Introduction
The value of certificate-based networks far outweigh that of credential-based networks. Passwords are no longer secure enough for organizations to protect their network and data. Password-related disconnects can also be a strain on the IT department. Many organizations are hesitant to employ digital certificates because of perceived difficulty, but that’s simply not the case.
Integrating SecureW2’s Cloud PKI with Radiator will simplify not only the certificate enrollment process, but device onboarding as well. Our cloud-based software can easily integrate within your current Radiator infrastructure so you won’t need to drastically change anything. Our robust managed PKI services, provide the ability to generate Root and Intermediate CA’s, industry-exclusive certificate management technology, auto-generated Base and Delta CRLs, and much more.
The guide below showcases how you can set up a Radiator Software RADIUS Server, with SecureW2’s PKI services to deploy certificate-based authentication. If you have any questions, please don’t hesitate to contact us here.
Integration Process Overview
- Configure SecureW2 PKI Services
- Our PKI services are completely turnkey because all the necessary tools for PKI implementation are setup through our Getting Started wizard.
- Integrate SecureW2’s PKI with Radiator
- Our PKI services can adapt to any major RADIUS vendor and can be implemented without needing to change your current infrastructure.
- Configure the Identity Provider
- SecureW2 can integrate with any major IDP. Once setup, devices will be able to self-enroll for certificates which are linked to the user’s identity. These certificates cannot be removed and will expire on a pre-determined date.
- Enrolling User Devices for Certificates
- Set up Onboarding SSID for BYOD
- Our JoinNow Suite allows end users to quickly and easily configure their devices to automatically authenticate and enroll for a certificate. After a few button clicks, their device will be set up with a certificate and gain access to the network.
- Use Gateway APIs for Managed Devices
- Using SecureW2’s Management Portal, Gateway APIs can be setup to automate the certificate enrollment process for all managed devices. You no longer need to manually enroll every managed device.
- Set up Onboarding SSID for BYOD
Creating a Network Profile
Start by logging in to the SecureW2 Management Portal and creating a Network profile, and then
download the Root and Intermediate CA and the links to the Certificate Revocation List (CRL)
To do so, perform the following steps:
- Log in to the JoinNow Management Portal.
- Navigate to Device Onboarding > Getting Started.,
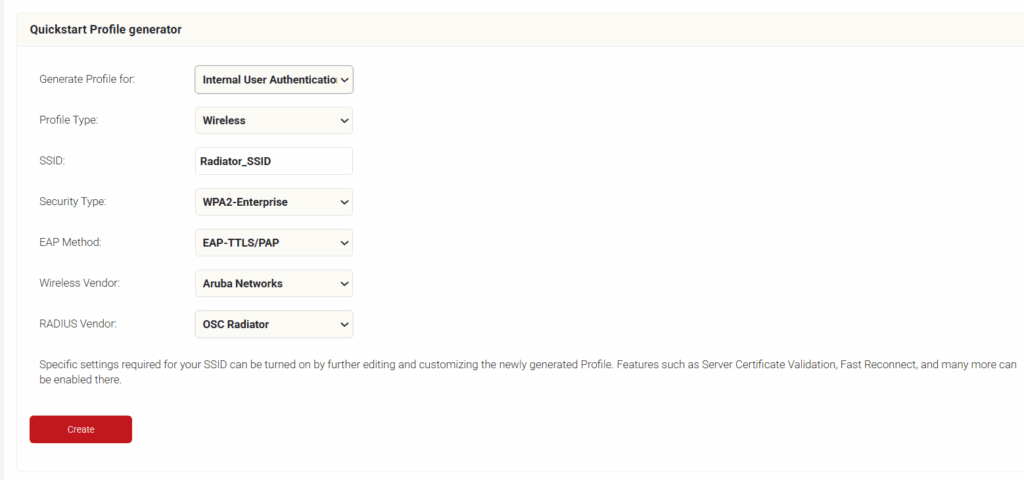
- On the Quickstart Network Profile generator page, from the Profile Type drop-down list, select Wireless.
- In the SSID field, type the name of a profile.
- From the Security Type drop-down list, select WPA2-Enterprise.
- From the EAP Method drop-down list, select EAP-TLS.
- From the Policy drop-down field, retain DEFAULT.
- From the Wireless Vendor drop-down list, select the required wireless controller vendor.
- From the RADIUS Vendor drop-down list, select a OSC Radiator vendor.
- Click Create and everything you need gets set up within 60-90 seconds.
Downloading the Root and Intermediate CAs and Links to the CRL
Download the Root and Intermediate CAs and the links to the Certificate Revocation List (CRL) by
performing the following steps:
- Navigate to Dynamic PKI > Certificate Authorities.
- Download the Root and Intermediate CAs that correspond with the Network Profile created in the Creating a Network Profile section.
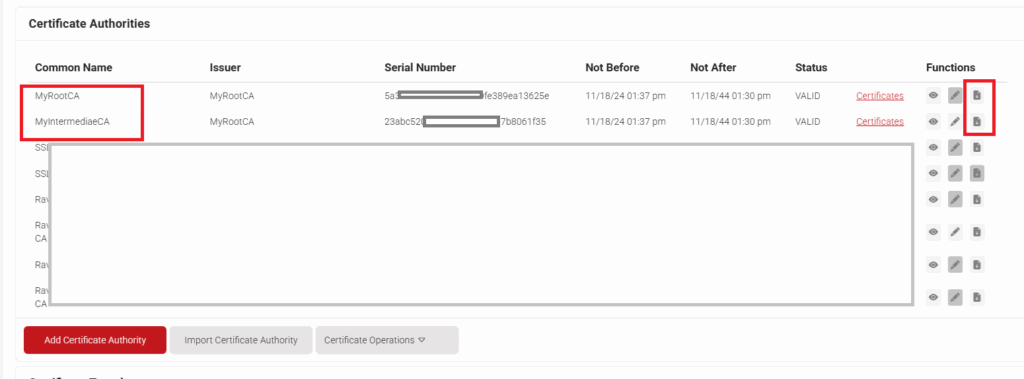
- Click View on the Intermediate CA and you will see a link to the Base and Delta CRL; copy both of the links and save them for later in the guide.
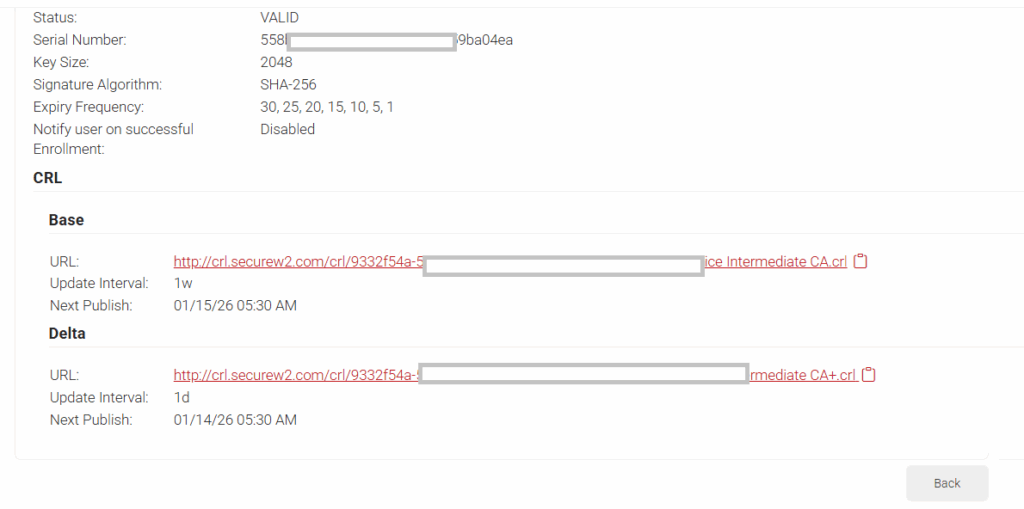
NOTE: Right-click the crl link and select Copy link URL or Copy link address to copy the crl from the JoinNow Management Portal properly.
Configuring Certificate Notifications
With SecureW2, you can configure email notifications to be sent to end users upon certificate
enrollment and pending expiration.
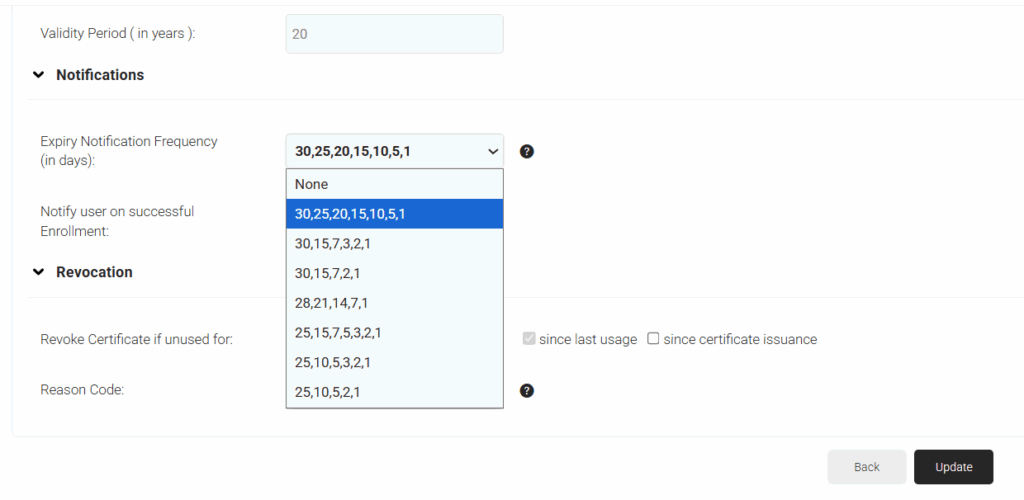
- Navigate to Dynamic PKI > Certificate Authorities and click Edit on your
organization’s Intermediate CA. - Here you can configure the intervals in which the certificate expiration notifications are
sent out. - Select the required frequency from, Expiry Notification Frequency (in days) drop-down list.
Configuring Radiator Software for EAP-TLS
To configure Radiator Software for EAP-TLS, perform the following steps:
- Install Radiator Software with the required Perl modules. The perl-LDAP module is
mandatory. - Create the following directory: /etc/radiator/certificates/
- In /etc/radiator/certificates/ create an empty file securew2.pem and insert the
downloaded Root and Intermediate certificates from SecureW2, into the securew2.pem
file. - Get your RADIUS server CA and upload it to the Network Profile to enable server certificate
validation. To do so, perform the following steps:- Navigate to Device Onboarding > Network Profiles.
- Click Edit on the Network Profile created earlier using Getting Started.
- Navigate to the Certificate section:
- Select Add/Remove certificates and upload your RADIUS server certificate.
- Scroll through the list until you find the uploaded certificate and select the checkbox.
- Click Update.
- Click Edit on your Network Settings.
- Check Enable Server Certificate Validation.
- Uncheck the DigiCert CA option.
- Check the CA (RADIUS Server CA) you just uploaded.
- Delete the *.securew2.com value from Connect to these server names.
- Add your RADIUS Server CA common name in Connect to these server names.
- Click Update.
- Now back in the Network Profile, delete the DigiCert CA from the Certificates section.
- Scroll down to the bottom and click Update.
Setting up Identity Lookup with Active Directory
Configure Radiator Software to perform an Identity lookup with Active Directory and check if the
user account is in disabled state. If the user account is in disabled state, the RADIUS
authentication will fail.
To do so, include the following configuration file in the radiator.conf file for this check.
NOTE: You can find a sample configuration file that contains the code discussed in this section
under Radiator Software installation location. The “securew2_configuration_example.cfg”
can be found in the goodies folder.
# LDAP settings
Host WIN-5CCF8CPJR8R.securew2-india-dev.com
Port 389
# Reuse existing LDAP connection
HoldServerConnection
# Service account
AuthDN securew2
AuthPassword ***********
# LDAP path and attributes
BaseDN CN=Users,DC=securew2-india-dev,DC=com
UsernameAttr userPrincipalName
# Match UsernameAttr with EAP-TLS CN or subjectAltName
SearchFilter (%0=%1)
# No password authentication
PasswordAttr
NoCheckPassword
# Additional LDAP attribute(s)
AuthAttrDef userAccountControl
# Check whether account is disabled and reject
# Ref: https://support.microsoft.com/en-gb/help/305144/how-to-use-theuseraccountcontrol-flags-to-manipulate-user-account-pro
PostSearchHook sub {\
# Get LDAP entry userAccountControl attribute\
# and check for ACCOUNTDISABLE (0x0002) flag\
my $uac = $_[4]->get_value('userAccountControl');\
if ($uac && ($uac & 2)) {\
# Reject authentication\
$_[3]->get_check->add_attr('Auth-Type','Account disabled');\
}\
}NOTE: This sample configuration is just an example and should not be directly copied for use in a
production environment.
Setting up Radiator Software to Return VLAN Attributes Based on LDAP Groups
Setting up Radiator to return different VLAN ID based on the user groups we need to have a
separate file (vlan-groups.txt) created in /etc/radiator. We can configure the VLAN Id’s for the
necessary AD groups.
NOTE: You can find a sample configuration file that contains the code discussed in this section
under Radiator Software installation. The “securew2_vlan_groups_example.txt” file can be
found in the goodies folder.
# Start of file vlan-groups.txt
#
## DEFAULT entries are evaluated from the top to the bottom with the first to
match
#
# Group ‘user_group1’ is mapped to VLAN 100
DEFAULT Group-Authorization=AD,Group="CN=testgroup1,CN=Users,DC=securew2-
india-dev,DC=com"
Tunnel-Type=1:VLAN,
Tunnel-Medium-Type=1:Ether_802,
Tunnel-Private-Group-ID=1:11
#
# Group ‘user_group2’ is mapped to VLAN 200
#DEFAULT Group-Authorization=AD,Group="CN=2ndgroup,CN=Users,DC=securew2-indiadev,DC=com"
# Tunnel-Type=1:VLAN,
# Tunnel-Medium-Type=1:Ether_802,
# Tunnel-Private-Group-ID=1:1
#
## Uncomment the following DEFAULT entry if access should be allowed
## when no authorisation group matches. This entry does not have any
## check items and therefore matches the rest of the users. No reply
## attributes are added here.
#DEFAULT
# End of fileThis file needs to be included in the radiator.conf
# VLAN group mappings
<AuthBy FILE>
Identifier Group-VLANs
# File to contain VLAN group mappings
Filename %D/vlan-groups.txt
# Do not try to authenticate
NoEAP
NoCheckPassword
</AuthBy FILE>Since the configuration now requires the group membership values to be given by AD in the LDAP
requests, the below configuration needs to be added to store and restore the user group details.
PostAuthHook sub {\
# Store LDAP user groups in EAP context\
if (${$_[2]} == $main::CHALLENGE) {\
my $int_vars = ${$_[0]}->{internal_vars};\
return unless $int_vars->{user_is_in_group};\
my $ctx = ${$_[0]}->{EAPContext};\
return unless $ctx;\
$ctx->{piv_user_groups} = $int_vars->{user_groups};\
$ctx->{piv_user_is_in_group} = $int_vars->{user_is_in_group};\
}\
# Restore LDAP user groups from EAP context\
elsif (${$_[2]} == $main::ACCEPT) {\
my $int_vars = ${$_[0]}->{internal_vars};\
my $ctx = ${$_[0]}->{EAPContext};\
return unless $ctx;\
# Full TLS handshake done\
if ($ctx->{eaptls_session_reuse_method} == 0) {\
$int_vars->{user_groups} = $ctx->{piv_user_groups};\
$int_vars->{user_is_in_group} = $ctx->{piv_user_is_in_group};\
# TLS session resumed\
}\
elsif ($ctx->{eaptls_session_reuse_method} == 1) {\
return 1;\
}\
}\
}Setting up the Certificate Revocation Lists in the RADIUS Server
Certificate Revocation List (CRL) is a file that contains a list of revoked certificates.
The following are the forms of CRLs:
- BaseCRL: A CRL that contains all non-expired revoked certificates.
- DeltaCRL: A CRL that contains all non-expired certificates that have been revoked since
the last base CRL was published.
The BaseCRLs are updated weekly and the DeltaCRLs are updated daily.
For testing purpose, we have set up an hourly cron for DeltaCRL and a daily cron for BaseCRL.
Set up a new directory crl in the following path:
/etc/radiator/certificates/
NOTE: Make sure your directory name has crl is in lower case.
Create a cron for getting the DeltaCRL using the CRL links you got earlier from the Management
Portal.
/etc/cron.hourly #vi delta.sh //creating a file called delta #!/bin/sh wget -O /etc/radiator/certificates/crl/delta.pem http://crl.securew2.com/crl/12345/Intermediate%20CA+.crl
NOTE: Right-click the crl link and select Copy link URL or Copy link address to copy the crl from
the SecureW2 Management Portal properly.
Save the file and run the following command:
chmod +x delta.sh
Similarly, do the same for the BaseCRL cron.daily.
/etc/cron.daily #vi base.sh //creating a file called base #!/bin/sh wget -O /etc/radiator/certificates/crl/base.pem http://crl.securew2.com/crl/12345/Intermediate%20CA.crl
NOTE: Right-click the crl link and select Copy link URL or Copy link address to copy the crl from
the SecureW2 Management Portal properly.
Save the file and run the following command:
chmod +x base.sh
After these files are created in the cron folder, update the radiator.conf file to include the following
checks for the base and delta CRLs.
#EAP-TLS CRL check EAPTLS_CRLCheck EAPTLS_CRLCheckUseDeltas EAPTLS_CRLFile %D/certificates/crl/*.pem
Concluding Thoughts
Now that SecureW2’s Cloud PKI solutions have been integrated with your Radiator, you will be able to deploy EAP-TLS authentication and safely onboard new users. The benefits of using certificate-based authentication include eliminating password-related disconnects and MITM attacks, tying users and devices to network connections, improving network performance, and many more. Deploying certificate-based solutions used to take weeks, but SecureW2’s software can help you get it done in just a few hours. Our solutions can adapt to any vendor and are very affordable, click here to check our pricing.