Configure EAP-TLS Authentication with a Cisco ISE RADIUS
Introduction
The fundamental function of any secure wireless network is to authenticate network users in a protected and efficient environment. SecureW2 provides all the necessary tools to boost your RADIUS with certificate-based 802.1x authentication. Our PKI services are vendor neutral and boast a streamlined configuration process. All the necessary elements are provided by SecureW2 (CAs, certificate management software, HSM-protected PKI, Cloud RADIUS, and more) to get your users authenticating with certificates.
Prefer a Video? Contact us today for access to all our Video documentation!
The advantages of certificate-based authentication become quickly apparent after users complete the simple onboarding software. By eliminating the need for credentials, users no longer grapple with password change policies or cumbersome authentication processes.
Managed devices can also be easily outfitted with certificates using SCEP Gateway to distribute with no end user interaction. Additionally, applying server certificate validation guarantees that users won’t fall victim to a Man-In-The-Middle attack.
The improvements to your networks security and user experience begins after upgrading to certificate-based authentication with your Cisco ISE RADIUS.
An overview of the configuration process is as follows:
- Configuring SecureW2 PKI Services
- Configuring and managing a PKI is difficult. This is why we designed our PKI Services to be completely turnkey. Everything that’s required for EAP-TLS (Certificate Authorities, CRL, Management Software, etc.) is created using our simple Getting Started Wizard.
- Configuring the RADIUS Server
- Integrating SecureW2 PKI Services with a RADIUS Server
- Our PKI services integrate seamlessly with all major RADIUS servers. We can work with your existing infrastructure to make implementation simple and painless. No RADIUS infrastructure? No problem! SecureW2 comes built-in with our Cloud RADIUS. Click here to read more about our RADIUS Solutions.
- Integrating SecureW2 PKI Services with a RADIUS Server
- Identity Provider Integration
- SecureW2 Integrates with every major LDAP and SAML IDP to authenticate users and enroll them for certificates. Below are some of our integration guides detailing how SecureW2 integrates with Identity Providers:
- Getting Users Enrolled for Certificates
- Set up an Onboarding SSID for BYOD Self-Service Certificate Enrollment
- Users can easily enroll themselves for certificates and get their devices configured for secure network access using the JoinNow Suite; our Best-In-Class Onboarding Software. They can use it to set up their devices from the comfort of their own home, or you can configure an Open SSID to redirect users to the JoinNow Onboarding Solution to ensure the enrollment process goes off without a hitch.
- Using Gateway APIs to Auto-Enroll Managed Devices for Certificates
- Rather than manually enrolling every managed device for a certificate, use our Managed Device Gateway APIs to automatically enroll all your managed devices for machine and/or user certificates using any major MDM software.
- Set up an Onboarding SSID for BYOD Self-Service Certificate Enrollment
Integrating the SecureW2 PKI with Cisco ISE
Our PKI Services were designed to be as turnkey as possible. In a matter of minutes, you can begin testing the #1 rated Certificate Onboarding system in the industry.
To complete this setup, you need to have already configured:
- A Cisco ISE RADIUS Server
- A SecureW2 Network Profile
- An Identity Provider
We need to setup an Identity Provider in ISE similar to how we had set it up in SecureW2. By this, we mean providing information about our IDP (the LDAP server in this case), such as the IP address, administrator credentials, and port number into Cisco ISE. For detailed information on how Active Directory integrates with Cisco ISE, please refer to Cisco’s official documentation.
Adding the SecureW2 Root and Intermediate CAs to the ISE Trust List
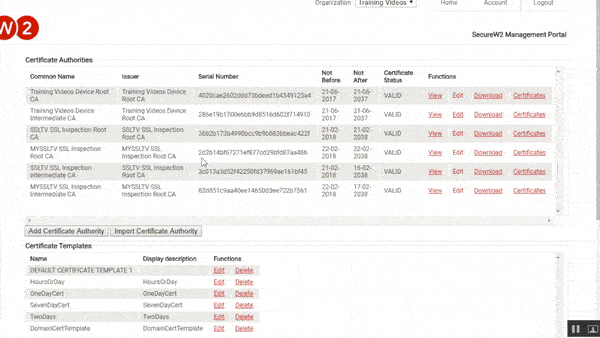
- Beginning in the SecureW2 Management portal, in the PKI Management Section, click Certificate Authorities
- Download the root and the intermediate certificate that corresponds with your network profile from the Certificate Authorities list
- Once the certificates are downloaded, navigate to the Cisco ISE page
- Click Administration on the menu bar and click Certificates
- From there, click Trusted Certificates under Certificate Management
- Click Import and add the root and intermediate certificates
Configuring ISE for EAP-TLS Certificate-Based Authentication
After setting up and integrating the SecureW2 PKI with ISE, you need to configure your RADIUS server to authenticate your devices via EAP-TLS.
Adding the Identity Provider
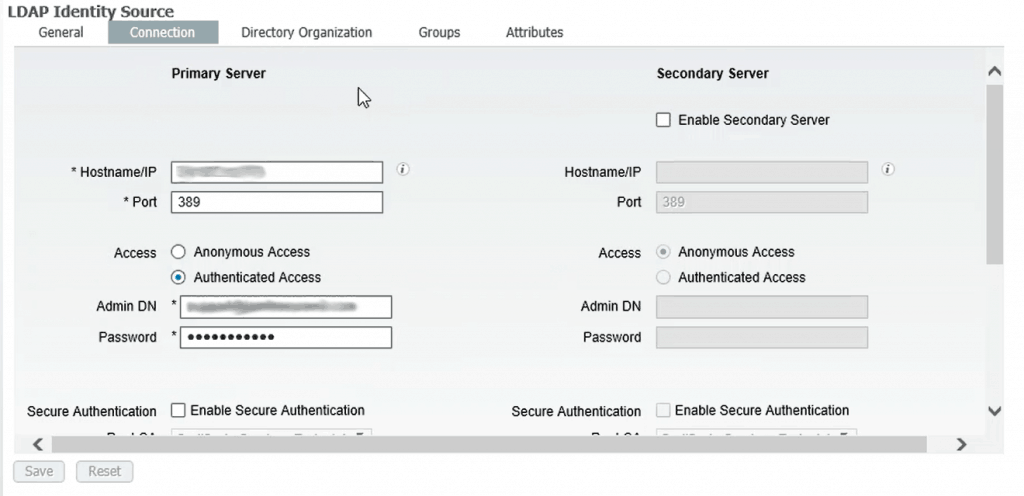
- Go to Administration on the menu bar and under Identity Management, click External Identity Sources
- Create a new Identity Source within the LDAP folder
- Under General, enter a Name, Description, and set the Schema as Active Directory
- Under Connection, enter the Server’s IP address under Hostname/IP, 389 for the Port, select Authenticated Access, and input the server’s credentials under Admin DN and Password
Configuring the EAP-TLS Authentication Policy
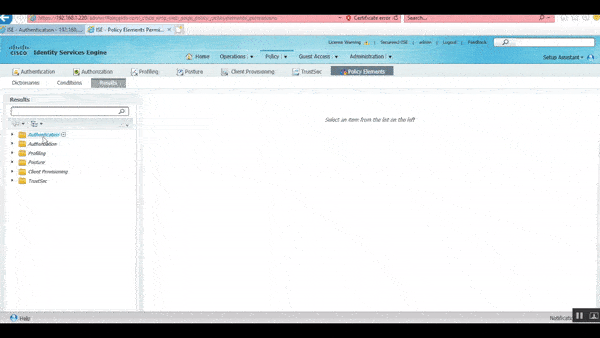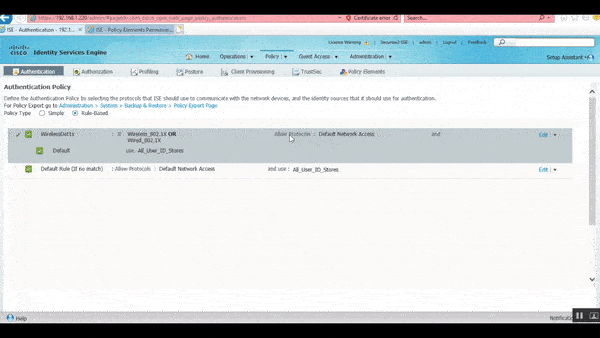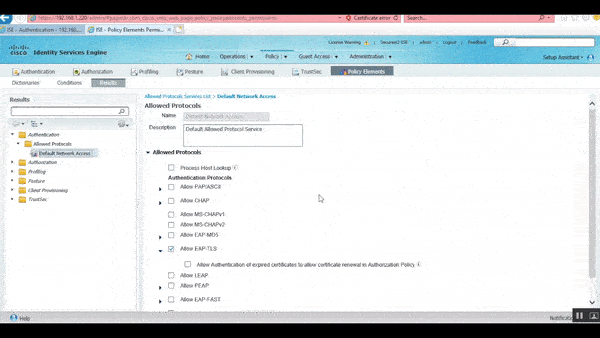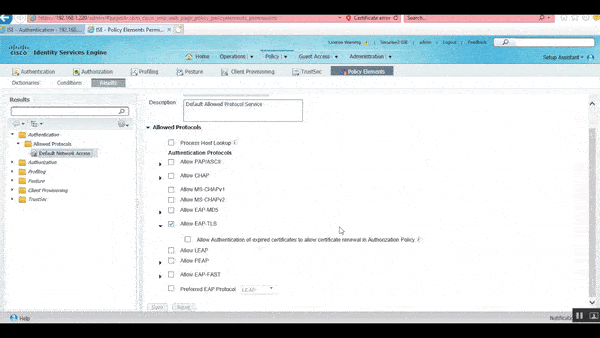
- Start by navigating to Policy on the menu bar and clicking Authentication
- By default, you will have a set of authentication policies
- Delete the set of default policies
- Create a new policy and name it
- In this guide, the policy is named “WirelessDot1x“
- Click the plus (+) symbol next to the If dialog box
- Here you can add the Attributes that you would want for an authentication policy
- Ensure that under Condition Name, both Wireless_802.1X and Wired_802.1X are added and that the dialog box with the options AND / OR is set to OR
- The Allow Protocols: option should be set to Default Network Access
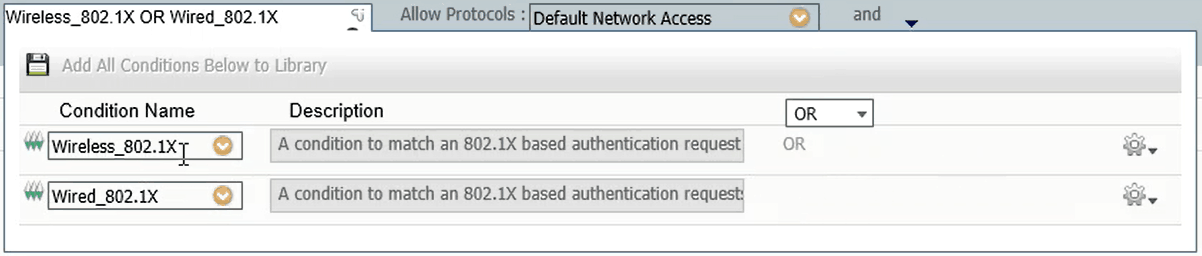
The condition must be set to ‘OR’ because ‘AND’ indicates that it must satisfy both the wireless and wired conditions. It should be set to ‘OR’ because it is not valid to do connection attempts always from wired and wireless devices.
After confirming that the Default Network Access is set, we need to figure out how it was calibrated. To find this:
- Go to the menu bar, and under the Results tab, click Policy
- In the drop-down menu that appears, open Conditions in a new tab
- On the left side, click the drop-down arrow next to Authentication and then the similar arrow next to Allowed Protocols
- From here, click Default Network Access
Configuring the EAP-TLS Authorization Policy
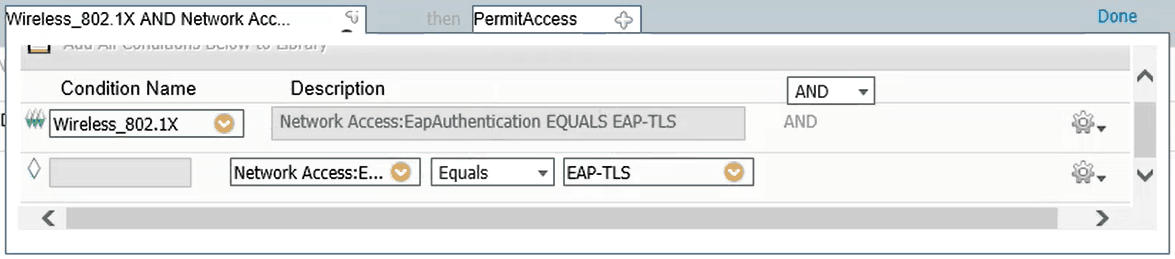
- Under the Policy dropdown menu, click Authorization and create a new rule
- For Rule Name, enter Wireless TLS
- The If condition should be set to Any
- For the next condition, click the (+) plus sign and confirm that it is configured as an AND condition
- The Condition Name should be Wireless 802.1X
- Click the settings symbol on the right side to create conditions so the Description reads Network Access:EAPAuthentication EQUALS EAP-TLS
- Set the Permissions to PermitAccess and click Done
Here is where you could setup an identity lookup by creating a couple more AND clauses and conditions. It would read along the lines of “users will be accepted only if they are set up for EAP-TLS, AND only if the user is from the Active Directory, AND only if the user from the Active Directory is marked ‘ACTIVE’.
PermitAccess tells ISE to send an ACCESS_ACCEPT response. You can see how it’s configured by doing the following:
- Navigate to the Cisco ISE page we had opened for the Authentication Policy and click Conditions on the left side
- Click Authorization and then Compound Conditions
- Under Name, click Wireless_802.1X
- Based on the condition, we can see that it is requiring EAP Authentication for a secured connection
- Next to Conditions, click Results
- From here, click Authorization, then Authorization Profiles, and finally click PermitAccess
- Here you can see that the Access Type is ACCESS_ACCEPT
Adding the RADIUS Server Certificate
If you go back to the SecureW2 Management Portal, you can click Edit by the profile we just evaluated, and you’ll see that a RADIUS server certificate has not been added. Using a RADIUS server certificate is integral to preventing MITM attacks. To add a RADIUS server certificate:
- Navigate to the Cisco ISE page and click Certificates in the dropdown menu for Administration
- Click System Certificates, and click Import to import the server certificate
- Select the certificate by clicking the small box next to it and then clicking Edit above
- Select what you want to use the certificate for under Usage, and then click EAP Authentication
- Navigate back to the SecureW2 Management Portal and upload the certificate in the Certificates section
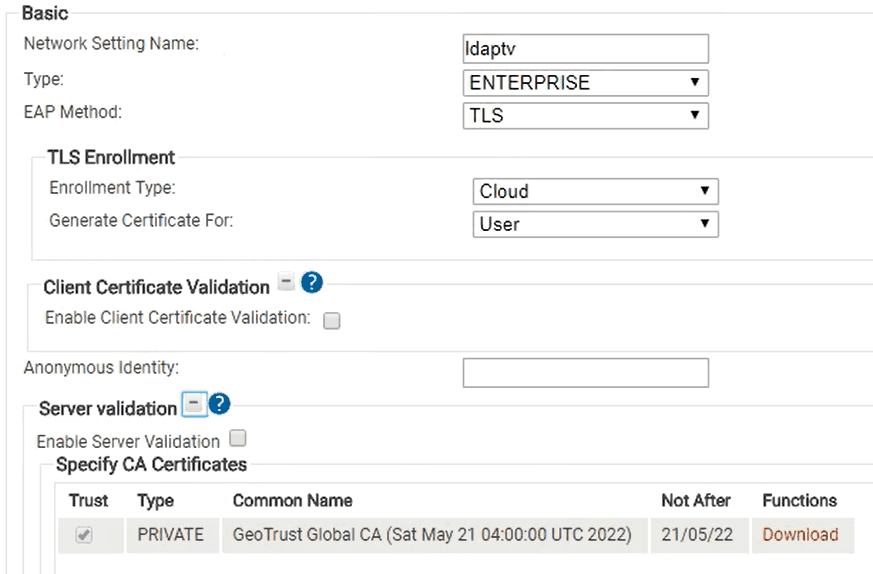
- Under Network Settings, click Edit
- This will take you to a page where you can enable server validation
- Check Enable Server Certificate Validation
- Check the Trust Box next to the certificate
- Write in the domain name the certificate was issued in Connect to these server names
Concluding Thoughts
Now, the wireless network is configured for WPA2-Enterprise with EAP-TLS authentication. Network users will only need to complete the onboarding process once for uninterrupted and secure Internet use. Network administrators will see their IT help desk tickets reduced and if a problem should arise, they can easily diagnose it. The benefits of using certificate-based authentication include eliminating password-related disconnects and MITM attacks, tying users and devices to network connections, improving network performance, and many more. However, many wrongfully assume the level of difficulty in deploying the EAP-TLS protocol. Historically, setting up this type of network would have taken weeks, but with SecureW2, setting up certificate-based authentication with a Cisco ISE RADIUS can take just a few hours. It’s also an incredibly cost effective solution, click here if you’d like to see our pricing.
Cisco and Cisco ISE are either registered trademarks or trademarks of Cisco Systems Inc in the United States and/or other countries. Other trademarks, logos and service marks used in this site are the property of SecureW2 or other third parties.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing