Key Points
- Conventional credentials-based authentication protocols, such as PEAP-MSCHAPv2 and EAP-TTLS/PAP, are susceptible to various over-the-air attacks, such as MITM, and usually take a lot more time to communicate.
- These drawbacks can be easily eliminated by using EAP-TLS, the most secure protocol that relies on mutual server certificate validation. In this protocol, both the client and server present digital certificates to verify each other identities.
- EAP-TLS uses public-private key encryption and usually carries out authentication in 12 steps, which is twice as fast as credential-based protocols.
- SecureW2 has helped over a thousand organizations adopt EAP-TLS by providing managed cloud RADIUS and PKI services that integrate directly with cloud identity services.
Extensible Authentication Protocol–Transport Layer Security (EAP-TLS) is an IETF open standard defined in RFC 5216. More colloquially, EAP-TLS is the authentication protocol most commonly deployed on WPA2-Enterprise networks to enable the use of X.509 digital certificates for authentication.
EAP-TLS is considered the gold standard for network authentication security, but despite being universally recognized as ultra-secure, it’s still not widely implemented. That’s largely because EAP-TLS was developed before the industry had the mature device onboarding solutions necessary for smooth device configuration at an enterprise scale.
Fortunately, EAP-TLS is much more viable with automated device onboarding solutions for BYOD and MDM, like SecureW2’s JoinNow MultiConnector. Streamlined onboarding makes configuration a simple task, making premium Wi-Fi security viable for a larger proportion of organizations.
What Is EAP-TLS and How Does it Work?
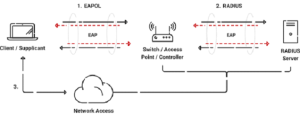
EAP-TLS is a very secure and commonly used authentication protocol in networking settings. In a nutshell, it uses digital certificates for both devices and servers to verify each other’s identities.
EAP-TLS relies on the strength of public key cryptography, further enhancing its security posture. Additionally, the protocol ensures the confidentiality and integrity of data transmitted between the client and the server by employing encryption techniques.
Certificates are created and function through a concept called asymmetric cryptography. EAP-TLS is often used in business settings, safe Wi-Fi networks, and virtual private networks (VPNs) to protect data and confirm identities.
In EAP-TLS, the authentication approach is made up of several important steps, each of which helps create a secure connection:
⦁ Initiation: The client requests the server to start EAP TLS authentication.
⦁ Server Hello and Certificate: The server answers with “Server Hello” and its SSL certificate. The server’s SSL certificate includes its public key and other data.
⦁ Client Certificate Request: The server requests the client’s authentication certificate. The server sends a “Client Certificate Request” message if it needs the client’s certificate.
⦁ Key Exchange: Clients transmit SSL certificates to servers. The client’s certificate contains its public key and other information. After sending its certificate, the client and server may exchange keys to create a shared secret.
⦁ Server Verification: The server checks the client certificate. It validates the client’s certificate and may examine the CRL or certificate chain.
⦁ Client Verification: The client checks the server’s certificate similarly to the server’s. The client verifies the server’s certificate.
⦁ Session Key Generation: After authenticating, the client and server produce a session key or set of keys to encrypt data.
⦁ Secure Communication: Once the session key is set, the client and server may use TLS to transmit data securely.
Is EAP-TLS Secure?
EAP-TLS is widely regarded as the most secure authentication protocol for 802.1X networks. The requirement for mutual certificate authentication has kept the protocol relevant and dominant for over 15 years.
One of the primary security benefits of EAP-TLS networks is the ability to perform server certificate validation. This technique renders your users all but invulnerable to common over-the-air attacks like the notorious man-in-the-middle attack.
Those hacks usually rely on spoofed access points (AP) to fool users’ devices into automatically attempting to authenticate to the fake AP. The device will automatically submit real credentials without the user’s knowledge, allowing the hacker to farm credentials with little effort.
Server certificate validation requires both the client and the server to validate their identity, so a device configured for EAP-TLS authentication (and thus server certificate validation) won’t ever mistake a spoofed AP for the real one.
That mutual authentication requirement is fundamental to all certificate-based authentication, the source of EAP-TLS’s strength. Certificates perform similar roles in secure applications like S/MIME and digital signature signing.
Benefits of EAP-TLS
EAP-TLS presents many advantageous features that render it highly favored among organizations aiming to fortify their security infrastructure while ensuring a seamless user journey. Let’s take a look at the various benefits of EAP-TLS.
Unparalleled Authentication Security
EAP-TLS is one of the most reliable options when comparing authentication security protocols. When X.509 digital certificates are encrypted using state-of-the-art cryptographic methods like elliptic curve cryptography (ECC), the protocol provides the highest level of security possible.
Due to its elaborate security mechanism, EAP-TLS is very resistant to eavesdropping, man-in-the-middle attacks, and other forms of network intrusion. Businesses may set up a very safe communication channel using digital certificates for robust encryption, protecting the privacy and security of any information sent over the network.
Enhanced Network Visibility and Access Control
EAP-TLS is an alternative to password-based authentication that uses digital certificates bound to individual users or devices. This feature greatly improves the network’s visibility, letting admins easily recognize and authenticate connected devices.
Risks connected with unauthorized access and possible security breaches may be mitigated if organizations know that only authenticated devices with valid certificates are permitted access. This function helps to improve the organization’s security by making the network architecture stronger and easier to manage.
EAP-TLS authentication, which uses digital certificates, improves network visibility and access control. Certificates provide a wealth of context information, such as user types, device ownership, device specifications, authorization history, user roles, and current situation. This information improves network security and administration.
Improved User Experience and Reduced Overhead
When opposed to credential-based networks, EAP-TLS provides a better user experience. Users are freed from the stress of memorizing and storing complicated passwords thanks to certificates fundamentally attached to devices and the ability to authenticate automatically.
IT departments can save time and effort by dealing with common authentication problems like forgotten passwords and needing to change them often. Administrators control a certificate’s validity time, allowing them to manage re-verification cycles and guaranteeing safe network access.
Superior Security Over Password-based Systems
Password reuse is a major security concern in password-based systems since it increases the likelihood of unauthorized access and data breaches. EAP-TLS, on the other hand, uses digital certificates to prevent certificate duplication and reuse, making it impossible to utilize stolen credentials in any way. EAP-TLS provides an enhanced security framework to protect sensitive data and resources by reducing the risks associated with password theft and reuse, strengthening the network against sophisticated cyber assaults.
Incorporating EAP-TLS into a company’s network infrastructure can increase security, enhance user experiences, and simplify administrative procedures, all of which contribute to a more secure and resilient networking environment better suited to long-term business operations and data protection.
Does EAP-TLS Require Certificates?
Technically, the standard does not mandate using X.509 digital certificates. However, the reality is that omitting certificates would negate the security benefits of the protocol and render much of the infrastructure pointless.
Since EAP-TLS requires mutual authentication, you’re unlikely to find an implementation that does not require client-side certificates.
⦁ EAP Tunneled Transport Layer Security (EAP-TTLS)
⦁ EAP Pre-Shared Key (EAP-PSK)
⦁ EAP Password (EAP-PWD)
⦁ Lightweight Extensible Authentication Protocol (LEAP)
⦁ EAP Encrypted Key Exchange (EAP-EKE)
⦁ EAP Transport Layer Security (EAP-TLS)
⦁ EAP-MD5
⦁ EAP Protected One-Time Password (EAP-POTP)
⦁ EAP Internet Key Exchange v. 2 (EAP-IKEv2)
⦁ EAP Authentication and Key Agreement (EAP-AKA)
⦁ EAP Authentication and Key Agreement Prime (EAP-AKA’)
⦁ EAP Flexible Authentication via Secure Tunneling (EAP-FAST)
⦁ Tunnel Extensible Authentication Protocol (TEAP)
⦁ EAP Subscriber Identity Module (EAP-SIM)
⦁ EAP Generic Token Card (EAP-GTC)
⦁ Nimble out-of-band authentication for EAP (EAP-NOOB)
EAP-TLS Compared
Not all EAP methods are created equally. It could be a critical mistake to assume that an authentication protocol is secure because it is ubiquitous.
Many legacy systems still use outdated wireless security paradigms, including authentication protocols with known vulnerabilities. Unfortunately, networking with some of these systems (particularly on-premise networks) can require you to use special infrastructure to bridge the gap or to sacrifice the security and convenience of contemporary authentication solutions.

Now, we’ll compare EAP-TLS to the other two most commonly used authentication protocols for 802.1X networks.
What’s the Difference Between PEAP and EAP-TLS?
PEAP is an EAP protocol, even though it breaks the naming convention a little bit. The ‘P’ in ‘PEAP’ stands for “Protected” (Extensible Authentication Protocol). PEAP was the product of a collaborative effort between Cisco, Microsoft, and RSA, meant to add intrinsic protection to EAP, which relies on protected communications by default.
PEAP itself technically does not define a particular method; rather, it contains instructions for chaining together EAP protocols for additional security. In practice, almost every PEAP implementation is PEAP-MSCHAPv2 due to its inclusion in ubiquitous Microsoft environments.
Unfortunately, PEAP is highly susceptible to man-in-the-middle attacks and has been for more than a decade now. This is particularly crippling in an era when hackers are taking the time to be more hands-on. It’s not difficult to imagine a dedicated hacker spoofing your office access point from a van parked outside your house, a scenario made all the more likely as C-suite level executives are certainly working from home during the pandemic.
EAP-TLS entirely circumvents this issue by using server certificate validation. Even in the scenario described above, it’s relatively simple to use a VPN to secure a connection to your office RADIUS server for remote authentication.
Want to learn more about using a VPN for remote authentication? Check out SecureW2’s remote authentication solution for VPN.
What’s the Difference Between EAP-TTLS and EAP-TLS?
The primary difference between EAP-TTLS and EAP-TLS is that the former only requires server-side certificates rather than the mutual certificate authentication that characterizes EAP-TLS.
To compensate, TTLS uses a tunnel (hence “Tunneled” Transport Layer Security). It’s essentially an SSL wrapper encapsulating the standard EAP message. It does not encrypt the message, however.
Unfortunately, EAP-TTLS communicates everything (including credentials) in clear text. And, since TTLS does not use server certificate validation, it’s particularly susceptible to being intercepted in over-the-air attacks — which completely bypass the tunnel and deliver credentials in clear text directly into the waiting hands of a hacker.
What Is Required for EAP-TLS Authentication?
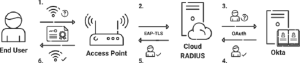
The minimum required infrastructure for EAP-TLS authentication is:
⦁ AAA/RADIUS
⦁ User Directory
⦁ 802.1X-Capable Access Point and Controller
⦁ Public Key Infrastructure (PKI)
Of course, that short list makes it look much simpler than it is. The PKI alone is composed of more than a dozen different components, each completely vital to the process of configuring, provisioning, revoking, and otherwise managing digital certificates.
The provisioning and onboarding of certificates is indeed a crucial component. Understanding the essential components, such as the Certificate Authority (CA), Registration Authority (RA), certificate templates, Certificate Revocation List (CRL), key preservation, and recovery, is required to configure an effective PKI.
Furthermore, developing an approach for distributing and maintaining certificates across several devices is critical. Depending on the size and complexity of the network, this may involve interaction with device management systems, customizing network policies, automatic enrollment methods, or manual distribution techniques.
There are ample open-source or otherwise free resources to cobble together a functional 802.1X network with EAP-TLS, such as FreeRADIUS and the Active Directory extensions NPS and AD CS.
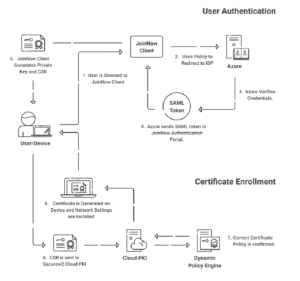
SecureW2’s JoinNow Connector PKI is cloud-based, giving it a significant edge over on-premises alternatives such as FreeRADIUS and NPS. Because of the cloud-based architecture, organizations can handle their certificate-based authentication from any location.
The graphic below depicts the JoinNow Connector PKI’s efficient flow, demonstrating how it automates the certificate management process. This cloud-based strategy guarantees that organizations can securely adopt EAP-TLS authentication without being constrained by on-premises infrastructure, increasing flexibility and operational efficiency.
Empowering Secure EAP-TLS Adoption With SecureW2’s Solutions
SecureW2’s Managed PKI is the foundation for enabling secure EAP-TLS authentication, allowing organizations to reap the security benefits associated with certificate-based authentication without the difficulties of constructing their own PKI infrastructure.
SecureW2 offers JoinNow MultiOS for faster onboarding, making setup easier for managed and unmanaged devices. This speeds up the distribution process. This approach reduces the possibility of misconfigurations while ensuring cross-platform compatibility and user self-service options.
SecureW2’s Cloud RADIUS also works with the EAP-TLS framework to strengthen it by allowing digital certificate-based authentication, better policy enforcement, and strong user and device context identification. It works well with popular cloud identity providers like Okta and Azure Active Directory, making the login process safe and quick.