Introduction
SecureW2 provides a Cloud RADIUS solution, allowing Okta customers to implement 802.1x and certificate-based authentication.
When Cloud RADIUS is integrated with Okta, it can communicate with your directory and enforce user policies during authentication. It can dynamically reassign users to different VLANs based on their role changes or deny their access if their risk score is too high.
Below, we lay out how you can integrate Cloud RADIUS with your Okta Infrastructure.
Prerequisites
The following are the required prerequisites for setting up certificate issuance with Okta:
- An active subscription with JoinNow MultiOS with CloudConnector subscription.
- An active subscription with Okta along with Super Admin privileges.
The above mentioned privileges for Okta are for the API token method required for auto configuration. For Manual configuration, refer to the Integrating SecureW2 CloudRADIUS with Okta guide available in the JoinNow management portal.
Creating an API Token in Okta
Cloud RADIUS talks directly with Okta (no LDAP required) using an API. To create an API Token, perform the following steps:
- Log in to the Okta Portal.
- On the left pane, from the Security menu, select API.
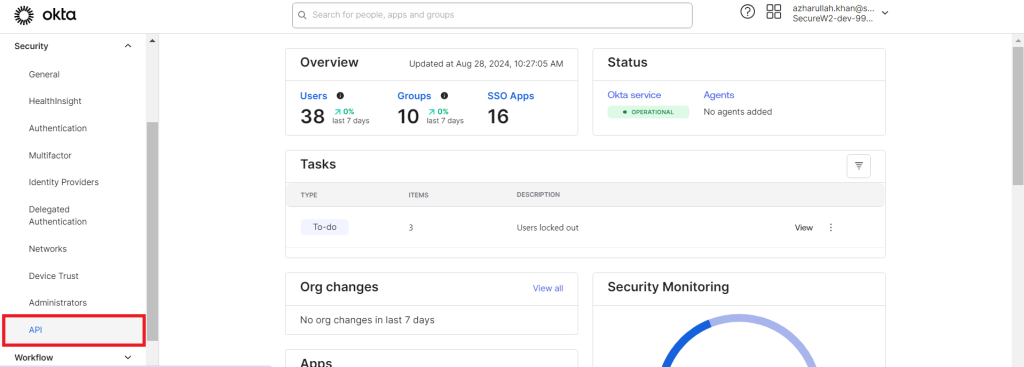
- Select the Tokens tab and on the displayed screen, click the Create token button.
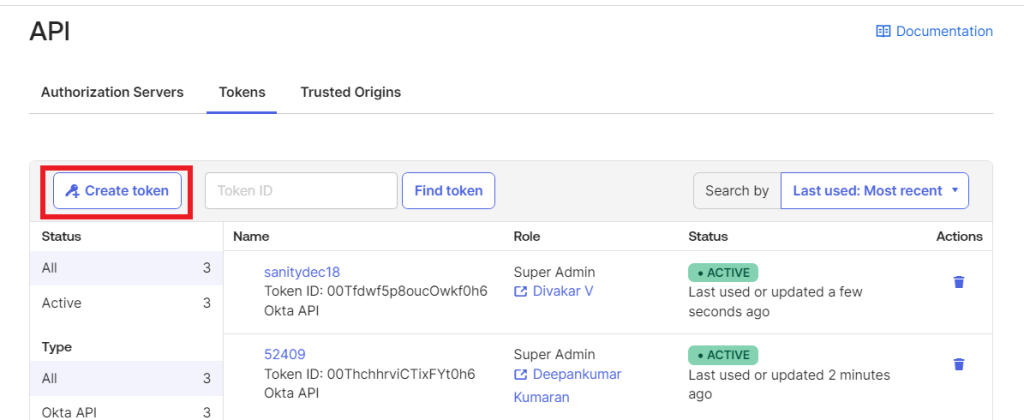
- In the Create token dialog box, enter a name for the token
- From the API calls made with this token must originate from drop-down, select the origin for the API tokens.
- Click Create token.
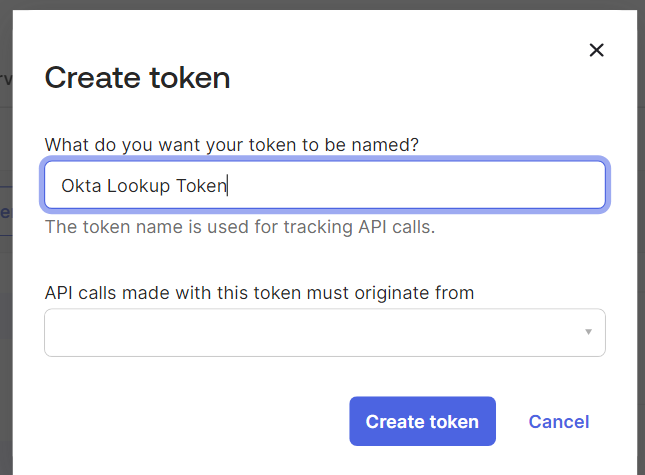
- On the displayed screen, copy the token value on your console.
NOTE: Ensure that you save the token value on your console.
Configuring Account Lookup in JoinNow Management Portal
After we’ve created the API Token in Okta, we can configure the policies in the JoinNow Management Portal. These policies validate the certificate each time a Wi-Fi connection request is made, along with the user’s account status in Okta. This ensures that network access is dynamically authorized based on the user’s real-time status in Okta.
Creating a Core Platform
To create an Identity Lookup Provider, perform the following steps:
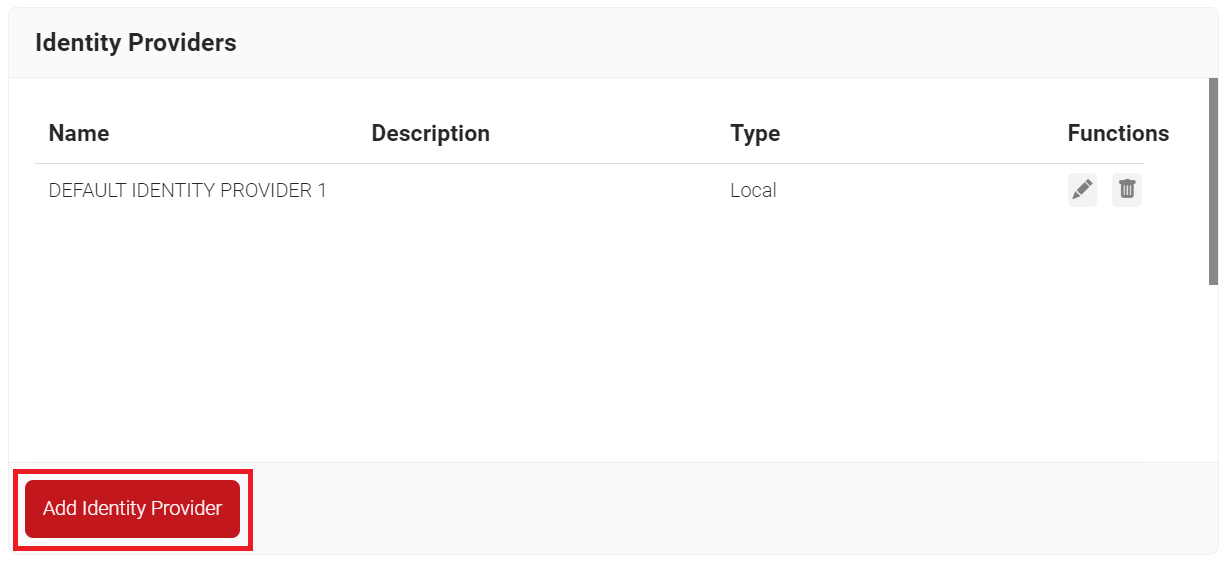
- Navigate to Integration Hubs > Core Platforms.
- Click Add Identity Provider.
- In the Basic section, enter the name of the IDP in the Name field.
- In the Description field, enter a suitable description for the IDP.
- From the Type drop-down list, select Okta Identity Lookup.
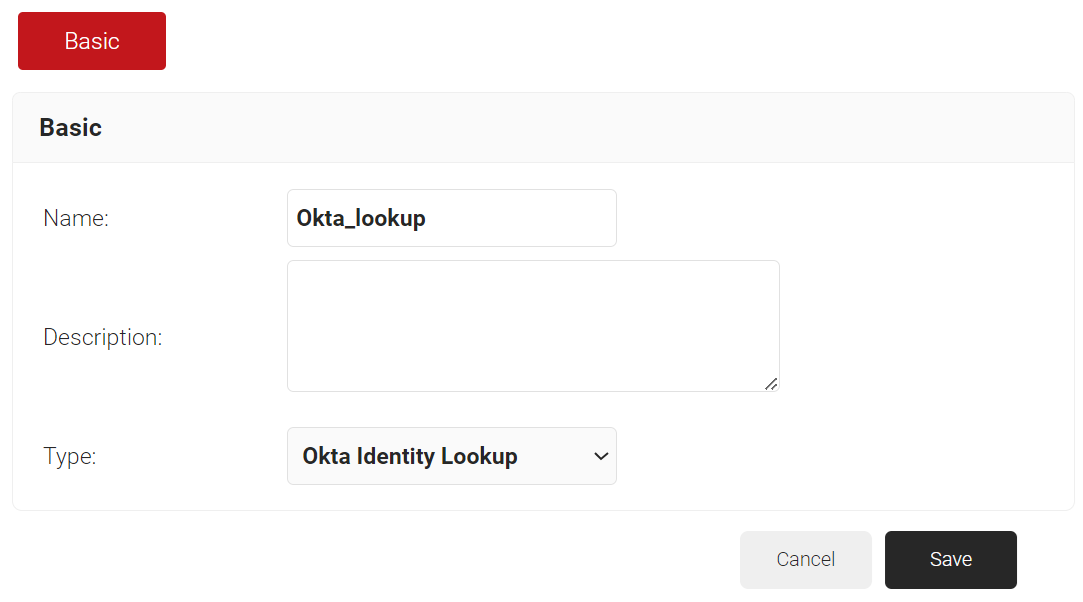
- Click Save.
- The page refreshes and displays the Configuration, Attribute Mapping, and Groups tabs.
- Click the Configuration tab.
- Under the Configuration section, provide the following information.
- In the Provider URL field, enter your Okta organization URL, such as
https: //dev—123456.okta.com/
NOTE: Do not use “admin” in the organization URL, as the lookup will fail. - In the API Token field, enter the token you obtained from the Okta portal (see the Creating an API Token in Okta section).
- Click the Validate button to check the connection with Okta.
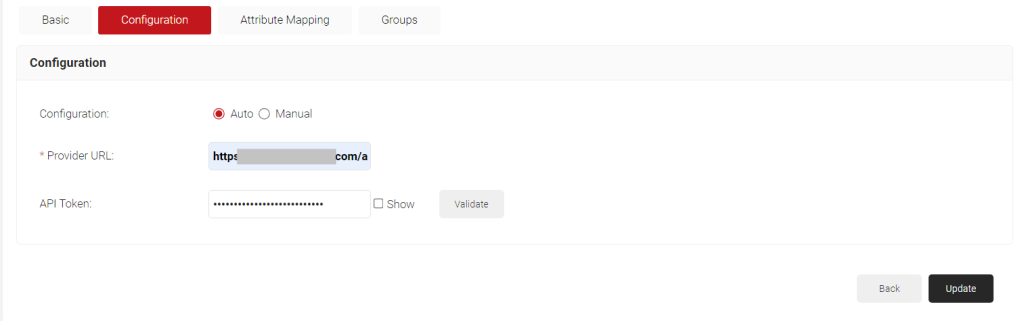
- Click Update.
- In the Provider URL field, enter your Okta organization URL, such as
NOTE: By creating the Identity Lookup Provider in JoinNow with the API token from Okta, a service app is created in Okta along with a Read-Only admin role.
If the Identity Lookup Provider is deleted in the JoinNow Management Portal, the service app in the Okta portal is also deleted. API Token needs manual deletion in the Okta portal.
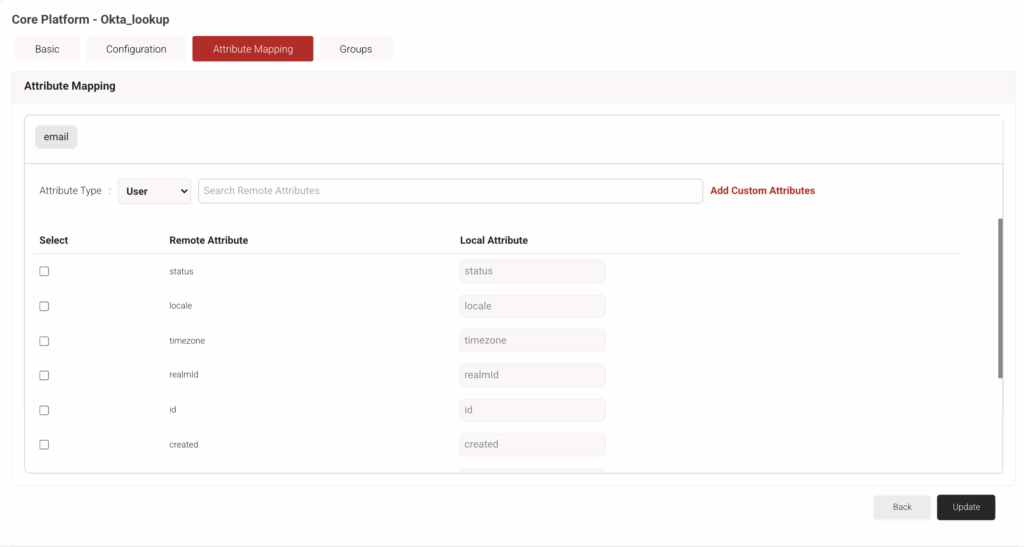
Configuring Attributes
To add a custom attribute to the identity lookup provider, follow the below steps.
- Navigate to Integrations Hub > Core Platforms.
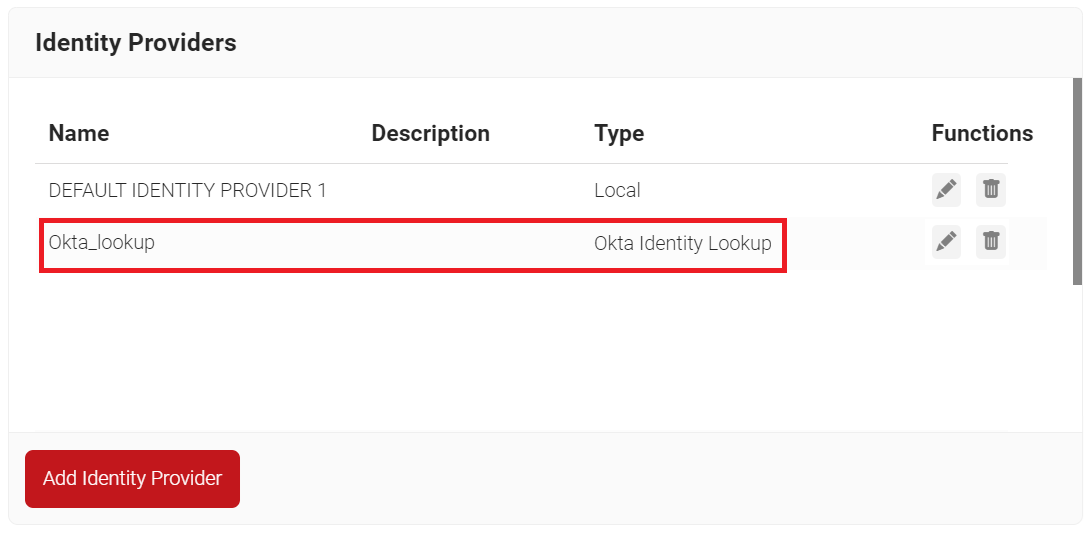
- Click the Edit link on the Identity Lookup Provider created earlier (refer to the Creating an Identity Lookup Provider section).
- Navigate to the Attribute Mapping tab.
- From the Attribute Type drop-down, select the category to display the recommended attributes. The following are the attribute types offered by JoinNow for Okta Lookup:
- Device
- User
- Custom
- Click Update after selecting the required attributes
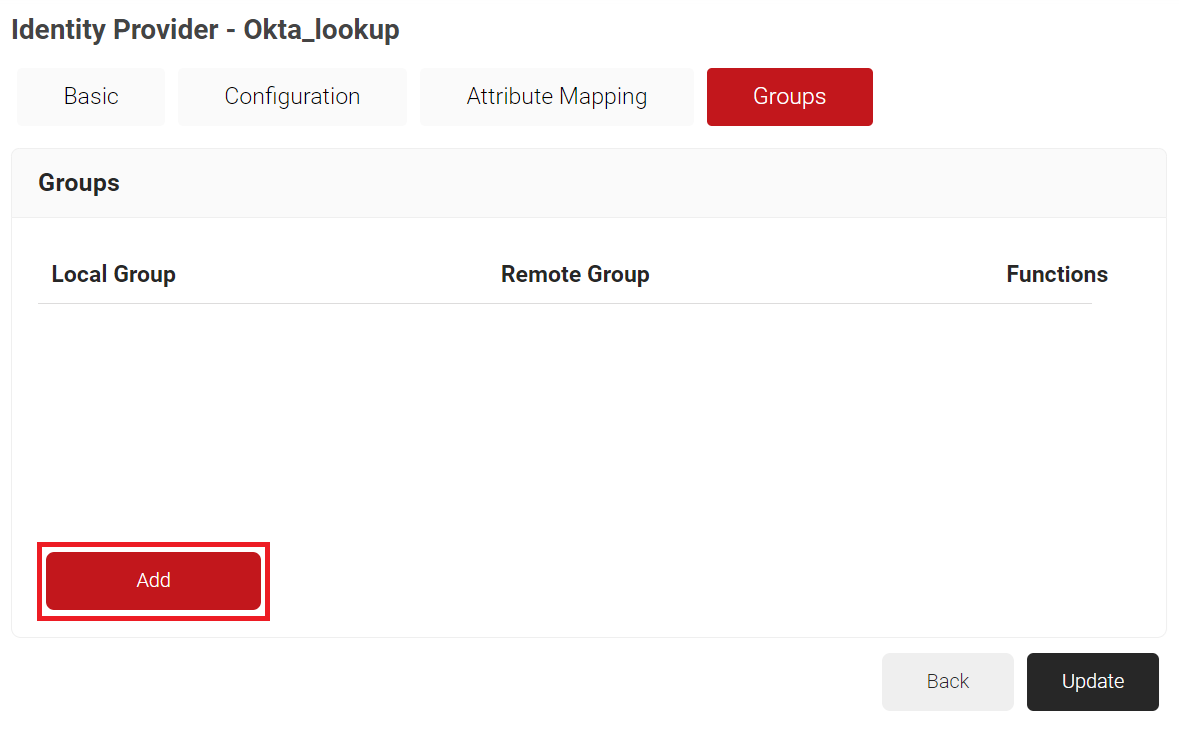
Configuring Groups
Here is where we will map the group attributes we want to use in our network policies.
- Navigate to Integrations Hub > Core Platforms.
- Click the Edit link on the Identity Lookup Provider created earlier (refer to the Creating an Identity Lookup Provider section).
- Navigate to the Groups tab.
- Click Add.
- In the Local Group field, enter a name for the group. This group name can be used to configure the Network Policies.
- In the Remote Group field, enter the name of your group as it is configured in the Okta portal.
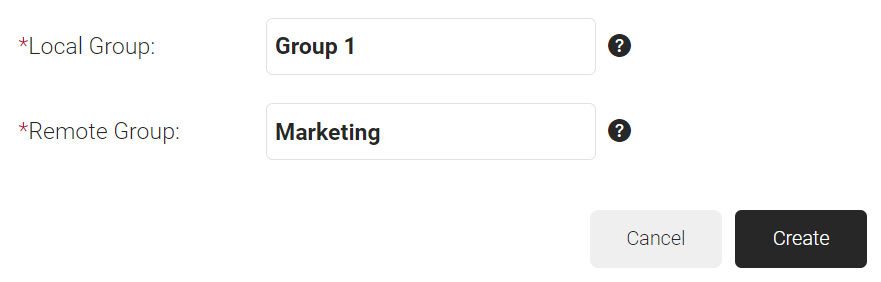
- Click Create.
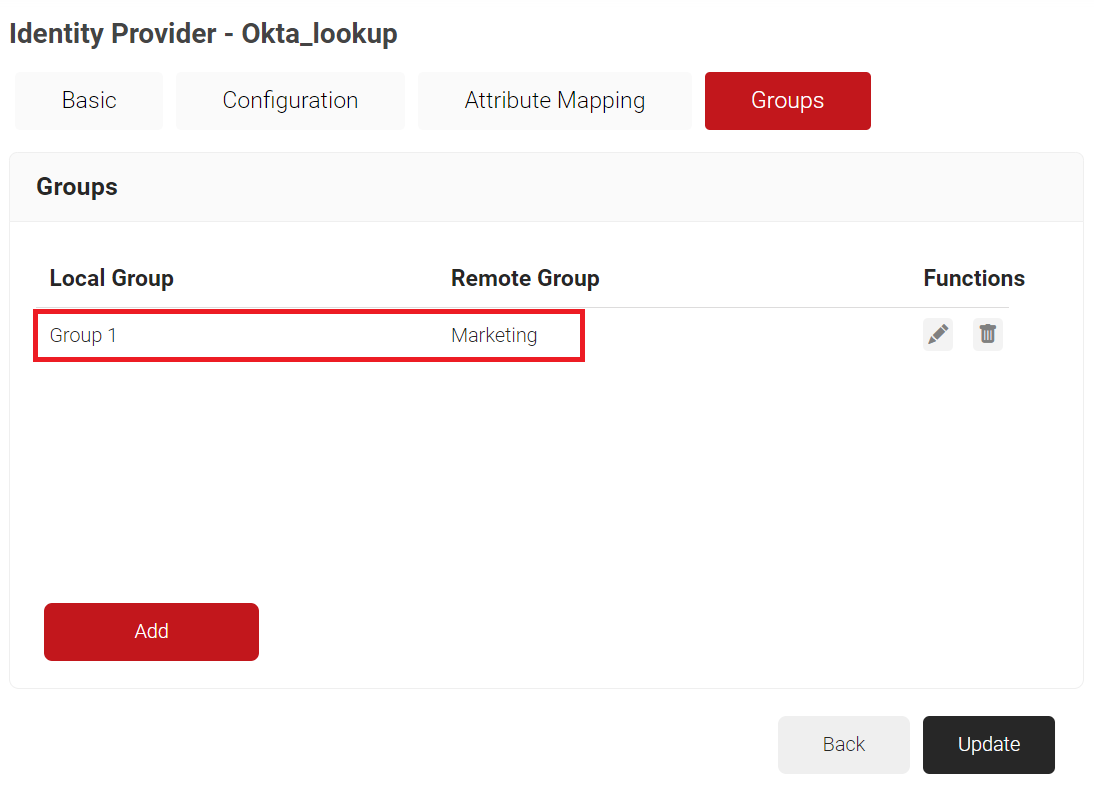
NOTE: Repeat the process as required for the groups you wish to create network policies around.
Configuring Policies
The following policies need to be configured:
Configuring Security Signal Source
Lookup Policies tie our new Identity Lookup Provider to domains. Here, we will create a condition that ties our domain to the new Identity Lookup Provider we created in the previous section ( see the Creating an Identity Lookup Provider section).
- Navigate to Policy Management > Security Signal Sources.
- Click Add Security Signal Source.
- In the Basic section, enter the name of the Account Lookup Policy in the Name field.
- In the Display Description field, enter a suitable description for the Account Lookup Policy.
- In the Lookup Purpose field, select the RADIUS Authentication checkbox to add the policy to the RADIUS Authentication workflow.
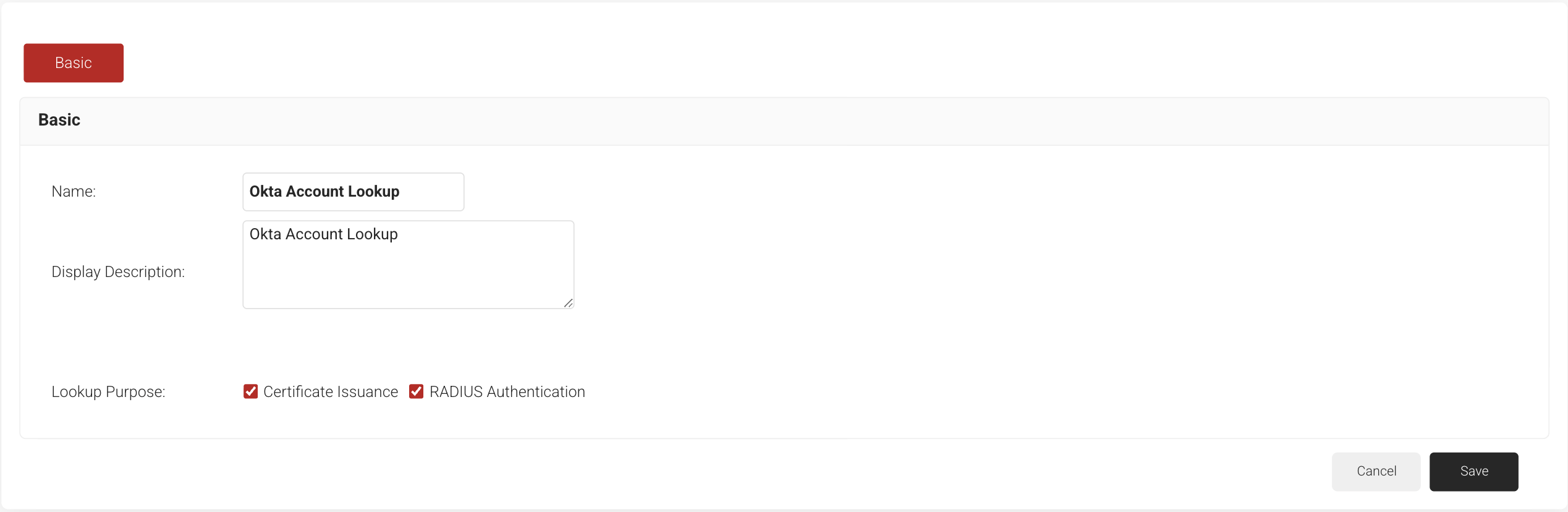
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
- Select the Conditions tab.
- Under the Conditions section, select the appropriate value from the Identity drop-down list.
- Configure Regex to match the values of your devices configured in the Identity field.
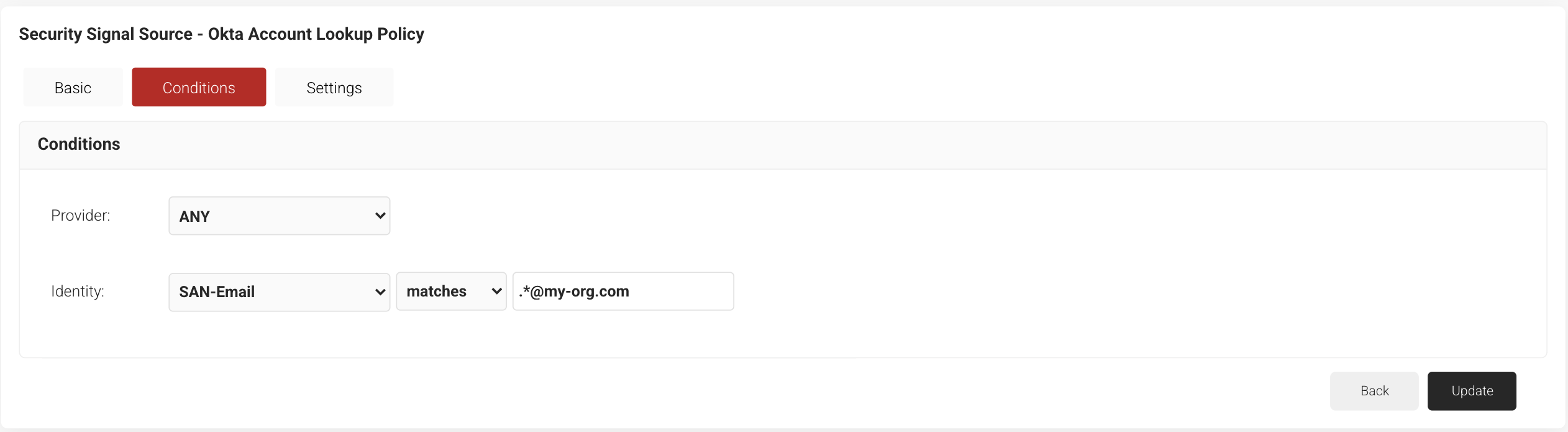
- Click Update.
- Select the Settings tab.
- Under the Settings section, from the Identity Provider Lookup drop-down list, select the Identity Lookup Provider created in the previous section (see the Creating an Identity Lookup Provider section).
- From the Lookup Type drop-down list, select the lookup type:
- Auto: The system automatically uses identity as the Lookup attribute.
- Custom: The Identity drop-down list is displayed. Select a device or user identity for lookup.
- The user identities are:
- Username
- Certificate-CommonName
- Certificate-SAN-UPN
- Certificate-SAN-Email
- The device identities are:
- Certificate-SAN-DNS
- Client ID
- Computer Identity
- The user identities are:
- In the Lookup Purpose field, select the purpose of Account Lookup
- Certificate Issuance – To lookup user/device account during Certificate Issuance.
- RADIUS Authentication – To lookup user/device account during RADIUS Authentication
- Select the Revoke On Failure checkbox to automatically revoke a certificate if an account lookup fails, if necessary.
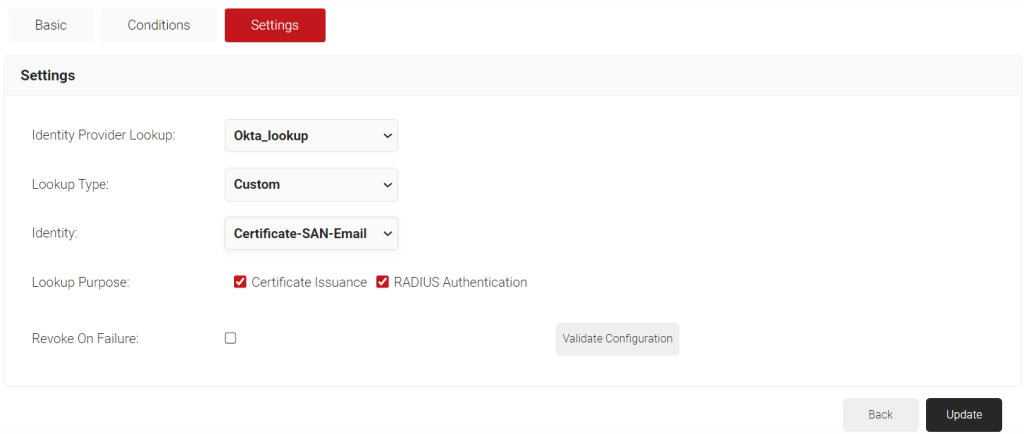
- Click the Validate Configuration button to check if the lookup is valid.
- On the Validate Configuration pop-up window, in the Enter a valid identity field, enter the identity (user/device) to validate the lookup, and click Validate.
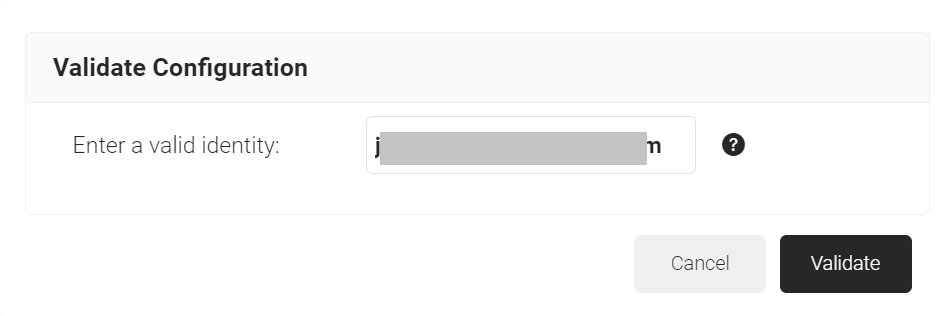
- After the successful validation, the associated attributes and groups of the Identity Provider Lookup are displayed on the Lookup Details prompt. The admin can use this information to configure the network policies and verify the user’s validity.
NOTE: When the Admin enters an invalid identity on the Validate Configuration pop-up window, the following error message is displayed: “Account lookup failed.”
- Click Update.
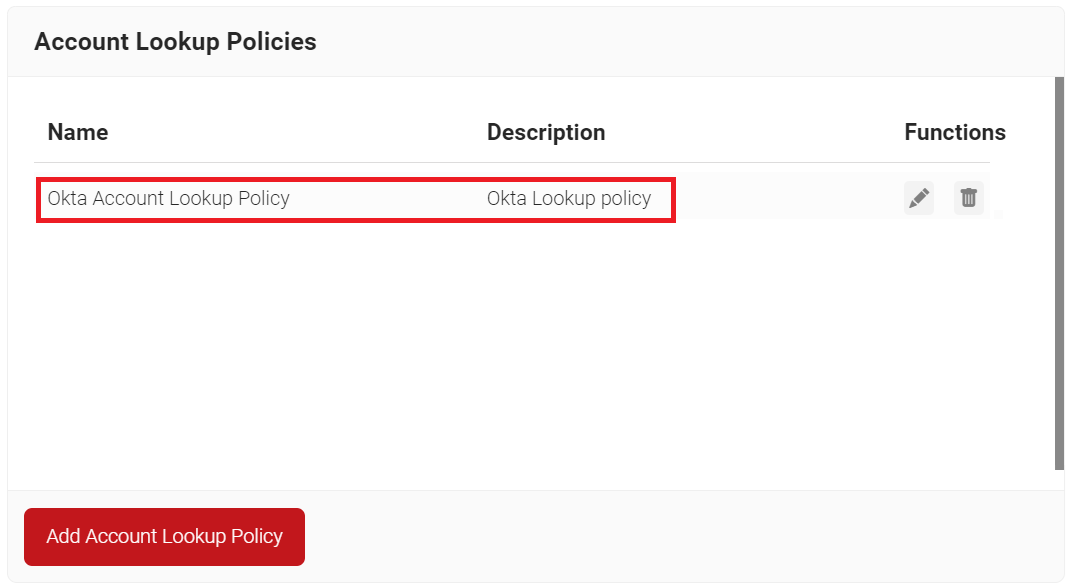
Configuring Policy Workflow
The following Policy Engine Workflows need to be configured:
Policy Engine Workflow for Network Authentication
First, create a role policy for network authentication. This policy will be used by Cloud RADIUS Dynamic Policy Engine to lookup user status at the moment of authentication. Then, Cloud RADIUS can dynamically apply Network policies, which you will configure next.
- Navigate to Policy Management > Policy Engine Workflows.
- Click Add Policy Engine Workflows.
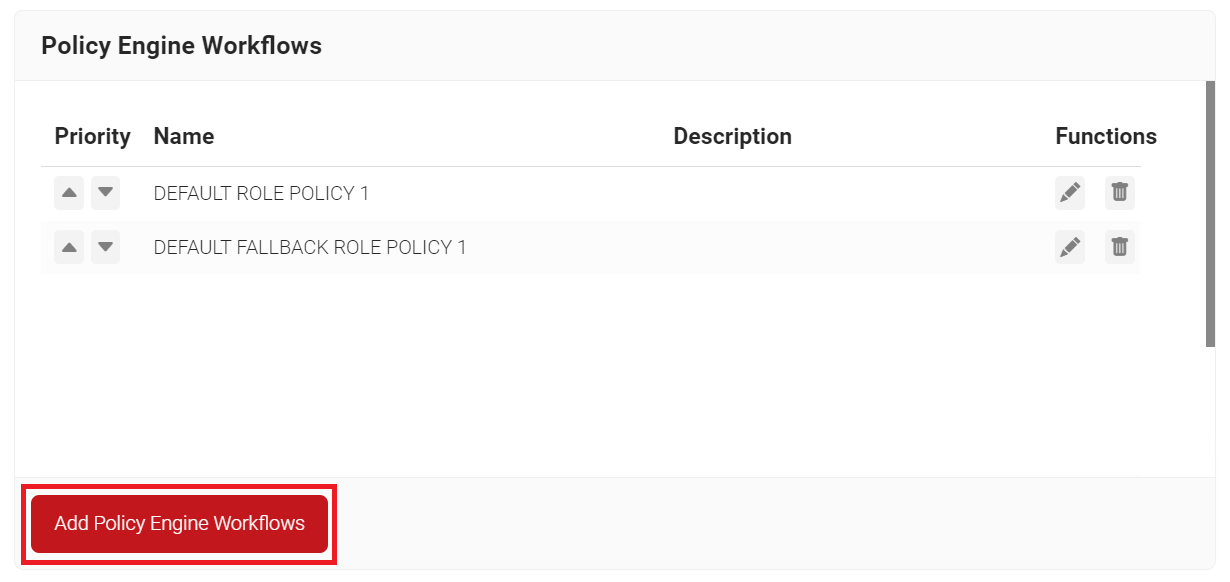
- In the Name field, enter the name of the Policy Engine Workflow.
- In the Display Description field, enter a suitable description for the Policy Engine Workflow.
NOTE: Ensure that you create a separate Policy Engine Workflow for authentication.
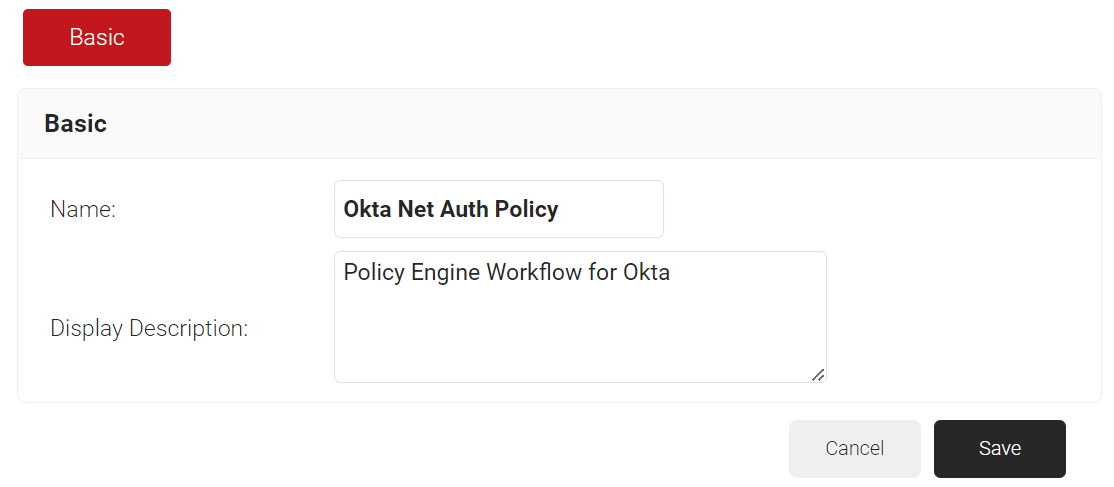
- Click Save.
- The page refreshes and displays the Conditions tab.
- Select the Conditions tab.
- From the Core Provider drop-down list, select the Okta Identity Lookup Provider created in the previous section (see the Creating an Identity Lookup Provider section).
- Click + Add Attribute to add the required attributes.
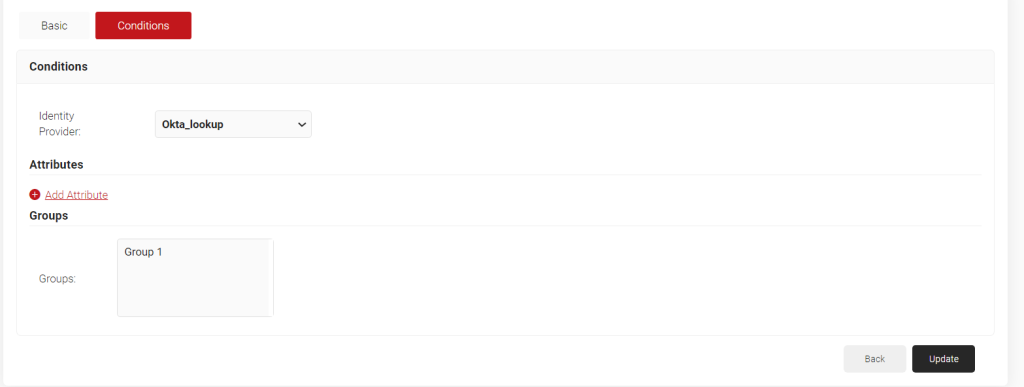
- Click Update.
Group Policy Engine Workflow for Network Authentication
Next, create role policies for groups you want to give differentiated network access. We can then leverage Cloud RADIUS’ Dynamic Policy Engine to send unique RADIUS attributes based on the users’ group with the network policies.
- Navigate to Policy Management > Policy Engine Workflows.
- Click Add Policy Engine Workflows.

- In the Name field, enter the name of the Group Policy Engine Workflow.
- In the Display Description field, enter the suitable description for the Group Policy Engine Workflow.
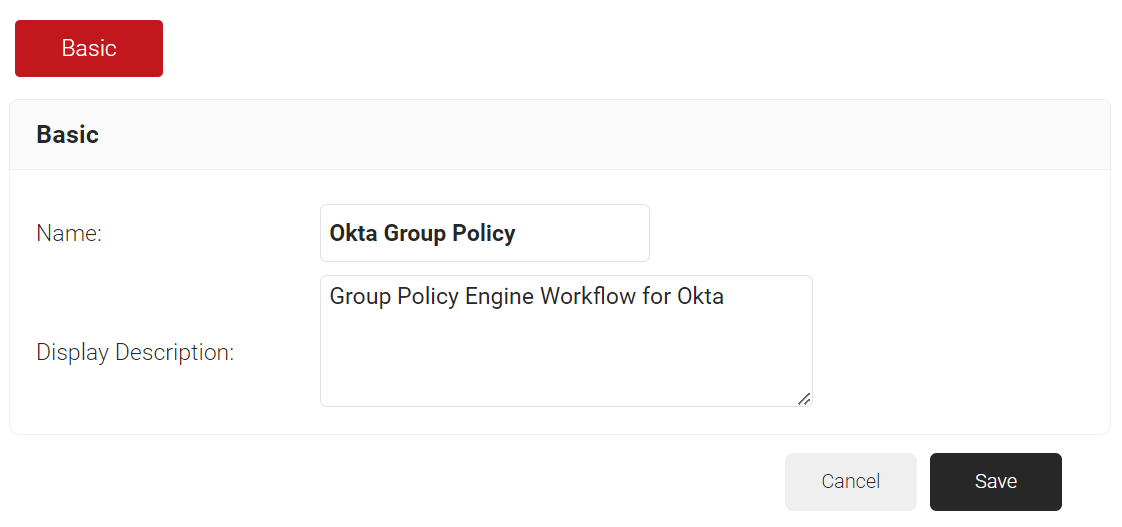
- Click Save.
- The page refreshes and displays the Conditions tab.
- Select the Conditions tab.
- From the Identity Provider drop-down list, select the Okta Identity Lookup Provider you created (see the Creating an Identity Lookup Provider section).
- In the Groups field, select the group to which you want to apply this role to.
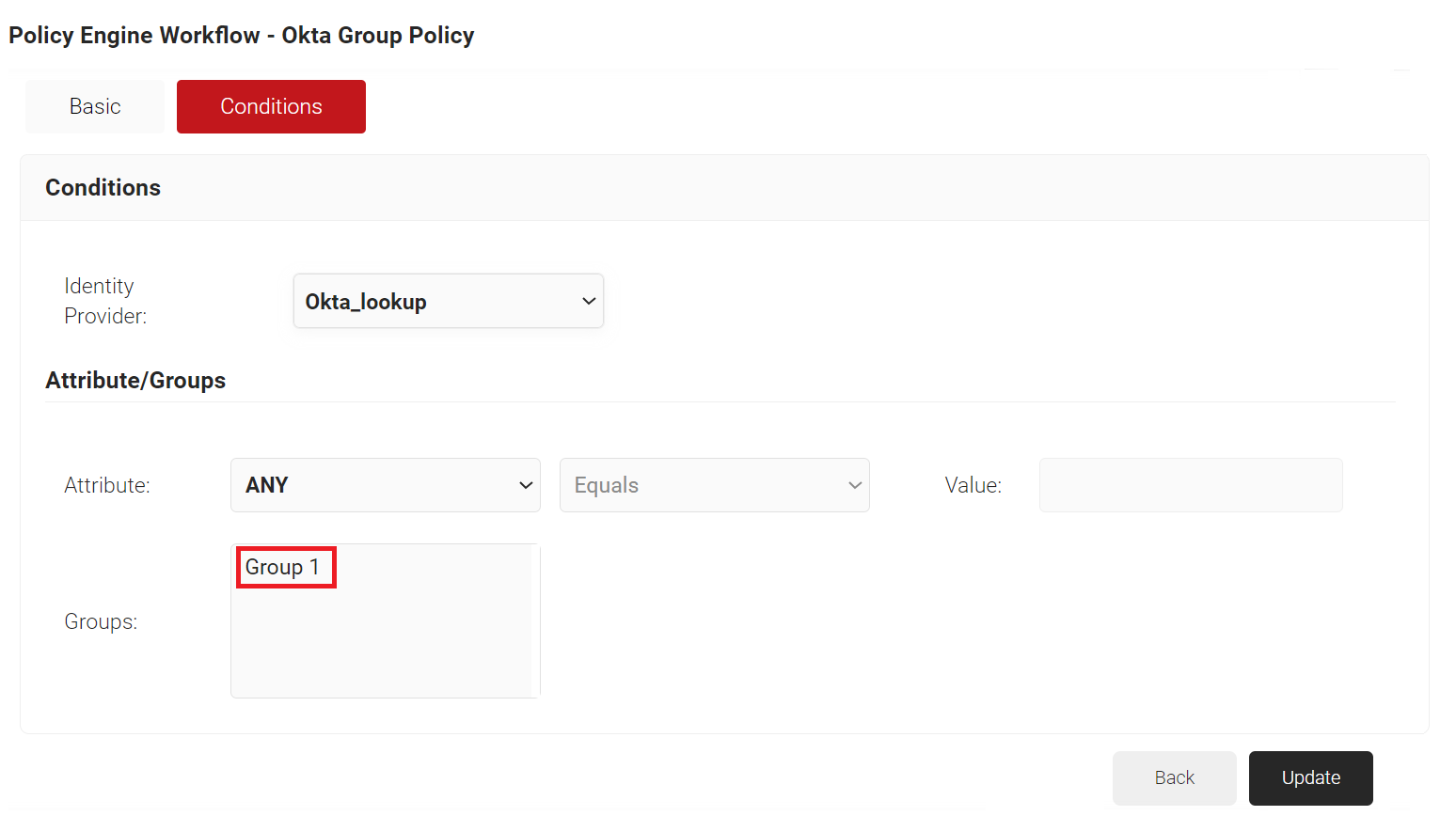
NOTE: The displayed group names are the Local Groups you configured in the Identity Lookup Provider. - Click Update.
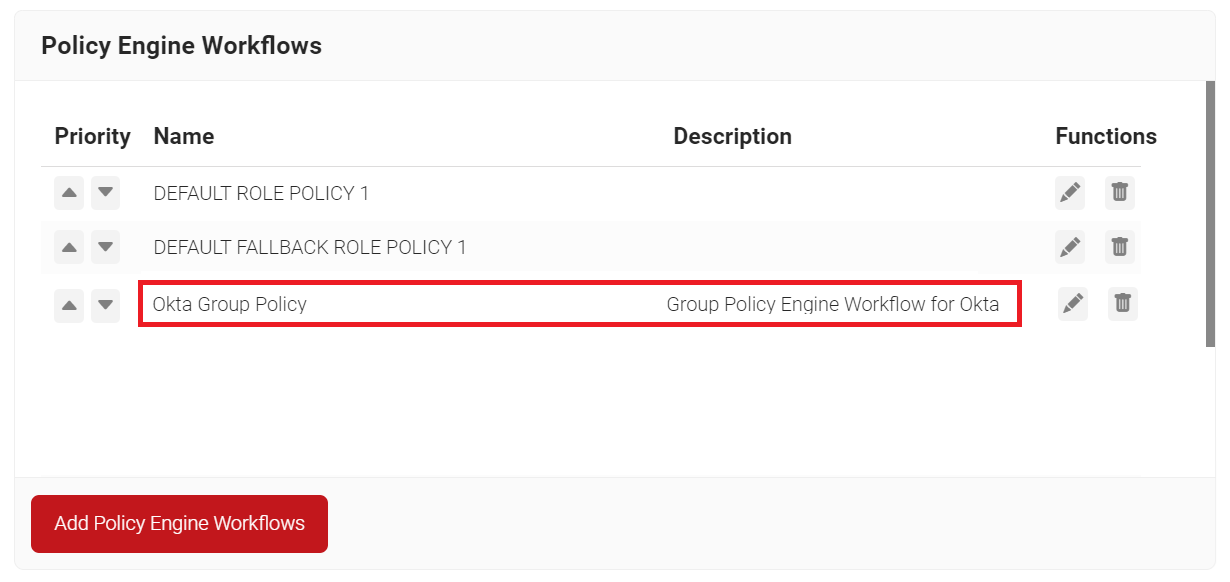
Default Fallback Policy Engine Workflow
You may notice that your Policy Engine Workflows have a “DEFAULT FALLBACK ROLE POLICY” after you create an Identity Lookup Provider.
If the Identity lookup fails, this policy allows the user to still authenticate to the network but assigns them a unique role.
This ensures that users don’t experience disconnections if there’s a small hiccup in the connection between Okta and Cloud RADIUS. Your network can remain secure, and you can have those users auto-assigned into a Guest VLAN.
Configuring Network Policy
A Network Policy specifies how Cloud RADIUS will authorize access to a particular Policy Engine Workflow.
A typical Network Policy would say something like the following: “If User Role = Staff, authorize access and assign them to VLAN 2.”
You can configure any RADIUS Attribute to be sent to the wireless controller. If you leave the attribute section blank, it will just send an “Access Accept” message.
To create and configure the Network Policy, follow the steps below:
- Navigate to Policy Management > Network.
- On the Network Policies page, click Add Network Policy.
- In the Basic section, in the Name field, enter the name of the Network Policy.
- In the Display Description field, enter the suitable description for the Network Policy.
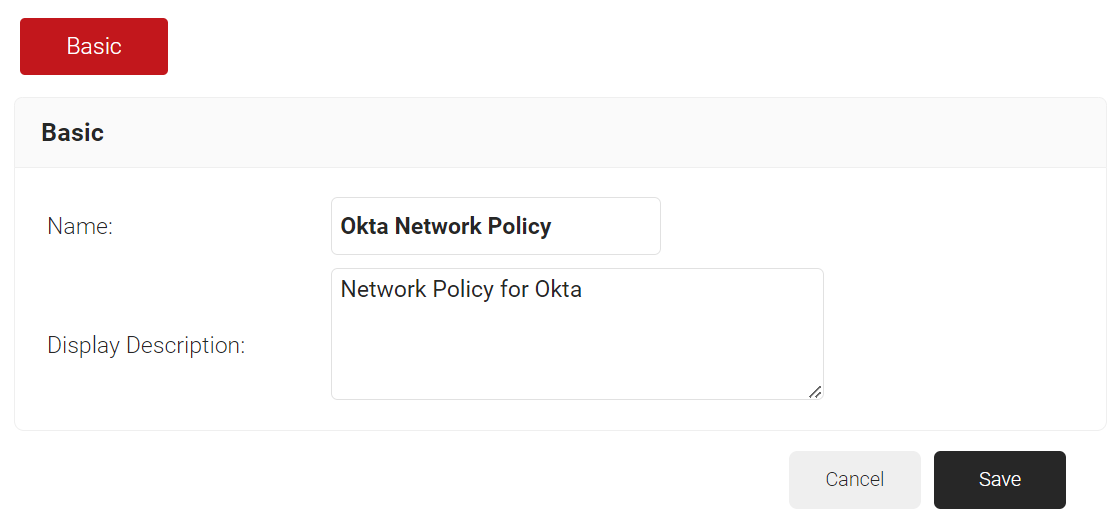
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
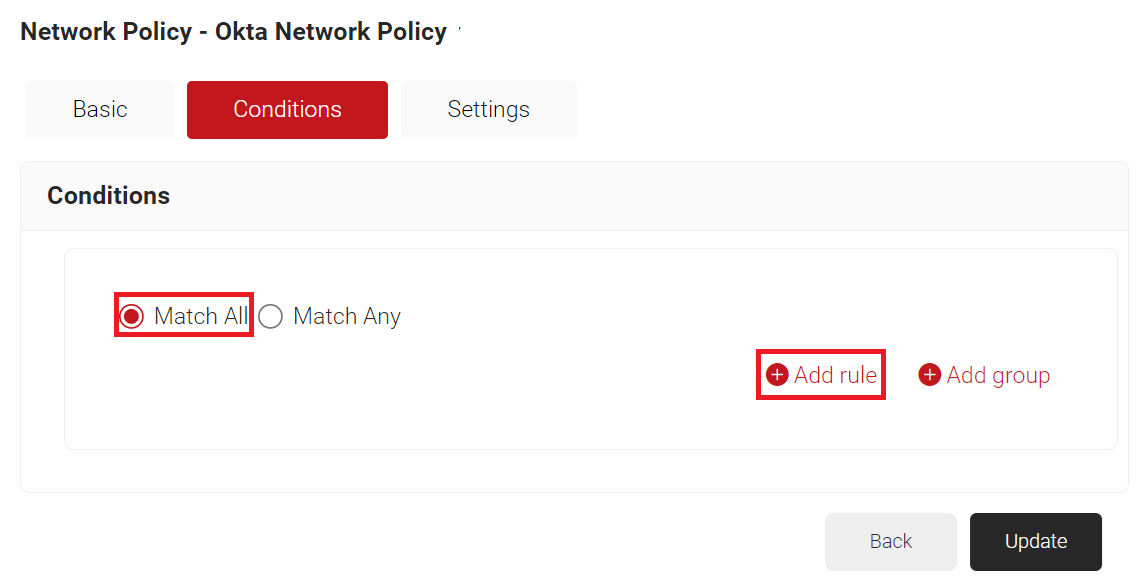
- Select the Conditions tab.
- Select Match All or Match Any based on your requirement to set authentication criteria. In the case explained here, we are selecting Match All.
- Click Add rule.
- Expand Device and select the Device Role option.
- Expand Identity and select the Role option.
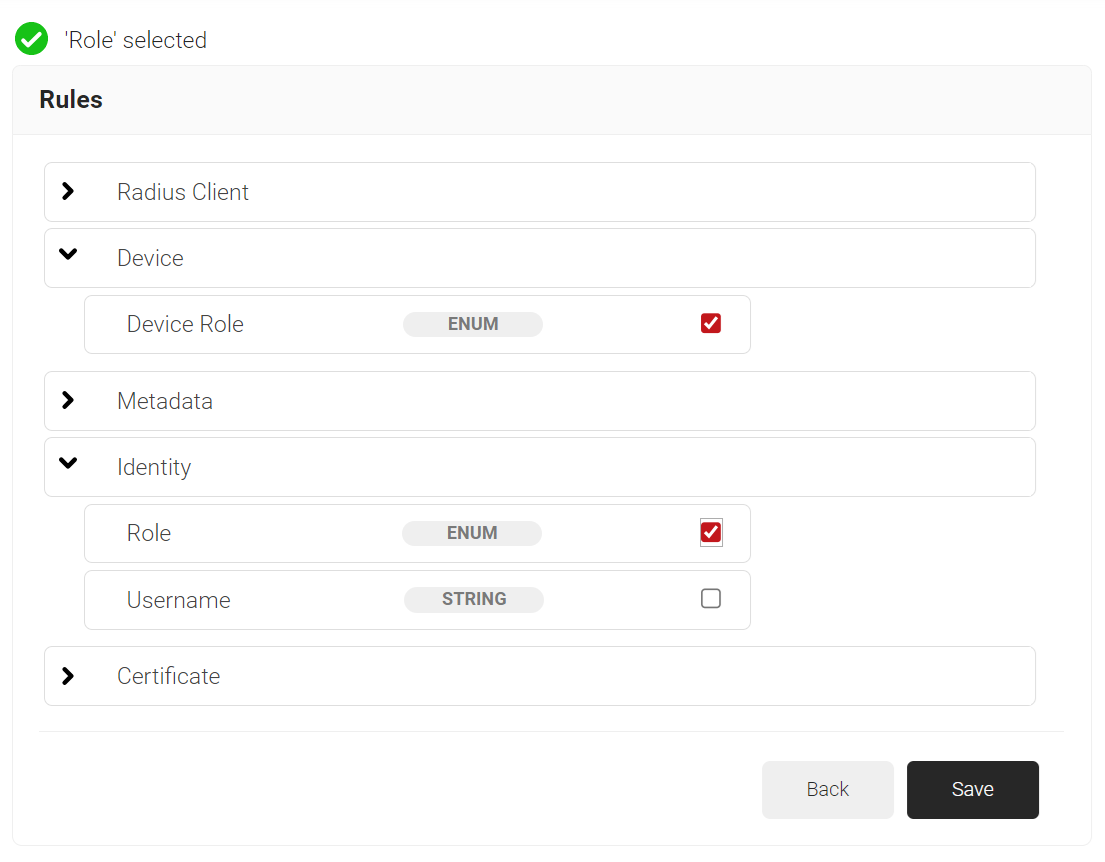
- Click Save.
- The Device Role and Role options appear under the Conditions tab.
- From the Device Role Equals drop-down list, select the default device role policy. (Further to the explained roles, you can leverage your network segmentation by using the other rules available. The explained above are the minimal configurations required for setting up a network policy).
- From the Role Equals drop-down list, select the Policy Engine Workflow you created earlier (refer to the Policy Engine Workflow for Network Authentication section). You can select multiple Policy Engine Workflows to assign to a Network Policy.
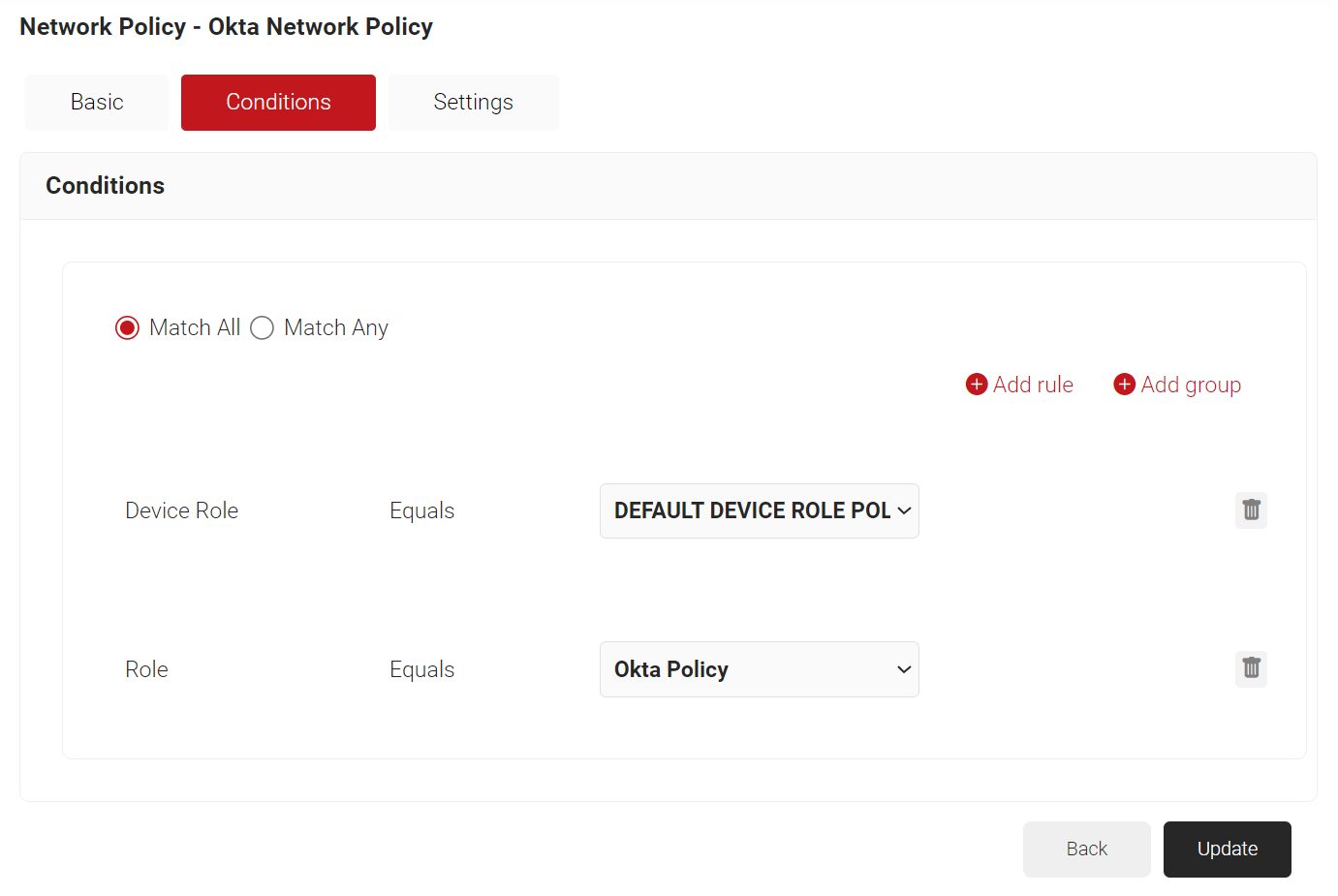
NOTE: You can assign a network policy to multiple user roles. - Select the Settings tab.
- Click Add Attribute.
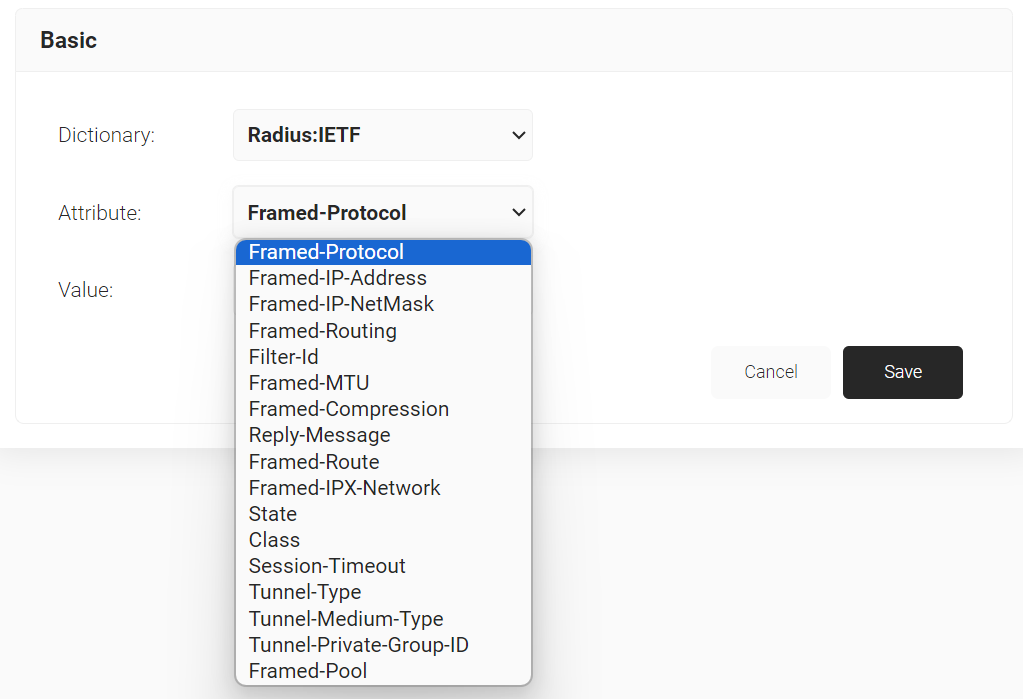
- From the Dictionary drop-down list, select an option: Radius: IETF or Custom.
- From the Attribute drop-down list, select a RADIUS attribute and enter the value for the RADIUS attribute in the Value field. After successful RADIUS authentication, the specified RADIUS attribute values are sent to the Controller to configure the device. The supported attributes in the RADIUS IETF dictionary are:
- Framed-Protocol
- Framed-IP-Address
- Framed-IP-NetMask
- Framed-Routing
- Filter-Id
- Framed-MTU
- Framed-Compression
- Reply-Message
- Framed-Route
- Framed-IPX-Network
- State
- Class
- Session-Timeout
- Tunnel-Type
- Tunnel-Medium-Type
- Tunnel-Private-Group-ID
- Framed-Pool
- In the Value field, enter the appropriate value for the attribute.
- Click Save.
- Click Update.
NOTE: Repeat the process for all the attributes you want to send to the Policy Engine Workflow.
Conclusion
Dynamic RADIUS will revolutionize the way certificate-based WPA2-Enterprise networks are run. It eliminates all traces of security weaknesses and the SecureW2 solution helps to manage certificates and users. SecureW2 has affordable options for organizations of all sizes. Click here for further details.