Introduction
SecureW2’s vendor neutral solution provides all the tools needed to integrate certificate-based 802.1xauthentication to your Extreme RADIUS-supported network. Our certificate onboarding solution empowers users to enroll for certificates within minutes and be connected to the secure network for the life of the certificate.
Once equipped, the network is then protected from damaging over-the-air attacks that take advantage of weak credential security. The ExtremeControl RADIUS can also be equipped with a server certificate to enable server certificate validation and ensure users do not unknowingly connect to a hostile SSID.
The certificate solution can be easily customized to authenticate BYOD and managed devices. The management portal provides clear identity context of approved network users. The rapid deployment and unmatched security of ExtremeControl RADIUS and SeucreW2’s certificate solutions provides peace of mind and a highly efficient secure wireless network.
Integration Process Overview
- Integrate SecureW2’s PKI solutions with ExtremeControl RADIUS
- SecureW2’s cloud PKI solution provides all the necessary tools to implement certificate-based authentication. This vendor neutral solution can be easily integrated with existing infrastructure and equip your network devices with certificates with ease.
- Add your Identity Provider to the ExtremeControl RADIUS
- Our certificate solution integrates with IDP from all major vendors. Once a user is equipped with a certificate, the certificate is tied to the user’s identity and device’s identity. The certificate cannot be removed or transferred and automatically expires at a pre-determined date.
- Configure ExtremeControl RADIUS to Authenticate Requests from SecureW2 Certificates
- Certificate authentication protects against over-the-air attacks that target credential-based networks. Because certificates utilize public-private key encryption, they are sent over the air in a format that is unreadable. Additionally, enabling server certificate validation guarantees that users only send their certificates to the ExtremeControl RADIUS.
- Connect SecureW2’s CRL
- Although certificates are configured to expire at a pre-determined date, situations arise where they must be revoked prematurely. SecureW2’s CRL allows admins to indicate that a specific user’s certificate should not be authenticated. If that user attempts to connect, the authentication process will stop when checking it against the CRL, barring their connection.
- Configure Authentication Rules to authenticate 802.1x certificates with an LDAP authentication method
- Once configured, the network is ready for enrollment. Users will be able to follow the onboarding client and be equipped with a certificate in minutes that promises sustained network connection for life.
To complete this setup, you will need to have configured:
- An ExtremeControl RADIUS Server
- A SecureW2 Network Profile
- An Identity Provider
Configuring ExtremeControl for Identity Lookup
- On the Extreme dashboard, select Control > Access Control > Configurations > Default > Rules
- Click Add to add a new rule
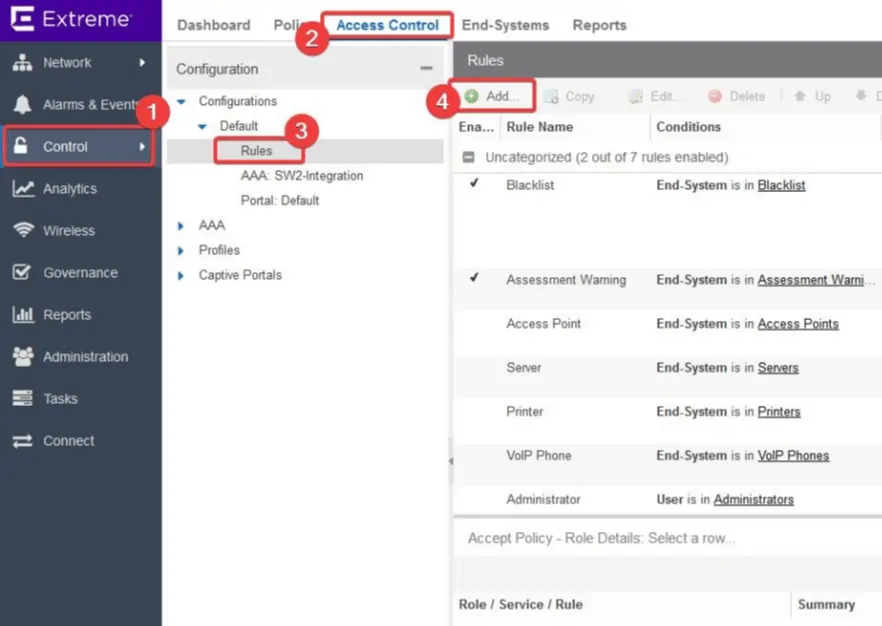
- Enable the Rule Enabled option
- Navigate to Conditions > User Group
- From the drop-down menu, select New
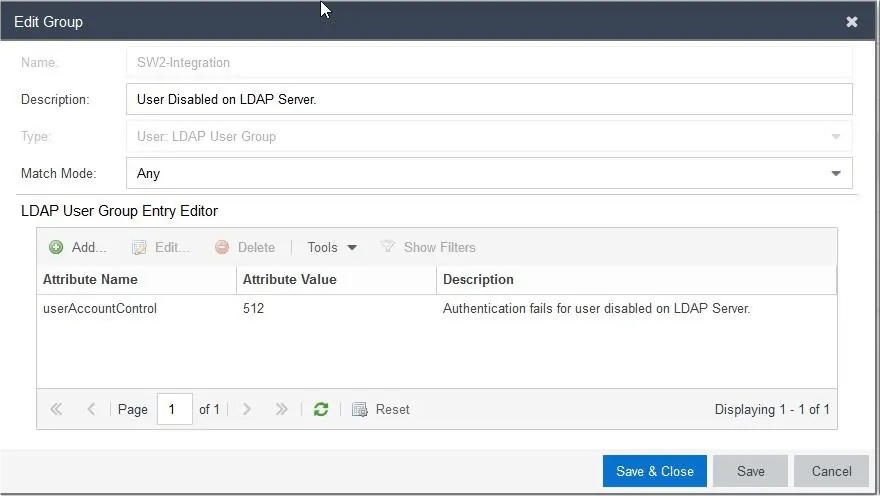
- Enter a Name and Description
- Select Type as User: LDAP User Group
- Click Create
- In the next window, select Match Mode as Any
- Under LDAP User Group Entry Editor, enter the following values:
- Enter Attribute Name as userAccountControl
- Enter Attribute Value as 512
- From the drop-down menu, select the LDAP Server configured
- Click Update
Configuring ExtremeControl with AAA SecureW2 CRL
- Select Control > Access Control > AAA
- Click Add
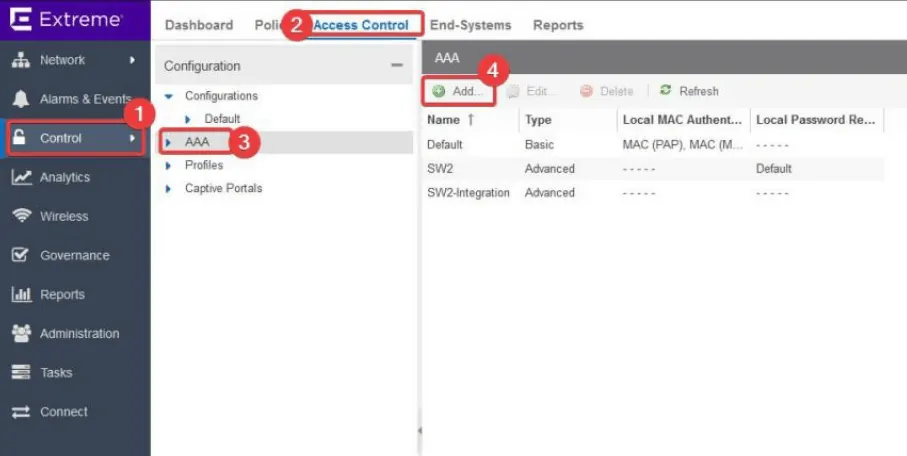
- Enable Advanced Configuration and add a name for your reference
- De-select the option Authenticate Requests Locally for
Authenticate with SecureW2 Certificates
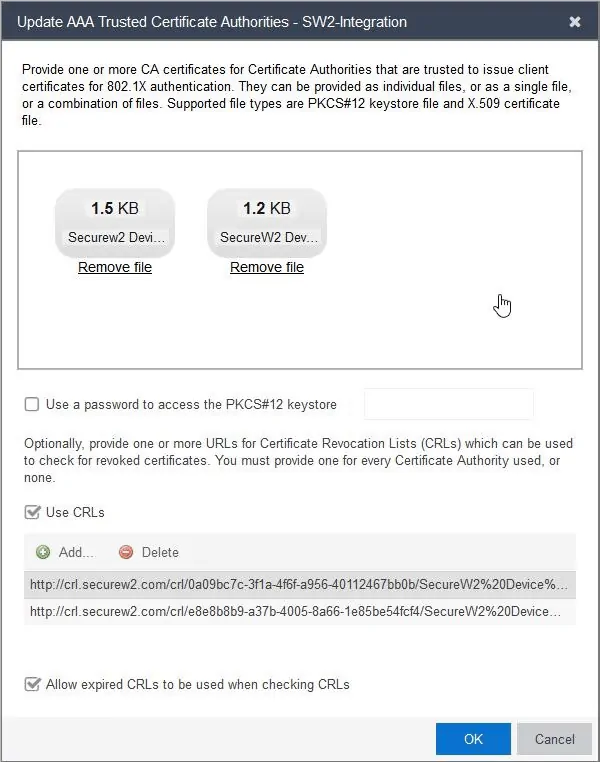
- Click on Update Trusted Authorities to open the Update AAA Trusted Certificate Authorities window
- In the Drop files here or click to browse section, the SecureW2 Root and Intermediate certificates need to be selected
- Select the Use CRLs option
- Click on Add and enter the Base CRL of SecureW2 Root certificate
- Repeat this step and enter the Base CRL of SecureW2 Intermediate certificate
- If you want to allow your Extreme Access Control to authenticate end-users when the Extreme Access Control is unable to reach the SecureW2 servers to validate the status of user-certificates, enable the option Allow expired CRLs to be used when checking CRLs
- Click Ok
Update Authentication Method to 802.1x
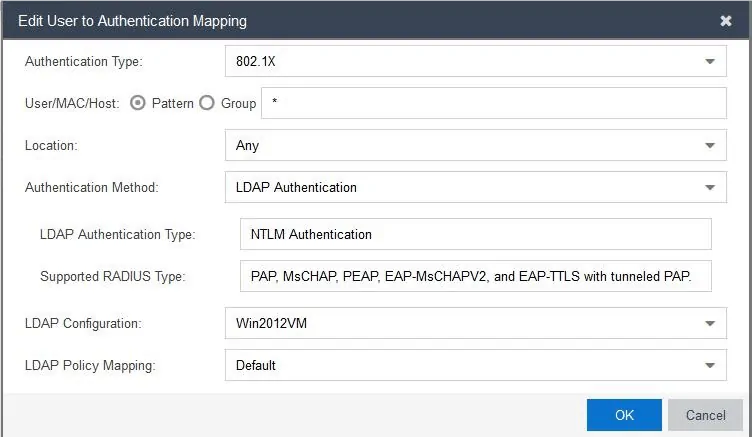
- Under Authentication Rules, click Add to open the Edit user to Authentication Mapping window and enter the following values
- Set Authentication Type as 802.1x
- Set Authentication Method as LDAP Authentication
- Set LDAP configuration as your LDAP server that is already configured
- Click Ok
- Click Save
- Map the newly configured AAA configuration to be pushed to the Extreme Access Control
Concluding Thoughts
Network users can now seamlessly self-onboard their devices for an EAP-TLS WPA2-Enterprise network. Once they are assigned certificates, the security risks of data breaches and credential theft drop dramatically. Additionally, network administrators can take full advantage of the network visibility enhancements, such as tying each user and device to a connection, or remotely diagnosing connection issues. So if you’d like to try out SecureW2, or have any questions about how we integrate with ExtremeControl, drop us a line! Or click here to see our pricing for this cost effective solution.
ExtremeControl and Extreme Networks are either registered trademarks or trademarks of Extreme Networks in the United States and/or other countries. Other trademarks, logos, and service marks used in this site are the property of SecureW2 or other third parties.