Introduction
This guide demonstrates the authentication process of devices based on their respective physical MAC addresses using Media Access Control (MAC). Once the source MAC address is identified, the switch generates an access-request message, with the user/machine’s MAC address as the identity, and sends it to the RADIUS server. The RADIUS server performs MAC authentication after getting the access-request message.
The RADIUS authentication server determines whether to grant access to the user/device and specifies the level of access the client should receive. After making this decision, the RADIUS server transmits the access-accept, allowing the user/machine to access the network.
If you are interested in setting up EAP-TLS Authentication, you can find the relevant instructions and resources at the following link: How to Set Up Passwordless RADIUS Authentication with an Ubiquiti Unifi Access Point
Creating an Identity Provider in SecureW2
Identity providers (IdPs) manage digital identities that help organizations to authenticate their users or employees and grant or revoke access permissions as needed. Follow the below steps to create an Identity Provider in JoinNow Management Portal and configure it for MAC Authentication:
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to Identity Management > Identity Providers.
- Click Add Identity Provider.
- In the Name field, enter a name for your IdP.
- In the Description field, enter a suitable description for your IdP.
- From the Type drop-down list, select MAC Authentication.
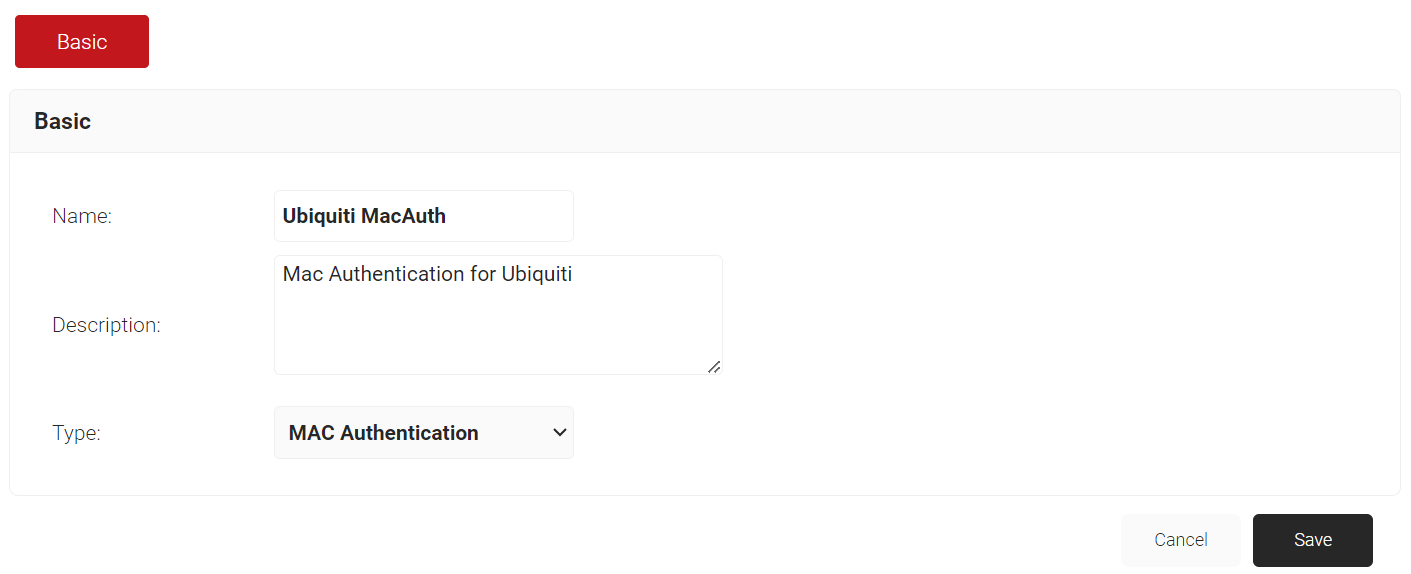
- Click Save.
- The page refreshes and displays the Configuration and Groups tabs.
- Select the Groups tab.
- Click Add group.
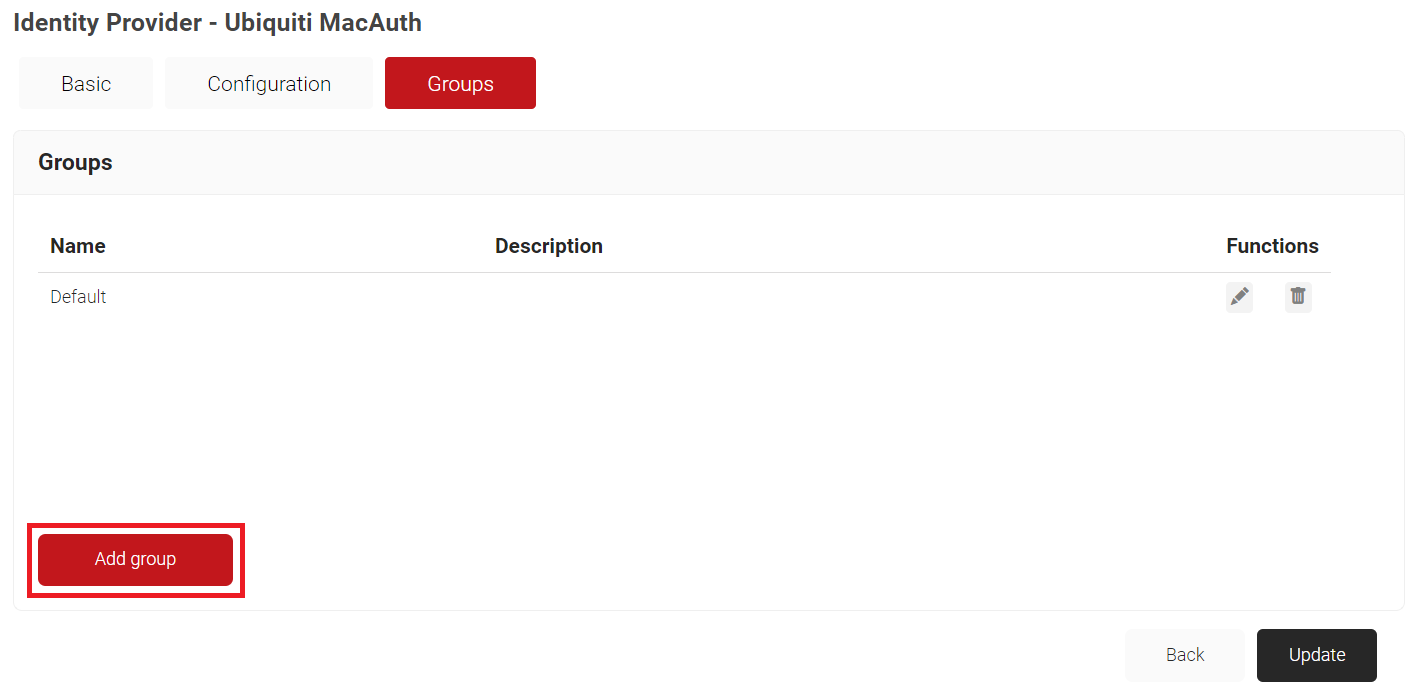
- On the displayed pop-up window, in the Name field, enter a name for your group.
- In the Description field, enter a suitable description for your group.
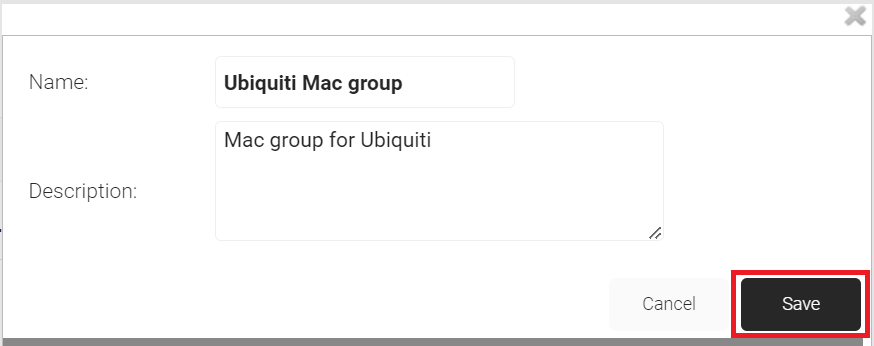
- Click Save.
- Select the Configuration tab.
- Click Add Device.
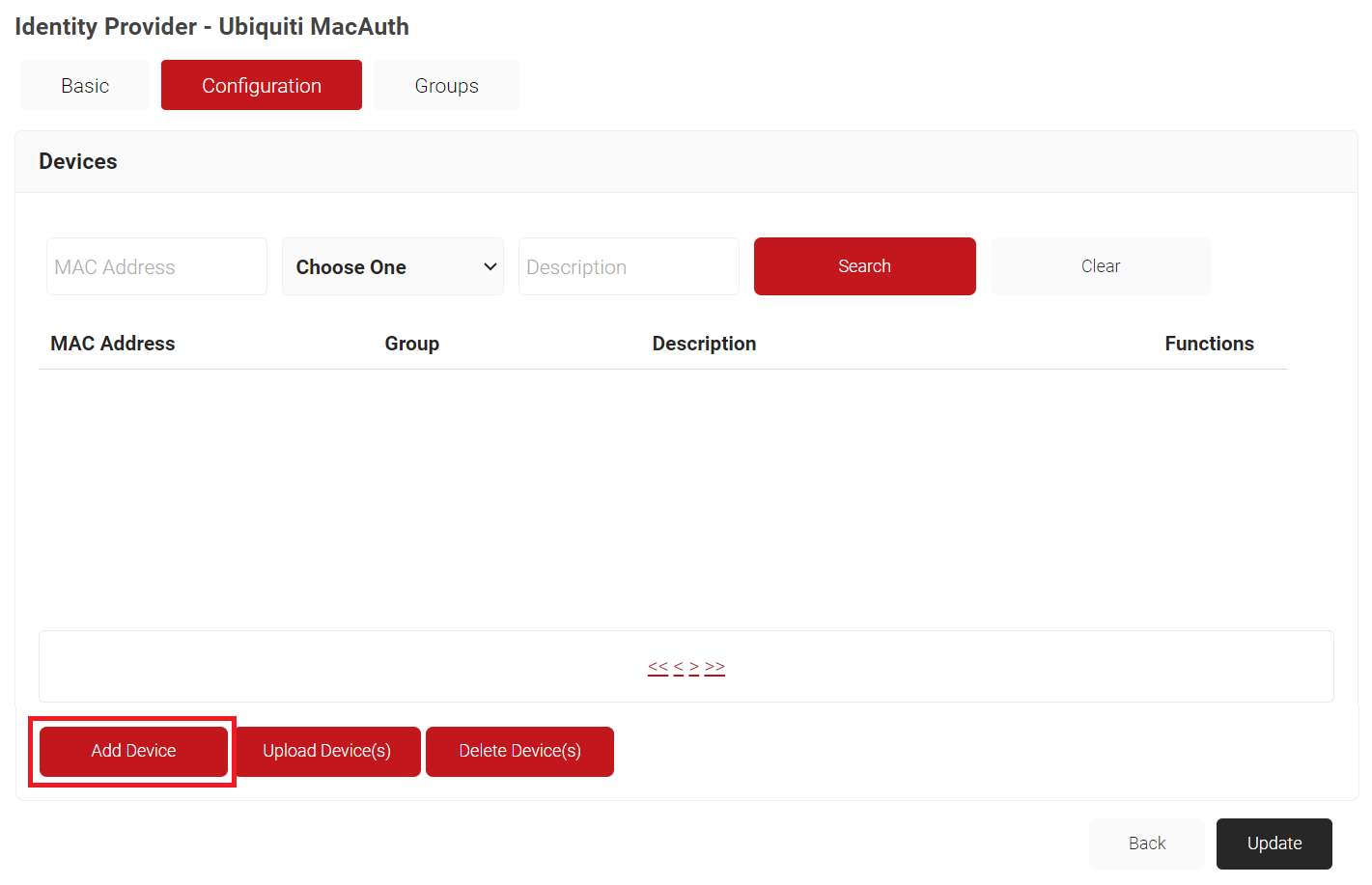
- On the displayed pop-up window, in the MAC Address field, enter the MAC address of the device that you want to authenticate.
- From the Group Name drop-down list, select the group name you created earlier.
- In the Description field, enter a suitable description for your device.
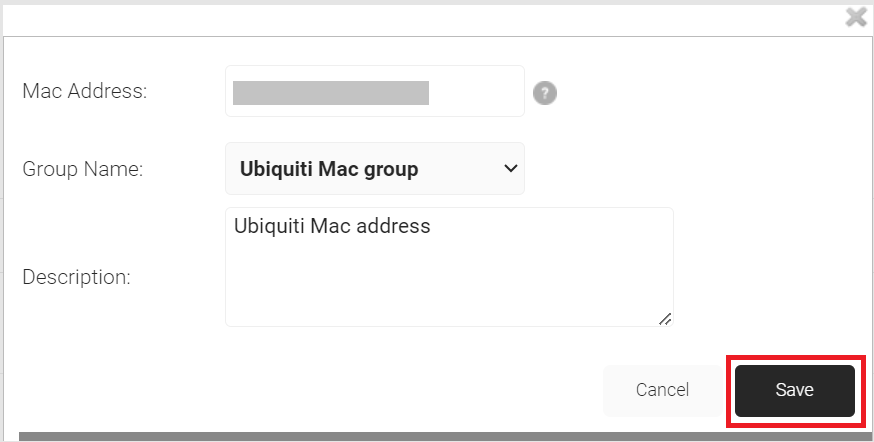
- Click Save.
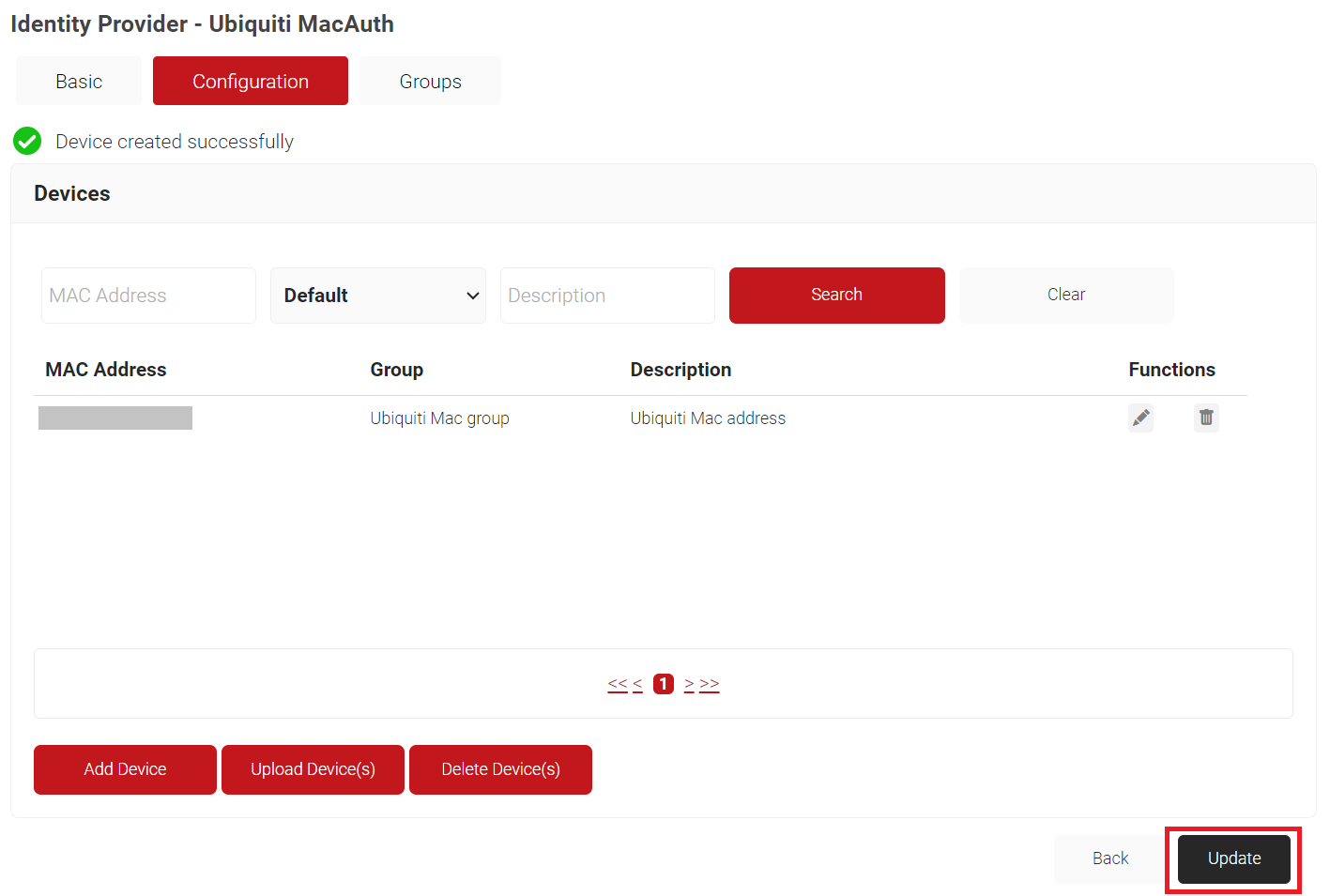
- Click Update.
Set up Role policy and Network policy
JoinNow Management offers policy-based management to facilitate VLAN-based segmentation. The policies to be configured are:
- Role Policy
- Network Policy
CREATING A ROLE POLICY
A Roles policy grants a user access to defined resources. To add a Role policy, perform the following steps:
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to Policy Management > Roles Policies.
- Click Add Role.
- In the Name field, enter a name for your role policy.
- In the Display Description field, enter a suitable description for your role policy.
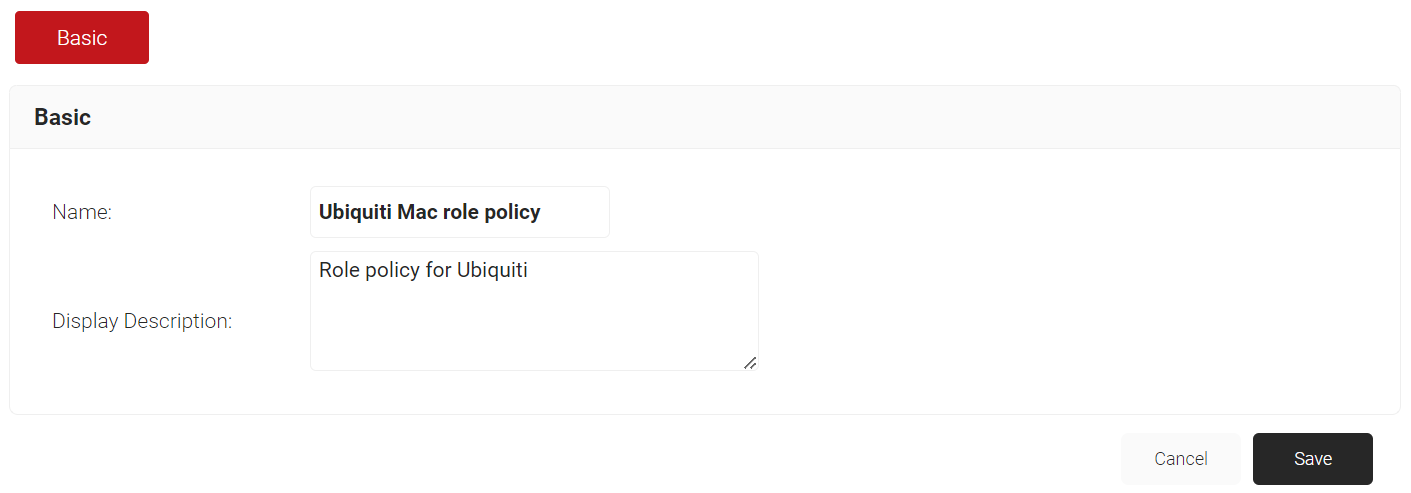
- Click Save.
- The page refreshes and the Conditions tab is displayed.
- Select the Conditions tab.
- In the Conditions section, from the Identity Provider drop-down list, select the IdP you created with the MAC Authentication type.
- In the Attribute/Groups section, in the Attribute field, retain ANY.
- In the Groups field, select the group you created earlier.
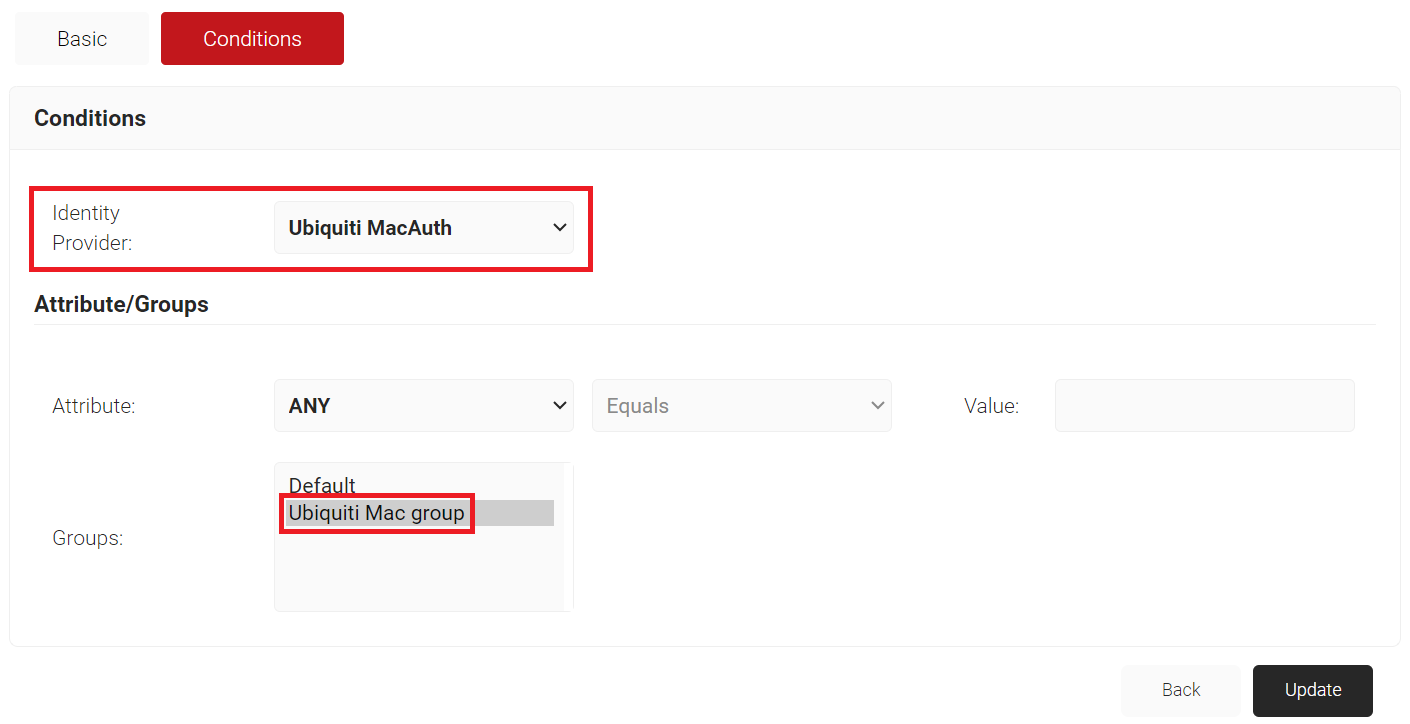
- Click Update.
CREATING A NETWORK POLICY
The purpose of a network policy is to specify how Cloud RADIUS will authorize access to a particular user role. To create and configure the Network policy, perform the following steps:
- Navigate to Policy Management > Network Policies.
- Click Add Network Policy.
- In the Name field, enter a name for your network policy.
- In the Display Description field, enter a suitable description for your network policy.
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
- Select the Conditions tab.
- In the Conditions section, select Match All or Match Any based on your requirement to set authentication criteria. In the case explained here, we are selecting Match All.
- Click Add rule.
- Expand Identity and select the Role option.
- Click Save.
- The Role option appears under the Conditions tab.
- From the Role Equals drop-down list, select the role policy you created earlier.
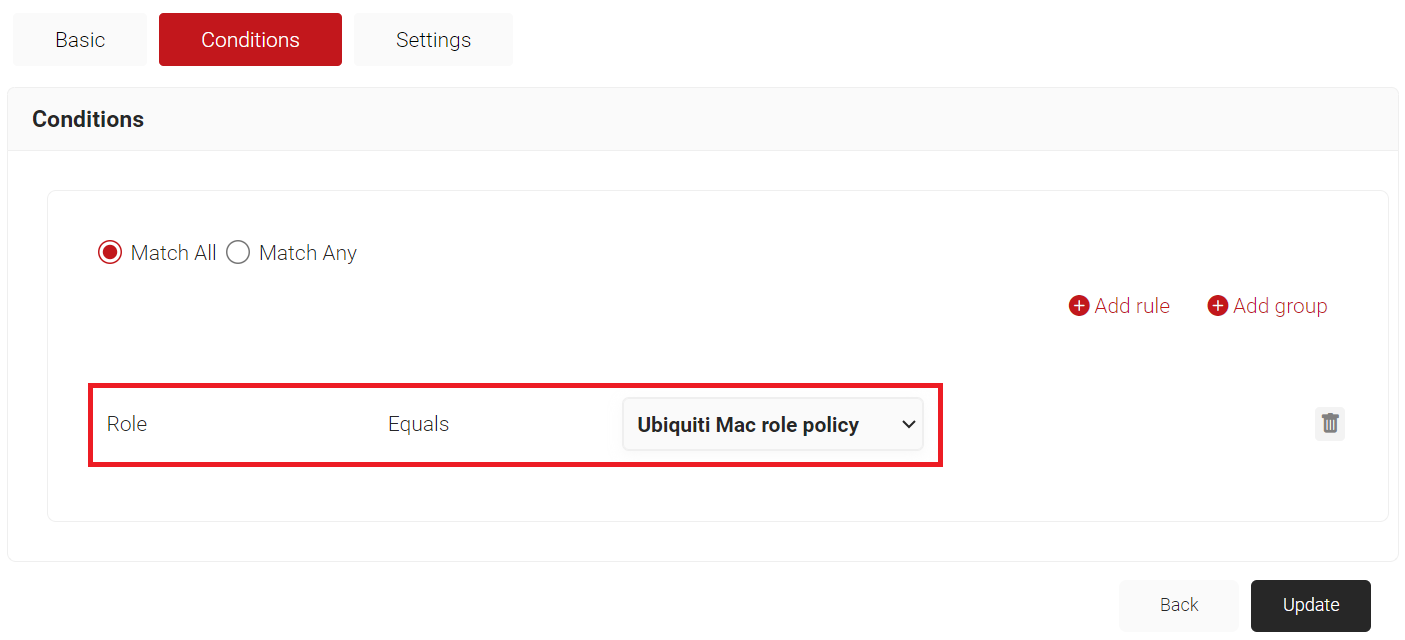
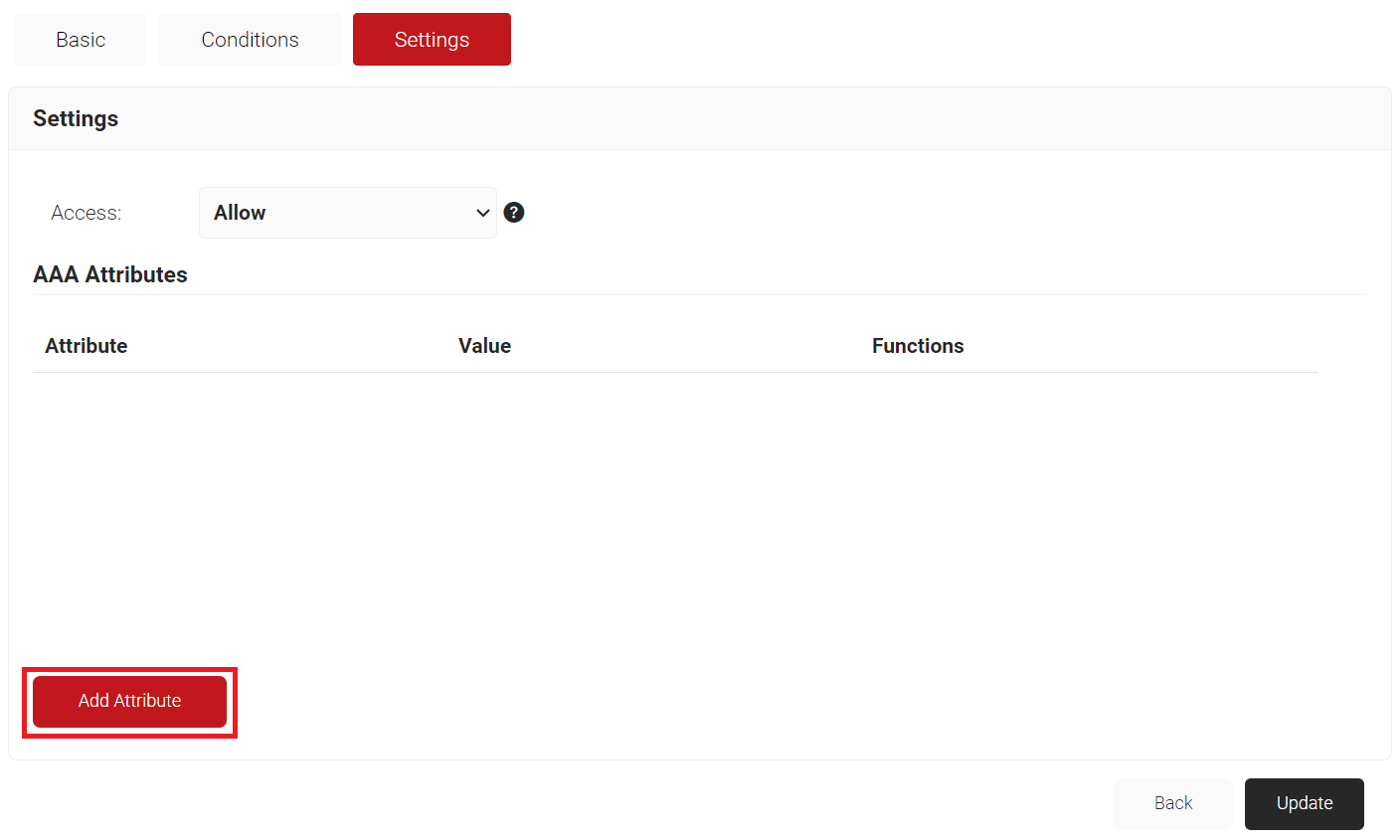
- Select the Settings tab.
- Click Add Attribute.
- From the Dictionary drop-down list, select an option: Radius:IETF or Custom.
- From the Attribute drop-down list, select Filter-Id.NOTE: Filter-Id is created on your access point to form a VLAN range.
- In the Value field, enter the VLAN filter-ID you wish to connect to.
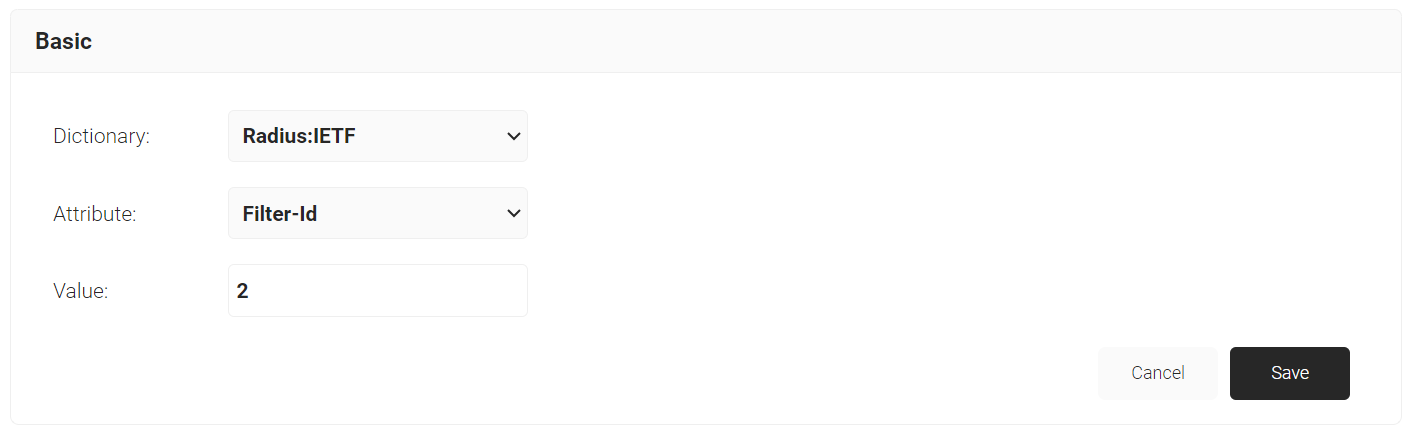
- Click Save.
Configuring MAC-based RADIUS Authentication in Unifi
Follow the below steps to set up MAC-based Authentication using Unifi:
- Log in to the Unifi Portal.
- On the left pane, select Profiles.
- Click Create New RADIUS Profile.
- In the New RADIUS Profile page, for the Name field, enter the name of your RADIUS profile.
- Under the RADIUS Assigned VLAN Support section, select the Enable checkbox for Wireless Networks.
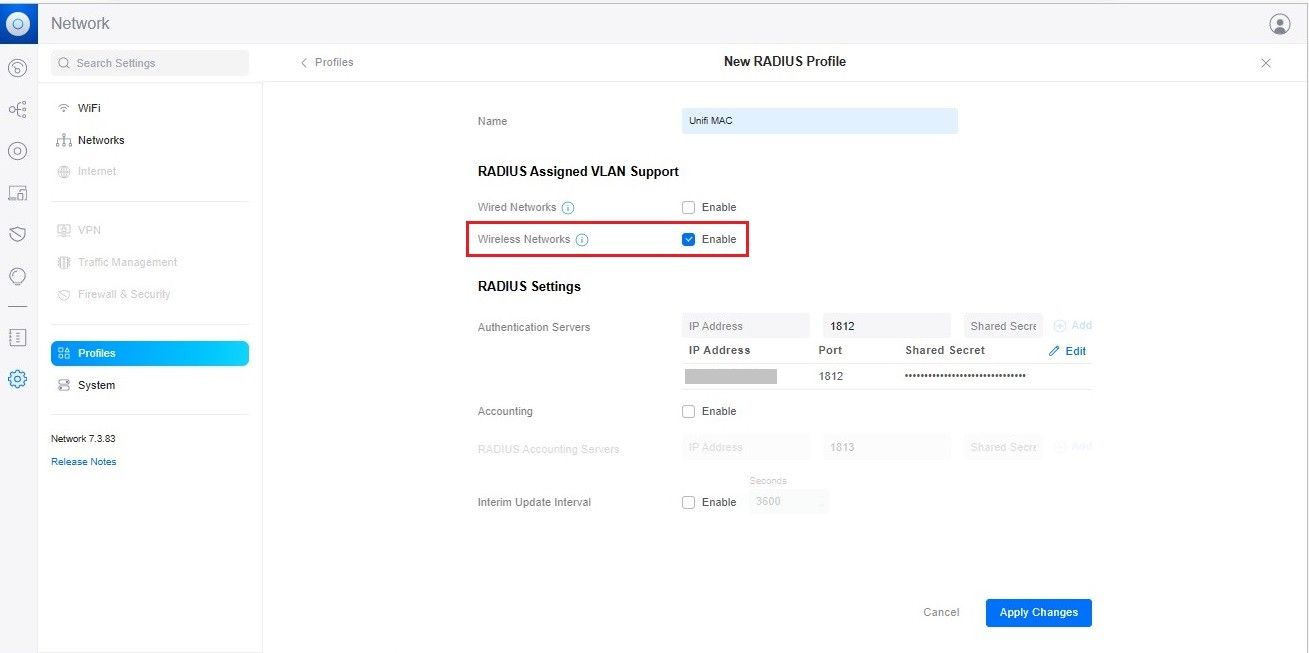
- In the RADIUS Settings section, for Authentication Servers, enter the IP Address, Port and Shared Secret. From the JoinNow MultiOS Management Portal (navigate to RADIUS > RADIUS Configuration), copy the IP Address, Port, and Shared Secret and paste them into the IP Address, Port, and Shared Secret fields in the Unifi.
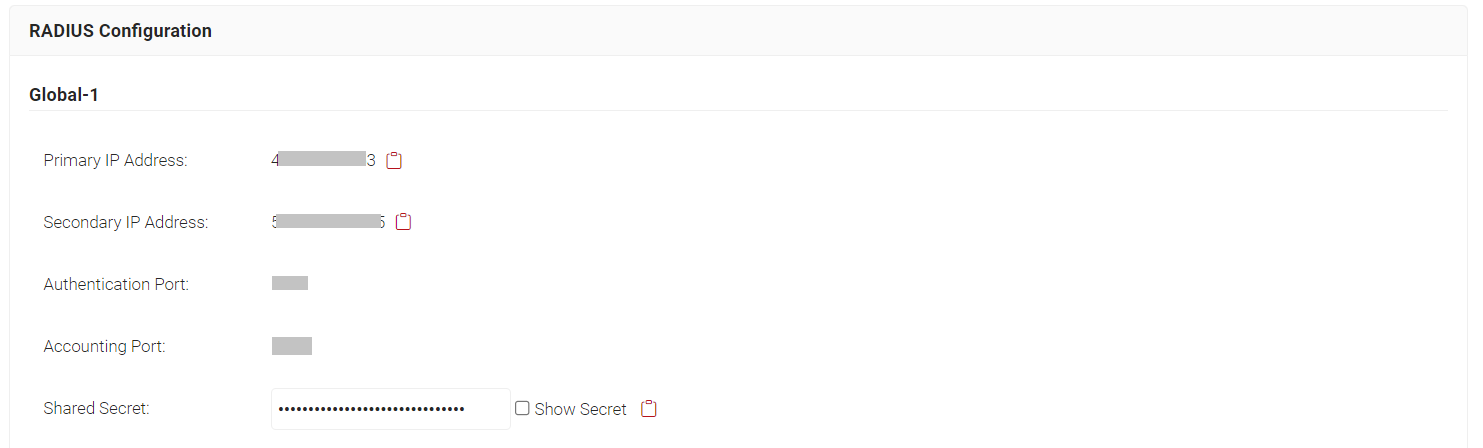 NOTE: The details of the RADIUS profile must be from the Organization in which MAC-based authentication IDP was created in the Creating an Identity Provider in SecureW2 section.
NOTE: The details of the RADIUS profile must be from the Organization in which MAC-based authentication IDP was created in the Creating an Identity Provider in SecureW2 section. - After entering the RADIUS details, click Add.
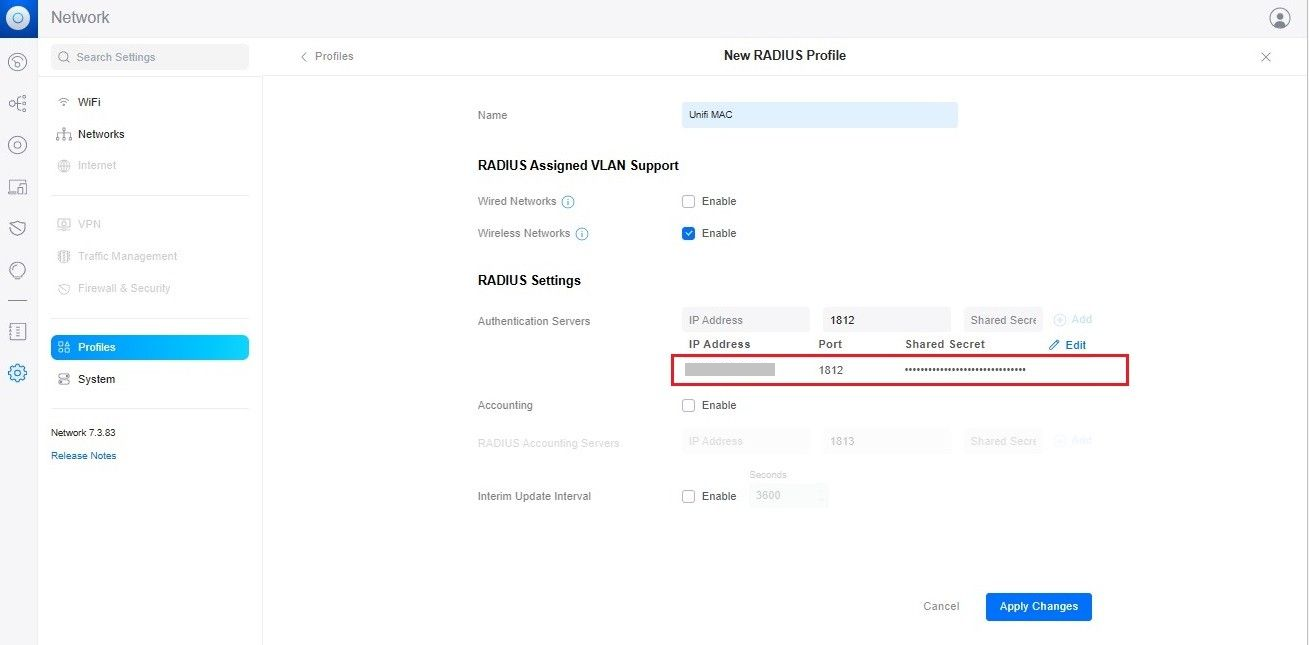
- Click Apply Changes.