Introduction
802.1X and EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) combined provide safe authentication methods. Client devices (RADIUS supplicants) and a RADIUS authentication server validate each other’s identities by authenticating the signatures on the device and server certificates they exchange.
This authentication method uses a RADIUS server that interfaces with an external LDAP database. It also necessitates a system for installing certificates on the server and all supplicants, which may be accomplished using a Windows NPS (Network Policy Server) and a GPO (Group Policy Object) to issue computer certificates, as well as an 802.1X SSID client setup for wireless authorizing access.
In this article, we dig into the complexities of integrating EAP-TLS authentication with Microsoft Network Policy Server (NPS), illuminating the synergy between these technologies. Understanding and deploying EAP-TLS with NPS is critical for reinforcing network security architecture as organizations prioritize data protection and network access management.
Integration Process Overview
- Configure the WPA2-Enterprise network to authenticate using 802.1x certificates
- Connect the Microsoft NPS RADIUS to the secure network
- The RADIUS will authenticate and authorize users for network access by confirming their identity within the identity provider.
- Connect the PKI and download and install the Certificate Authorities (CA)
- Connect the Root and Intermediate CA’s to the RADIUS and secure network. As users enroll for network access, they will be distributed certificates from the connected CA.
To complete this setup, you will need to have configured:
- A SecureW2 Network Profile
- A Microsoft NPS RADIUS Server
- An Identity Provider
What is EAP-TLS Authentication?
EAP-TLS stands for Extensible Authentication Protocol-Transport Layer Security. While the name is undoubtedly a mouthful, the purpose of EAP-TLS is to improve network security through digital authentication. EAP-TLS secures your network, enabling only authorized users to access company data, resources, and applications.
EAP-TLS often allows the use of X.509 digital authentication certificates, which are more secure than the alternative of passwords. These digital authentication certificates can be used by businesses to enable single sign-on (SSO) over a VPN or other network devices.
How Does EAP-TLS Work?
As previously stated, EAP-TLS is a certificate-based mutual authentication method, which means that certificates are required by both the client and the server for effective authentication. Once those certificates have been found, EAP-TLS will generate session-based keys for each side to complete the login.
The steps are as follows:
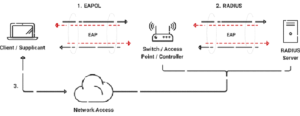
- A user seeks network access control via a wireless access point (AP) or authenticator app.
- The AP inquires about the user’s identification.When the AP receives user information, it sends it to an authentication server.
- The RADIUS authentication server asks the AP for identification verification.
- The AP obtains validation and transmits it to the RADIUS authentication server.
- The user connects to the network directly.
How Secure is EAP-TLS?
Because of the mutual authentication requirement between clients and the RADIUS server, EAP-TLS is an especially sound technique to safeguard 802.1X networks.
Overall, EAP-TLS minimizes the probability of cybercriminal activities, particularly man-in-the-middle attacks. In those attacks, scammers spoof and authenticate into bogus authorizing access points, allowing them to steal victims’ credentials rapidly. Over-the-air attacks are almost difficult since mutual authentication requires users to authenticate their identities.
Configure the Secure Network for 802.1x Certificates
To configure a secure network for 802.1x certificates, a solid basis for user authentication, authorization and accounting must be established. This process guarantees a secure and efficient network environment by capitalizing on the complexities of certificate authentication.
In this section, we’ll explain how you can start configuring EAP-TLS on your NPS Windows Server operating systems. We’ll also walk through how to ensure you no longer use insecure authentication methods on NPS to ensure greater network access protection.
- Go to Windows > Run > MMC
- In the Console, navigate to File > Add/Remove Snap-in
- In the Add/Remove Snap-in window, select Network Policy Server from the Available snap-ins, and click Add
- In the Select Computer window, select Local Computer, and click OK
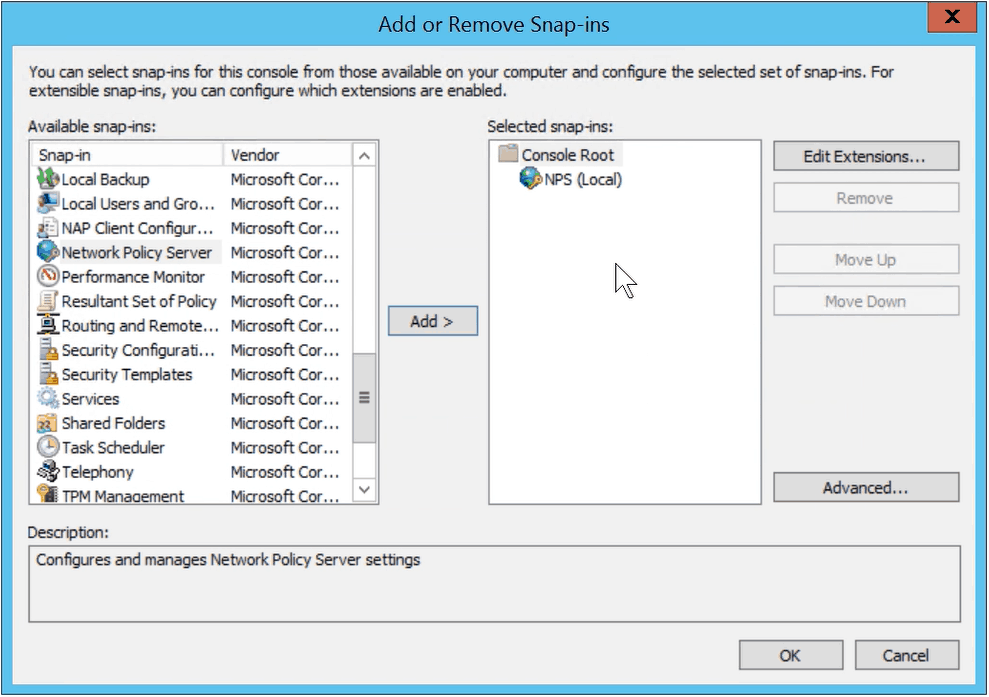
- In the Add/Remove Snap-in window, click OK
- In the Console, navigate to NPS (Local) > Policies > Network Policies
- In the Actions pane on the right, click New under Network Policies and the New Network Policy wizard will appear
- In the Specify Network Policy Name and Connection Type page, enter the Policy Name and click Next
- In the Specify Conditions page, click Add and the Select condition page appears
- Select NAS Port Type, and click Add, and the NAS Port Type window appears
- From the Common 802.1X connection tunnel types section, select Wireless – IEEE 802.1, and click OK
- The condition gets added to the Specify Conditions page
- Click Next and the Configure Authentication Methods window appears
- Under EAP Types, click Add and the Add EAP window appears
- Select Microsoft Smart Card or other certificate, and click OK
- De-select all the other check boxes under Less secure authentication methods and click Next
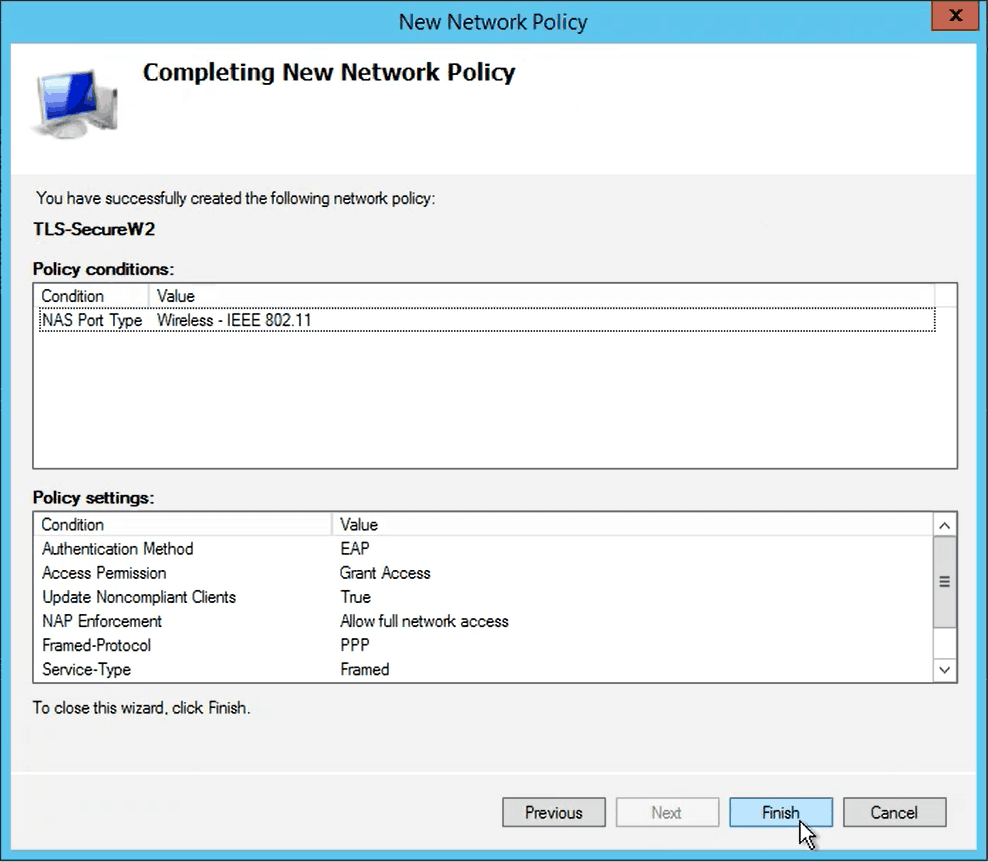
- In the Configure Constraints window, click Next
- In the Configure Settings window, click Next
- In the Completing New Network Policy window, click Finish
Connecting the Microsoft Network Policy Server RADIUS Client
The link between the Microsoft Network Policy Server (NPS) RADIUS client and the larger network environment is crucial to maintaining strong authentication and network access control. In this section, we’ll walk you through connecting RADIUS clients to your NPS Windows Server operating systems.
- Go to Windows > Run > MMC
- In the Console, navigate to NPS (Local) > RADIUS Clients and Servers > RADIUS Clients
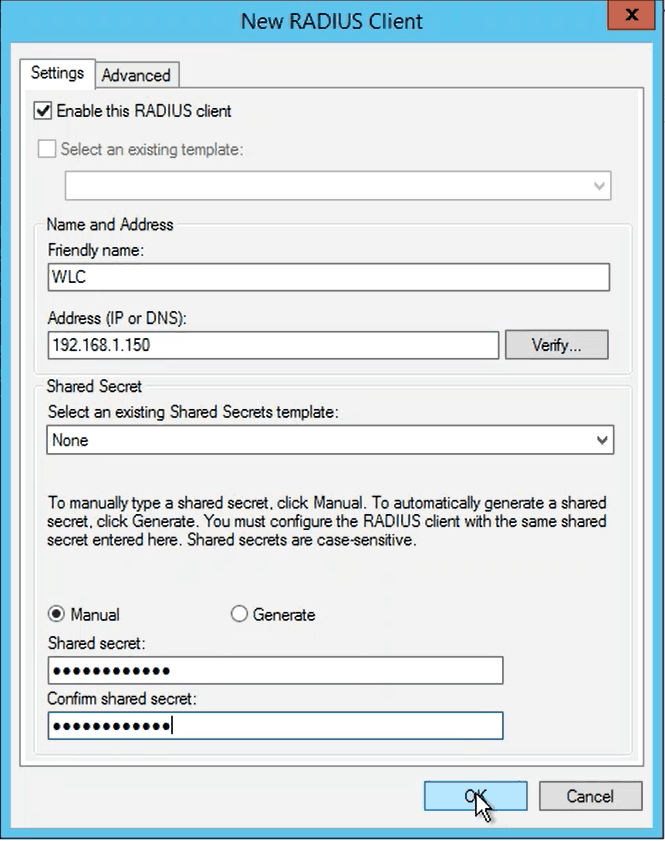
- In the Actions pane on the right, click New RADIUS Clients and the New RADIUS Client window appears
- Enter a Name and the IP address in the Friendly name and Address (IP or DNS) fields, respectively
- Enter the shared secret in the Shared secret and Confirm shared secret fields, and click OK
Downloading the Root and Intermediate CA from SecureW2
- Go to the SecureW2 JoinNow MultiOS and Connector Management Portal
- Navigate to PKI Management > Certificate Authorities
- Download both the Root and Intermediate CAs for the organization
Installing the Root and Intermediate Certificates
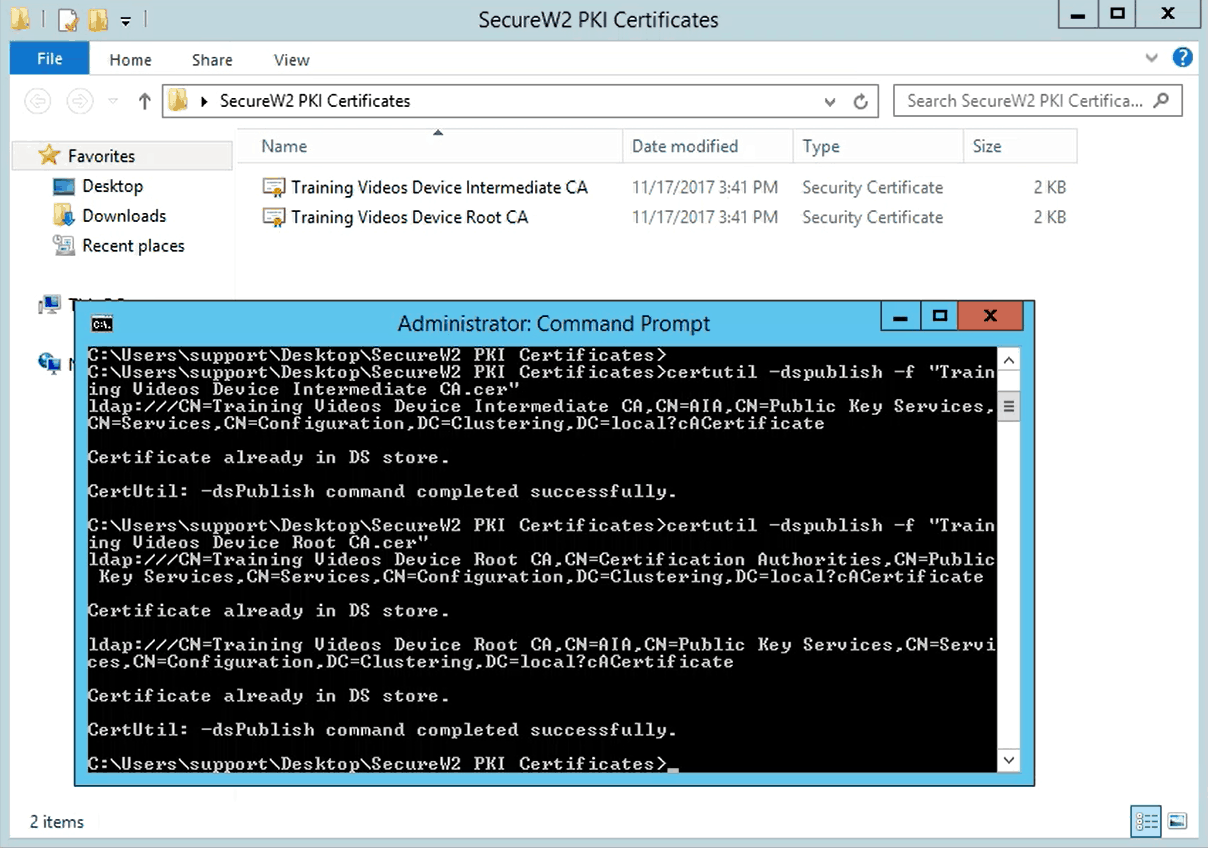
- Go to your server where you want to install your the certificates
- Go to Windows > Run > CMD and go to the folder where you have saved your certificates
- To install the certificates, run the following command consecutively for both the certificates:
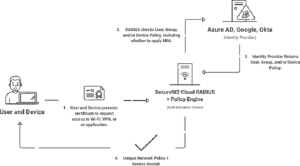
Move Past On-Premise NPS Windows Server Solutions to Cloud-Based & Passwordless RADIUS Servers
NPS can be used to accomplish passwordless authentication, but its on-premise architecture requires duplication at each location, which adds to the expense of organization-wide adoption. Organizations striving for cost-effectiveness and scalability must overcome the bind to on-premise technology. This is where Cloud RADIUS from SecureW2 proves to be a strong solution.
In addition to enabling certificate-based RADIUS authentication, cloud RADIUS removes the requirement for duplication of on-premise network infrastructure. Organizations can get the required passwordless security by avoiding the high expenses linked to extensive on-premise duplication.
Moreover, Cloud RADIUS guarantees seamless integration with existing infrastructure, offering a simple transition for enterprises looking for improved authentication capabilities. However, we also provide an alternative with our vendor-neutral managed PKI for users not ready to go straight to Cloud RADIUS. It easily connects with NPS, giving businesses an adaptable option to improve existing authentication procedures and preparing them for a future move to a passwordless, cloud-based platform.
Contact us to learn how SecureW2 might help your organization’s security system improve the security of its network infrastructure with certificate-driven security.
Microsoft Network Policy Server is either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. Other trademarks, logos, and service marks used on this site are the property of SecureW2 or other third parties.
Microsoft NPS is either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Other trademarks, logos and service marks used in this site are the property of SecureW2 or other third parties.