How to Set Up EAP-TLS WPA2-Enterprise With Meraki
Introduction
In this guide we will integrate SecureW2’s PKI, RADIUS, and Device Onboarding and Certificate Enrollment software with Meraki Access Points to deliver EAP-TLS, certificate-based 802.1x authentication.
With SecureW2, you can easily configure any 802.1x Wi-Fi infrastructure for EAP-TLS. Transitioning from credential to certificate-based authentication has never been easier, with many of our customers getting it done in less than a couple hours.
If you are interested in setting up MAC-based RADIUS Authentication, you can find the relevant instructions and resources at the following link: How to integrate MAC based RADIUS Authentication with Cisco Meraki
Configuring the SecureW2 PKI and RADIUS Server
To configure a Network Profile for wireless, perform the following steps.
- Log in to the JoinNow Management Portal.
- Navigate to Device Onboarding > Getting Started.
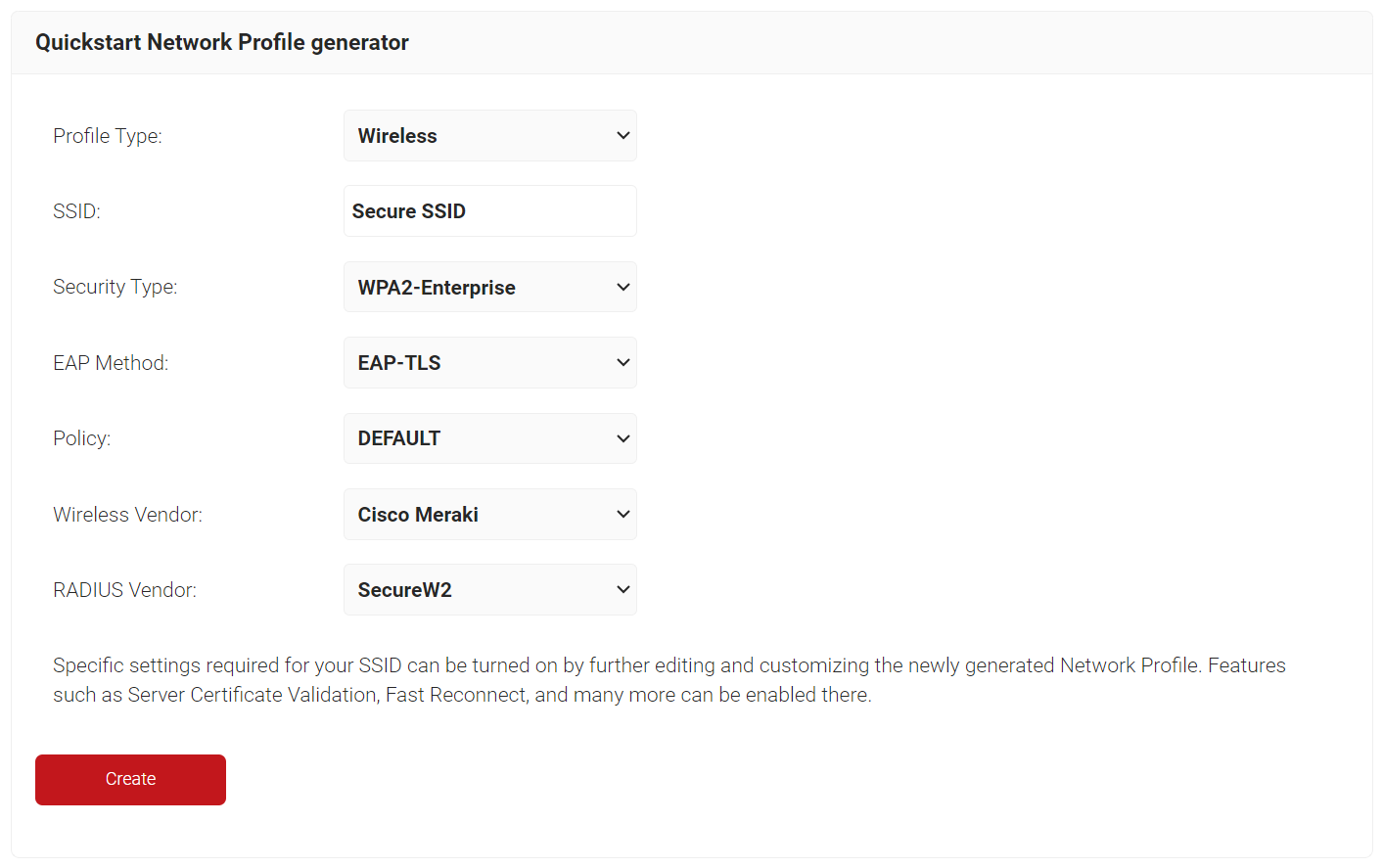
- On the Quickstart Network Profile generator page, from the Profile Type drop-down list, select Wireless.
- In the SSID field, type the name of a profile.
- From the Security Type drop-down list, select WPA2-Enterprise.
- From the EAP Method drop-down list, select EAP-TLS.
- From the Policy drop-down field, retain DEFAULT.
- From the Wireless Vendor drop-down list, select Cisco Meraki.
- From the RADIUS Vendor drop-down list, select a RADIUS vendor.
- Click Create.
To access the RADIUS details, follow the below steps.
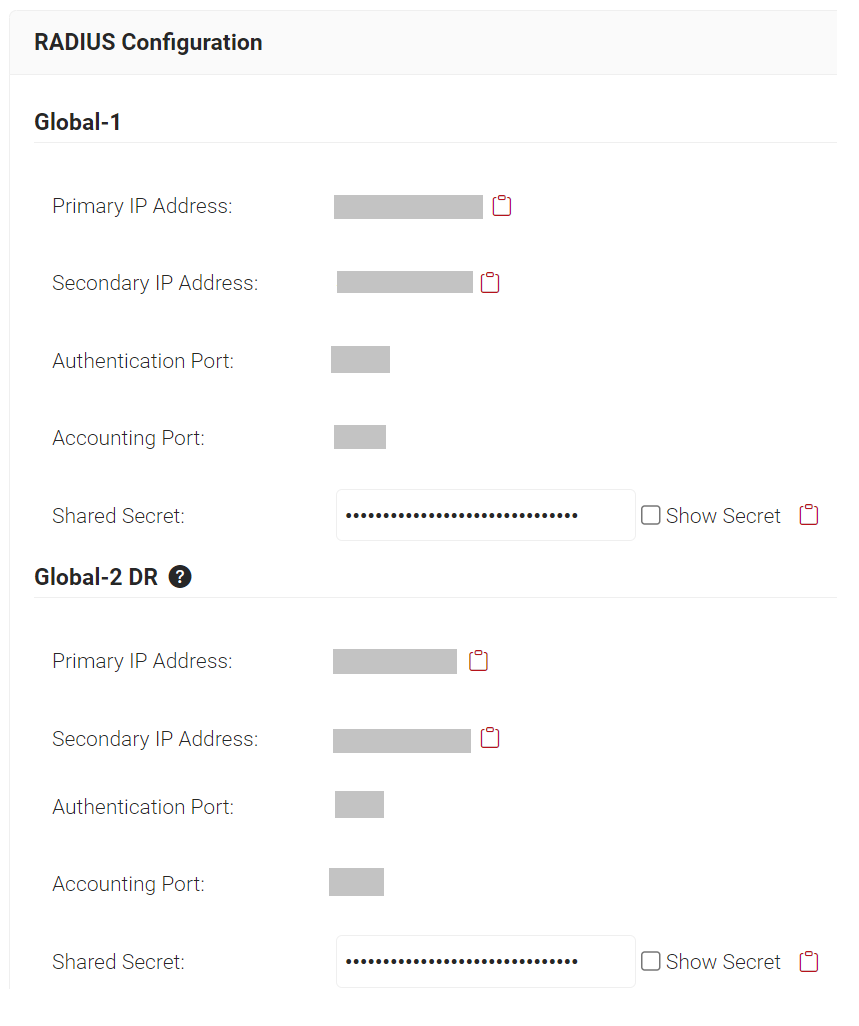
- Navigate to RADIUS > RADIUS Configuration.
- Copy the Primary IP Address, Authentication Port and Shared Secret of your subscribed region to your console.
Configuring Secure SSID
Follow the below steps to configure the Secure SSID.
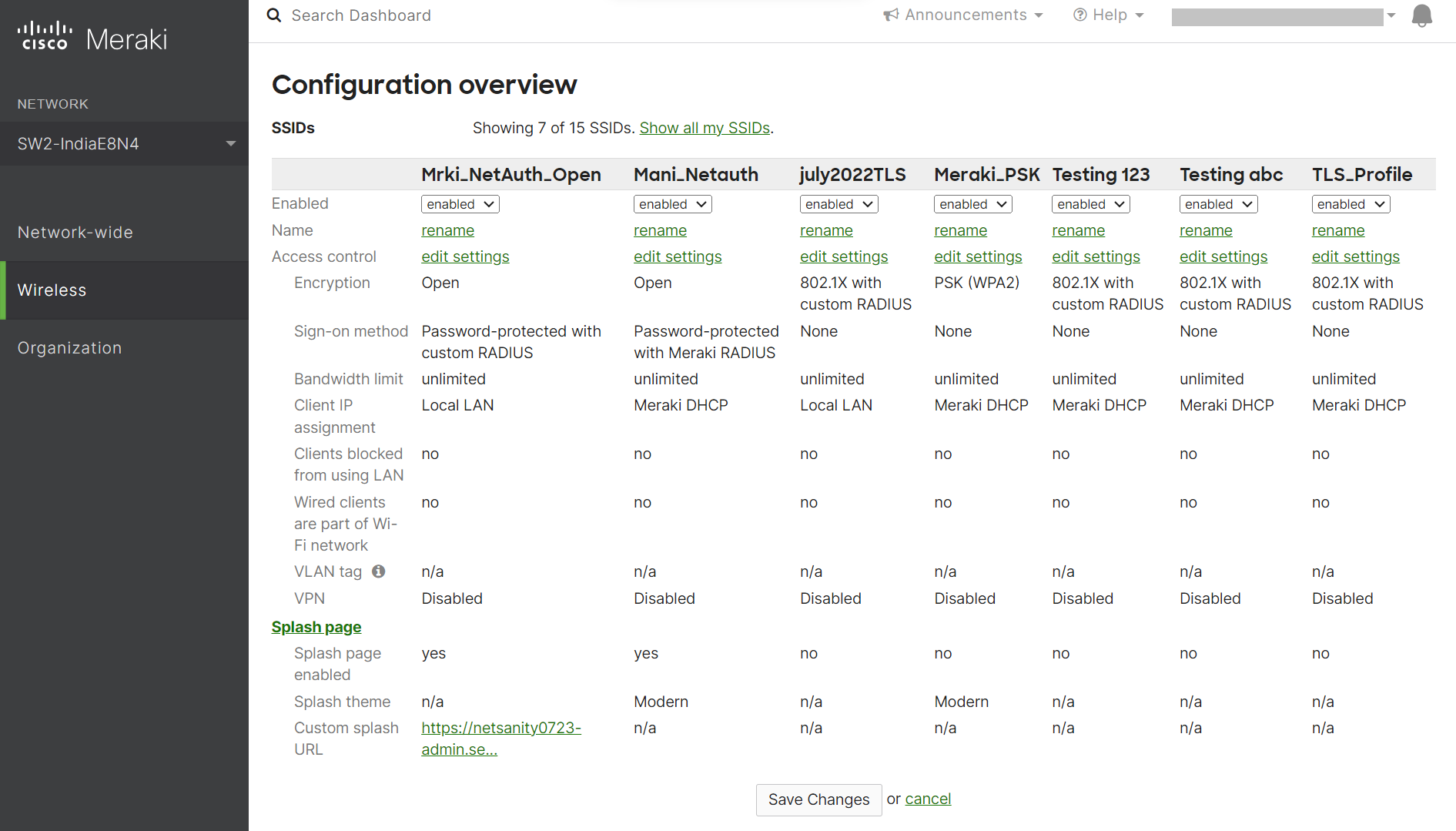
- Log in to the Meraki Dashboard.
- Navigate to Wireless > SSIDs.
- Select an unconfigured SSID and switch it from disabled to enabled.
- Click the rename link to change the SSID name (make sure it is the same name as the SSID in the Network Profile).
- Click Save Changes.
Setting Up SecureW2 as RADIUS Server in Meraki
Follow the below steps to configure the RADIUS server in Cisco Meraki.
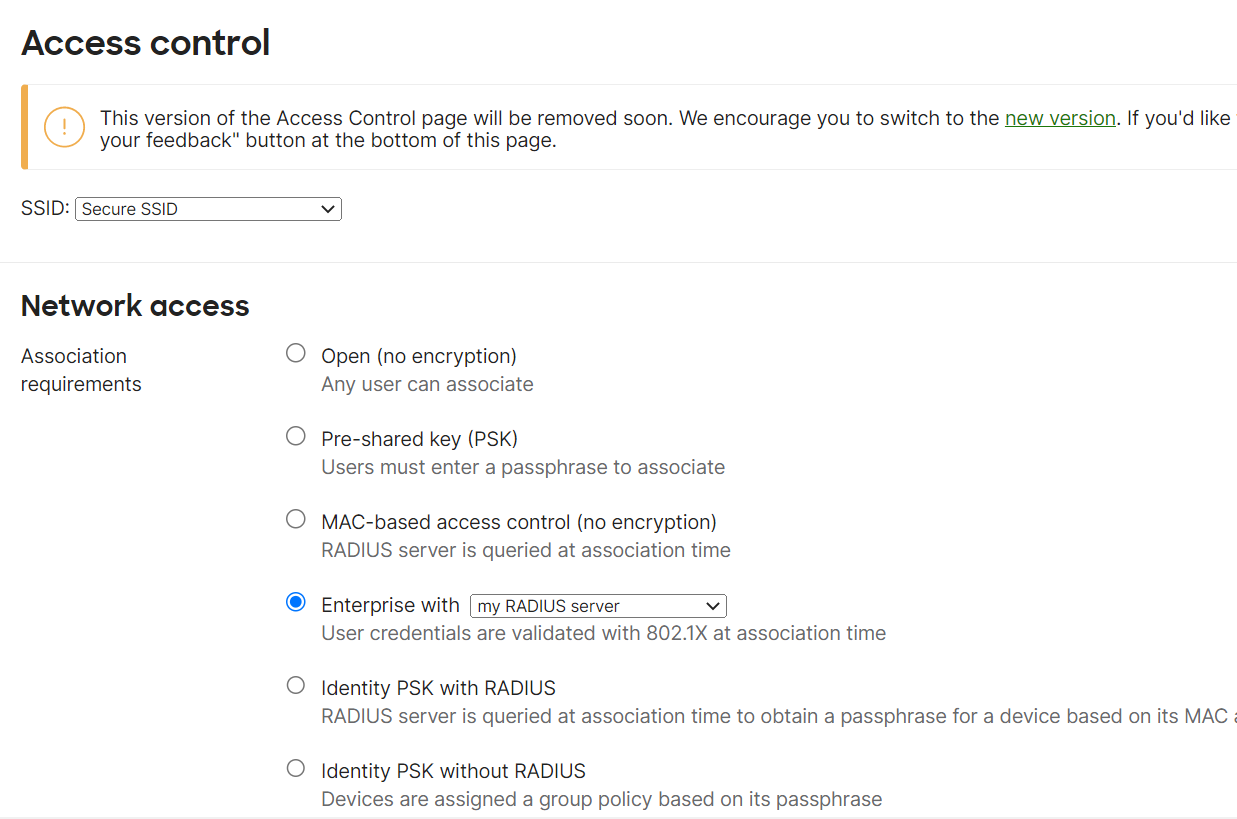
- Log in to the Meraki Dashboard.
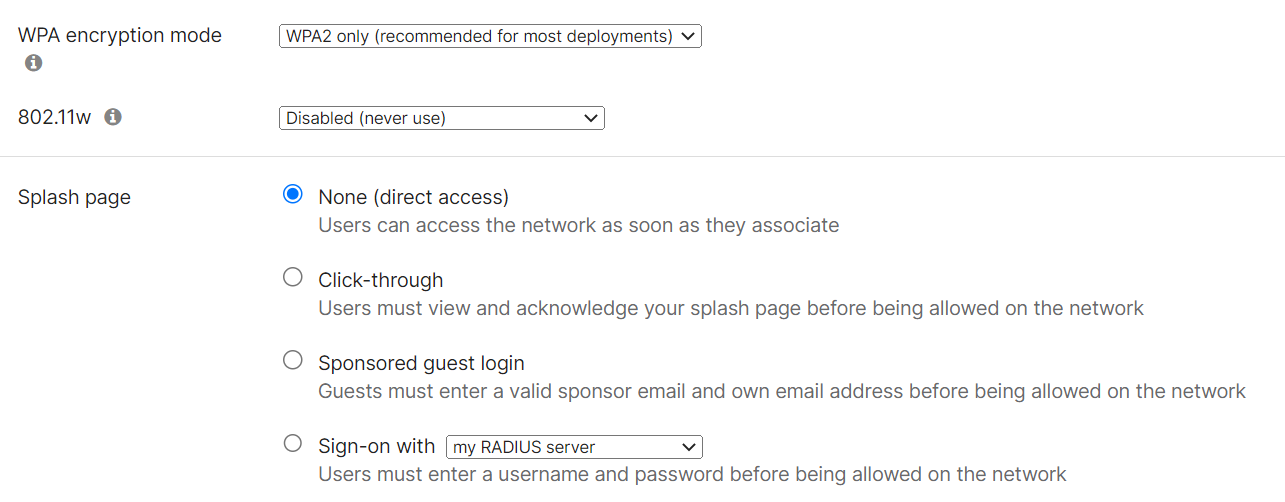
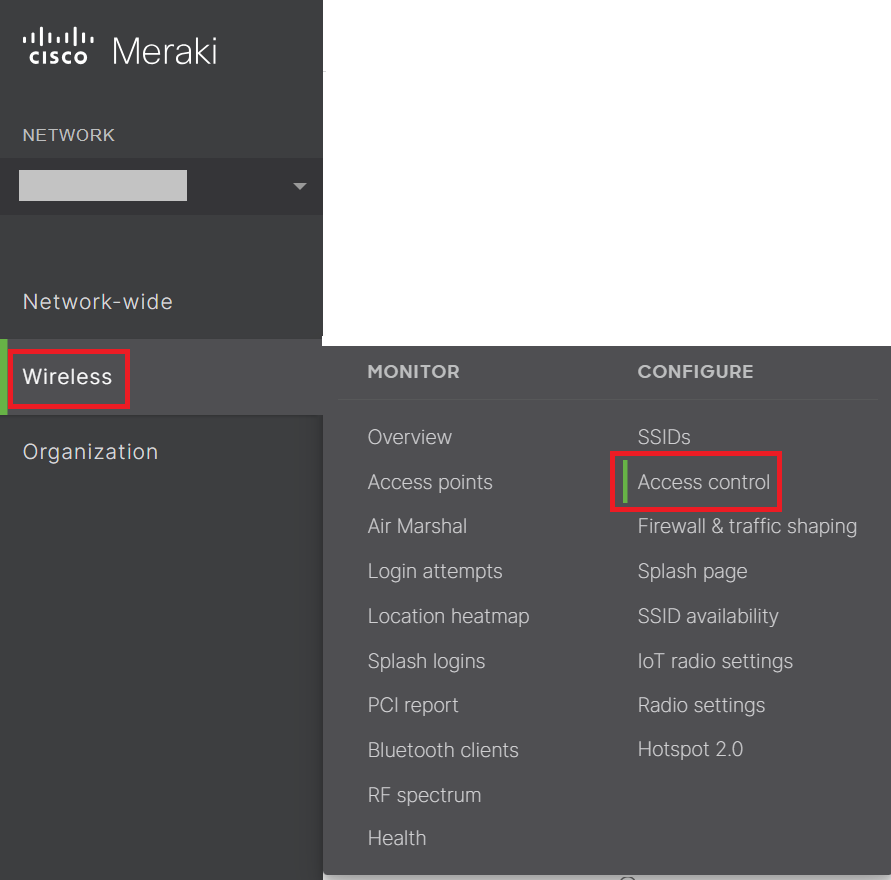
- Navigate to Wireless > Access control.
- In the Network access section, for Association requirements, from the Enterprise with drop-down list, select my RADIUS server.
- From the WPA encryption mode drop-down list, select WPA2 only (recommended for most deployments).
- Under Splash page, select None (direct access).
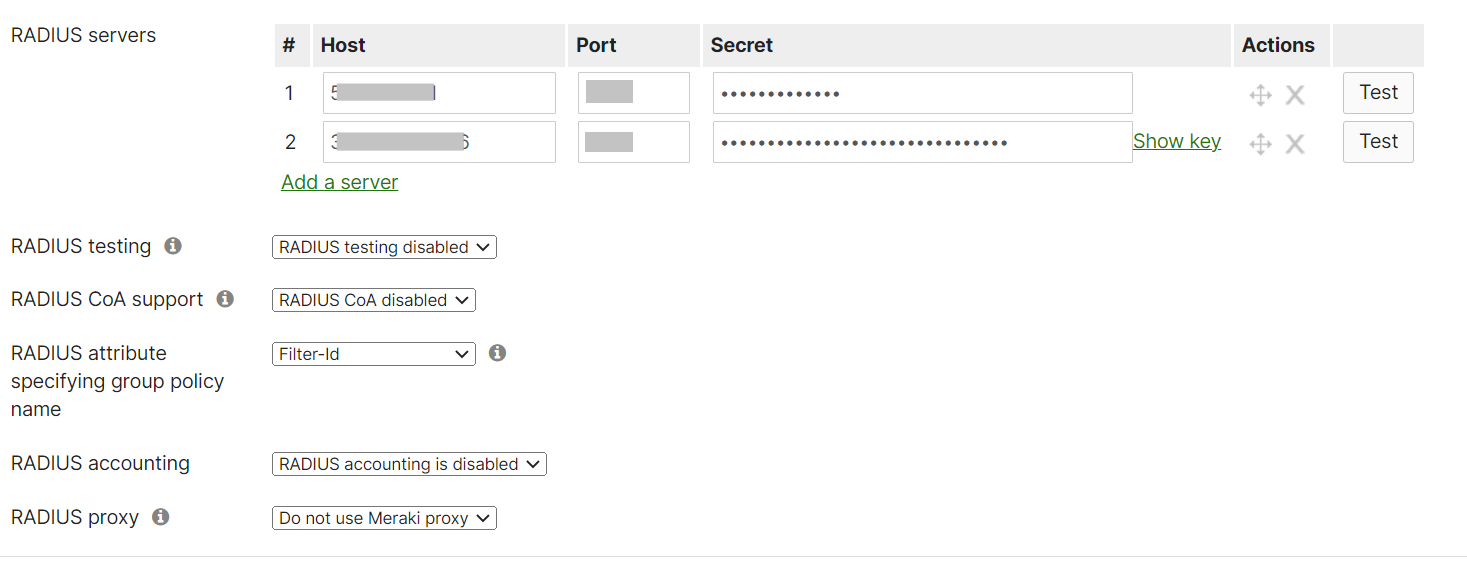
- In the RADIUS servers section, click Add a server.
- From the JoinNow Management Portal (navigate to RADIUS > RADIUS Configuration), copy the Primary IP Address, Authentication Port, and Shared Secret and paste them in the Host, Port, and Secret fields in the Meraki.
- In the RADIUS servers section, click Add a server again.
- From the JoinNow Management Portal (navigate to RADIUS > RADIUS Configuration), copy the Secondary IP Address, Authentication Port and Shared Secret and paste them in the Host, Port, and Secret fields in the Meraki.
- Click Save Changes.
Configure Access Point to use Splash Page
Follow the below steps to configure the Access point.
- Log in to the Meraki Dashboard.
- Navigate to Wireless > Access Control.
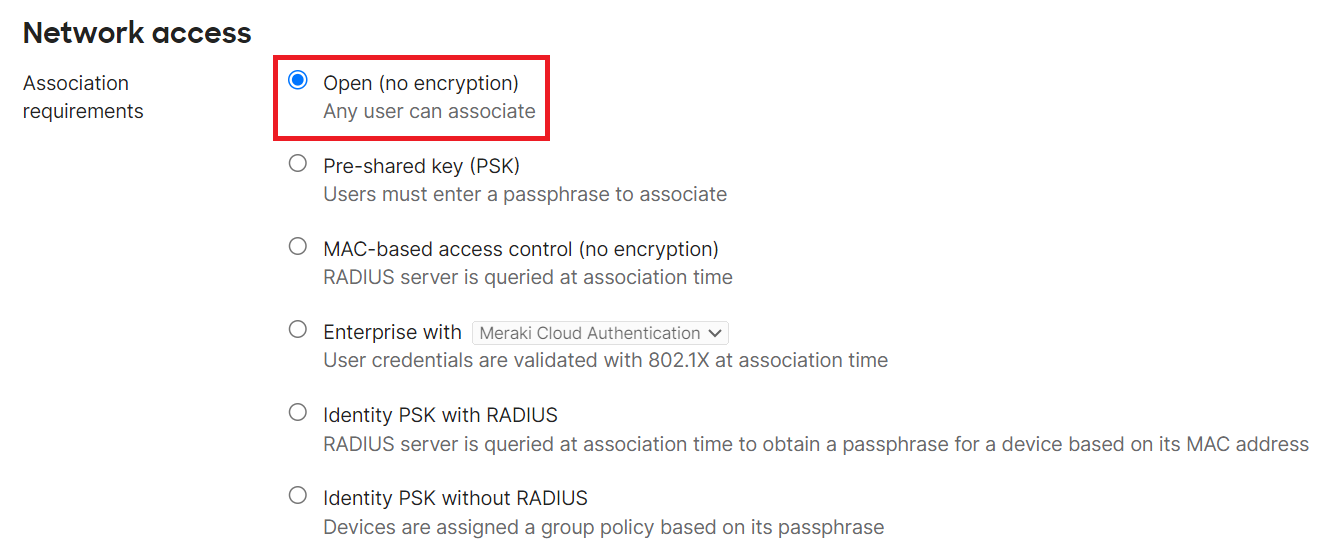
- Under Network access, in the Association requirements section, select Open (no encryption).
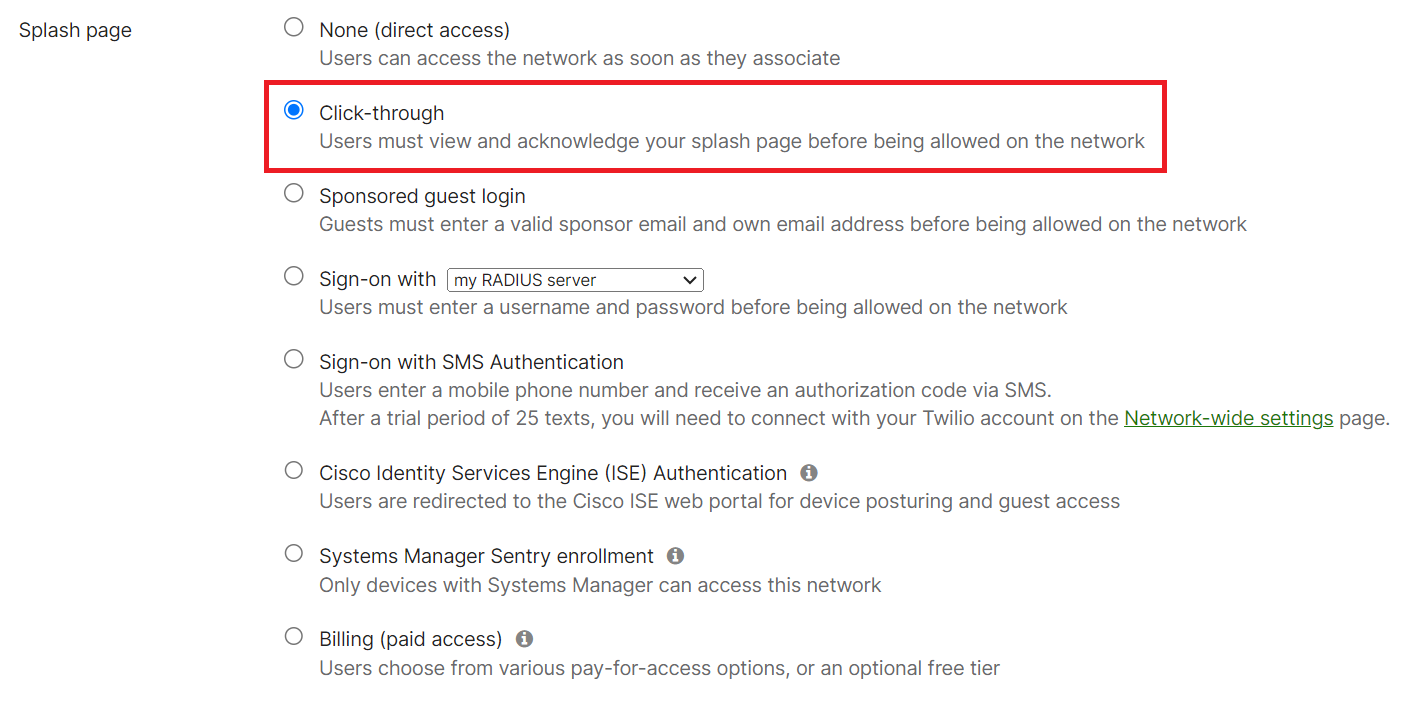
- Under Splash page, select Click-through.
This process redirects to the SecureW2 landing page.
Configuring Redirect to SecureW2 Landing Page
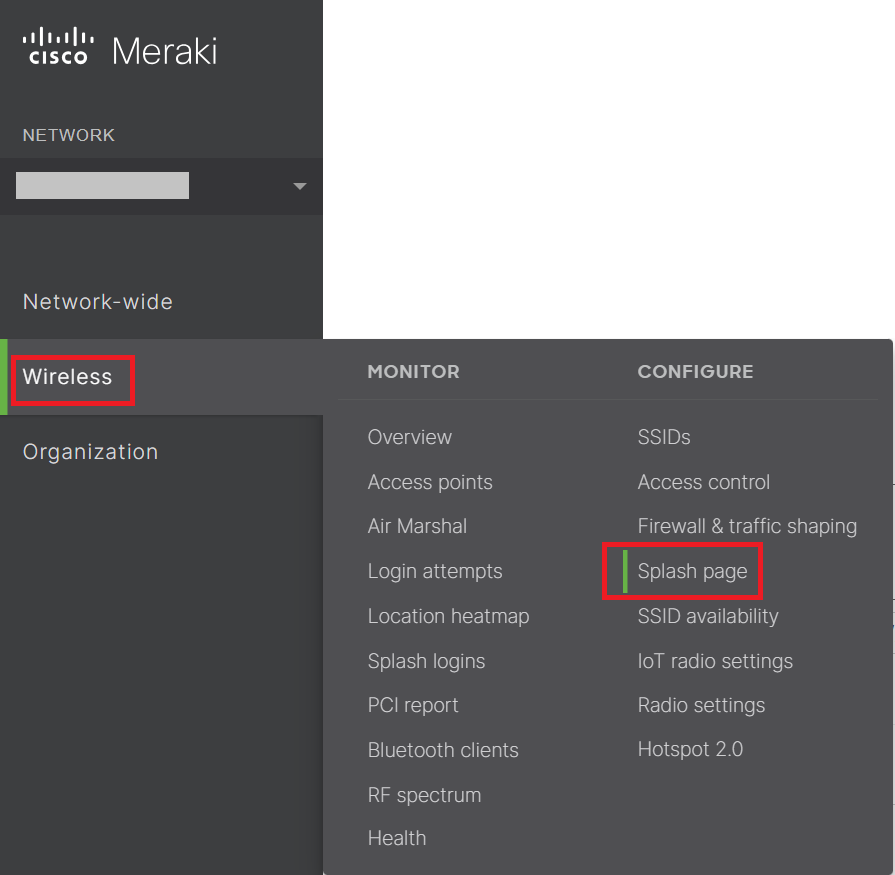
- Navigate to Wireless > Splash page.
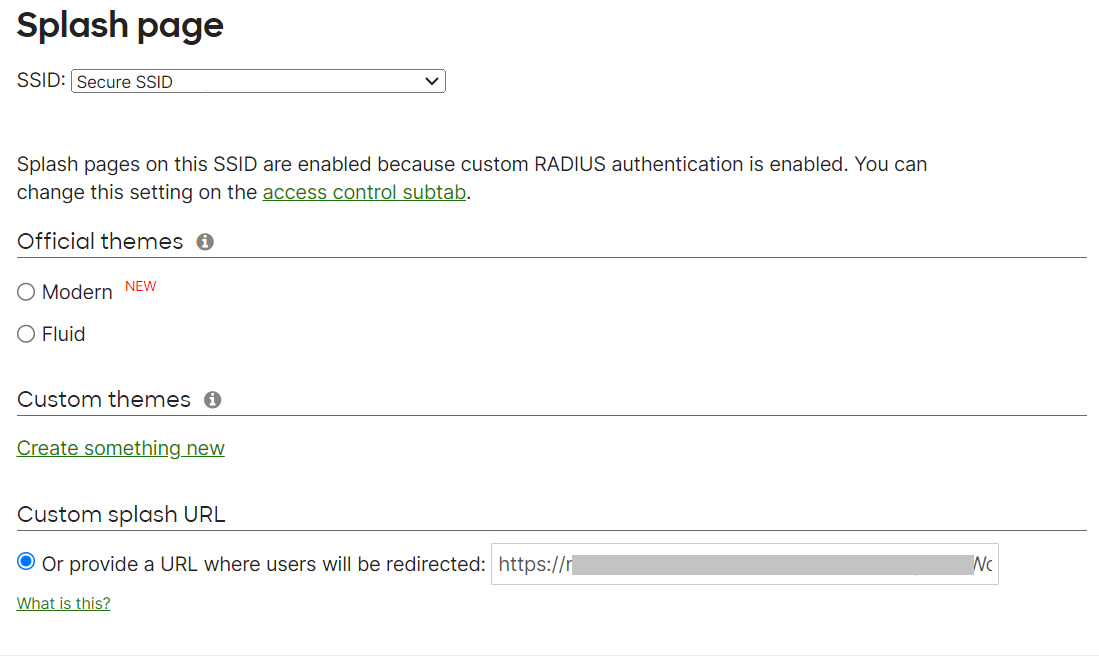
- Verify that the SSID field matches the SSID that you configured earlier (refer to the Configuring Secure SSID section).
- Under Custom splash URL, enter your network profile URL where the user will be redirected.
- Click Save changes.
Configuring Walled Garden
When implementing a BYOD system, it’s vital to keep corporate data and personal data separate and protected. A proven method has been the utilization of a walled garden. Instituting a walled garden keeps corporate data stored in a secure application that is separated from personal data. This creates insurance for the corporation that their sensitive data will not be breached.
For an Onboarding SSID, you need to allow onboarding-related resources. For example, the MultiOS solution uses an Android application to configure Android devices for WPA2-Enterprise, so we need to allow access to the Play Store on our Onboarding SSID.
Another example is the Apple CNA can get in the way of WPA2-Enterprise configuration. The CNA is prompted CNA from popping up.
We control what resources can be accessed on the Onboarding SSID by using a Walled Garden. It allows network administrators to control access to certain sites and applications, steering network users away from potentially harmful situations.
To configure the Walled Garden:
- Navigate to Wireless > Firewall & traffic shaping.
- Verify that the SSID field matches the SSID that you configured earlier (refer to the Configuring Secure SSID section).
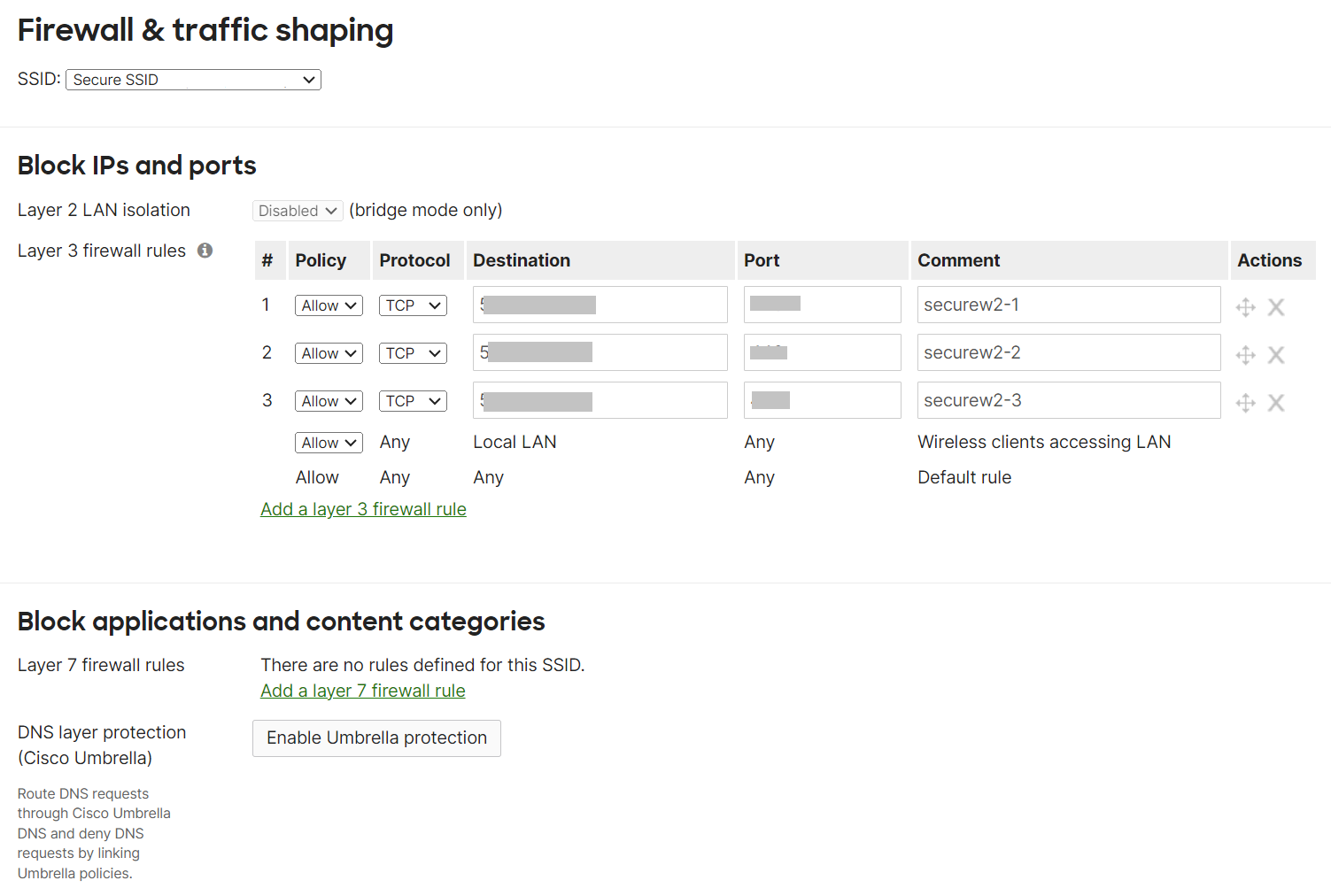
- Under Block IPs and ports, in the Layer 3 firewall rules section, click the Add a layer 3 firewall rule link and add a rule that Allow the firewall through to SecureW2 resources.
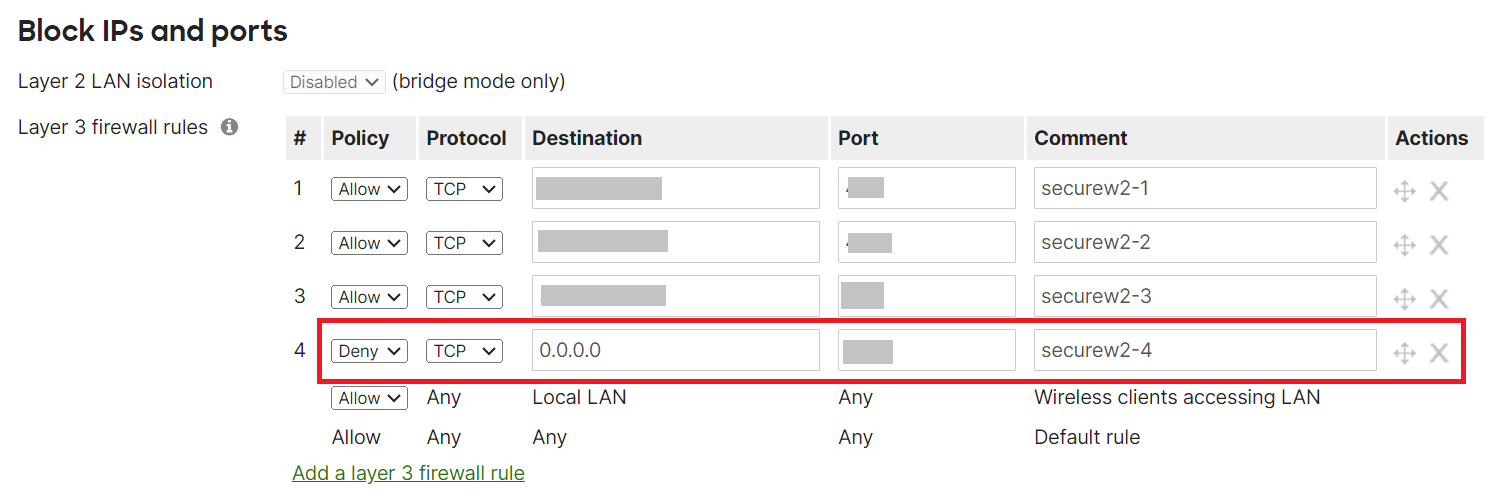
NOTE: To get the list of URLs, download the SecureW2 JoinNow Deployment Guide from the JoinNow Management Portal. To download the guide, navigate to General > Documentation. The SecureW2 JoinNow Deployment Guide is available under the JoinNow MultiOS tab. Scroll to the Firewall Rules section for the list of IPs that need to be added under the Layer 3 firewall rules. The SecureW2 JoinNow Deployment Guide also lists additional DNS and ALCs for Android Playstore, Apple CNAs, Microsoft SmartScreen, and so on. - Under the Layer 3 firewall rules, enter an additional rule with Deny as the Policy on the 0.0.0.0 IP address. This allows you to prevent abuse of the open SSID to access the Internet.
- Click Save Changes.
And that’s it, you’re on your way to a more secure wireless network! If you’re ready to get started, SecureW2 has affordable solutions for organizations of all shapes and sizes. Click here to learn more about our pricing.
Meraki is either registered trademarks or trademarks of Cisco Meraki in the United States and/or other countries. Other trademarks, logos and service marks used in this site are the property of SecureW2 or other third parties.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing