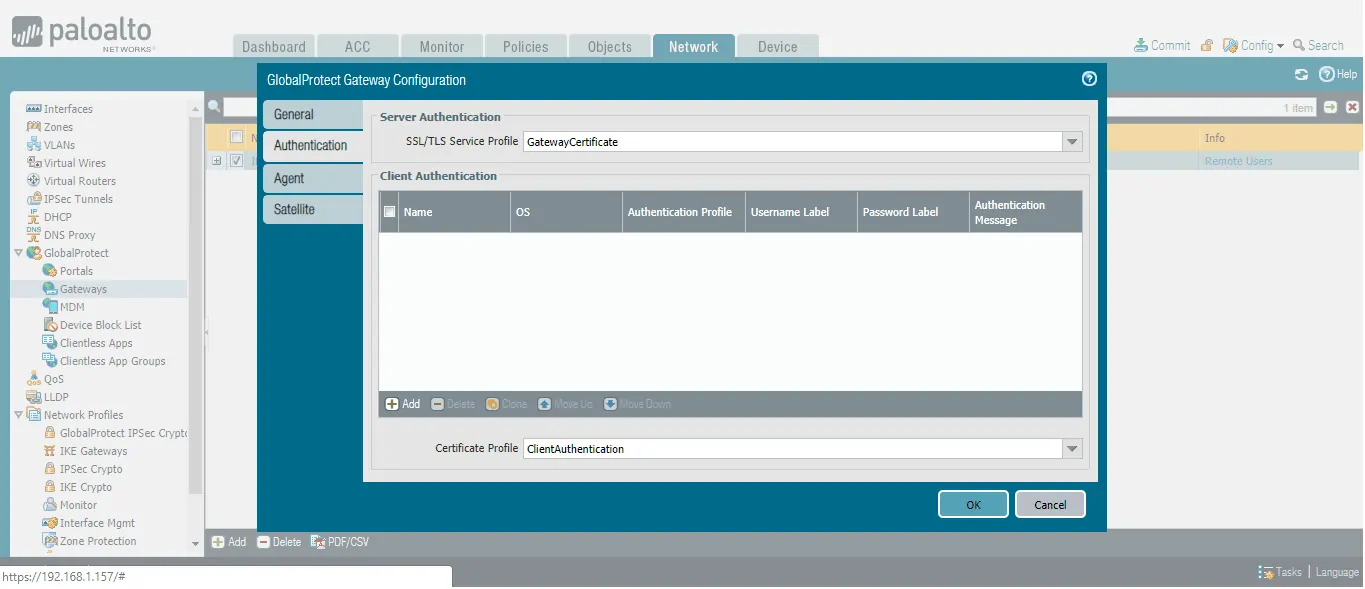
- Click the Authentication tab.
- Under SSL/TLS Service, select Firewall Certificate.
- Under Certificate Profile, select Certificate Profile.
- Click the Agent tab.
- Check to enable Tunnel Mode.
- Select the Tunnel Interface.
- Check to Enable IPSec.
- Click Ok to save the Gateway Configuration.
- Click Commit to commit the changes.
Configure GlobalProtect Portal for VPN
- Navigate to Network > GlobalProtect >Portals.
- Click Add to create a new Portal.
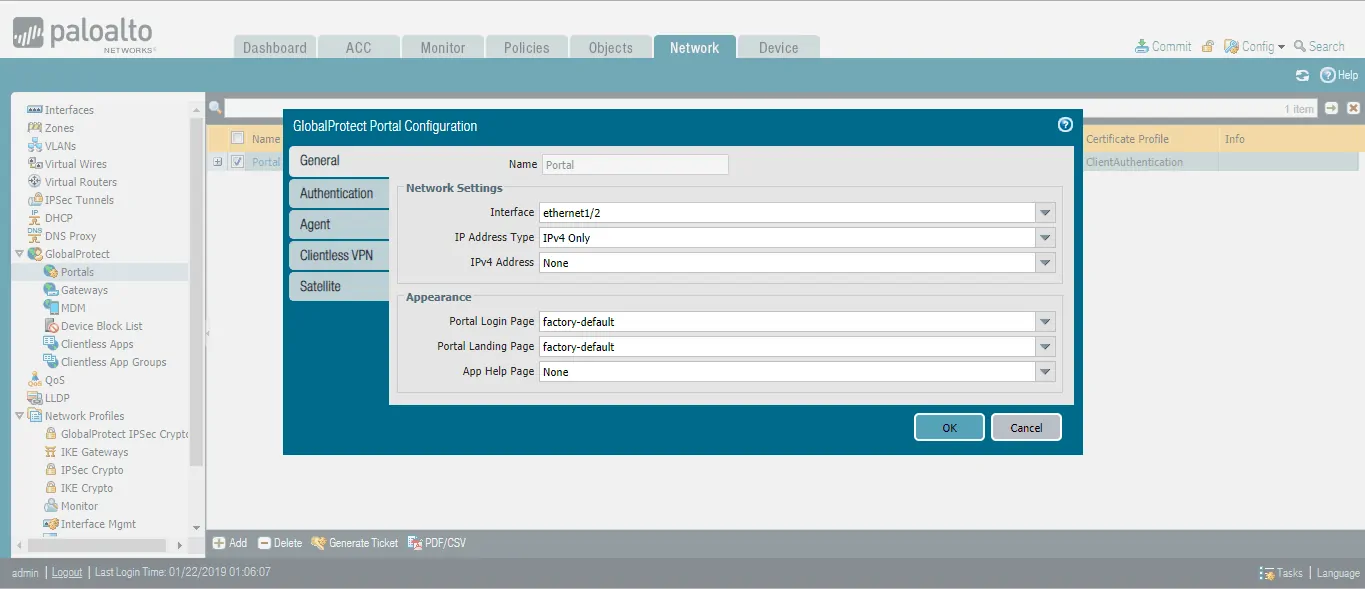
- Under the General tab.
- Provide a Name.
- Configure the Network Settings
- Click the Authentication tab.
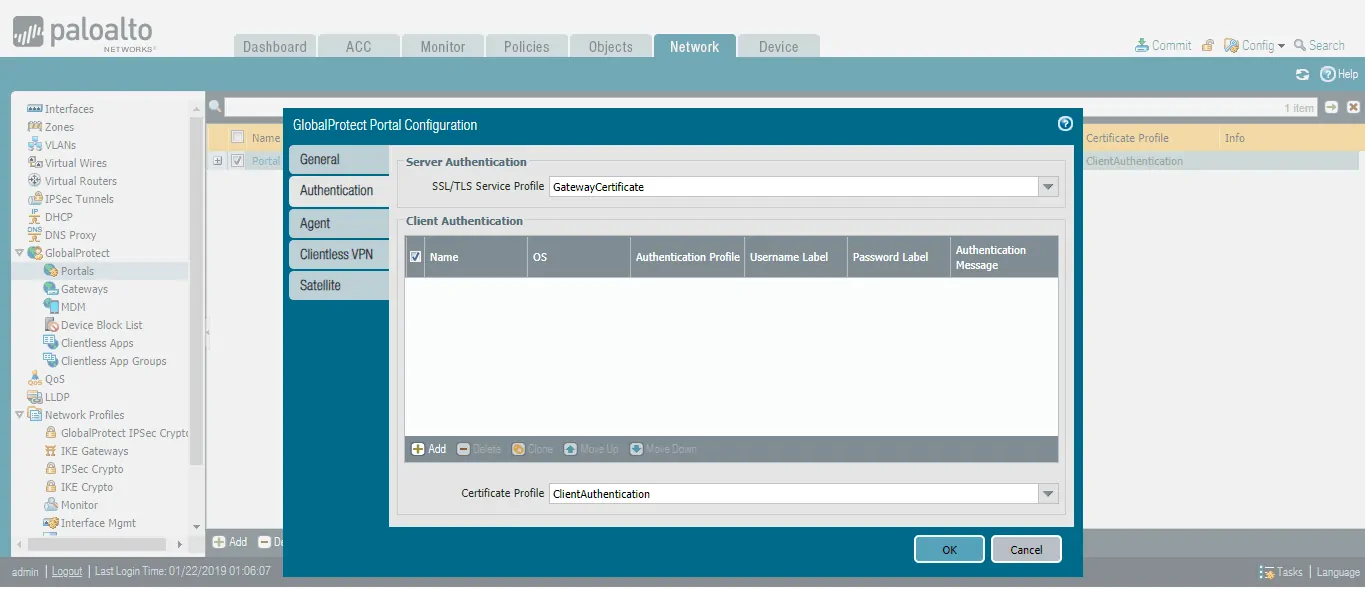
- (Here we are using the same interface and authentication settings for clients to connect to Gateway as well as Portal)
- Under SSL/TLS Service, select Firewall Certificate.
- Under Certificate Profile, select Certificate Profile.
- Click the Agent tab.
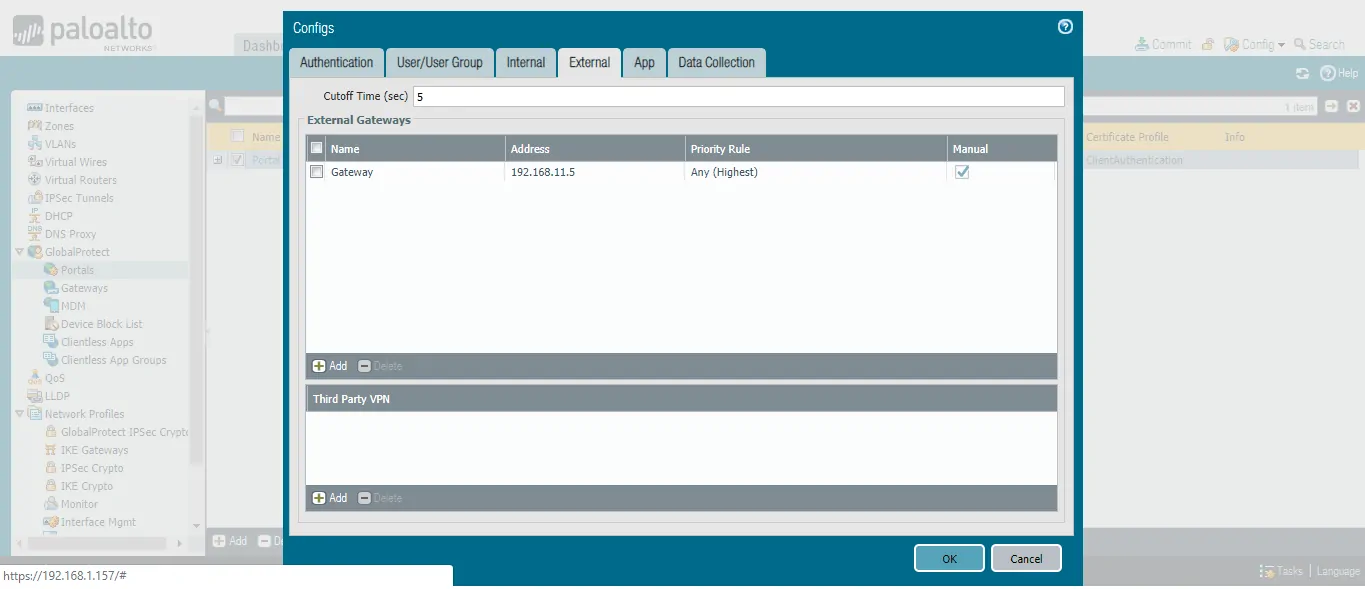
- Click Add.
- Provide a Name.
- Click User/UserGroup to map users/OS that can access this gateway. For this guide, we have used Any to allow access to everyone.
- Click the External tab and add the GlobalProtect Gateway we previously created.
- Click OK.
- Save the Portal Settings.
- Click Commit to commit the changes.
Configuring RADIUS Server in Palo Alto
To configure the RADIUS in Palo Alto, perform the following steps:
- Log in to Palo Alto.
- Under the Devices tab, navigate to Server Profiles > RADIUS.
- Click Add.
- Add the IP Address of the RADIUS Server, Shared Secret, and Port of the primary and secondary server.
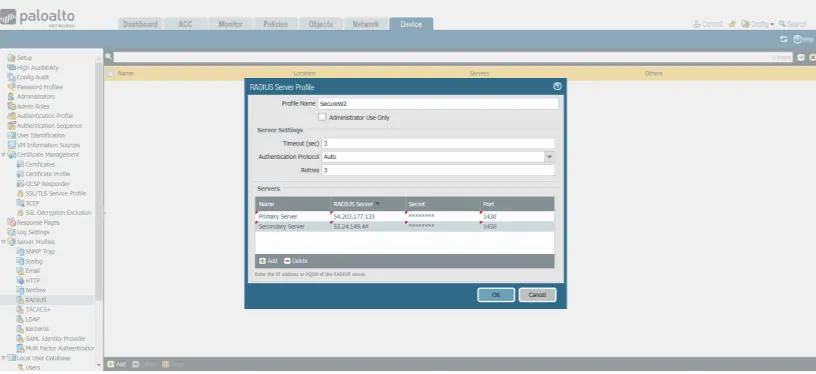
- Click OK.
Secure Authentication with Azure MFA
Any security professional will agree that the more levels of authentication you require, the more secure your network will be. SecureW2 easily integrates with Azure to provide dynamic cloud authentication solutions that are protected by Palo Alto.
In the Azure MFA settings, you’re required to update the RADIUS Authentication settings to bind to the same ports as Palo Alto Networks. The Management IP of the Palo Alto Networks firewall should be set to the IP address that will authenticate with the Azure MFA server.
This solution is highly effective because it does not rely solely on certificates, making it compatible with more vendors. If a vendor can only support biometrics or credentials, they can still experience the security of MFA.
You can also configure conditional access to protect resources from being viewed by just anyone. If a resource is secured, conditions can be set that must be met to view it. Lastly, there is no requirement for a RADIUS server. One of RADIUS’s strongest aspects is the logs generated when users authenticate, and the Palo Alto-Azure solution can still generate accounting logs similar to RADIUS to track network traffic.
Ready to enhance your security? SecureW2 offers affordable options for organizations of all sizes. Check out our pricing page to learn more.