Introduction
With the Intune CA Partner integration, organizations can automate their certificate lifecycle management based on the real-time status of their devices managed by Intune. This is achieved through the SCEP Protocol and an OAuth API. The API is invoked during the SCEP enrollment process to validate that the device requesting the certificate exists in your Intune organization. SecureW2 also periodically checks Intune to ensure that devices that are deleted, have changed permissions, or have fallen out of compliance have their authorization modified appropriately. The diagram created by Microsoft below illustrates the enrollment process.
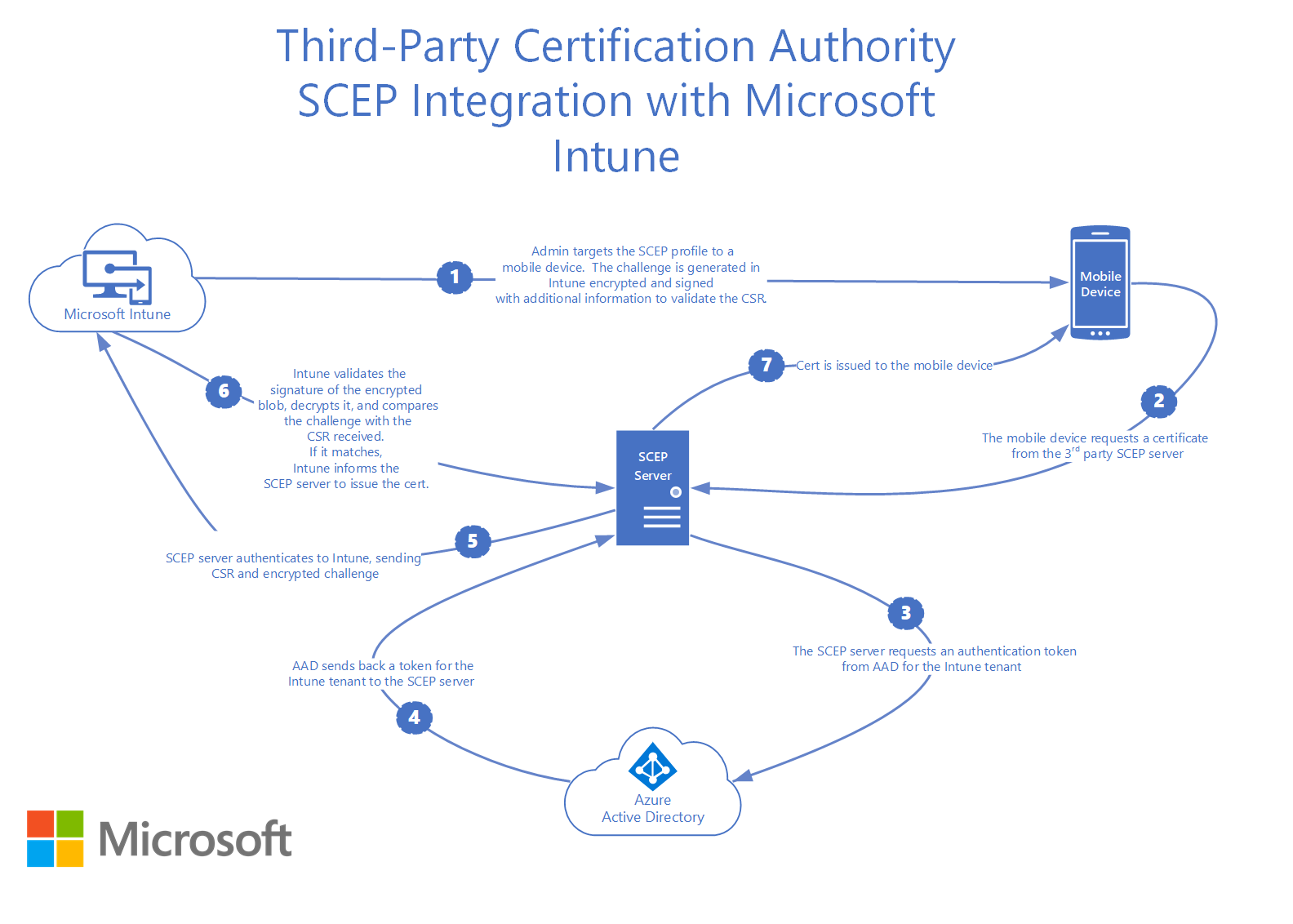
The flowchart below describes what you must do at a high level to set up the Third-Party CA integration.
Prerequisites
The following prerequisites are required to allow device enrollment for digital certificates using SCEP in Microsoft Intune:
- A Microsoft Online Services account with a Microsoft Intune (Microsoft Endpoint Manager) subscription, and the following roles assigned in the Entra ID:
- Intune Administrator
- Application Administrator
- Cloud App Security Administrator
- A valid JoinNow Cloud Management Portal account with a Managed Device Gateway license.
NOTE: By default, when a device enrolled through the Intune third-party CA integration is removed from Intune, the corresponding certificates are automatically revoked in the JoinNow Management Portal.
Device Profiles in Microsoft Intune
Device profiles allow you to add and configure settings, and then push those settings to devices in your organization. The following profiles are created for end-user devices to connect to the secured network using user certificates.
- Trusted Certificate Profile for the SecureW2 RADIUS Server Root CA
- Trusted Certificate Profile for the SecureW2 Root CA
- Trusted Certificate Profile for the SecureW2 Intermediate (Issuing) CA
- SCEP Profile for the SecureW2 SCEP certificate requests
- Wi-Fi profile for secure SSID configuration
NOTE: You must create a separate profile for each platform.
Configure Azure
This section describes the steps to configure Azure and Intune to work with the SecureW2 PKI.
Creating a New Application
To create an app in Azure to communicate with the CA Intune IdP, follow the given steps:
- Log in to the Azure portal.
- Go to App registrations.
- Click New registration.
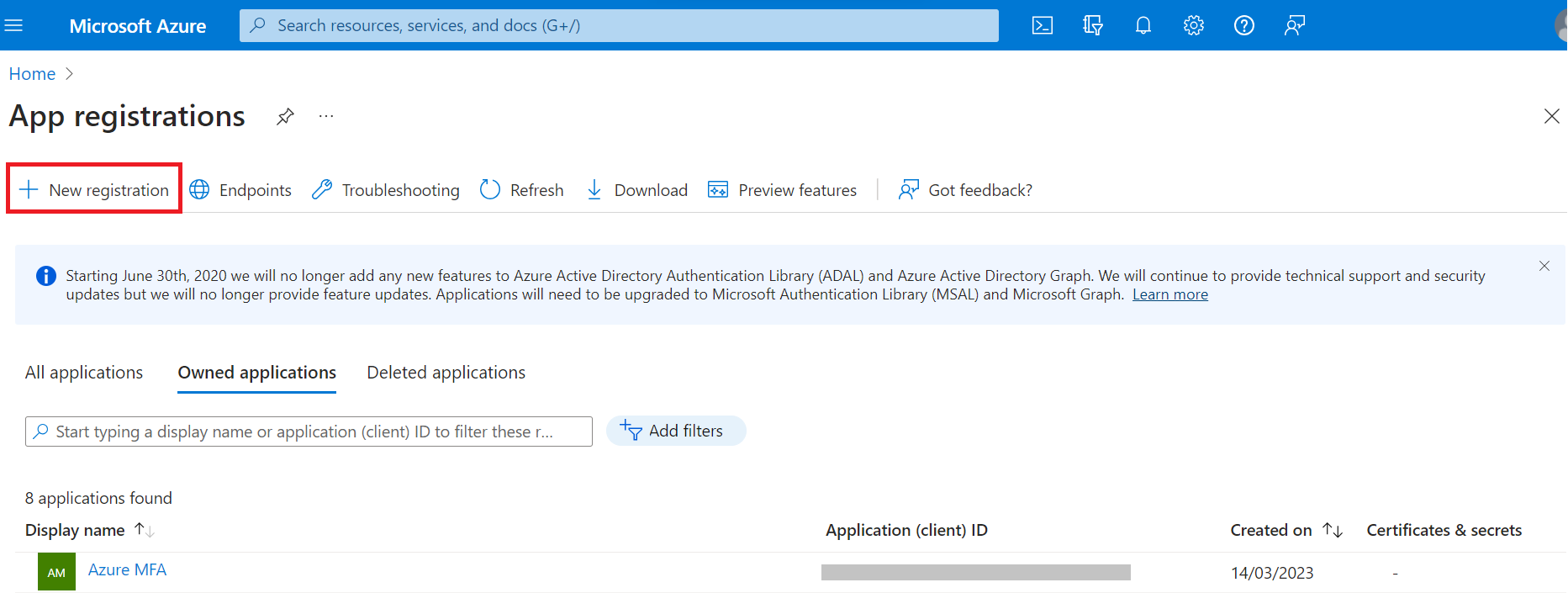
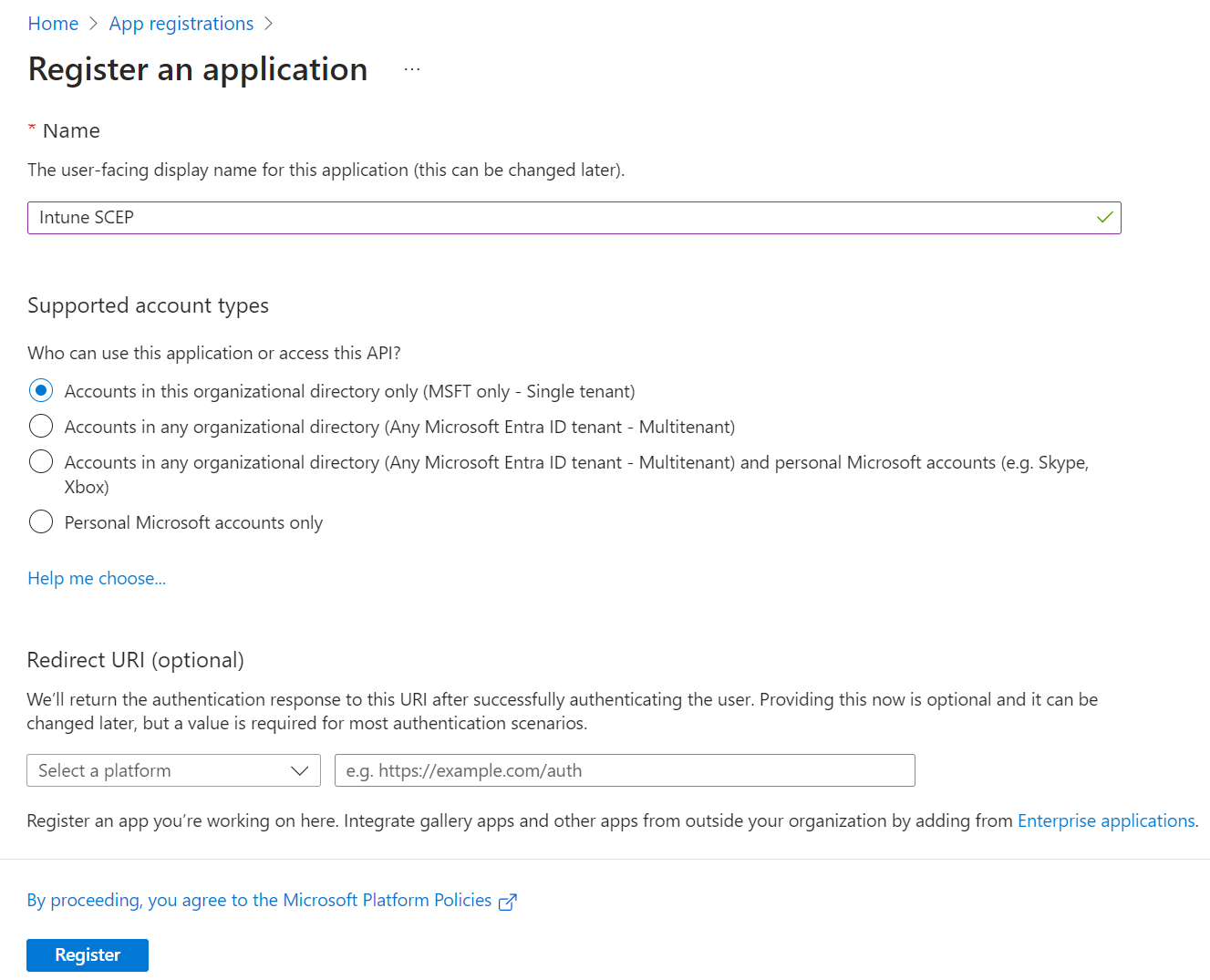
- On the Register an application page, enter the name of the application in the Name field.
- In the Supported account types section, specify who can use the application by selecting any one of the following options:
- Accounts in this organizational directory only (MSFT only – Single tenant)
- Accounts in any organizational directory (Any Microsoft Entra ID tenant – Multitenant)
- Accounts in any organizational directory (Any Microsoft Entra ID tenant – Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox)
- Personal Microsoft accounts only
- Click Register. The following screen is displayed.
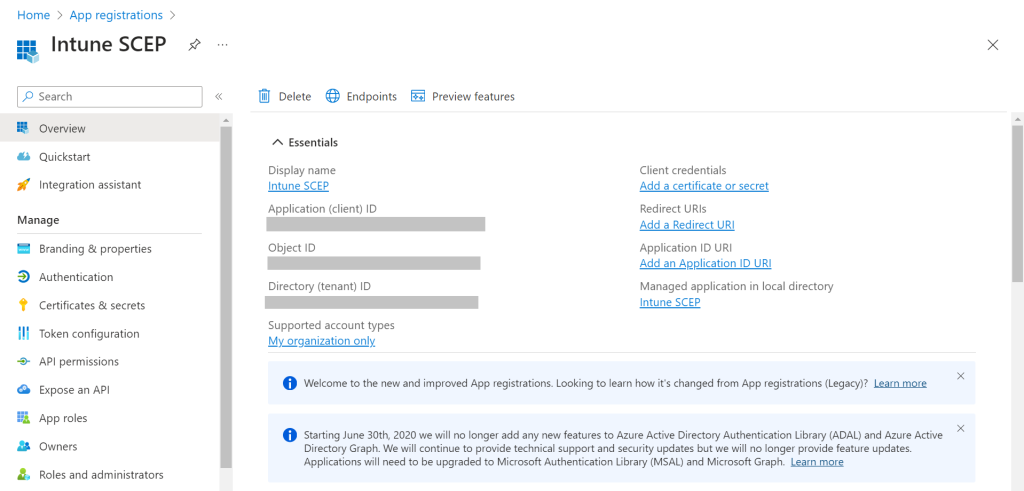
- Copy the Application (client) ID, Object ID, and Directory (tenant) ID values to your console. These values are required to create an Intune IdP in the JoinNow Management Portal (see the Creating an Intune CA IdP section).
Creating a Client Secret
- On the left pane, go to Manage and click Certificates & secrets.
- Click New client secret.
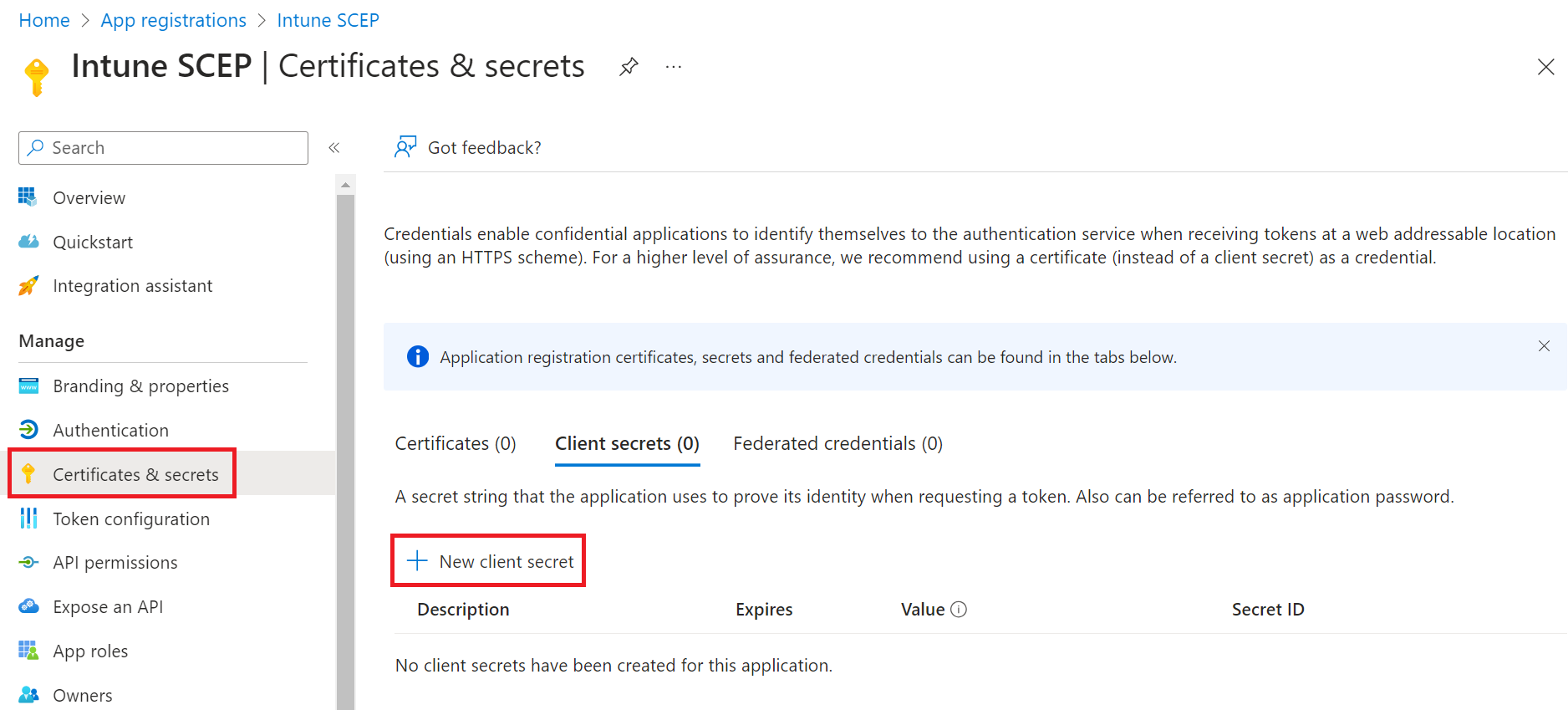
- In the Add a client secret pop-up window, enter a description for the client secret in the Description field.
- From the Expires drop-down list, select the expiration date of the client secret.
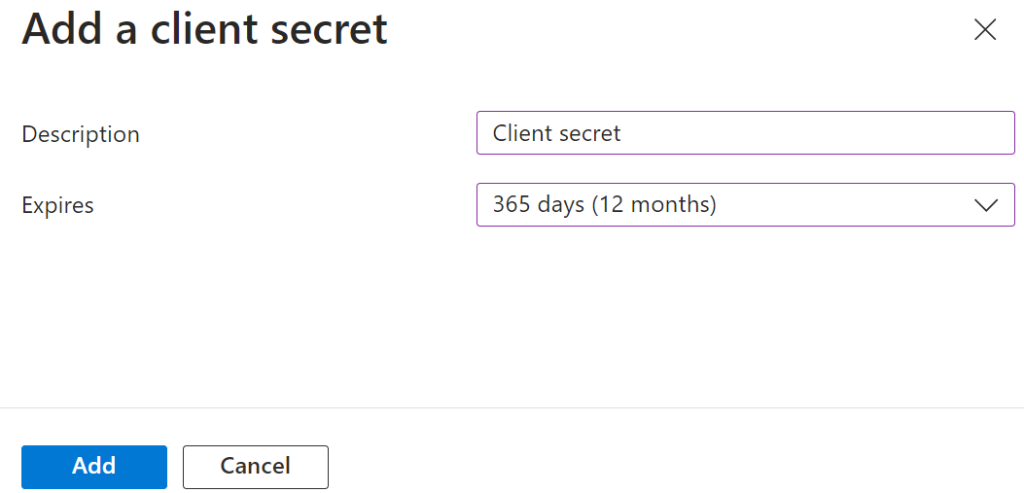
- Click Add.
- The client’s secret is displayed under the Value column.
NOTE: Ensure that you save the client secret on your console properly, as this secret is non-recoverable.
Adding API Permissions
To provide API permission for SecureW2 to access the Entra ID, provide the following steps:
- On the left pane, go to Manage and select API Permissions.
- On the API permissions screen, click Add a permission.
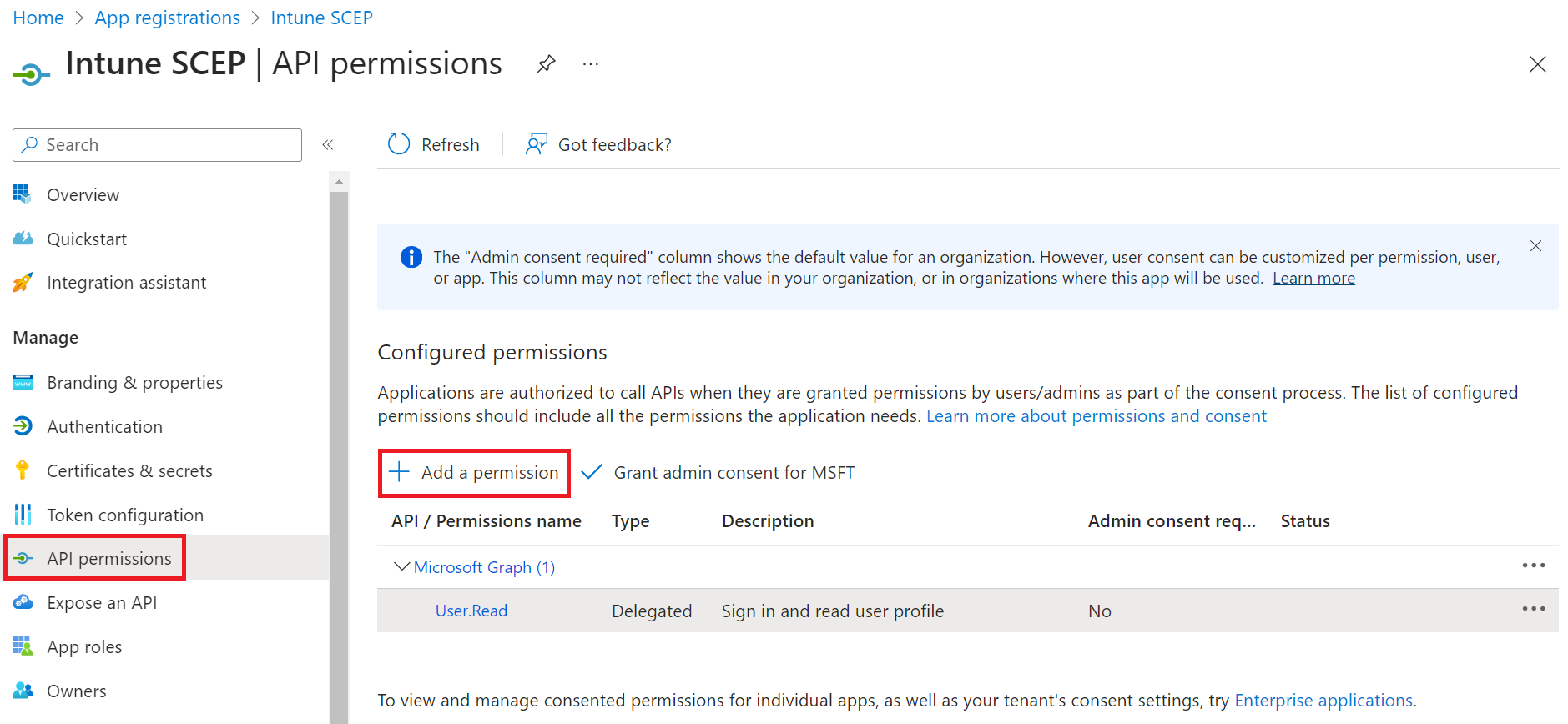
- Select Microsoft Graph.
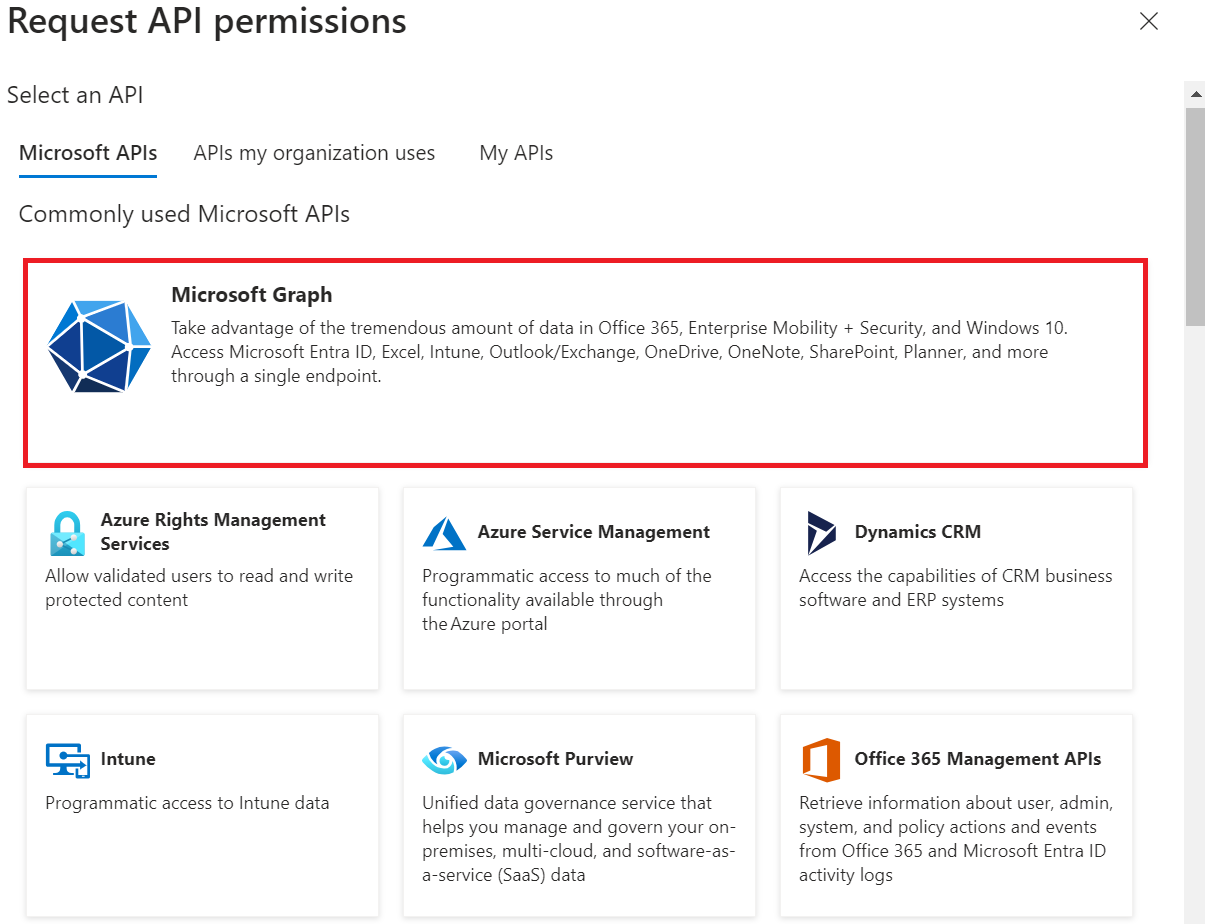
- Select Application permissions.
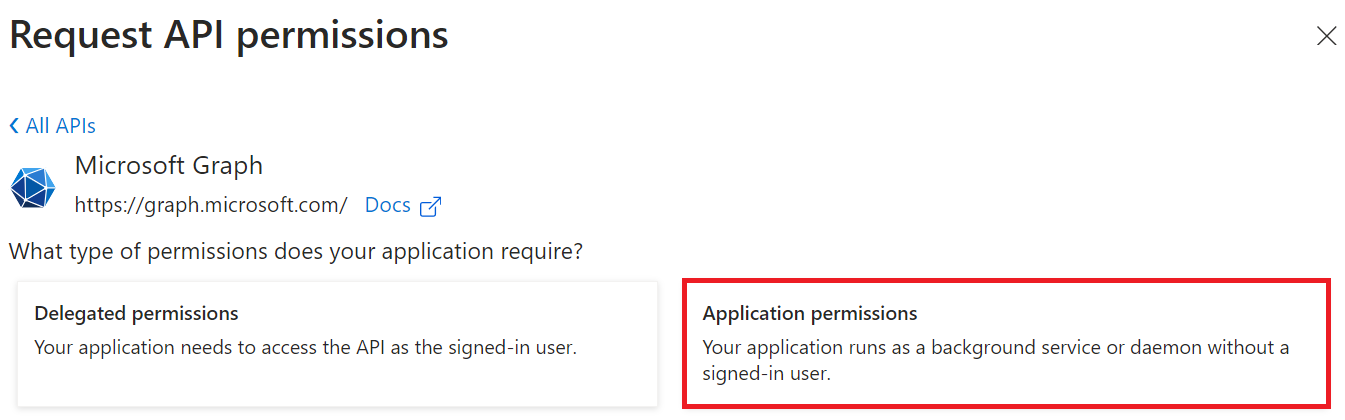
- In the Select permissions section, from the Application drop-down menu, select Application.Read.All.
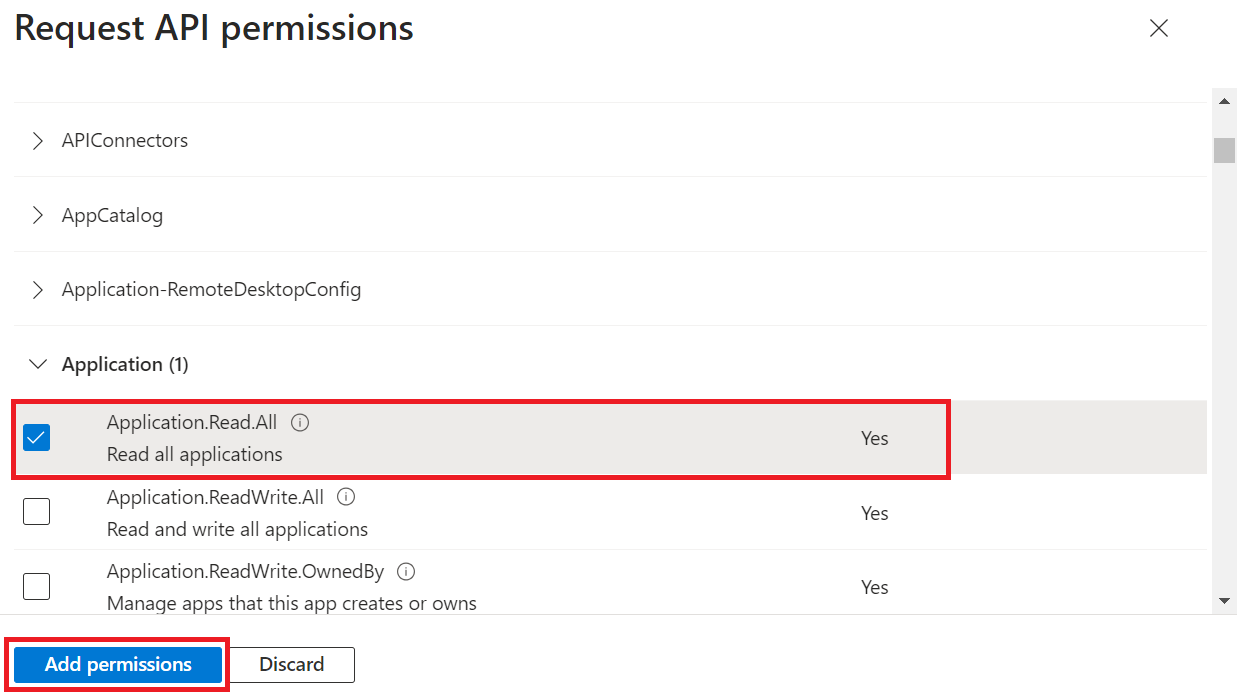
- Click Add permissions.
- Click Add a permission.
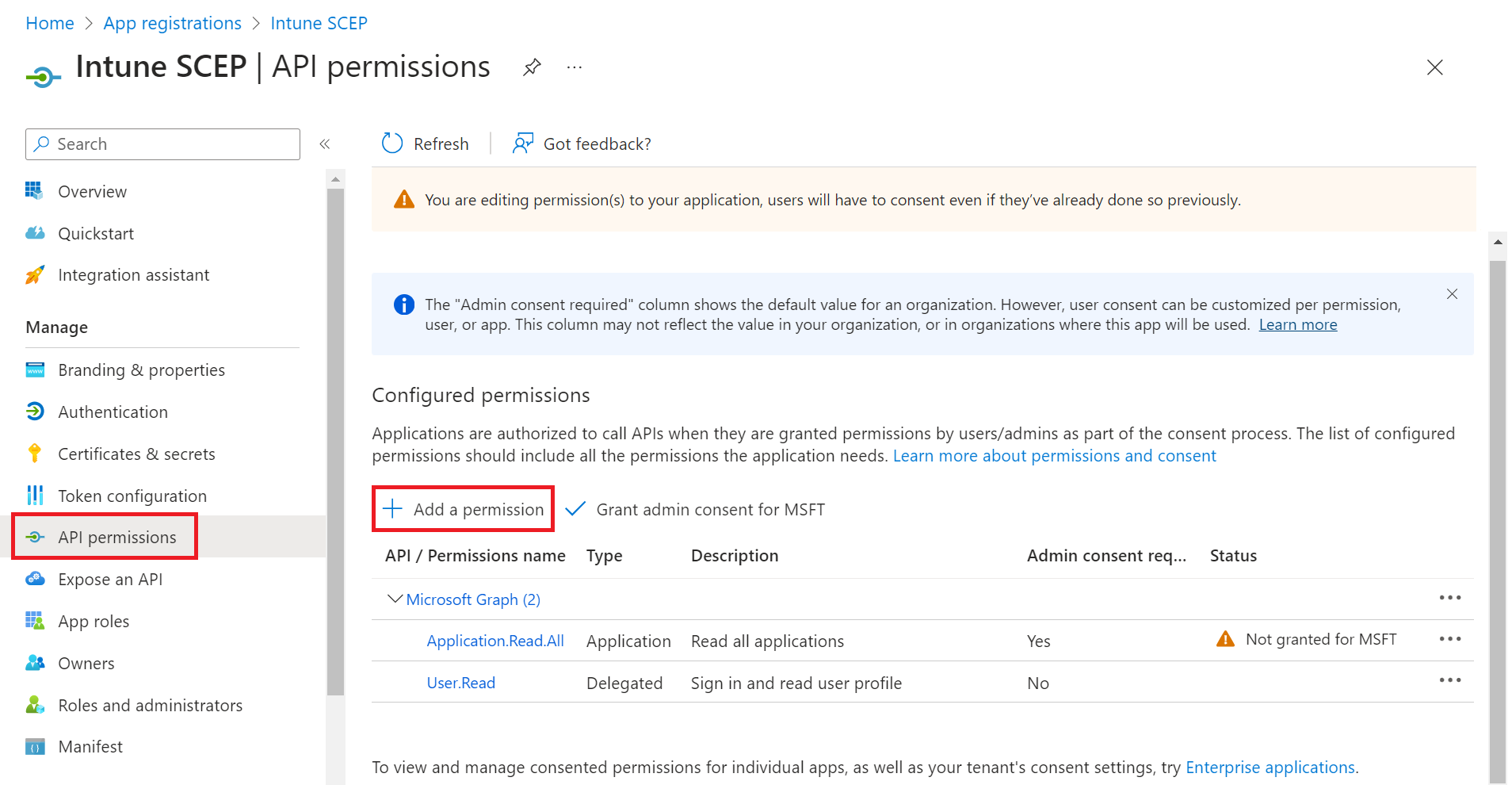
- Select Intune.
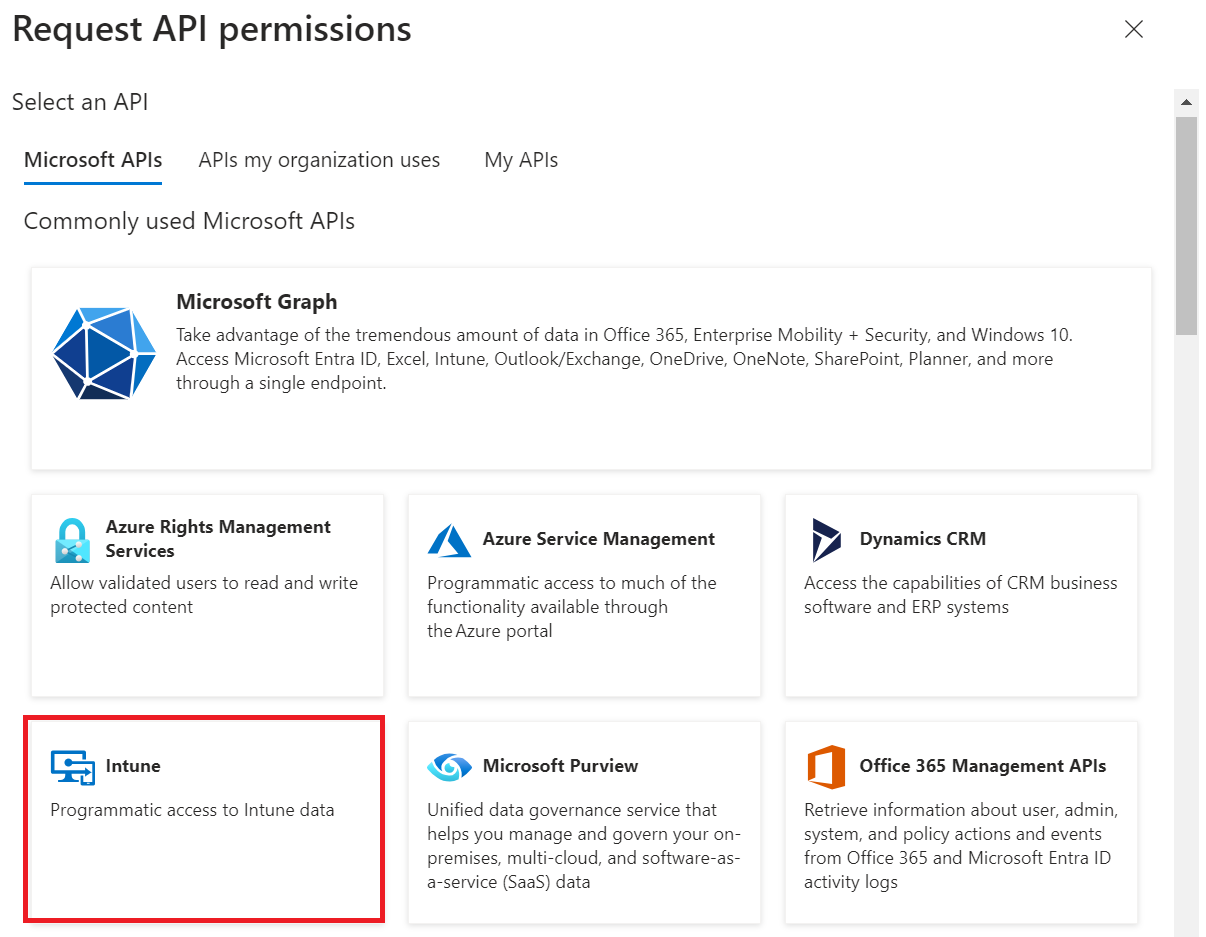
- Select Application permissions.
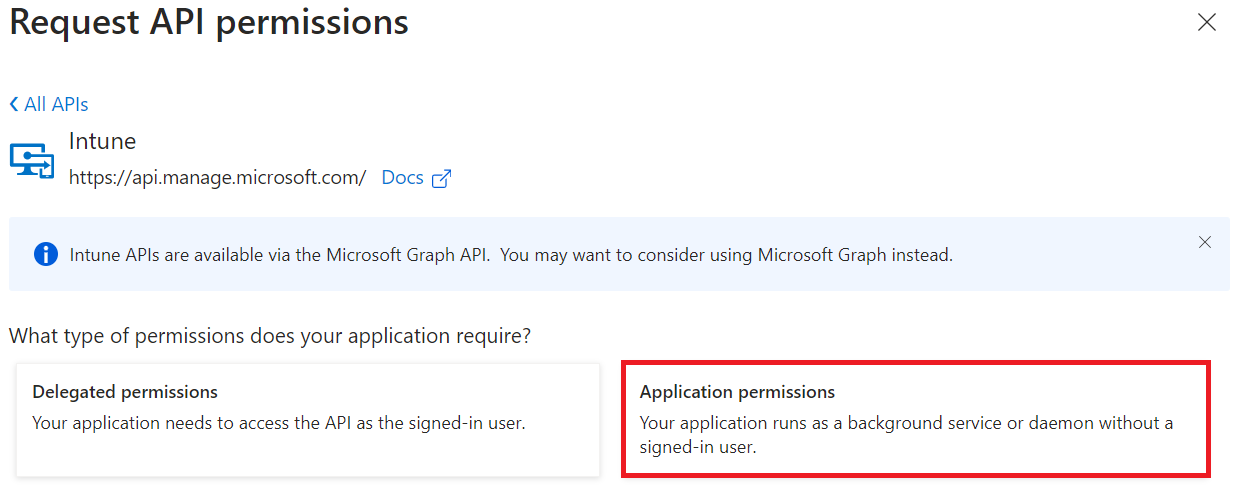
- In the Select permissions section, from the Permissions drop-down menu, select scep_challenge_provider for certificate request validation, and then click Add.
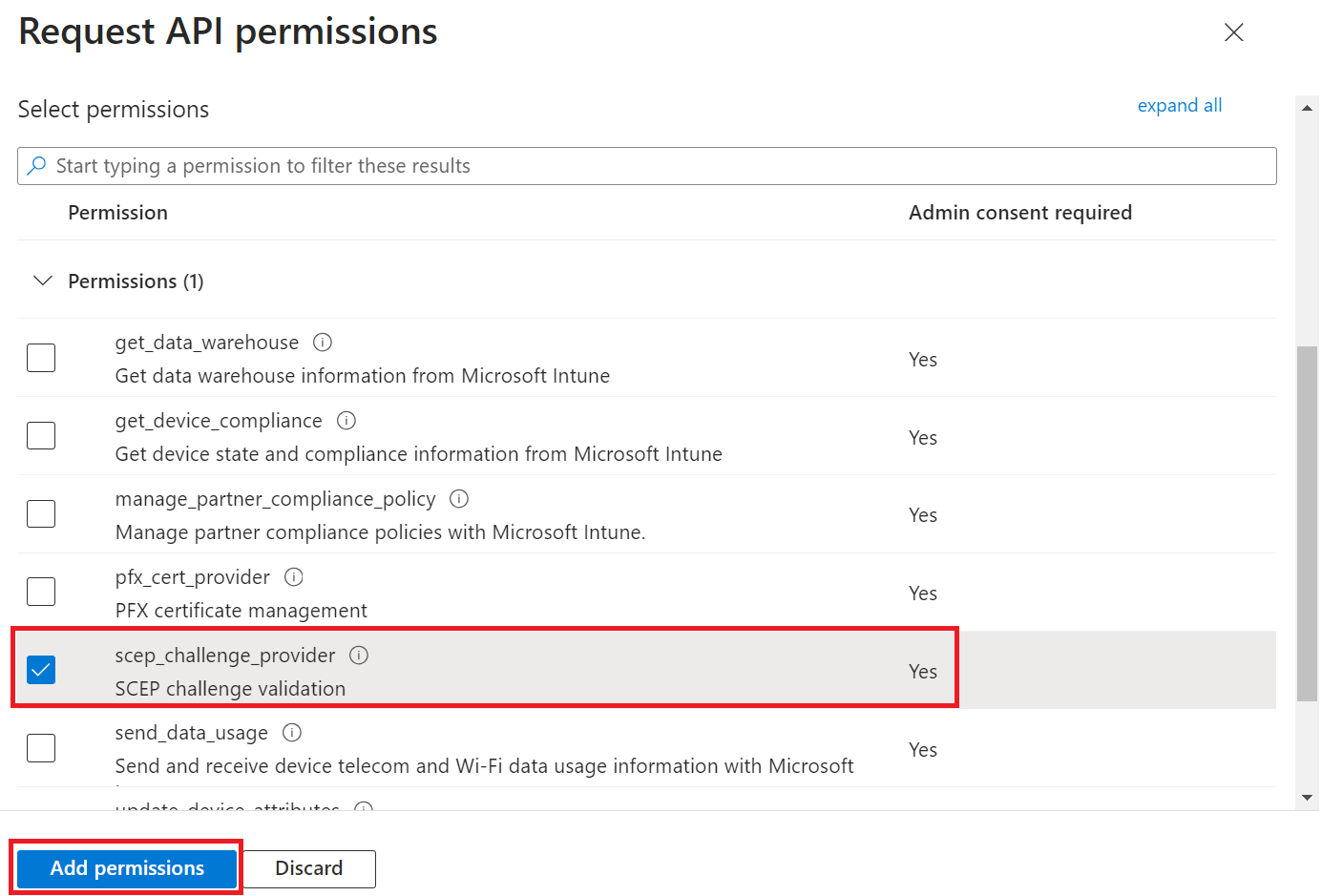
- After adding the permissions, click Grant admin consent for {your organization} to grant consent for the requested permissions.
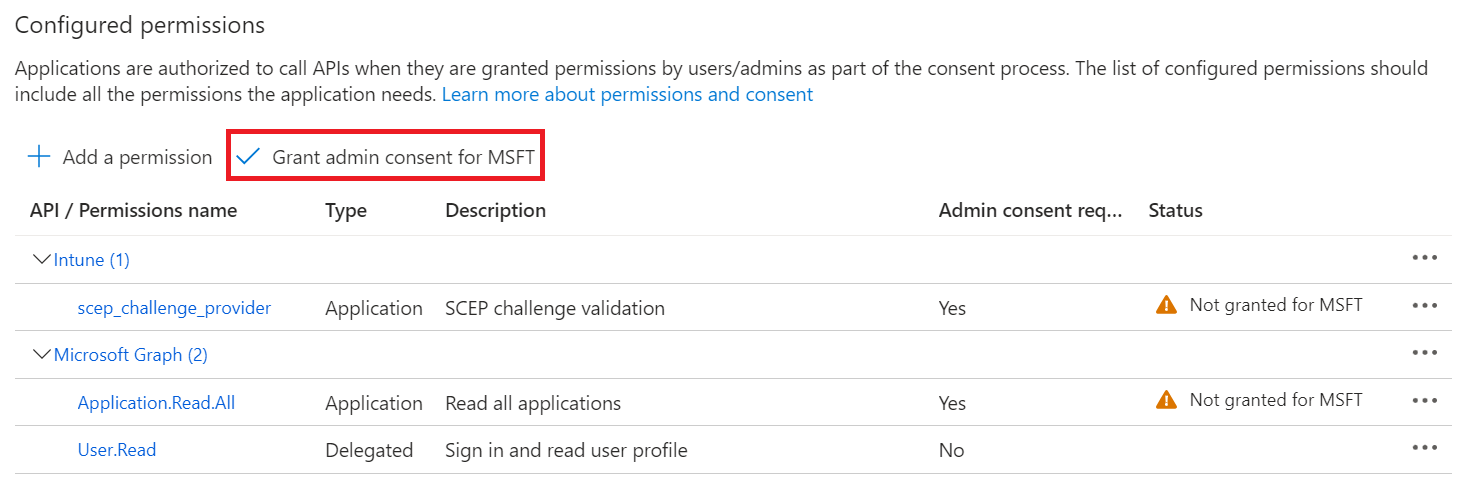
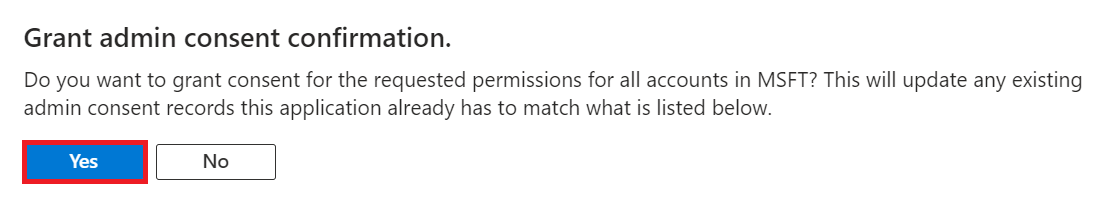
- In the Grant admin consent confirmation pop-up window, click Yes.
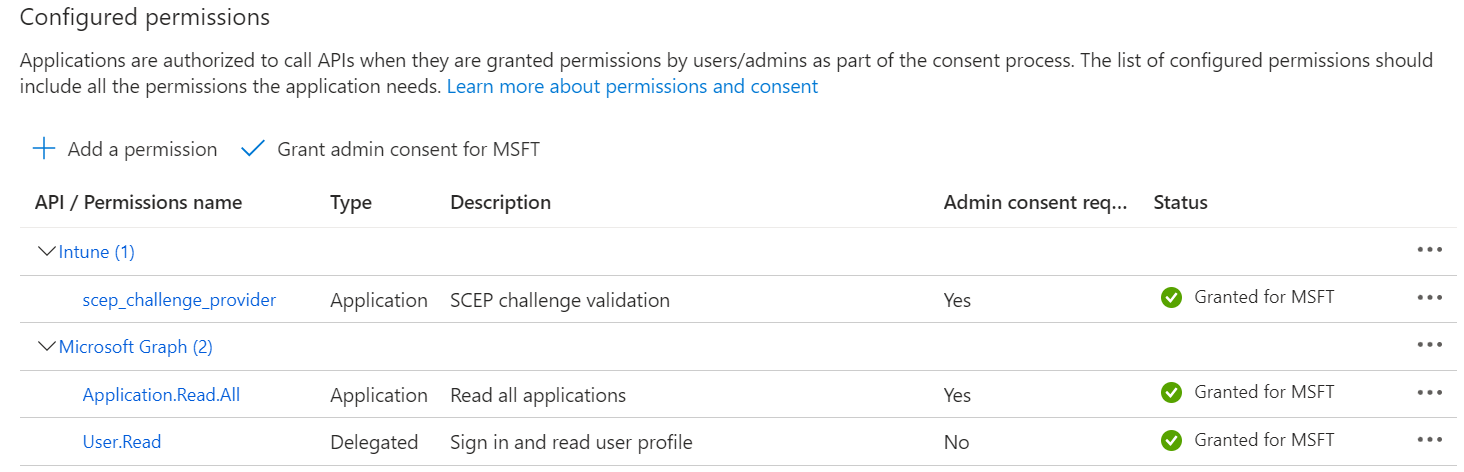
- The configured APIs are displayed on the Configured permissions page.
Configure SecureW2
This section describes the following procedures carried out in the JoinNow Management Portal:
- Creating a SecureW2 Intermediate CA
- Creating an Intune Certificate Template
- Creating an Identity Provider (IdP) for Intune CA
- Creating the policies (Role, Enrollment, and Network policies)
Creating an Intermediate CA for Intune SCEP Gateway Integration
As a best practice, SecureW2 recommends having a new intermediate CA for JoinNow SCEP Gateway integration with Intune. The CA that issues certificates to BYOD devices should be separate from the CA that issues certificates to managed devices because managed devices do not require email notifications. You can disable email notifications for a dedicated CA that issues certificates to Intune-managed devices.
To create a new intermediate CA:
- Log in to the JoinNow Management Portal.
- Navigate to PKI > Certificate Authorities.
- Click Add Certificate Authority.
- In the Basic section, from the Generate CA For drop-down list, select the Device and User Authentication option to authenticate devices and users.
- From the Type drop-down list, select Intermediate CA.
- From the Certificate Authority drop-down list, select the default Root CA that comes with your organization.
- In the Common Name field, enter a common name for the CA certificate. SecureW2 recommends a name that includes “SCEP.”
- From the Key Size drop-down list, select 2048 for the CA certificate key pair.
- From the Signature Algorithm drop-down list, select the signature algorithm for the certificate signing request. The option available is SHA-256.
- In the Validity Period (in years) field, enter the validity period of the CA certificate.
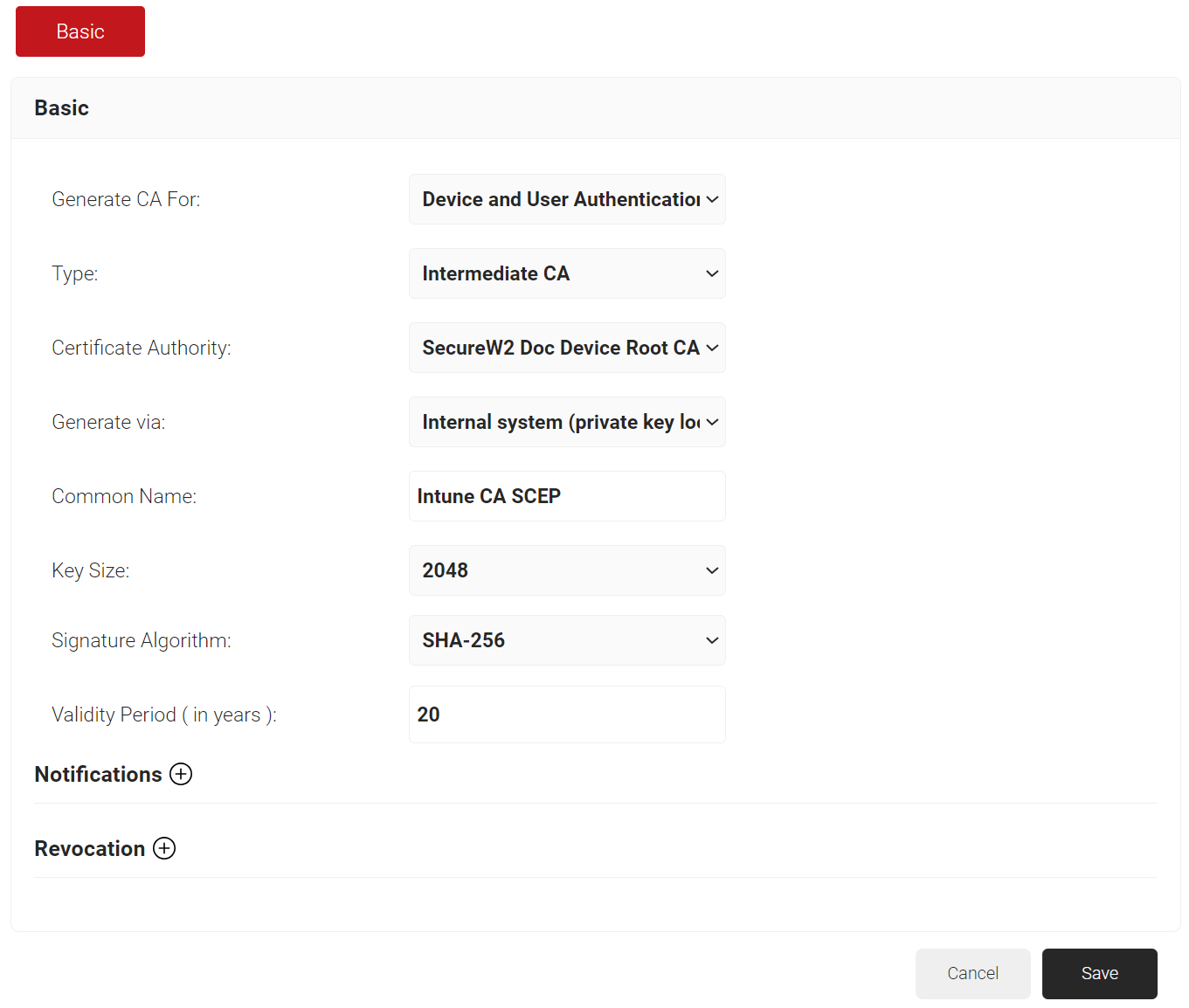
- Click Save. The new intermediate CA is generated.
Creating an Intune Certificate Template
To create an Intune Certificate Template:
- Navigate to PKI > Certificate Authorities.
- Scroll to the Certificate Templates section and click Add Certificate Template.
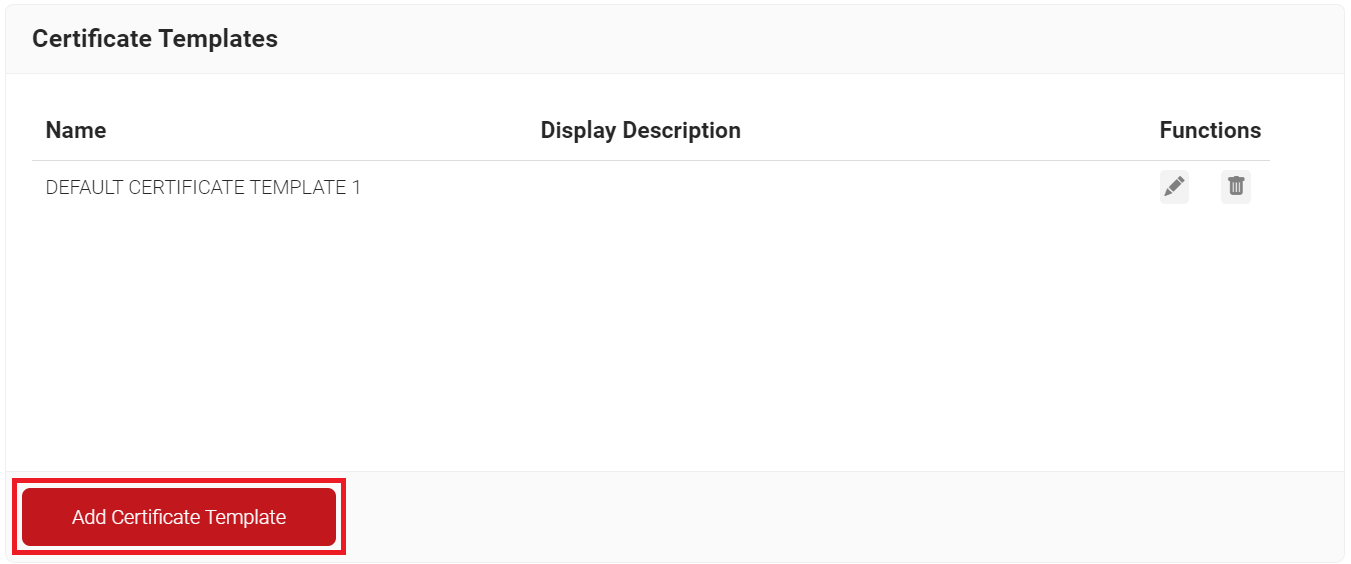
- In the Basic section, for the Name field, enter the name of the certificate template.
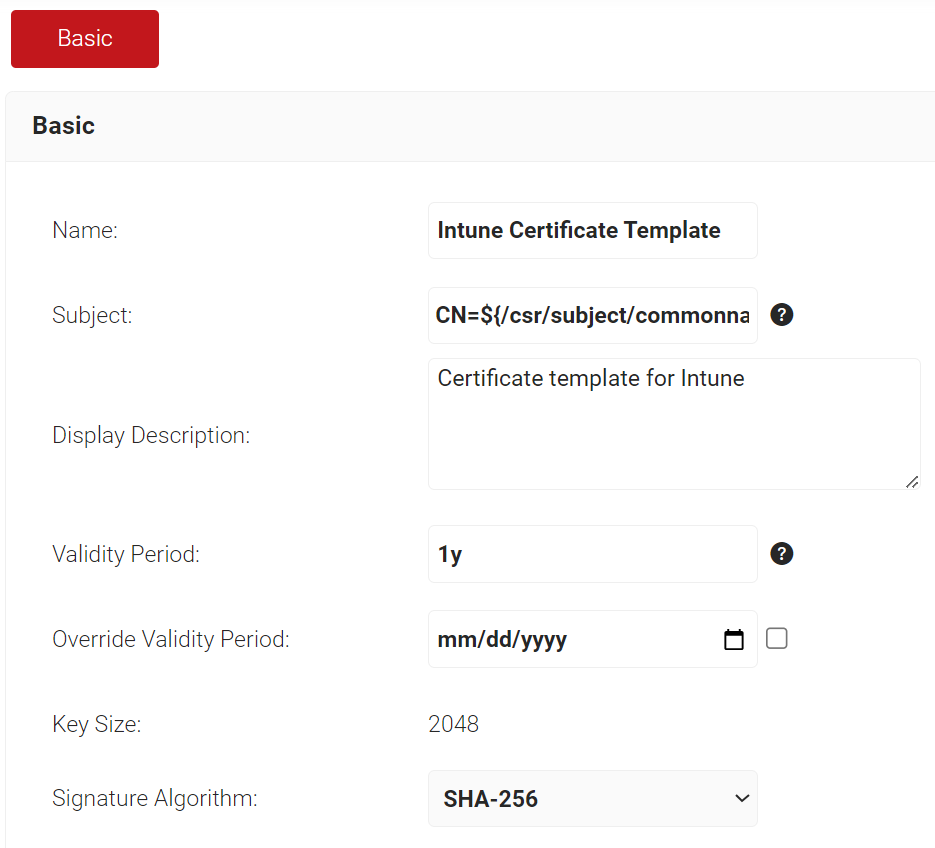
- In the Subject field, enter the following source value recommended for the Intune-specific certificate template: CN=${/csr/subject/commonname}.
- In the Display Description field, enter a suitable description for the certificate template.
- In the Validity Period field, type the validity period of the certificate (based on the requirement).
- From the Signature Algorithm drop-down list, select SHA-256 as the signature algorithm for the certificate signing request.
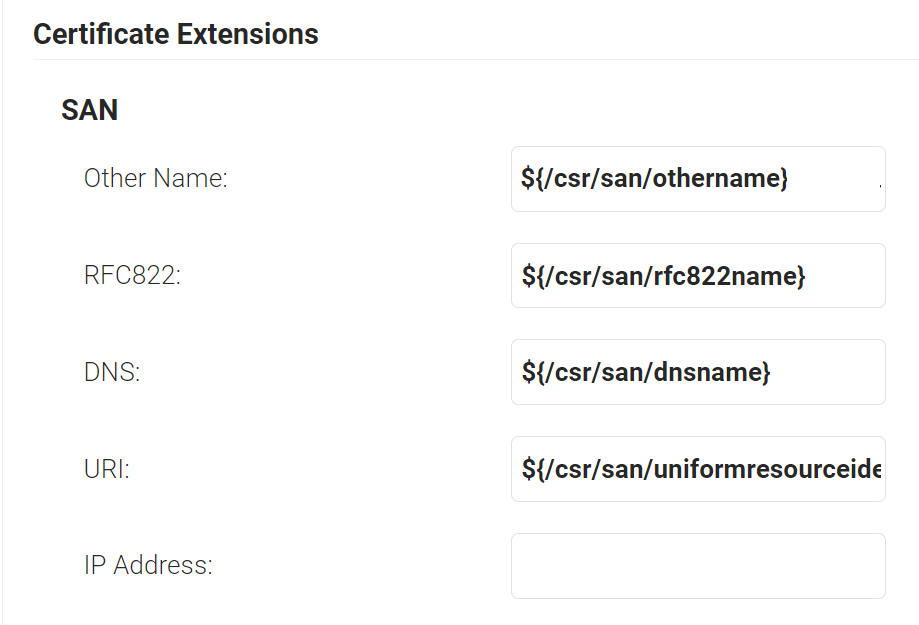
- In the SAN section, the following configurations are the recommended values. This can be changed as per the requirement of the infrastructure and setup.
- In the Other Name field, enter ${/csr/san/othername}
- In the RFC822 field, enter ${/csr/san/rfc822name}
- In the DNS field, enter ${/csr/san/dnsname}
- In the Extended Key Usage section, from the Use Certificate For list, select Client Authentication.
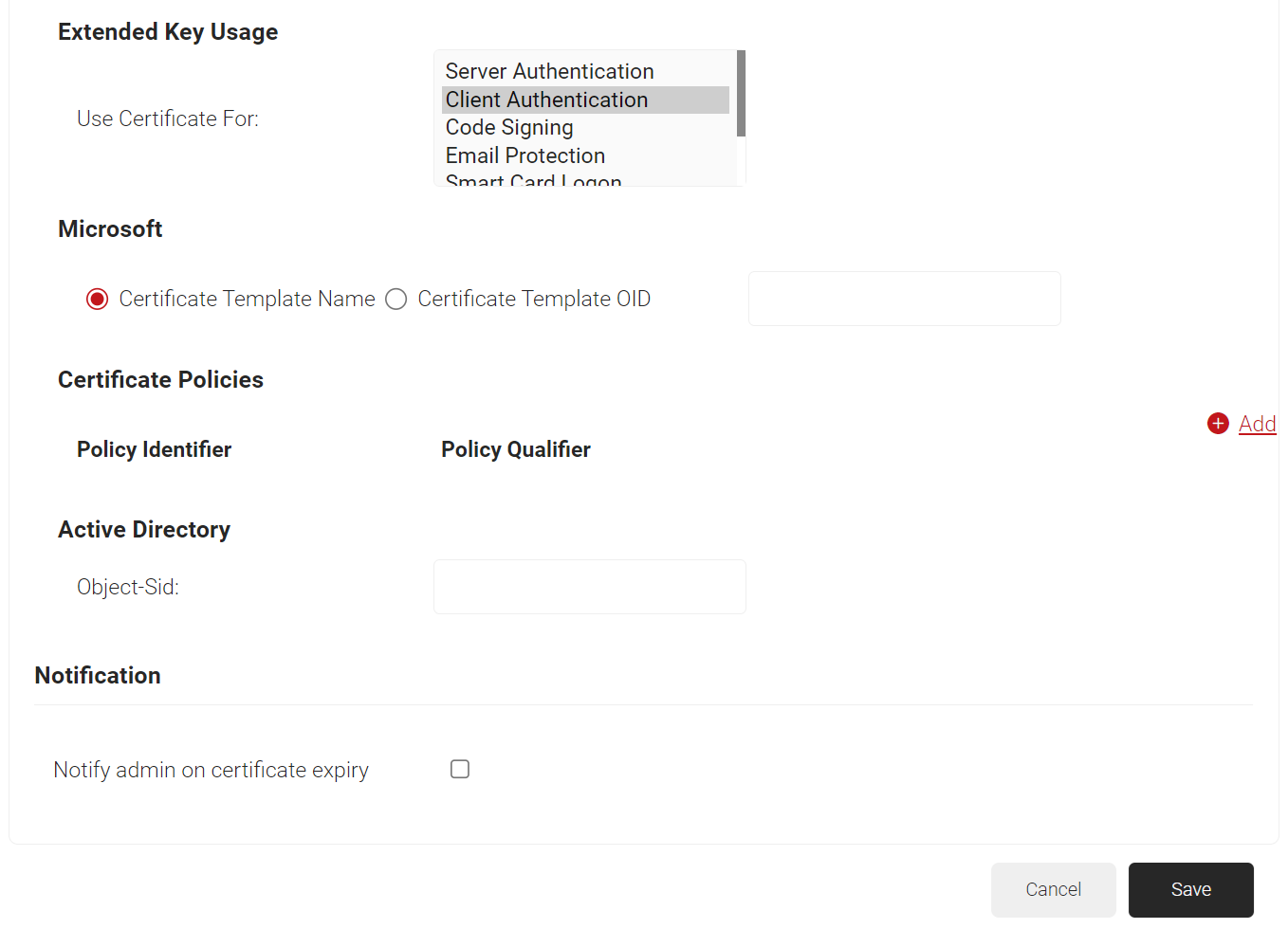
- Click Save.
Creating an Intune CA IdP
In the JoinNow MultiOS Management Portal, create an IdP for the Intune CA to accept requests from the Intune portal. The IdP provides the Endpoint URI for the SCEP profiles in Intune.
- Go to Identity Management > Identity Providers.
- Click Add Identity Provider.
- In the Basic section, enter the name of the IdP in the Name field.
- In the Description field, enter a suitable description for the IdP.
- From the Type drop-down list, select Intune CA Partner.
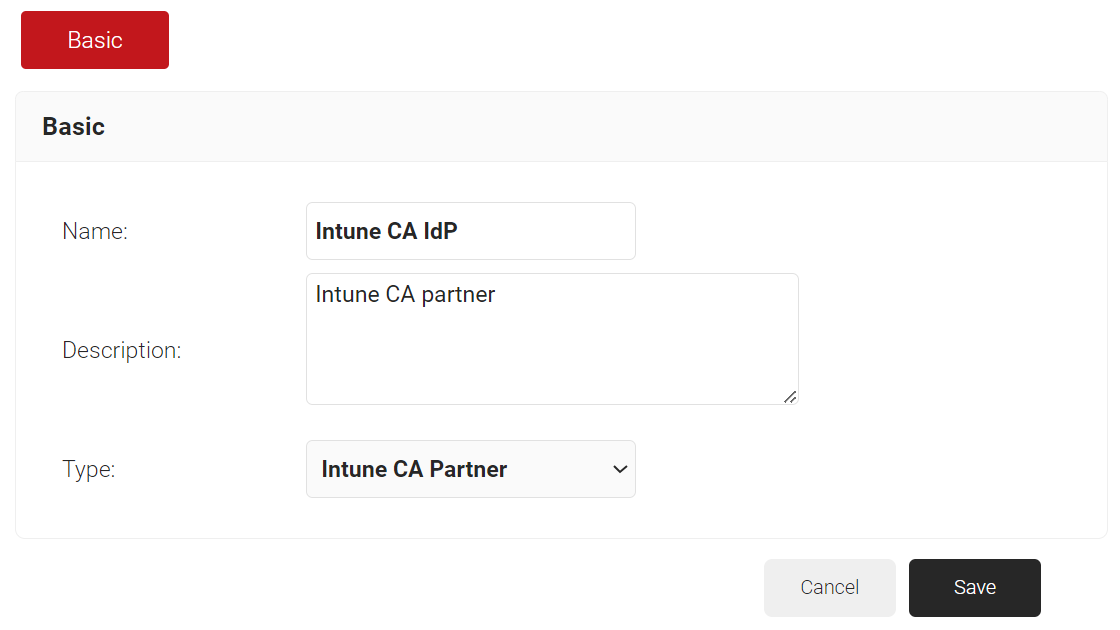
- Click Save.
- The page refreshes, and the Configuration tab is displayed.
- Select the Configuration tab.
- In the Configuration section, for the Client Id and Tenant Id fields, enter the values you obtained after creating a new application in the Azure portal (for more information, see the Creating a New Application section).
- In the Client Secret field, enter the value you obtained after creating the client secret in the Azure portal (see the Creating a Client Secret section).
- From the Certificate Authority drop-down list, select the intermediate CA you created earlier (see the Creating an Intermediate CA for Intune SCEP Gateway Integration section).
- Copy the Endpoint URI to your console. This Endpoint URI will be used while configuring a SCEP Profile in Intune.
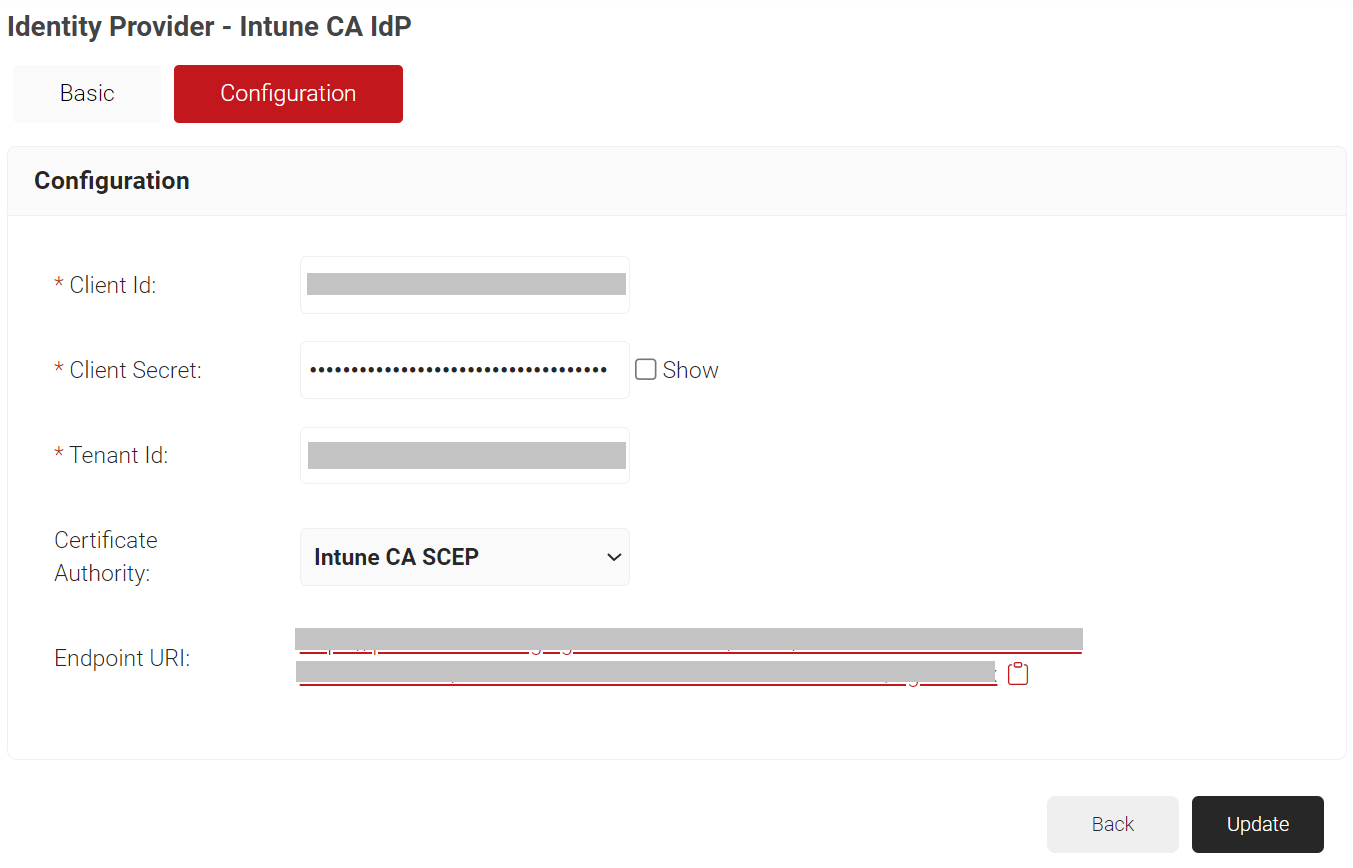
- Click Update.
Configuring Policy Management
Setting up Microsoft Intune requires three policies in the JoinNow MultiOS Management Portal:
- Policy Engine Workflow
- Enrollment policy
- Network policy
NOTE: Microsoft Intune does not need a dedicated Device Role policy. You can use the Default Device Role policy in the configuration.
Configuring a Policy Engine Workflow
To configure a Policy Engine Workflow:
- Navigate to Policy Management > Policy Engine Workflows.
- Click Add Policy Engine Workflows.
- In the Basic section, enter the name of the policy engine workflow in the Name field.
- In the Display Description field, enter a suitable description for the policy engine workflow.
- Click Save.
- The page refreshes, and the Conditions tab is displayed.
- Select the Conditions tab.
- In the Conditions section, from the Identity Provider drop-down list, select the Intune CA IdP you created earlier (see the Creating an Intune CA IdP section).
- In the Attributes/Groups section, for the Attribute field, retain ANY.
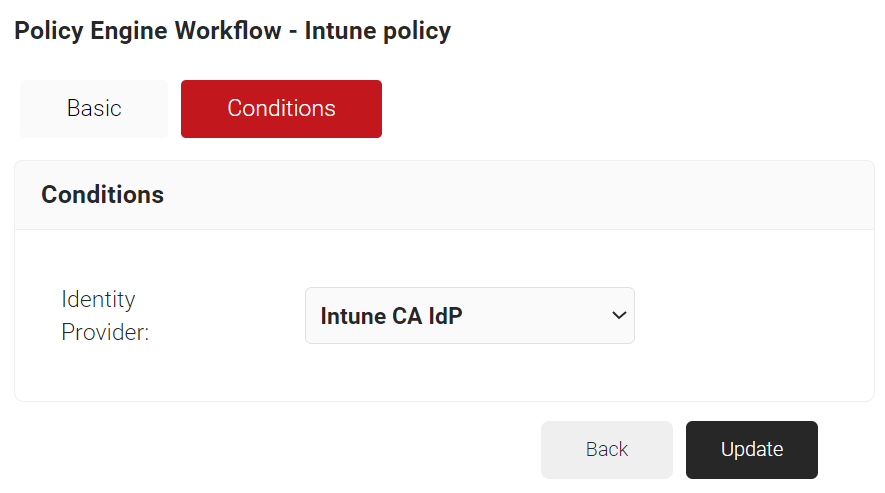
- Click Update.
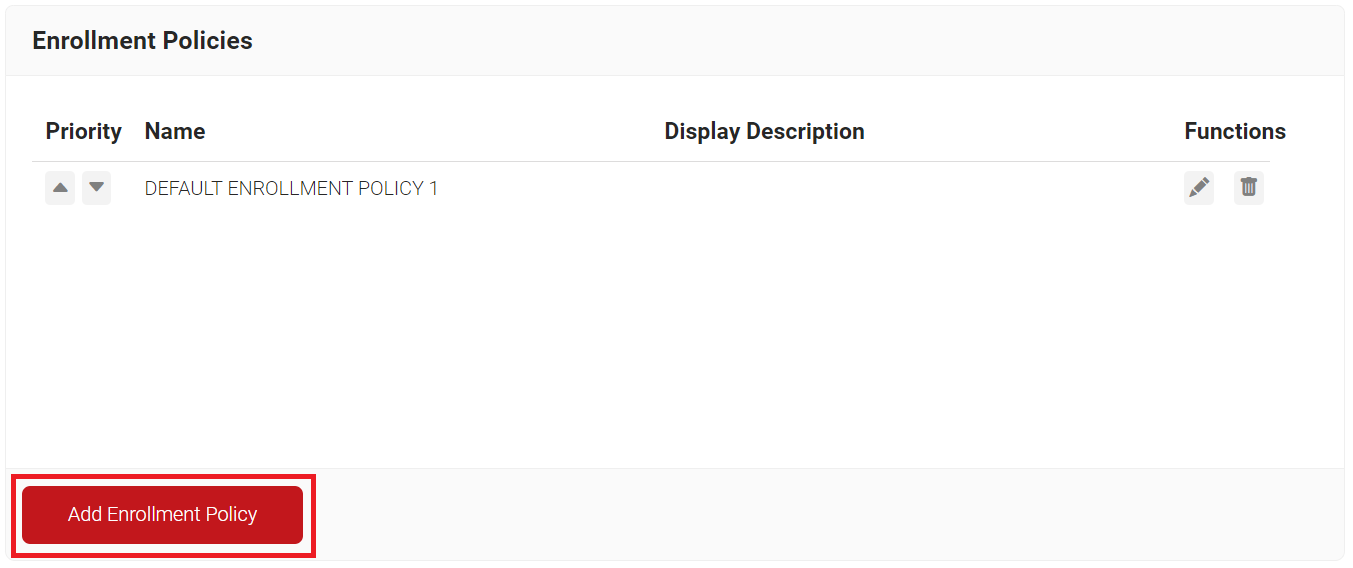
Configuring an Enrollment Policy
To configure an enrollment policy:
- Navigate to Policy Management > Enrollment Policies.
- Click Add Enrollment Policy.
- In the Basic section, enter the name of the enrollment policy in the Name field.
- In the Display Description field, enter a suitable description for the enrollment policy.
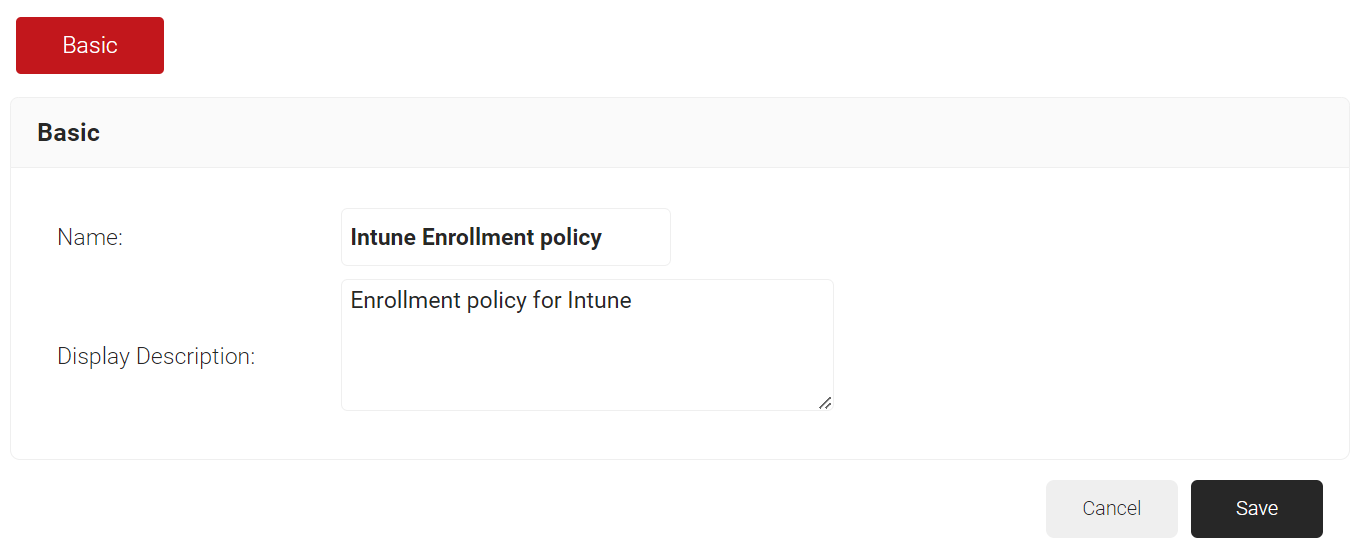
NOTE: You must select a User Role and Device Role for enrollment. You can use a Fallback Device policy to allow enrollment based on the Policy Engine Workflow.
Click Save.
- The page refreshes, and the Conditions and Settings tabs are displayed.
- Select the Conditions tab.
- In the Conditions section, from the Role drop-down list, select the Policy Engine Workflow you created earlier (see the Configuring a Policy Engine Workflow section).
- From the Device Role drop-down list, select DEFAULT DEVICE ROLE POLICY.
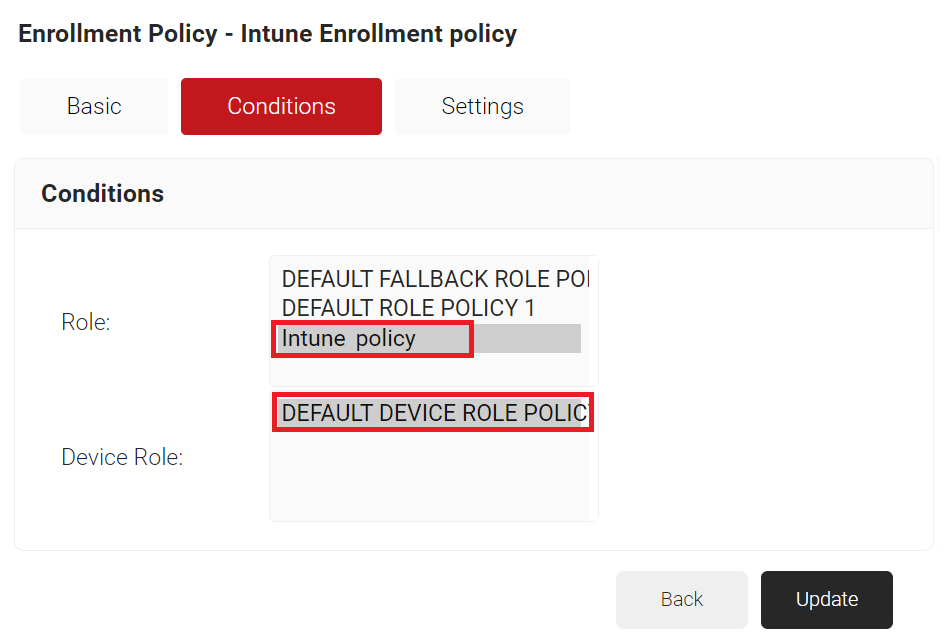
- Select the Settings tab.
- In the Settings section, from the Use Certificate Authority drop-down list, select the intermediate CA you created earlier (see the Creating an Intermediate CA for Intune SCEP Gateway Integration section).
- From the Use Certificate Template drop-down list, select the template you created earlier (see the Creating an Intune Certificate Template section).
- In the other settings, retain the default values.
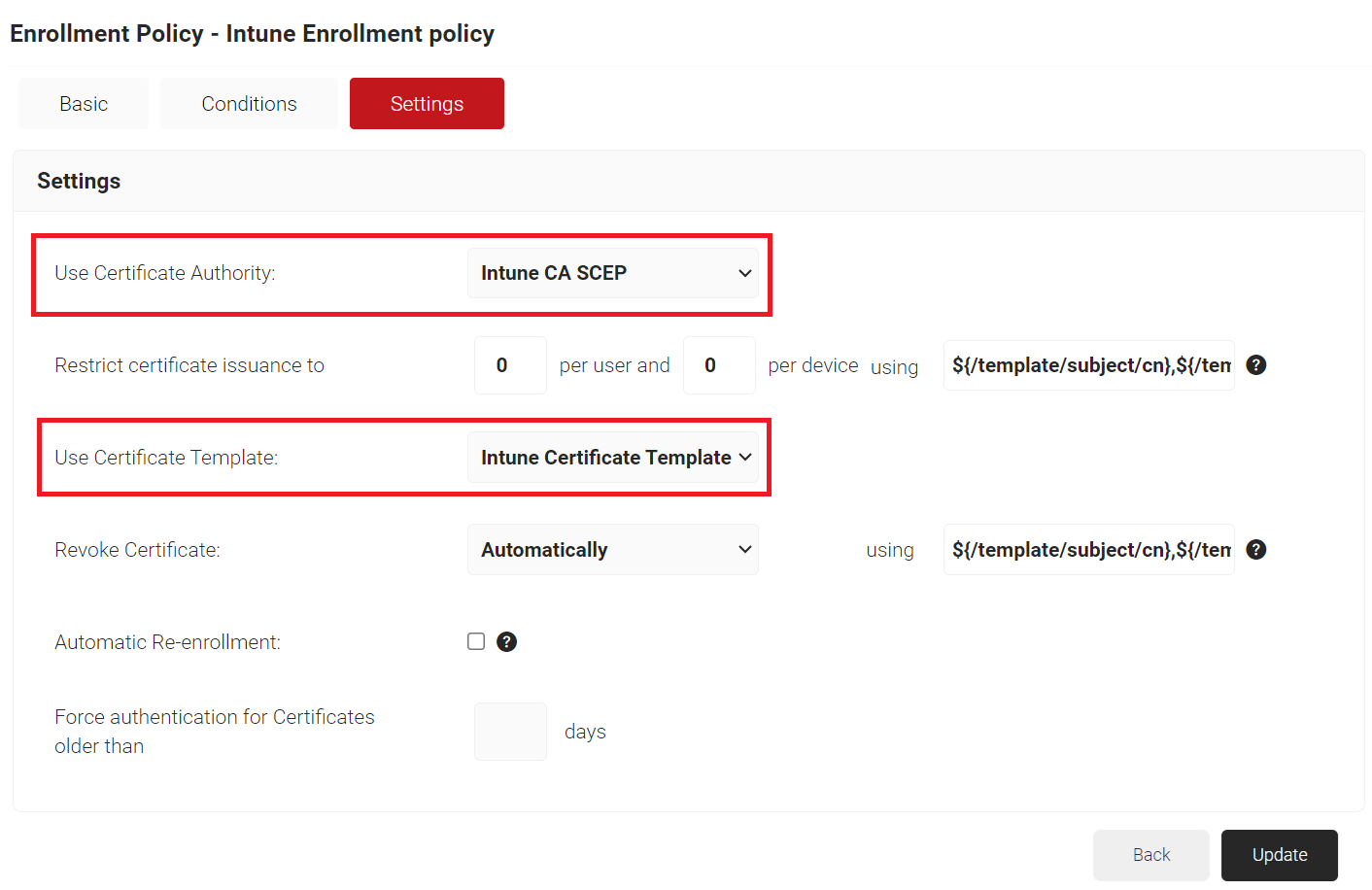
- Click Update.
Configuring Network Policy
To configure network policy:
- Go to Policy Management > Network Policies.
- Click Add Network Policy.
- In the Basic section, enter the name of the network policy in the Name field.
- In the Display Description field, enter a suitable description for the network policy.
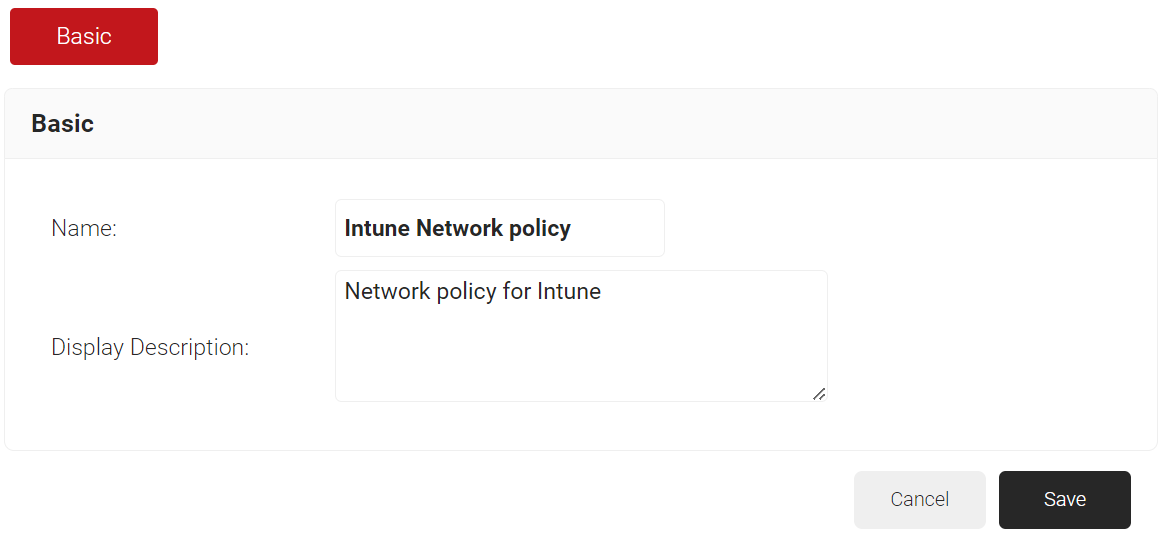
- Click Save.
- Select the Conditions tab.
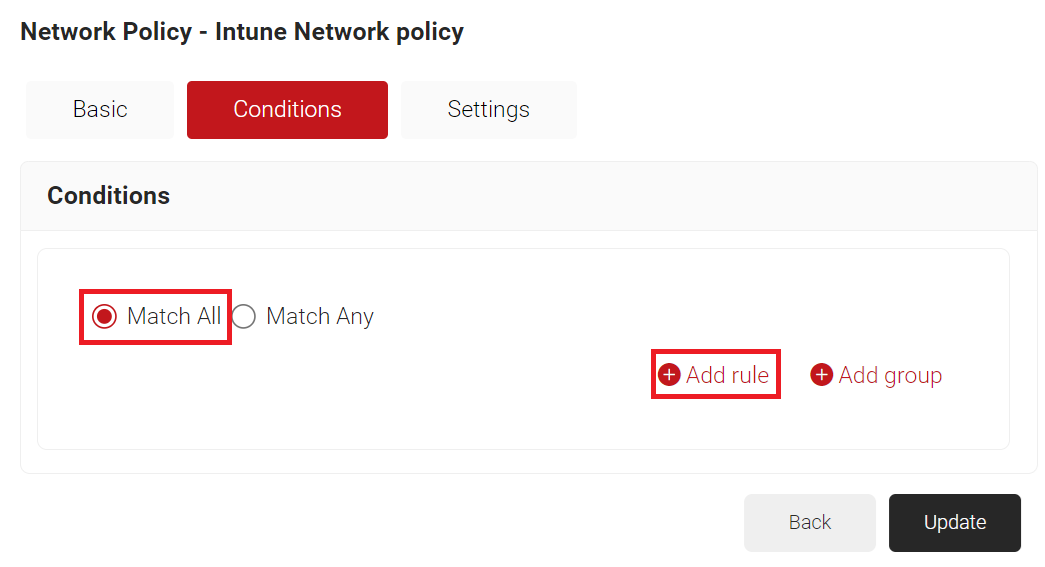
- Select Match All or Match Any based on your requirements to set authentication criteria.
- Click Add rule.
- Expand Identity and select the Role option.
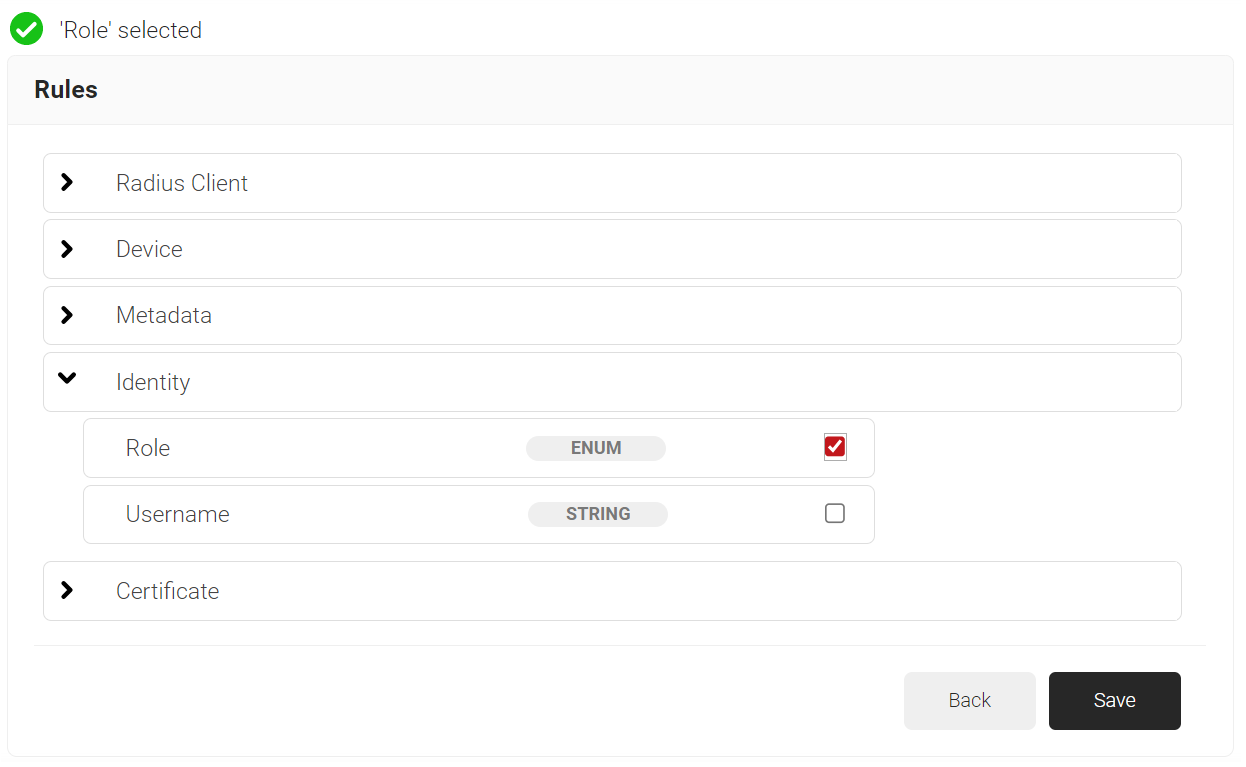
- Click Save.
- The Role option appears under the Conditions tab.
- From the Role Equals drop-down list, select the Policy Engine Workflow you created earlier (see the Configuring a Policy Engine Workflow section).
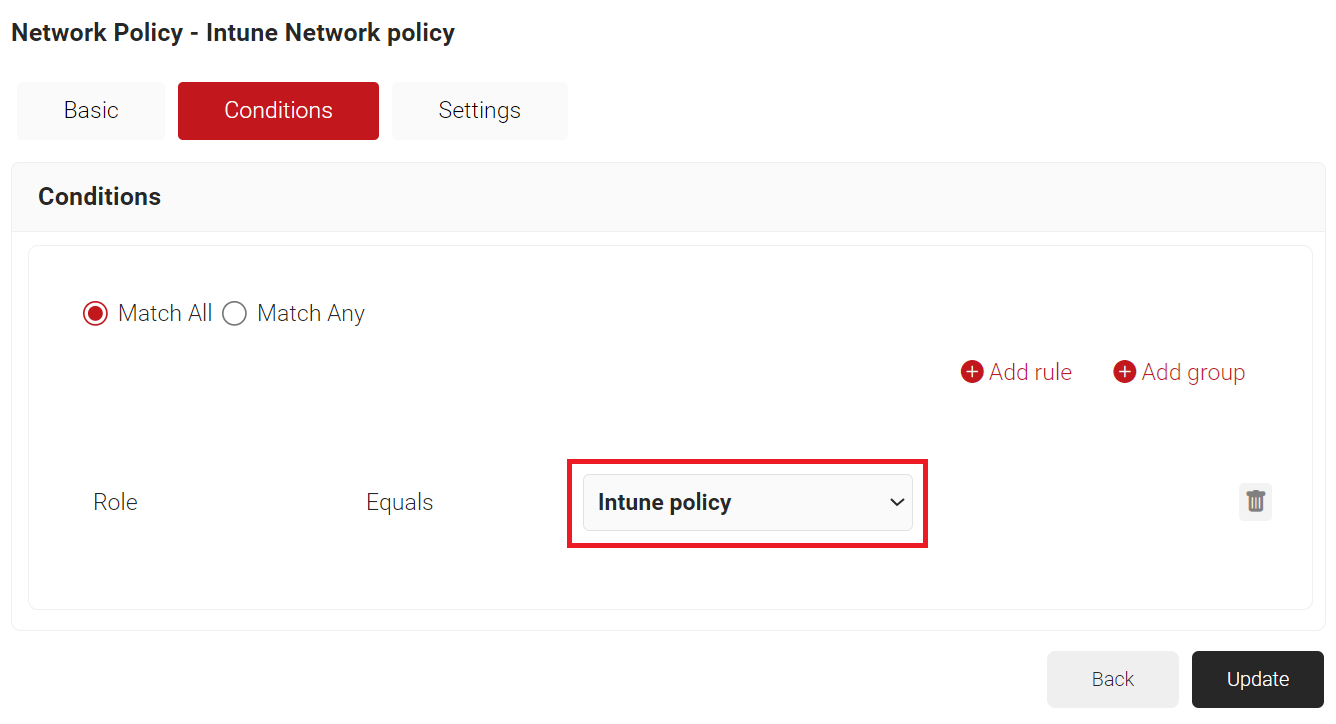
- Select the Settings tab.
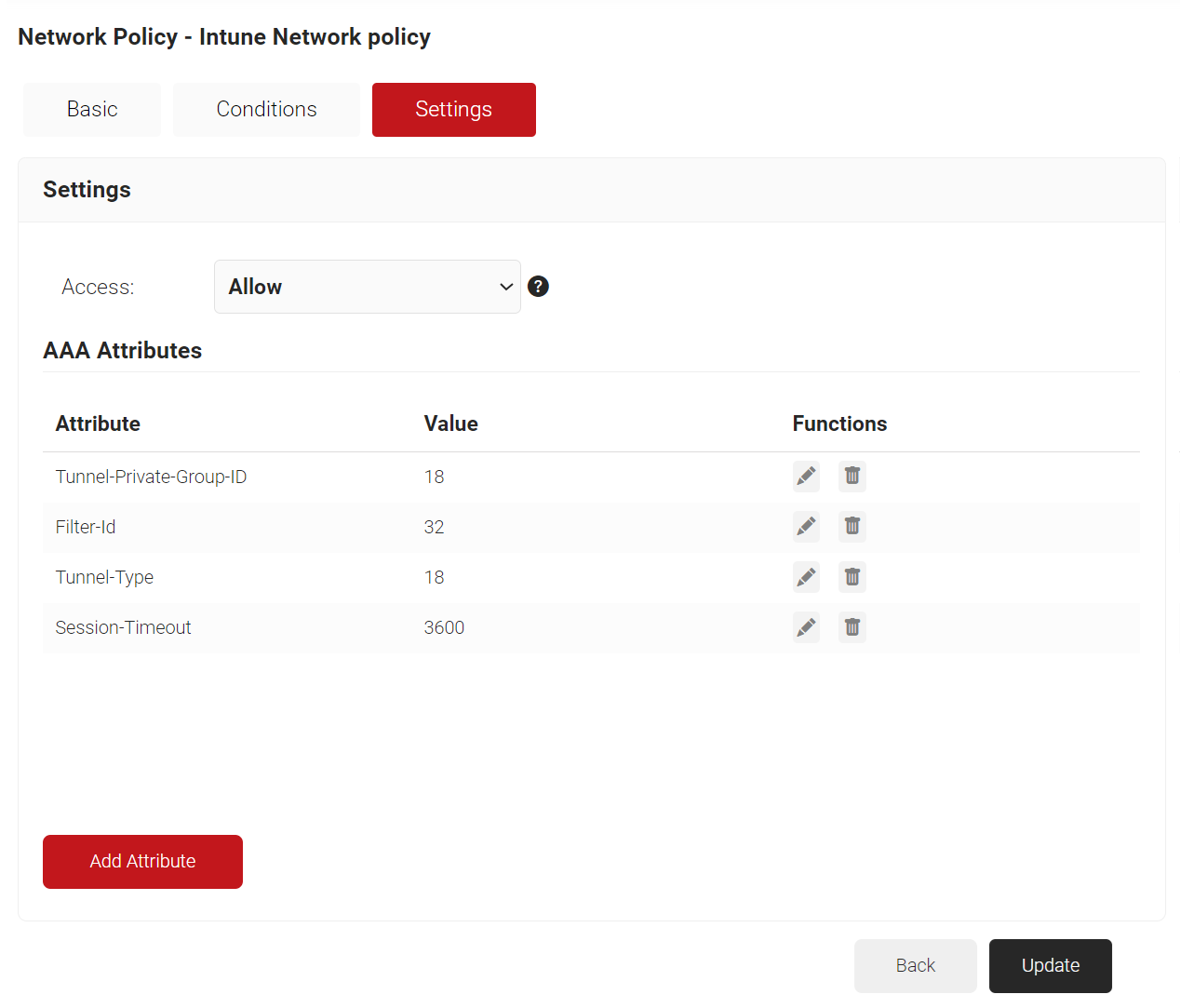
- Under the Settings tab, you can allow or deny the Wi-Fi connection and configure the required RADIUS attributes. These attributes are network parameters that can be sent to the Controller to configure the authenticating devices.
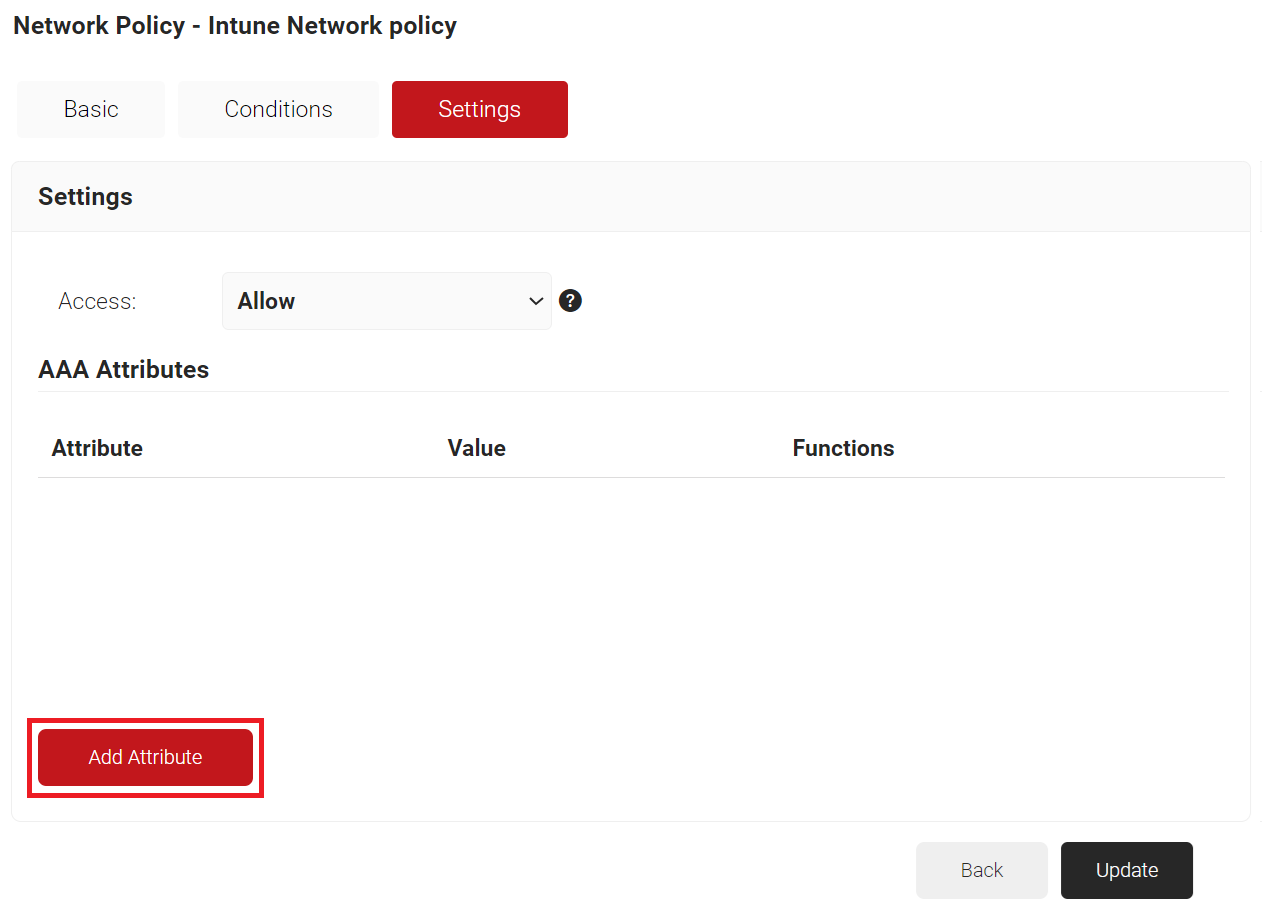
- Click Add Attribute.
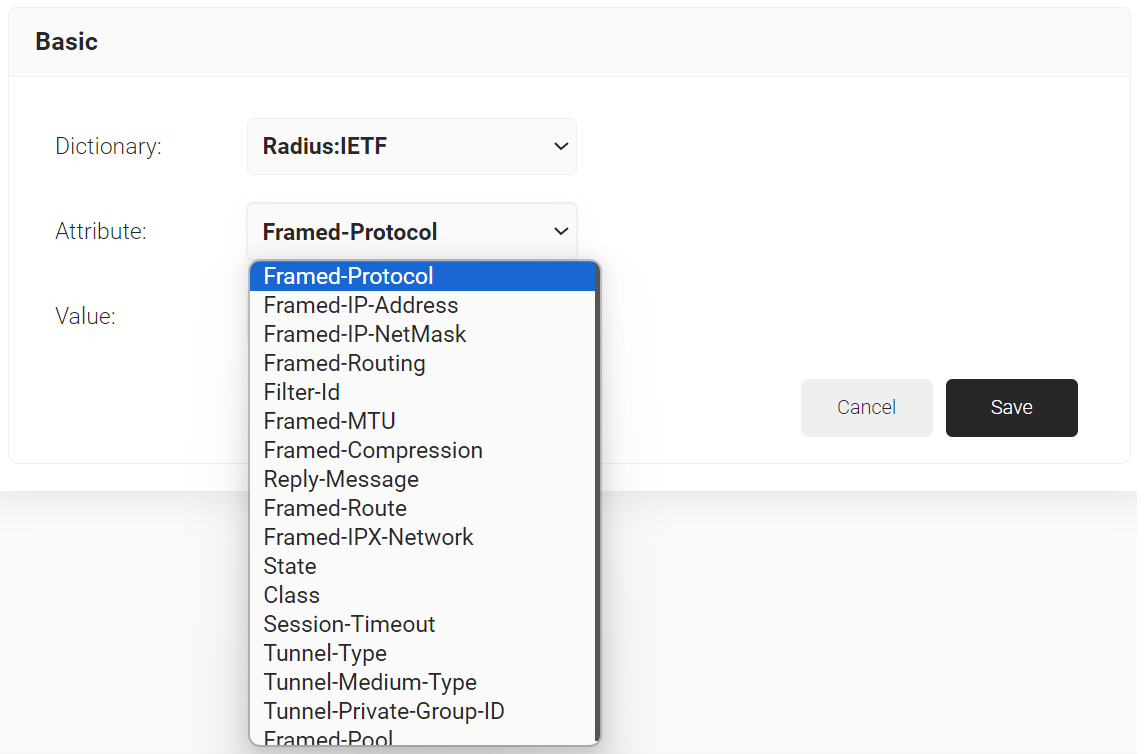
- From the Dictionary drop-down list, select Radius:IETF or Custom.
- RADIUS: IETF – RADIUS IETF represents the standard dictionary of attributes supported by all the Controllers.
- Custom – Custom dictionary of attributes supported by vendors.
- From the Attribute drop-down list, select a RADIUS attribute and enter the value for the RADIUS attribute in the Value field. After successful RADIUS authentication, the specified RADIUS attribute values are sent to the Controller to configure the device.The supported attributes in the RADIUS IETF dictionary are:
- Framed-Protocol
- Framed-IP-Address
- Framed-IP-NetMask
- Framed-Routing
- Filter-ID
- Framed-MTU
- Framed-Compression
- Reply-Message
- Framed-Route
- Framed-IPX-Network
- State
- Class
- Session-Timeout
- Tunnel-Type
- Tunnel-Medium-Type
- Tunnel-Private-Group-ID
- Framed-Pool
- Click Save.
- From the Dictionary drop-down list, select Radius:IETF or Custom.
Trusted Certificate Profiles
You should configure the Trusted Certificate Profile with the certificate of your RADIUS server certificate’s issuing authority. This is to make the devices trust your RADIUS server by validating the RADIUS server certificate. We achieve this server validation in the profile configuration by adding the Root and/or Intermediate Certificate Authority (CA) certificates that issued the RADIUS server certificate. When you assign this profile, the Microsoft Intune-managed devices receive the trusted certificates.
NOTE: For RADIUS vendors, other than the SecureW2 CloudRADIUS server, ensure that you have the Root or Intermediate CA that issues the RADIUS server certificate.
NOTE: You must create a separate profile for each OS platform. The steps to create trusted certificates are similar for each device platform.
Exporting the SecureW2 Root, Intermediate, and RADIUS CA
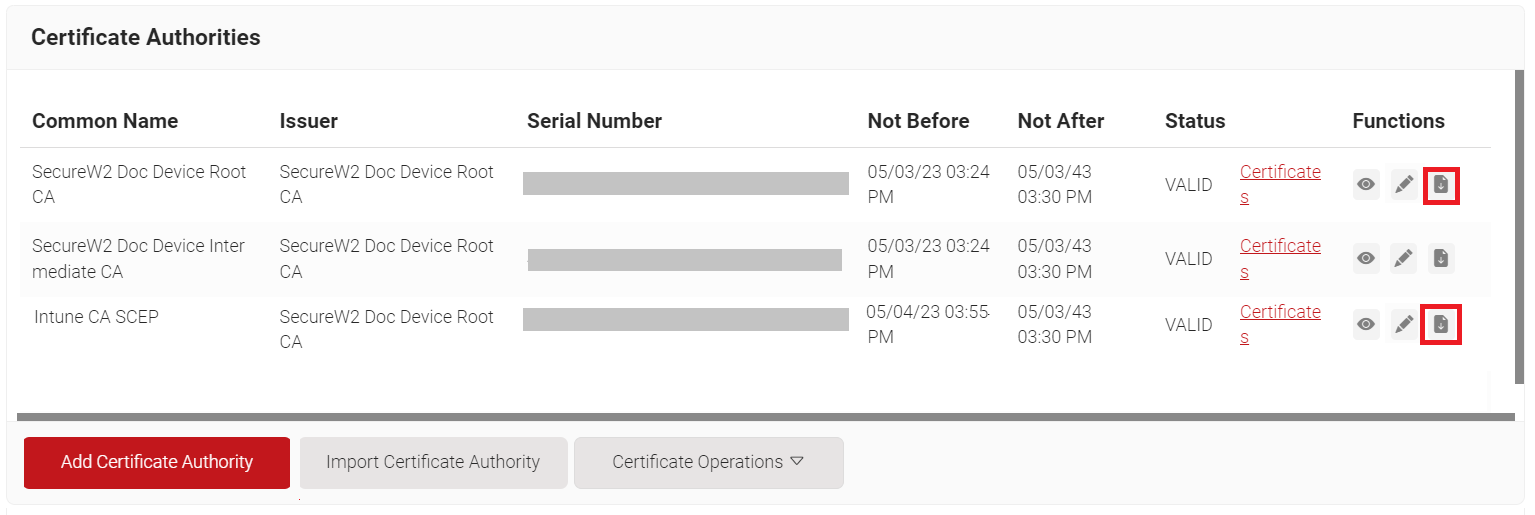
To create trusted profiles in Intune, the Root, Intermediate, and RADIUS Server CA must be uploaded in their respective profiles in the Intune Endpoint manager. To download these certificates from the JoinNow Management portal, follow the below steps:
- Log in to the JoinNow Management Portal.
- Navigate to PKI > Certificate Authorities.
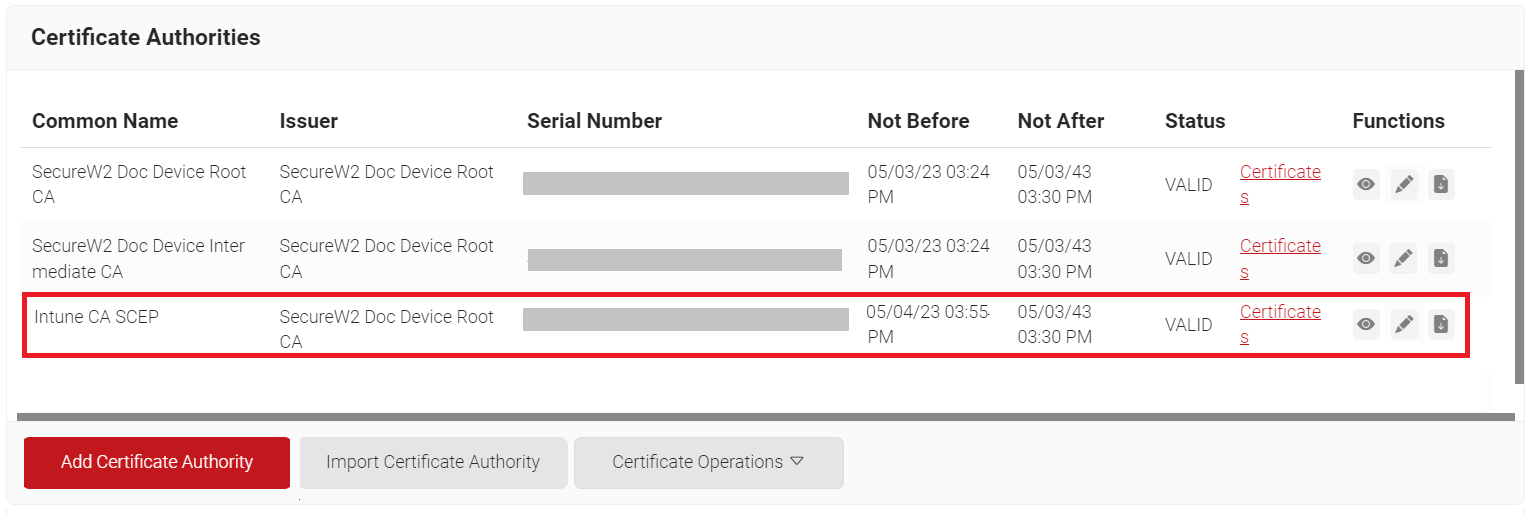
- In the Certificate Authorities section, click the Download link for the Root CA and Intermediate CA issued to your organization (see the Creating an Intermediate CA for Intune SCEP Gateway Integration section). An example of this is explained in the below screenshot:
Exporting RADIUS Root CA
Similarly, for downloading the RADIUS Server Root CA:
- Navigate to Device Onboarding > Network Profiles.
- On the Network Profiles page, click the Edit link of the network profile configured earlier.
- Scroll down to the Certificates section and click Add/Remove Certificate.
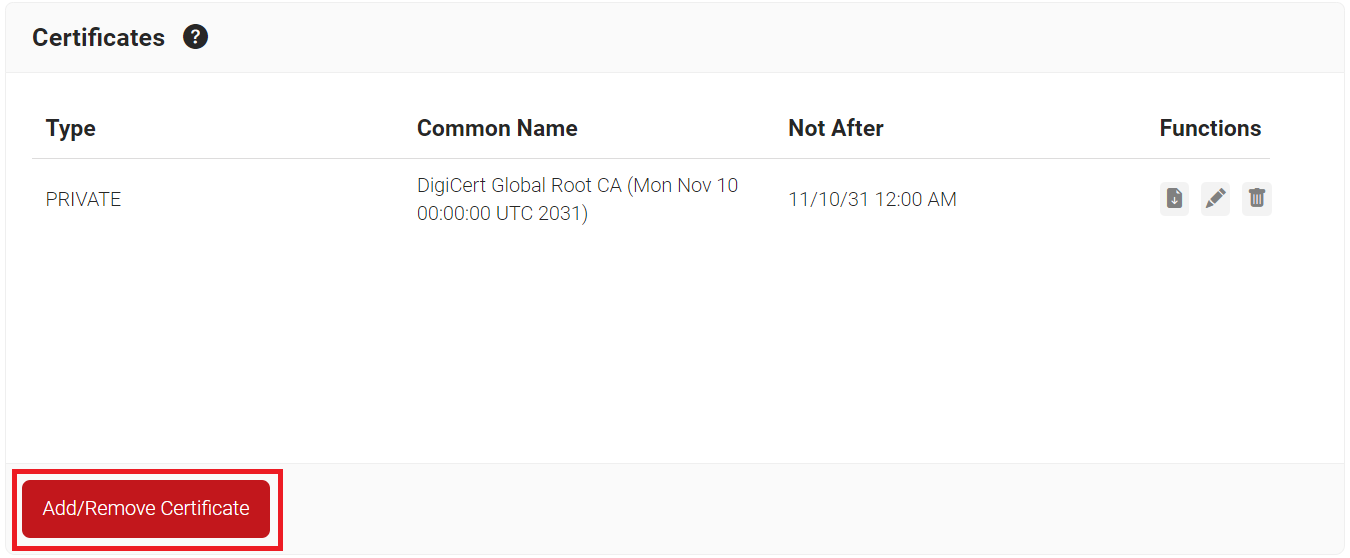
- Check the checkbox next to DigiCert Global Root CA (Mon Nov 10 00:00:00 UTC 2031) as shown in the following screen.
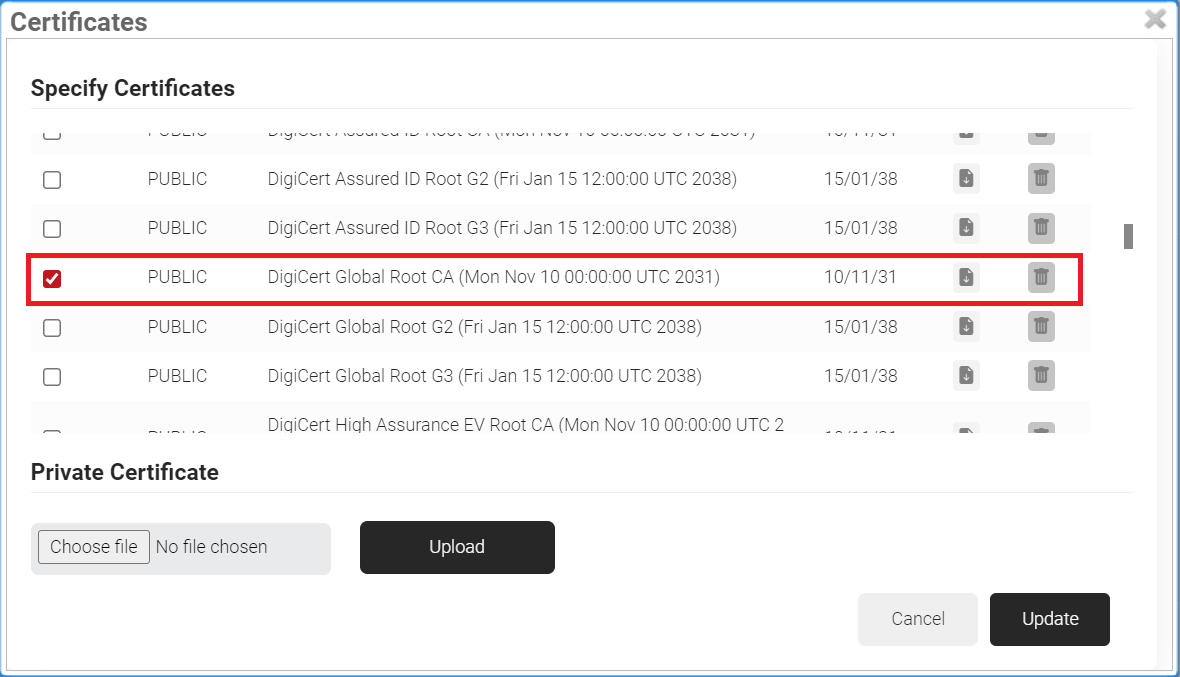
- Click Update.
- The CA appears in the Certificates section.
- Click Download.
Creating Trusted Certificate Profile – Root, Intermediate, and RADIUS Root CA
The downloaded CA certificates must be uploaded to the respective trusted profiles to deploy them in the client devices. Deploying these CA certificates is necessary to form a chain of trust during the enrollment and RADIUS authentication. Intune requires the creation of three trusted certificate profiles:
- Trusted Certificate Profile for Root CA
- Trusted Certificate Profile for Intermediate CA of the RADIUS Server certificate
- Trusted Certificate Profile for Root CA of the RADIUS Server certificate
To create trusted profiles in Intune:
- Sign in to the Microsoft Endpoint Manager portal.
- Navigate to Devices > Configuration.
- Click Create and select New Policy.
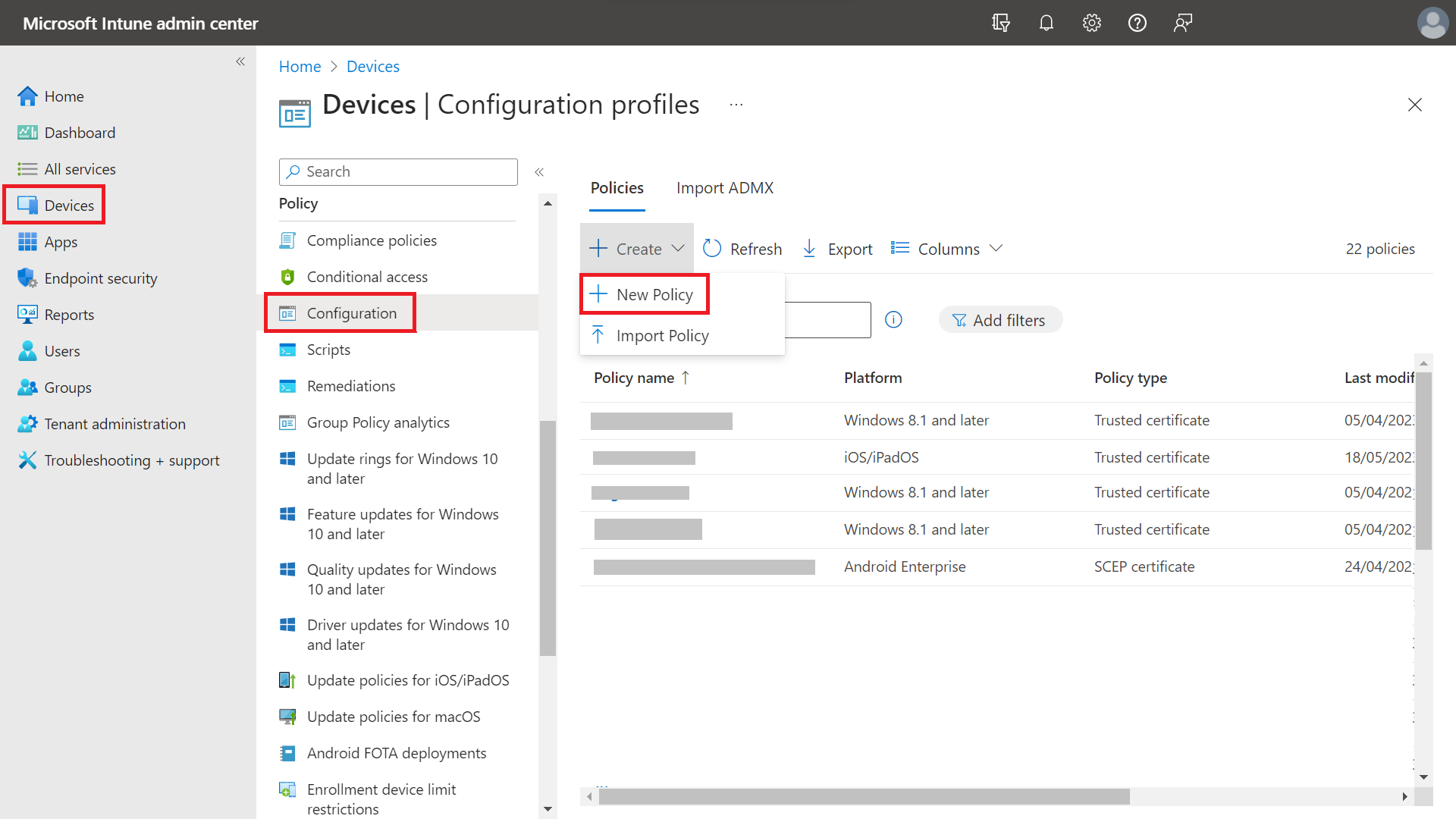
- On the Create a profile page, from the Platform drop-down list, select the device platform for this trusted certificate. The options are:
- Android device administrator
- Android (AOSP)
- Android Enterprise
- iOS/iPadOS
- macOS
- Windows 10 and later
- Windows 8.1 and laterNOTE: You must create a separate profile for each OS platform. The steps to create trusted certificates are similar for each device platform.
- From the Profile type drop-down list, select Templates, and then select Trusted certificate.
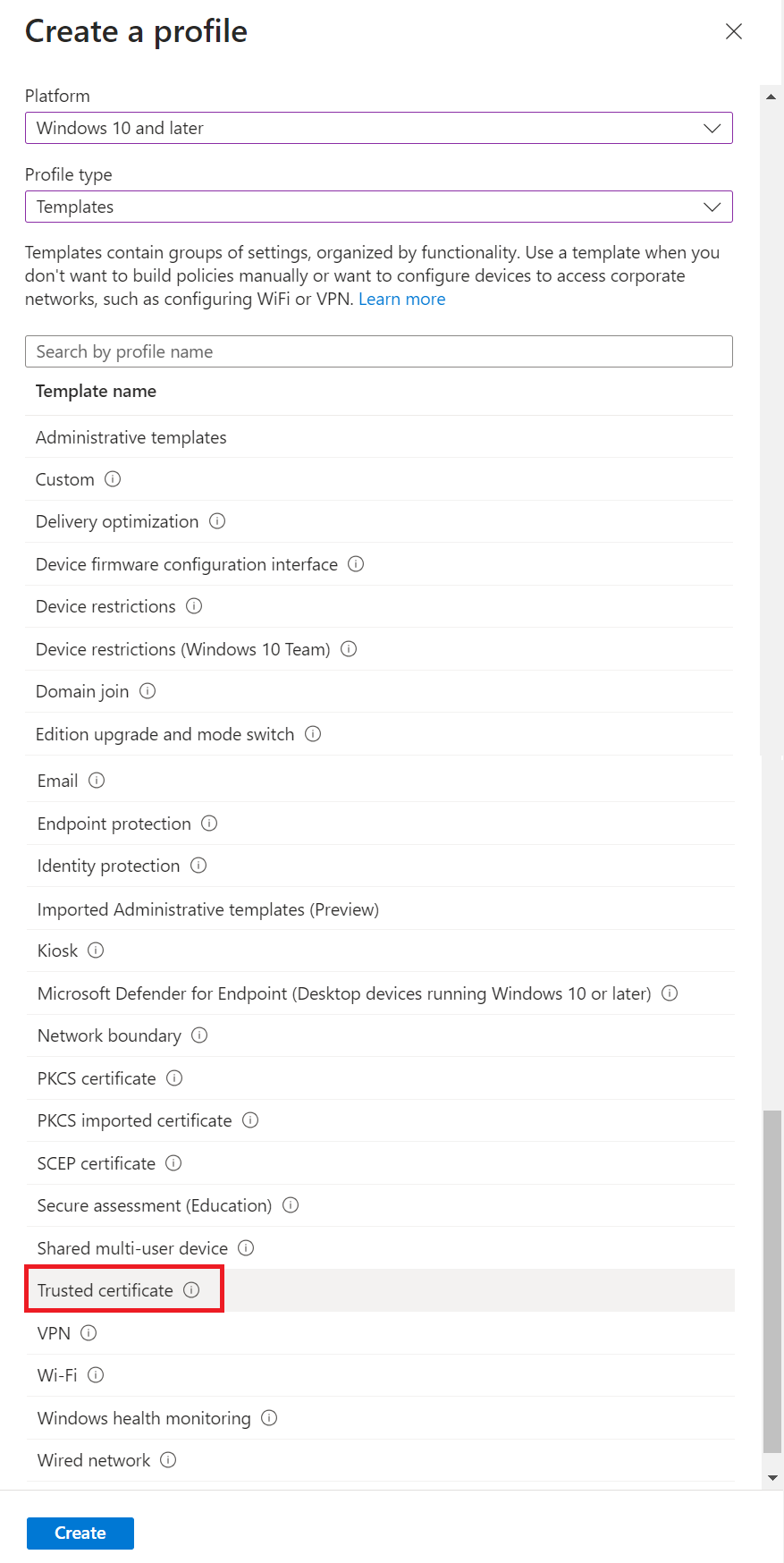
- Click Create.
- On the Trusted certificate page, in the Basics section, enter the name of the Trusted Certificate in the Name field. For easy identification, suitable naming conventions with “Root, Intermediate, and RADIUS CA” can be used.
- In the Description field, enter a suitable description for the trusted certificate.
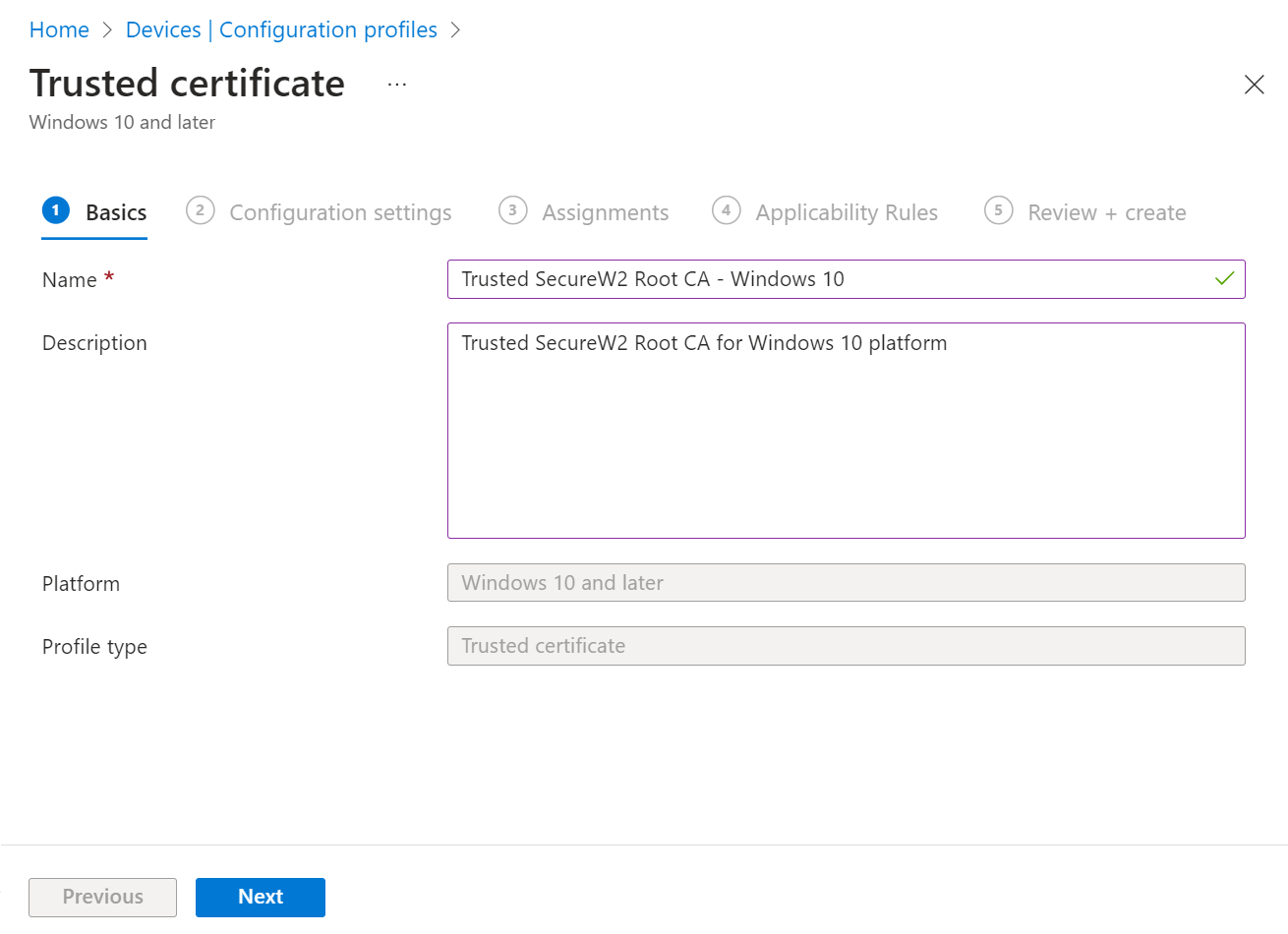
- Click Next.
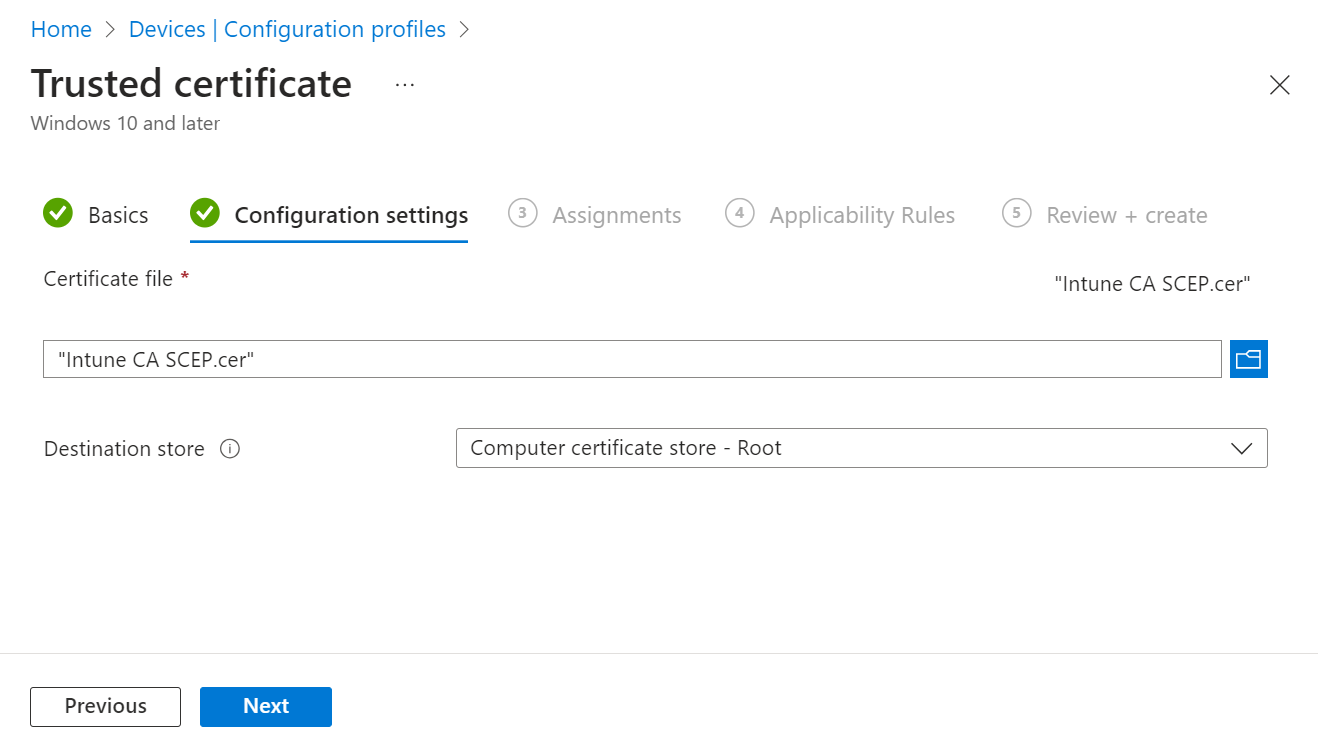
- In the Configuration settings section, click the Browse button in the Certificate file field. Select the certificate appropriate to the trusted profile being created, as shown in the below table:
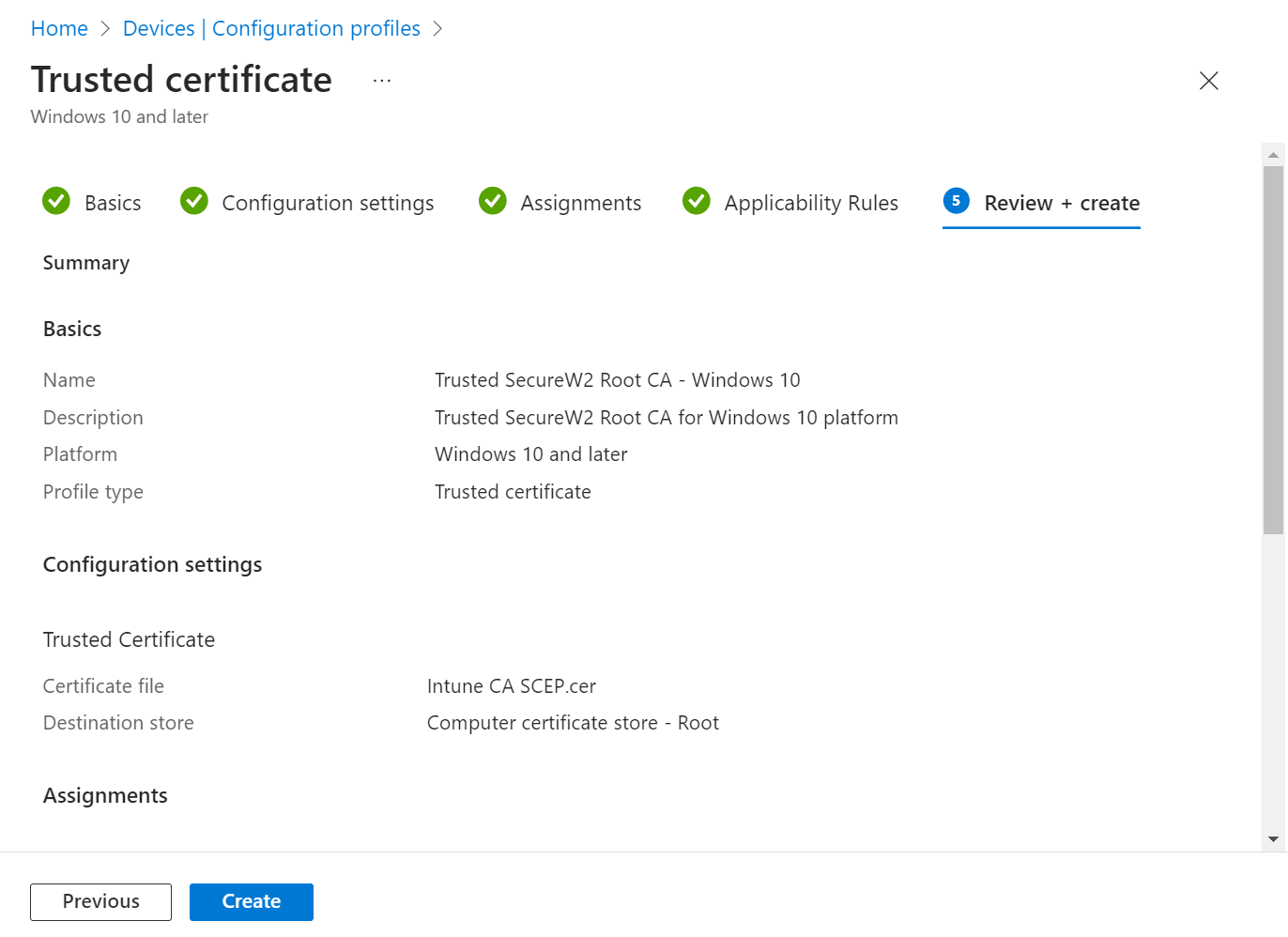
Trusted Profile mapped with Intermediate CA Trusted Profile mapped with Root CA Trusted Profile mapped with RADIUS Server Root CA Upload the Intermediate CA downloaded from the JoinNow portal in Exporting the SecureW2 Root, Intermediate, and RADIUS CA Upload the Root CA of the organization downloaded from the JoinNow portal in Exporting the SecureW2 Root, Intermediate, and RADIUS CA Upload the Root CA of the organization downloaded from the JoinNow portal in Exporting RADIUS Root CA From the Destination store drop-down list, select “Computer certificate store – Intermediate” From the Destination store drop-down, select “Computer certificate store – Root”. From the Destination store drop-down, select “Computer certificate store – Root”. - Click Next.
- Assign the profile to the appropriate Groups and Rules, review it, and click Create.
SCEP Profile for SecureW2 SCEP Certificate Requests
The SCEP profile is required for end-user devices to communicate with the SCEP Server—SecureW2 CloudConnector and request the enrollment of end-user certificates.
NOTE: You must create a separate profile for each OS platform. The steps to create trusted certificates are similar for each device platform.
Creating a SCEP Certificate Profile
To create a SCEP certificate profile, perform the following steps:
- Log in to the Microsoft Endpoint Manager portal.
- Navigate to Devices > Configuration.
- Click Create and select New Policy.

- On the Create a profile page, from the Platform drop-down list, select the device platform for this SCEP certificate. You can select one of the following platforms for device restriction settings:
- Android device administrator
- Android (AOSP)
- Android Enterprise
- iOS/iPadOS
- macOS
- Windows 10 and later
- Windows 8.1 and laterNOTE: You must create a separate profile for each OS platform. The steps to create trusted certificates are similar for each device platform.
- From the Profile type drop-down list, select Templates and then select SCEP certificate.
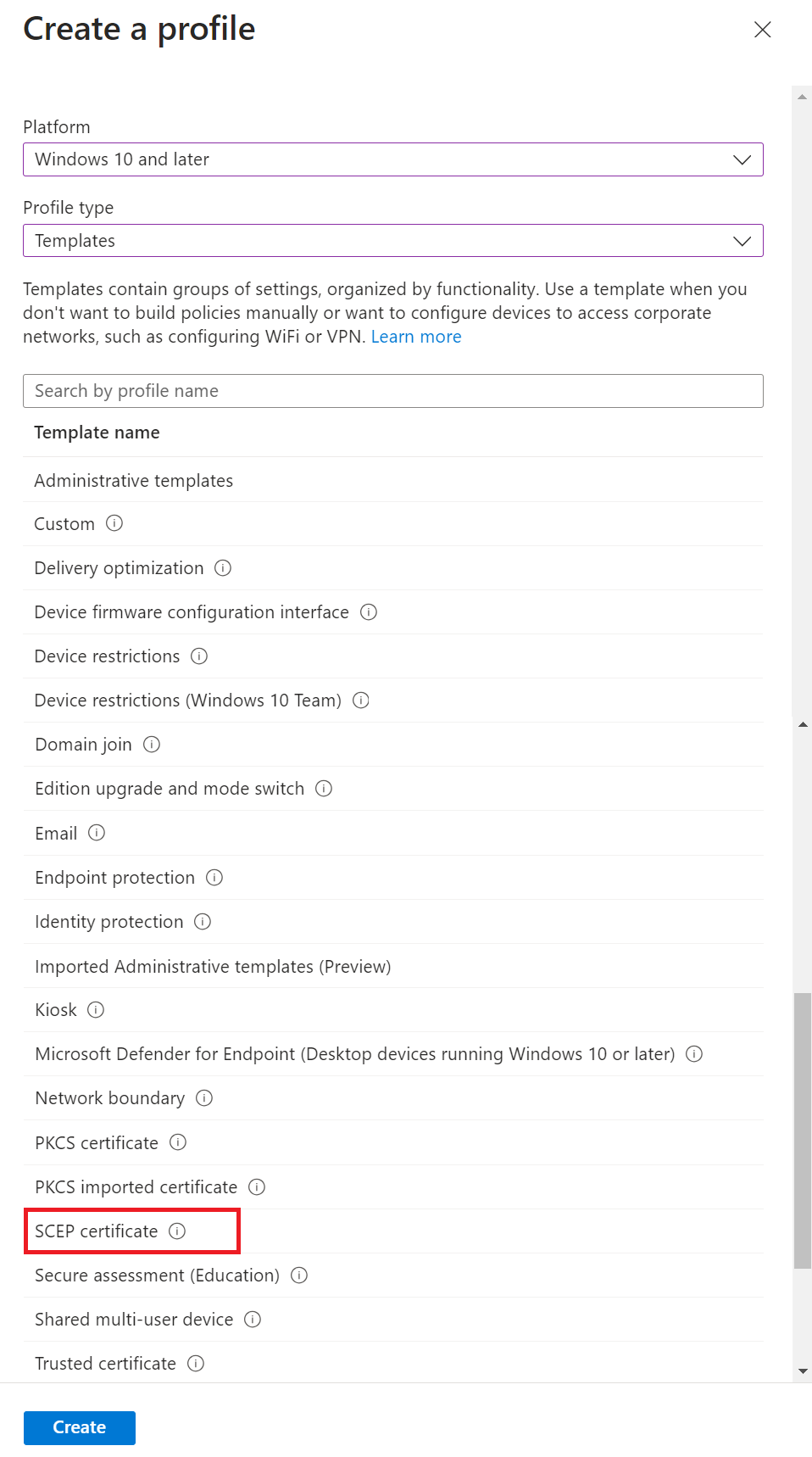
NOTE: You must create a separate profile for each OS platform. The steps to create trusted certificates are similar for each device platform. - Click Create.
- On the SCEP certificate page, in the Basics section, enter the name of the SCEP certificate in the Name field.
- In the Description field, enter a suitable description for the SCEP certificate.
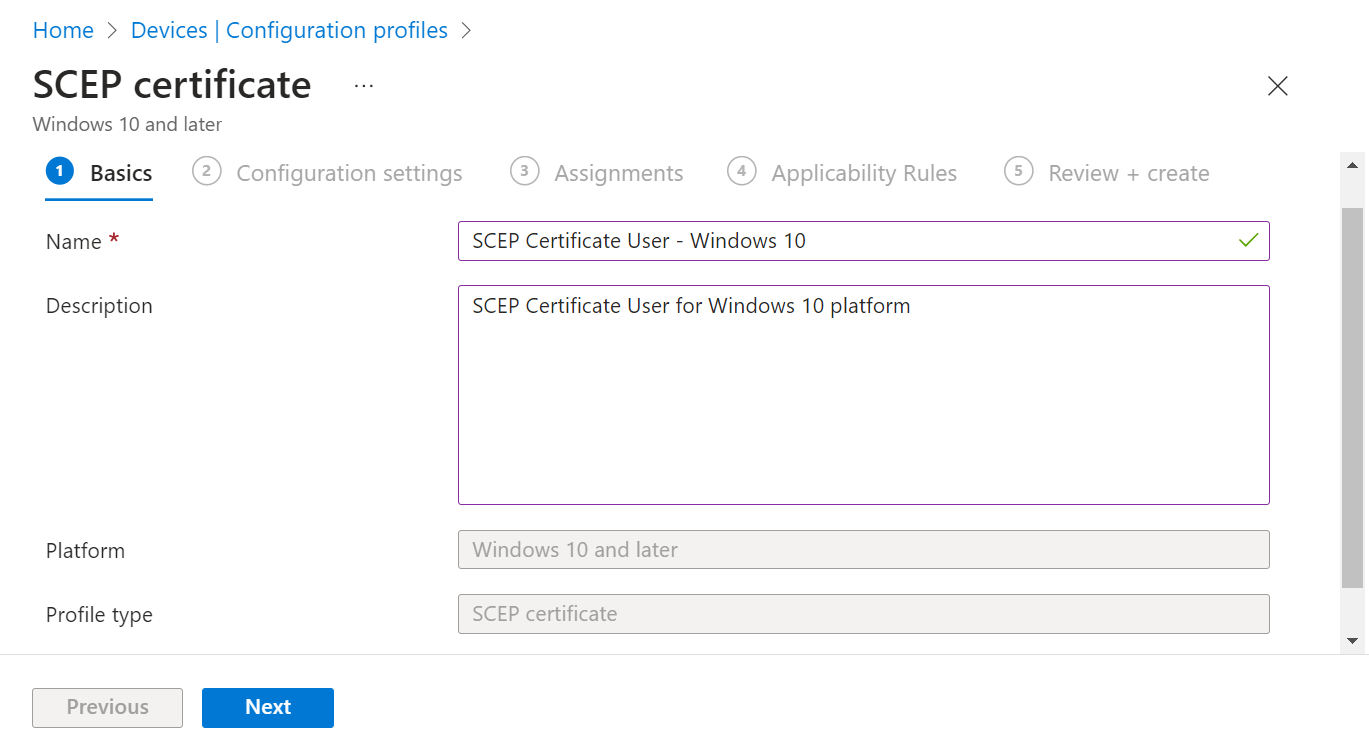
- Click Next. The Configurations settings tab opens. Two types of certificates can be issued to a client device.
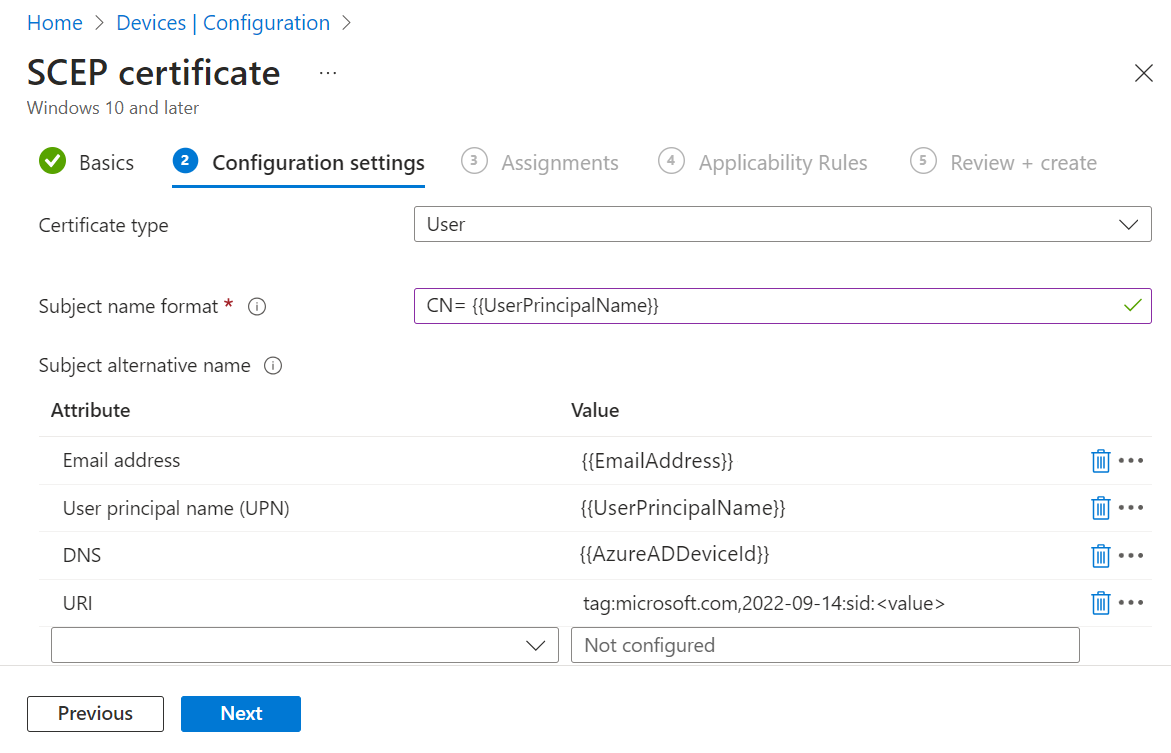
- For Certificate Type – User
- For Certificate Type – Device
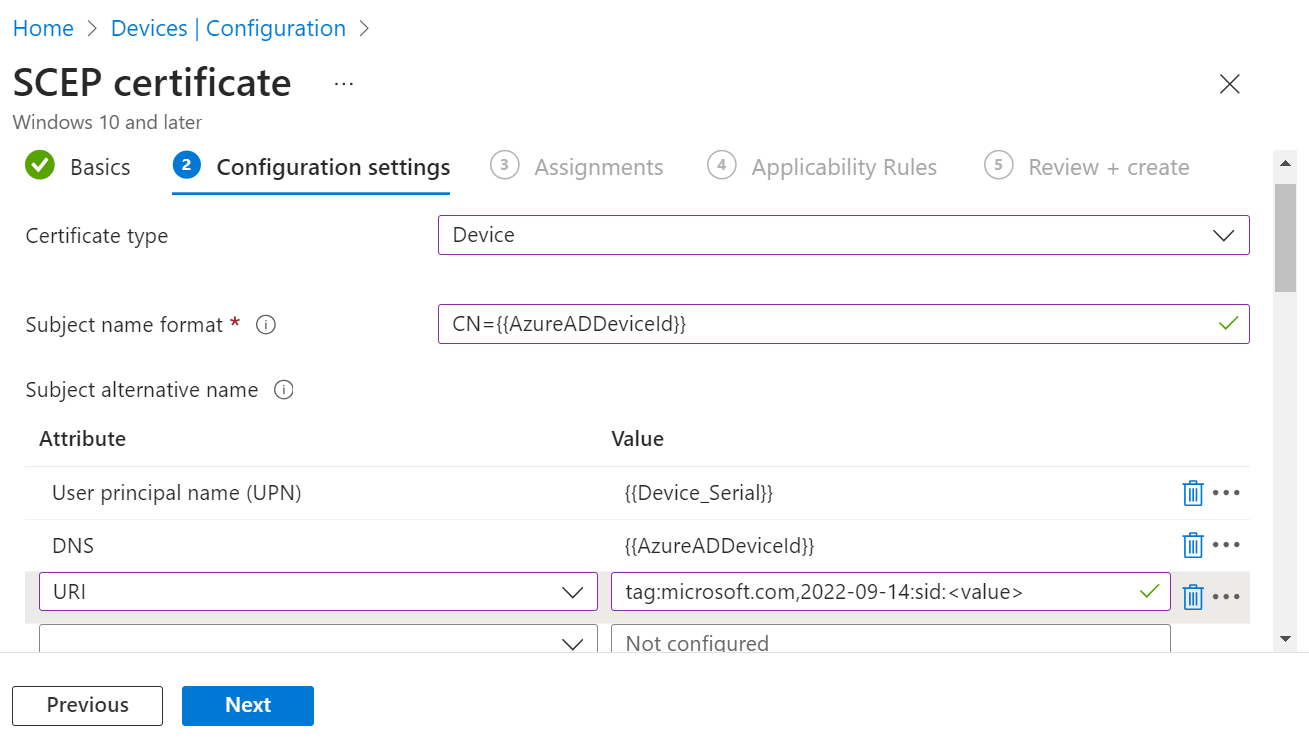
The following tabular column shows the recommended configuration values for the two SCEP profiles:Field User Certificate Device Certificate Certificate type Select User Select Device Subject name format CN= {{UserPrincipalName}} (recommended by SecureW2)
CN= {{UserName}}
CN= {{EmailAddress}}
CN={{AzureADDeviceId}} (recommended by SecureW2) Subject alternative name - Email address – {{EmailAddress}}
- User principal name (UPN) – {{UserPrincipalName}}
- DNS – {{AzureADDeviceId}}
- URI – tag:microsoft.com,2022-09-14:sid:<value>
- Email address – Not required
- User principal name (UPN) – {{Device_Serial}}
- DNS – {{AzureADDeviceId}}
- URI – tag:microsoft.com,2022-09-14:sid:<value>
Certificate validity period Validity in number of Years Key storage provider (KSP) Select Enroll to Trusted Platform Module (TPM) KSP if present, otherwise Software KSP to store the certificate’s key. Key usage Select both the Key encipherment and Digital signature checkboxes to exchange the certificate’s public key.
- Key encipherment: Allows key exchange only when the key is encrypted.
- Digital signature: Allows key exchange only when a digital signature protects the key.
Key size (bits) Select 2048 or 4096 as necessary. Hash algorithm Select SHA-2, the highest level of security that the connecting devices support. 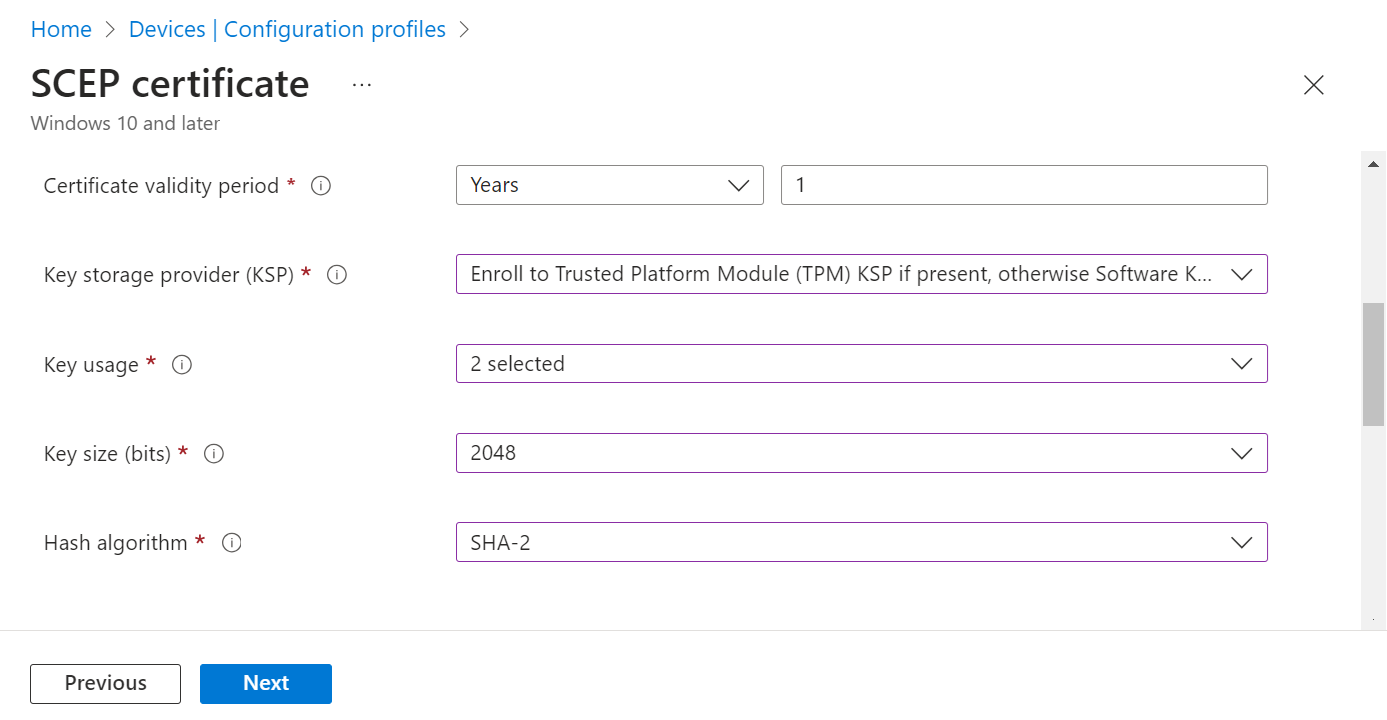
- For Certificate Type – User
- Click + Root Certificate.
- In the Root Certificate pop-up window, select the profile created earlier (see the Exporting the SecureW2 Root, Intermediate, and RADIUS CA section).
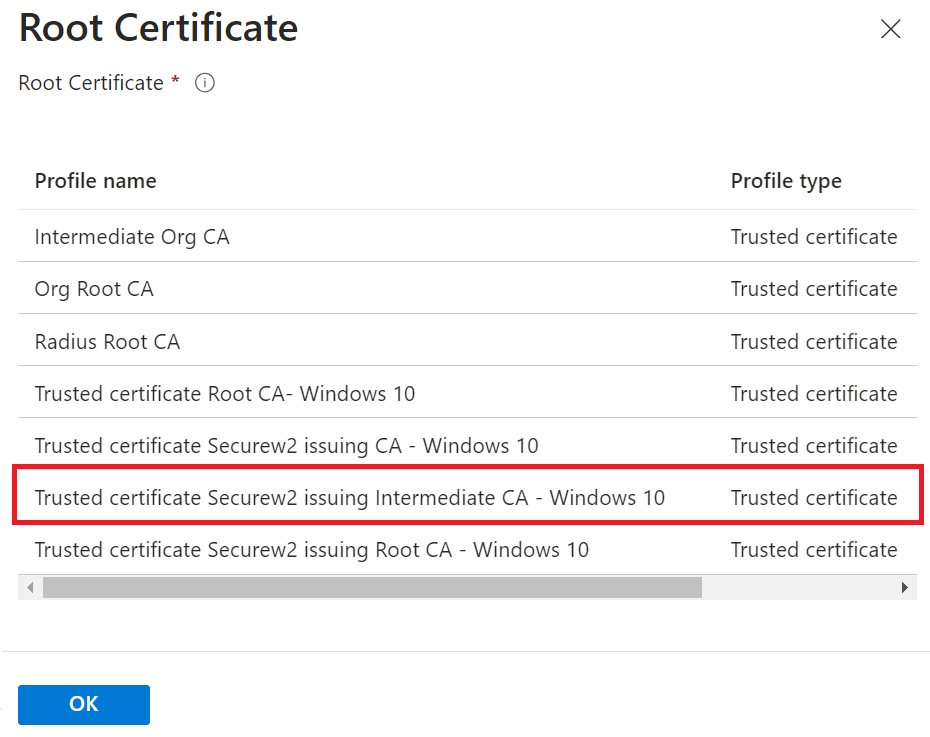
- Click OK.
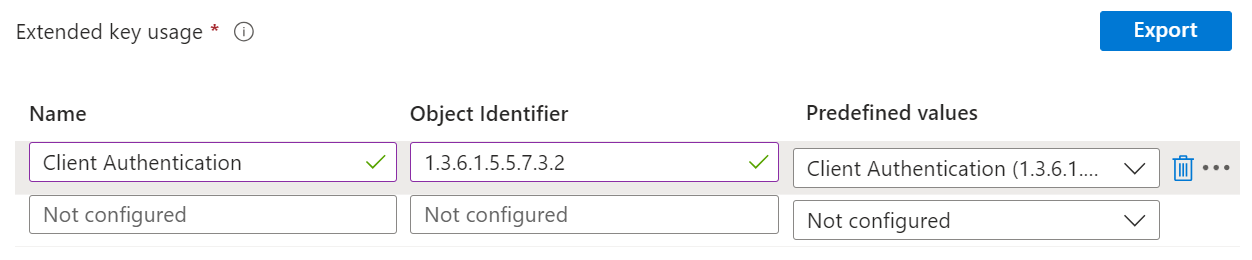
- Under the Extended key usage section, add values for the certificate’s intended purpose. In most cases, the certificate requires client authentication for the user to authenticate to a server.
- In the Name field, enter the name of the extended key usage.
- In the Object Identifier field, enter a unique string of decimal numbers to identify an object.
- From the Predefined values drop-down list, select Client Authentication.
- Under the Enrollment Settings section, in the Renewal threshold (%) field, enter the percentage of the certificate lifetime that remains before the device requests renewal of the certificate. The recommended value in Microsoft Intune is 20%.
- In the SCEP Server URLs field, enter the Endpoint URI generated from the JoinNow Management Portal (see the Creating an Intune CA IDP section).
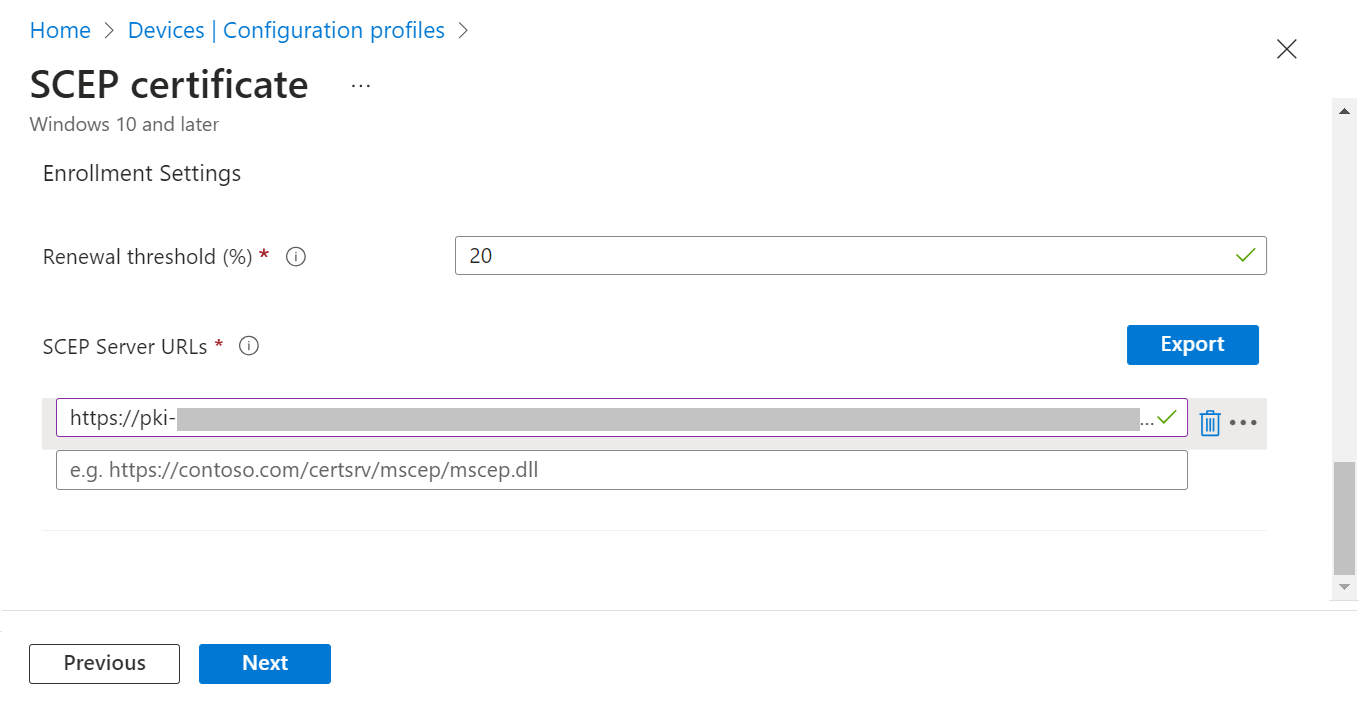
- Click Next.
- Assign the profile to the appropriate Groups and Rules, review it, and click Create.
Wi-Fi Profile for Secure SSID Configuration
Microsoft Intune includes built-in Wi-Fi settings that you can deploy to users and devices in your organization. This group of settings is called a profile, which can be assigned to different users and groups. Once you assign users a profile, they can obtain access to the network without configuring it themselves.
Creating a Wi-Fi Profile
- Sign in to the Microsoft Endpoint Manager portal.
- Navigate to Devices > Configuration.
- Click Create and select New Policy.
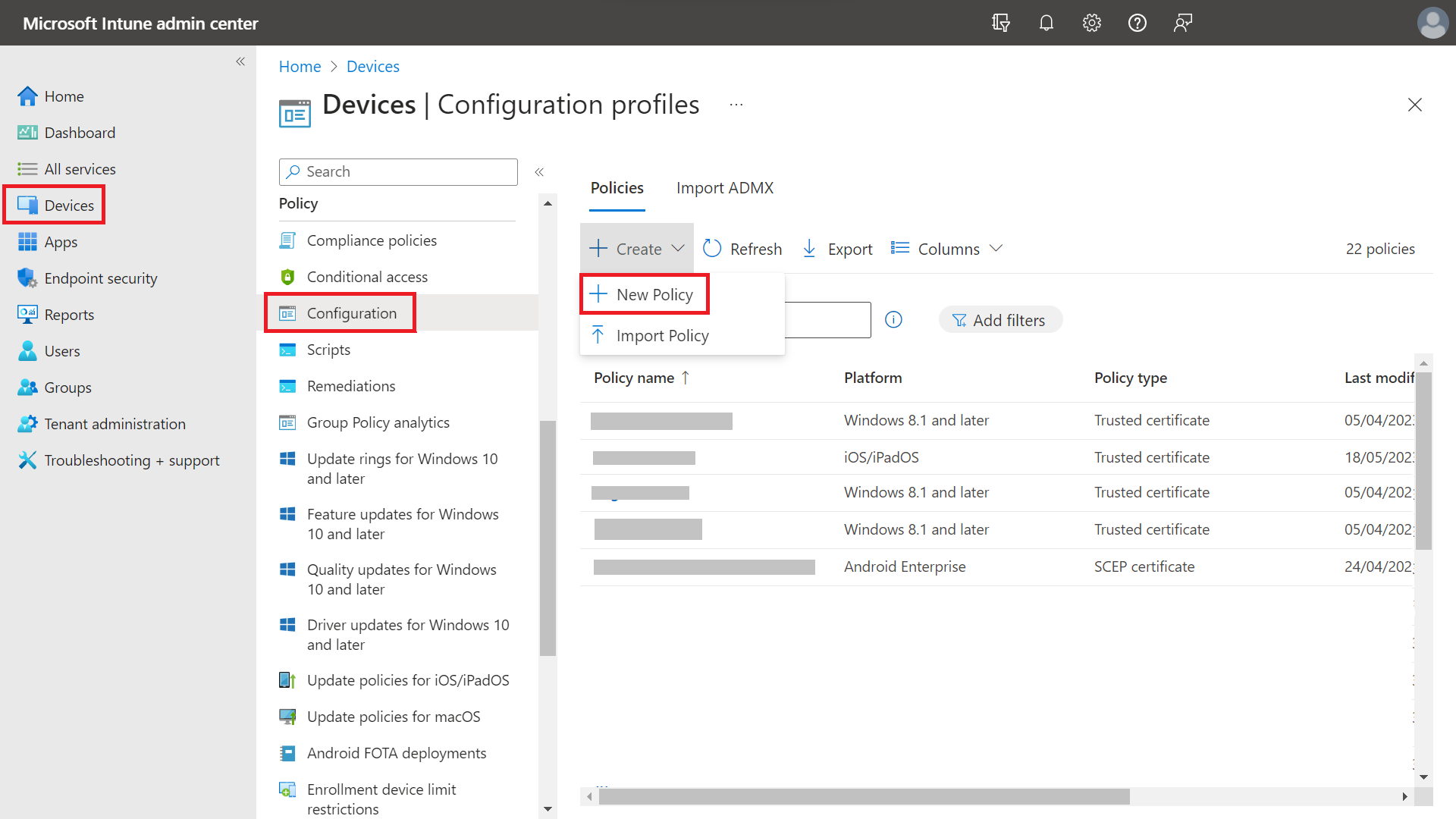
- On the Create a profile page, from the Platform drop-down list, select the device platform for this trusted certificate. The options are:
- Android device administrator
- Android (AOSP)
- Android Enterprise
- iOS/iPadOS
- macOS
- Windows 10 and later
- Windows 8.1 and later
NOTE: You must create a separate profile for each OS platform. The steps to create trusted certificates are similar for each device platform.
- From the Profile type drop-down list, select Templates and then select Wi-Fi.
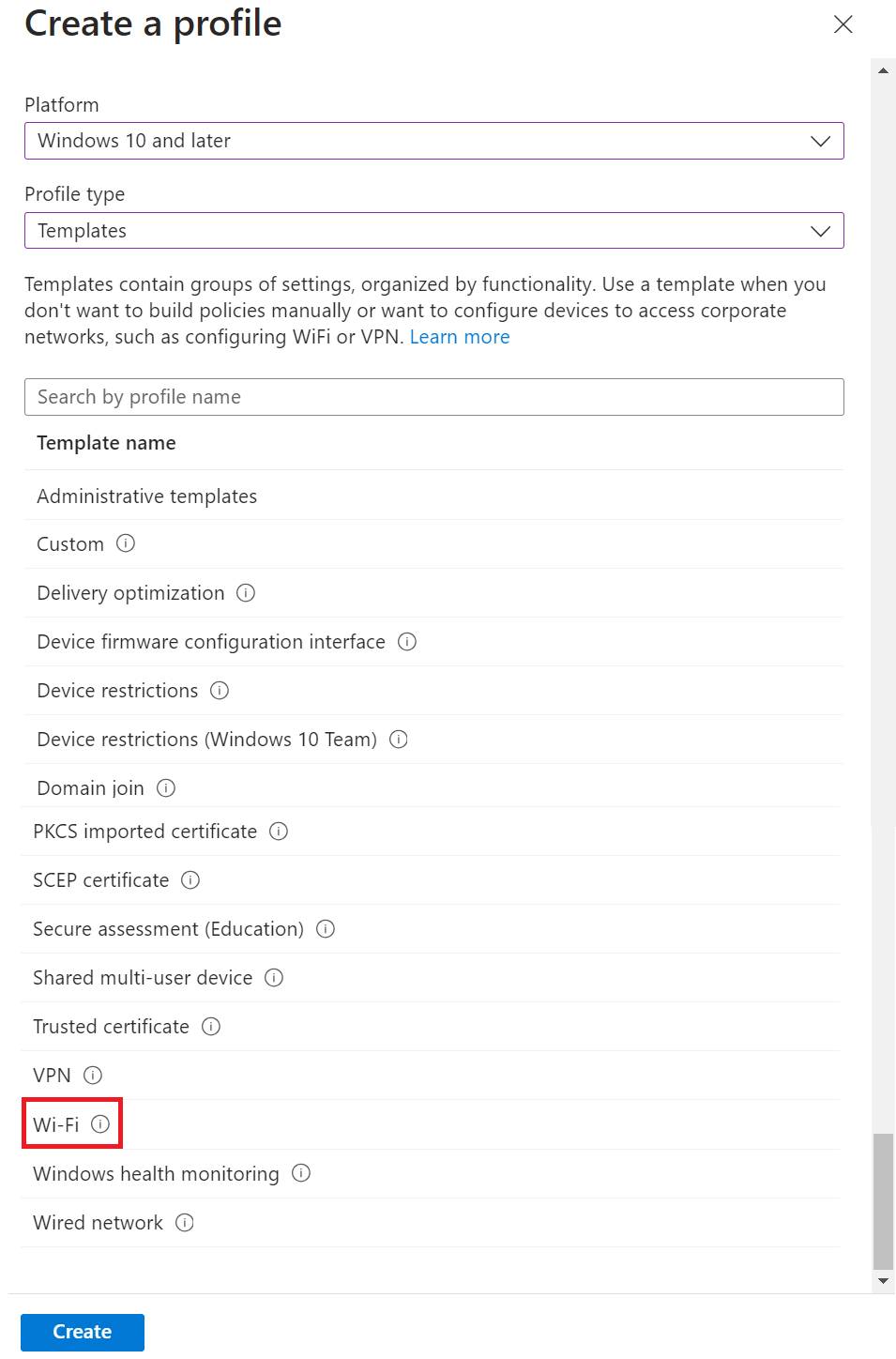
- Click Create.
- On the Wi-Fi page, in the Basics section, enter the Wi-Fi’s name in the Name field.
- In the Description field, enter a suitable description for the Wi-Fi.
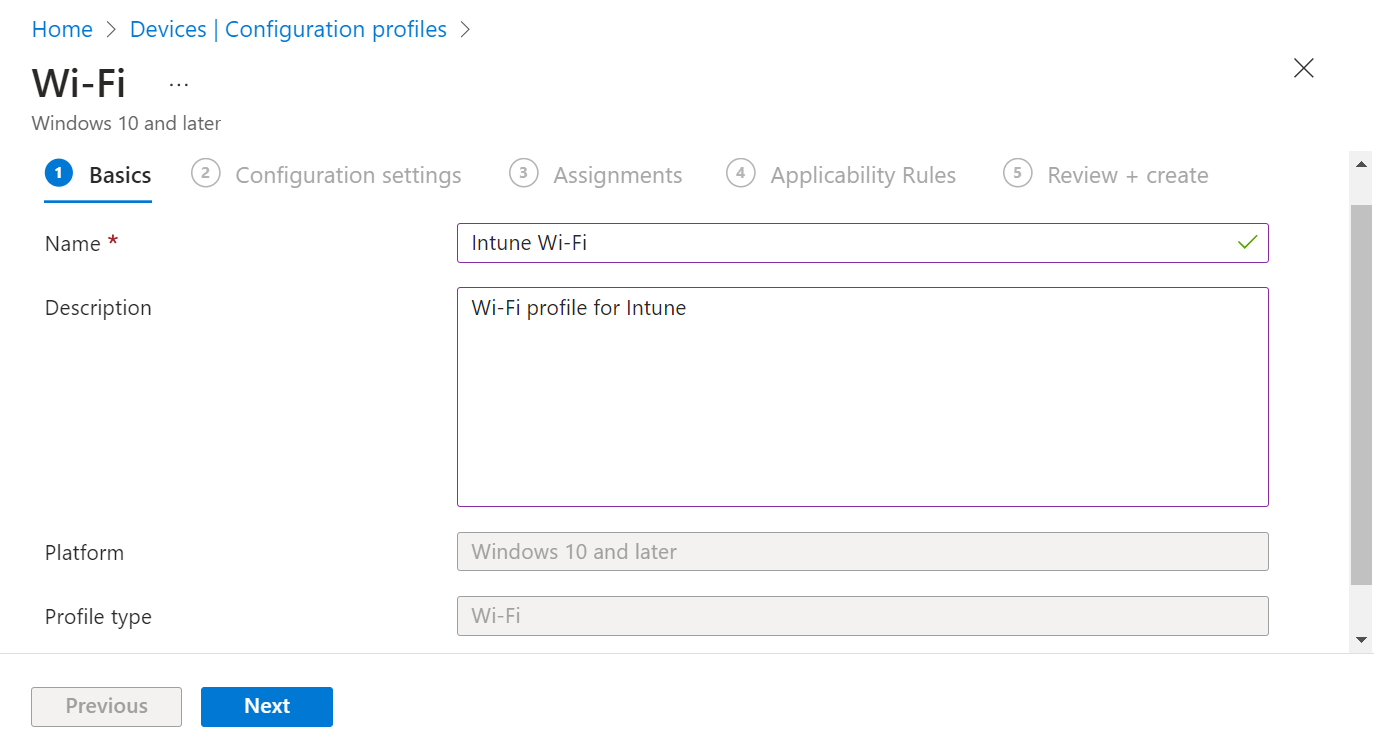
- Click Next.
- In the Configuration settings section, from the Wi-Fi type drop-down list, select any one of the following options:
- Basic
- Enterprise
- Configure your Wi-Fi settings and click Next.
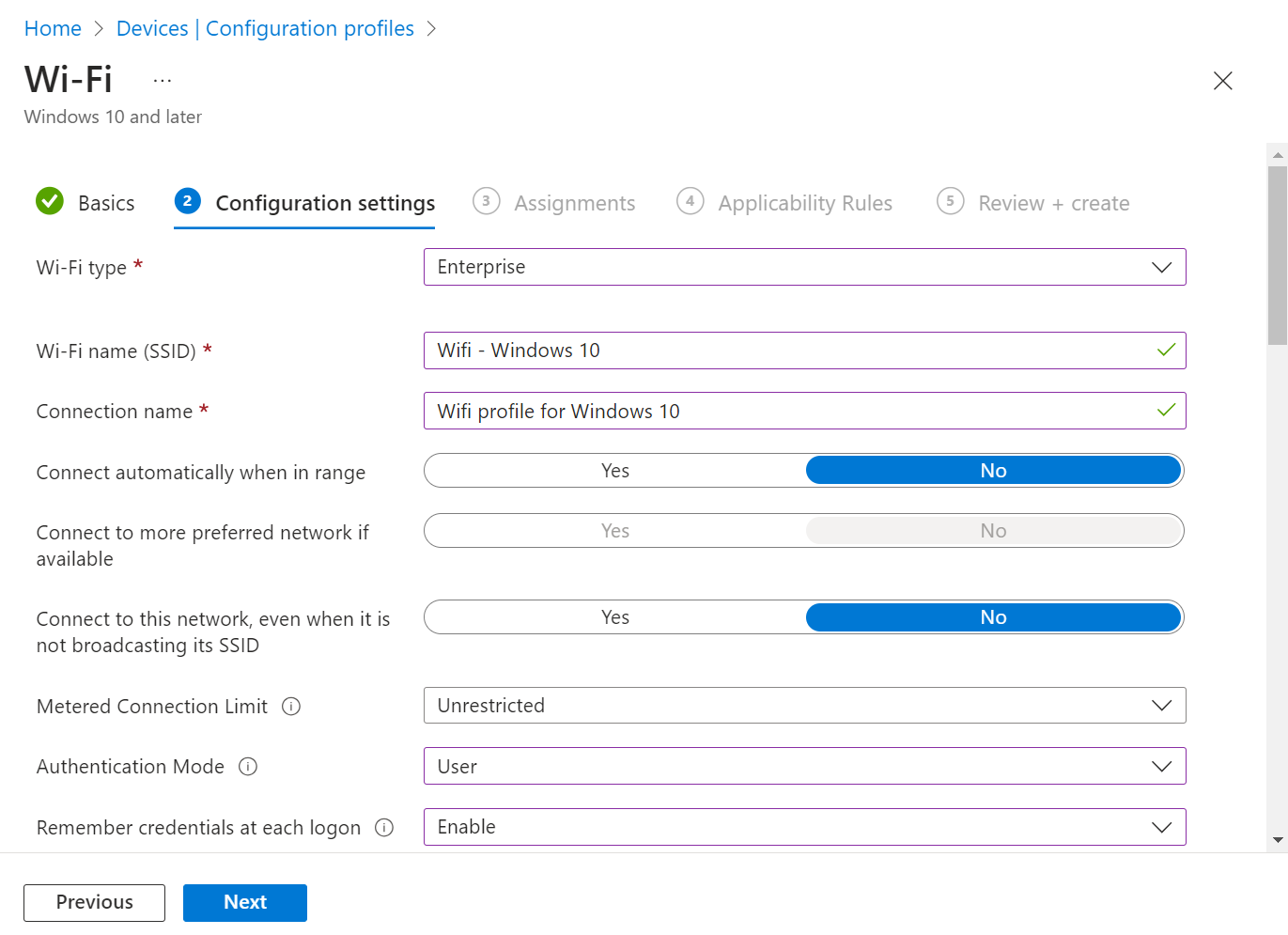
- Assign the profile to appropriate Groups and Rules, review it, and click Create.
Assign a Device Profile
After creating a profile, you must specify the devices to which the profiles are to be pushed. To assign the devices, perform the following steps:
- Sign in to the Microsoft Endpoint Manager portal.
- Navigate to Devices > Configuration.
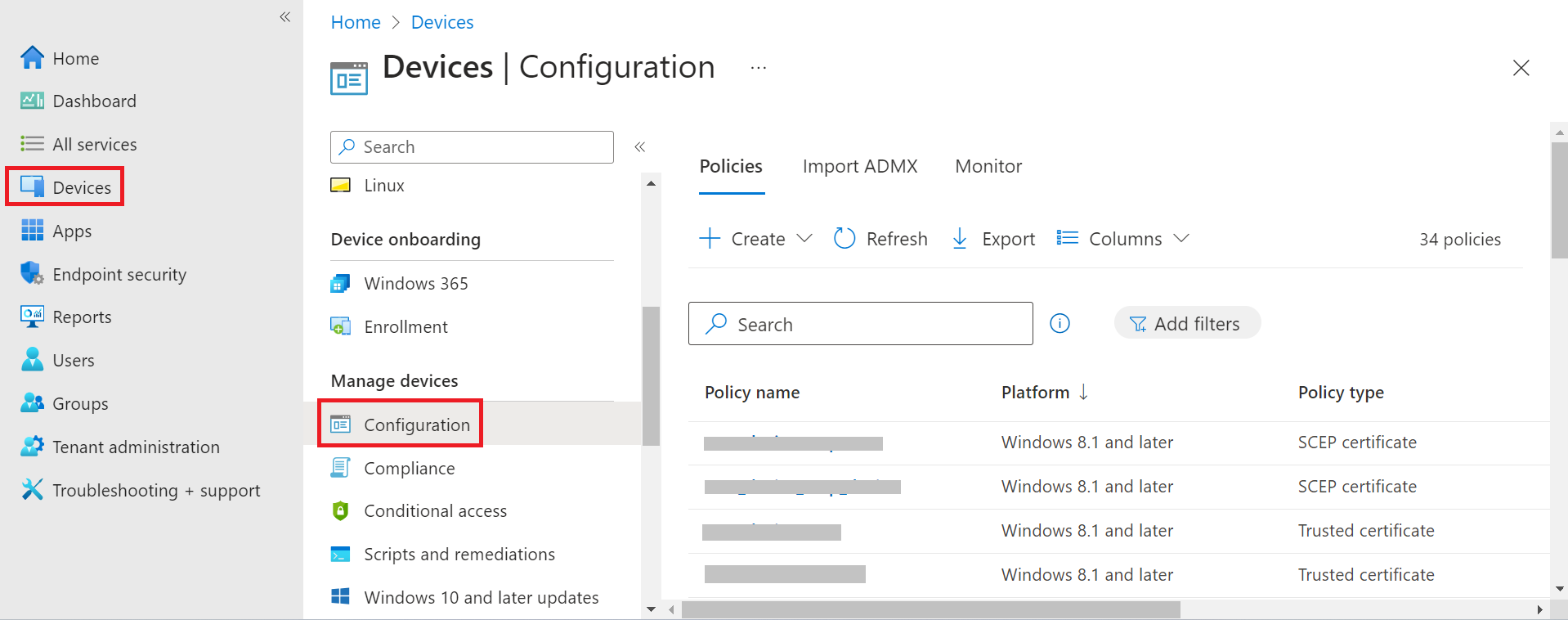
- Select the profile to which you want to assign a policy to users or groups.
- Scroll to the Assignments section and click the Edit link.
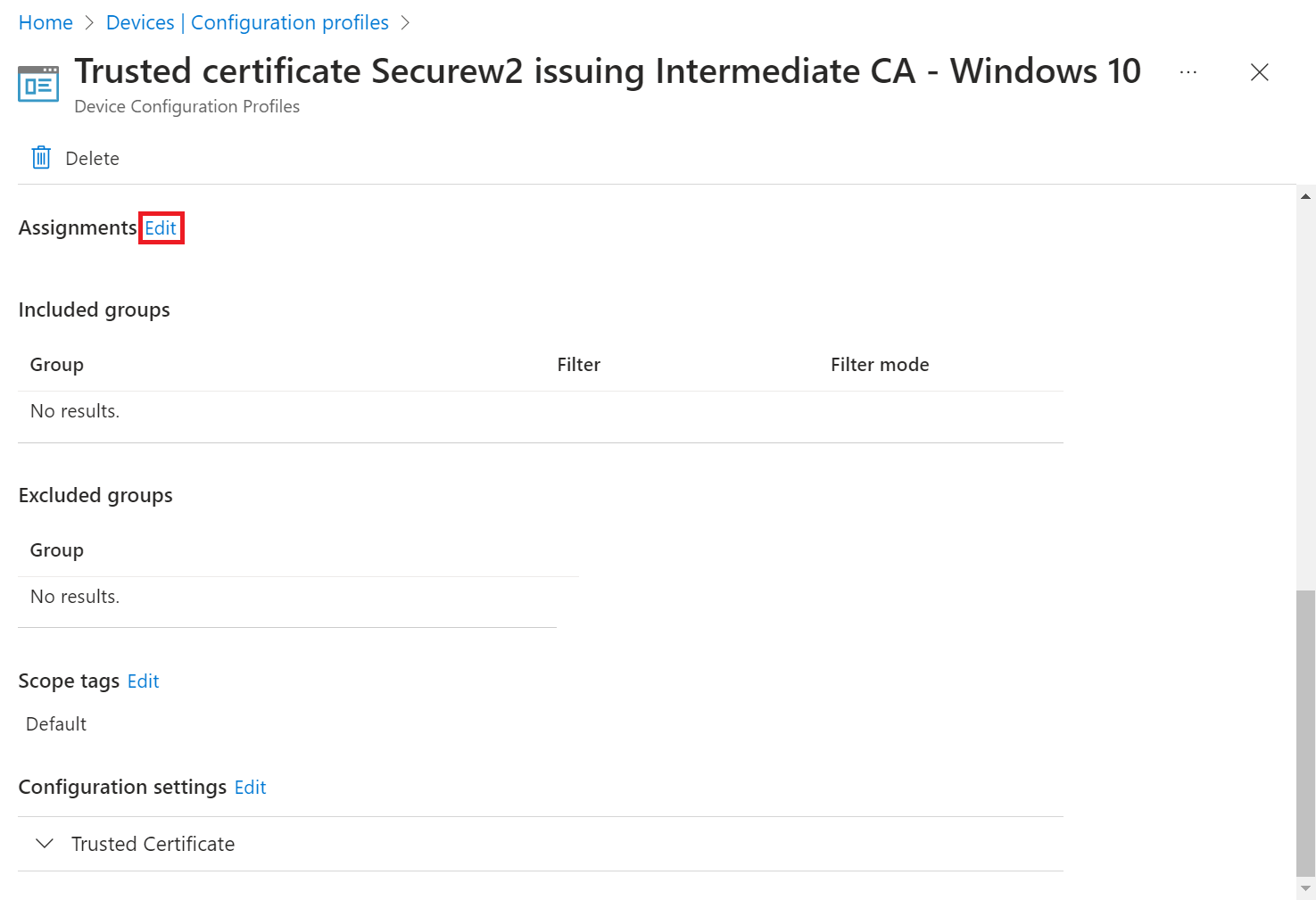
- Under the Included groups or Excluded groups section, click Add groups to add one or more Entra ID Groups. To apply the policy to all relevant devices, select Add all users or Add all devices.
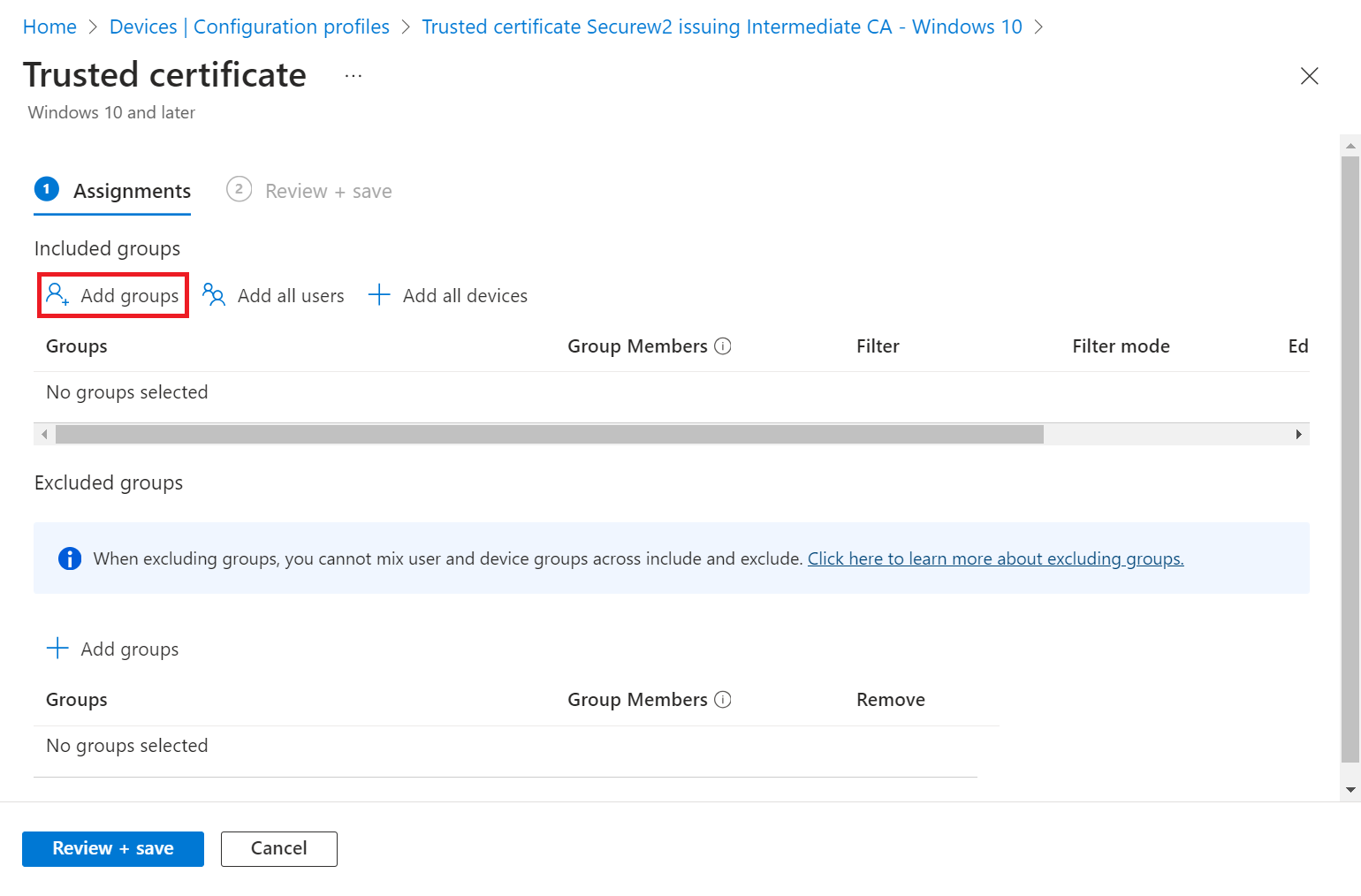
NOTE: If you click Add all users or Add all devices , the Add groups option is disabled. - On the Select groups to include page, select the Entra ID group to which the policy must be assigned and click Select to add the group.
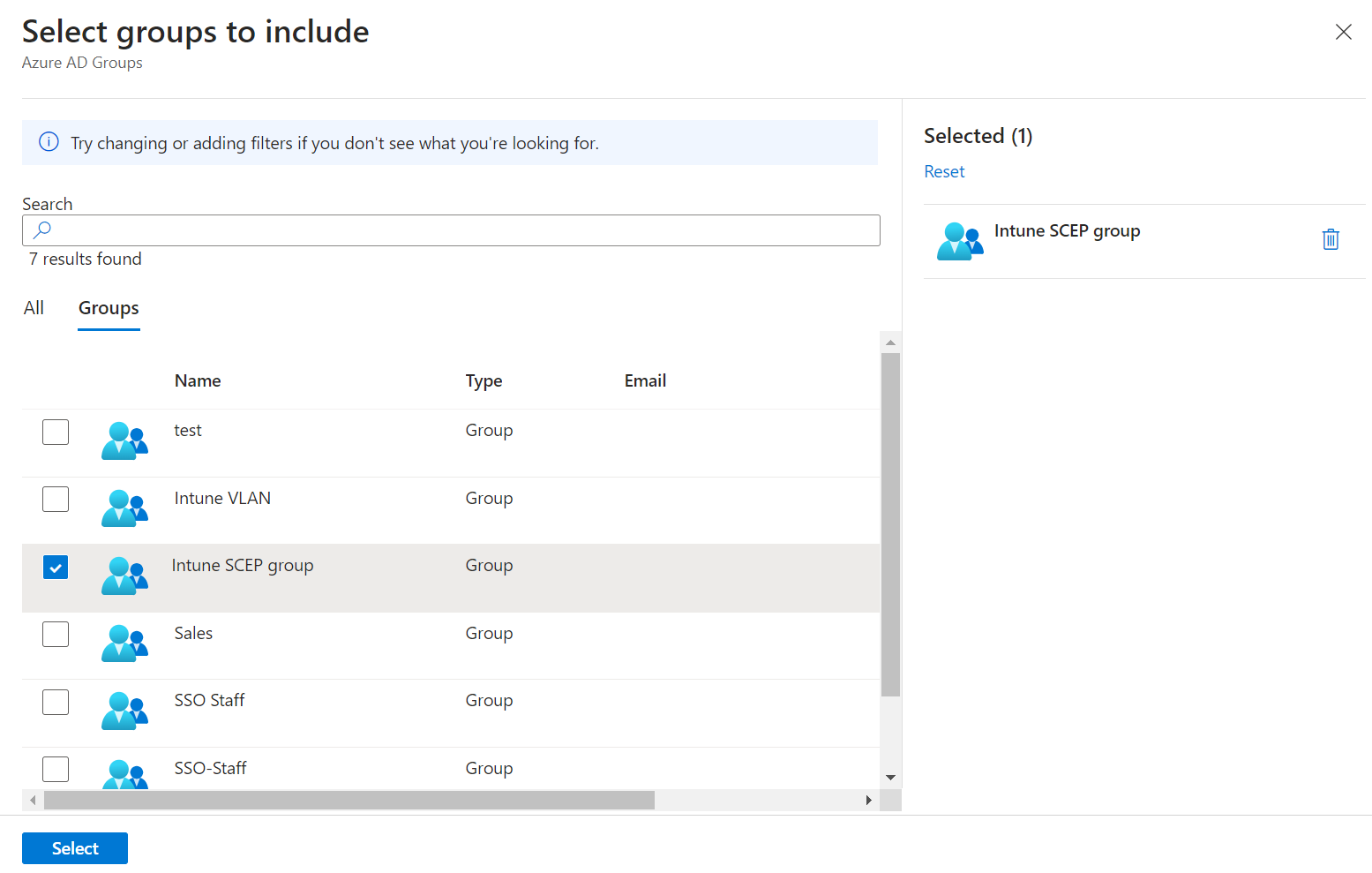
- Click Review + Save button.
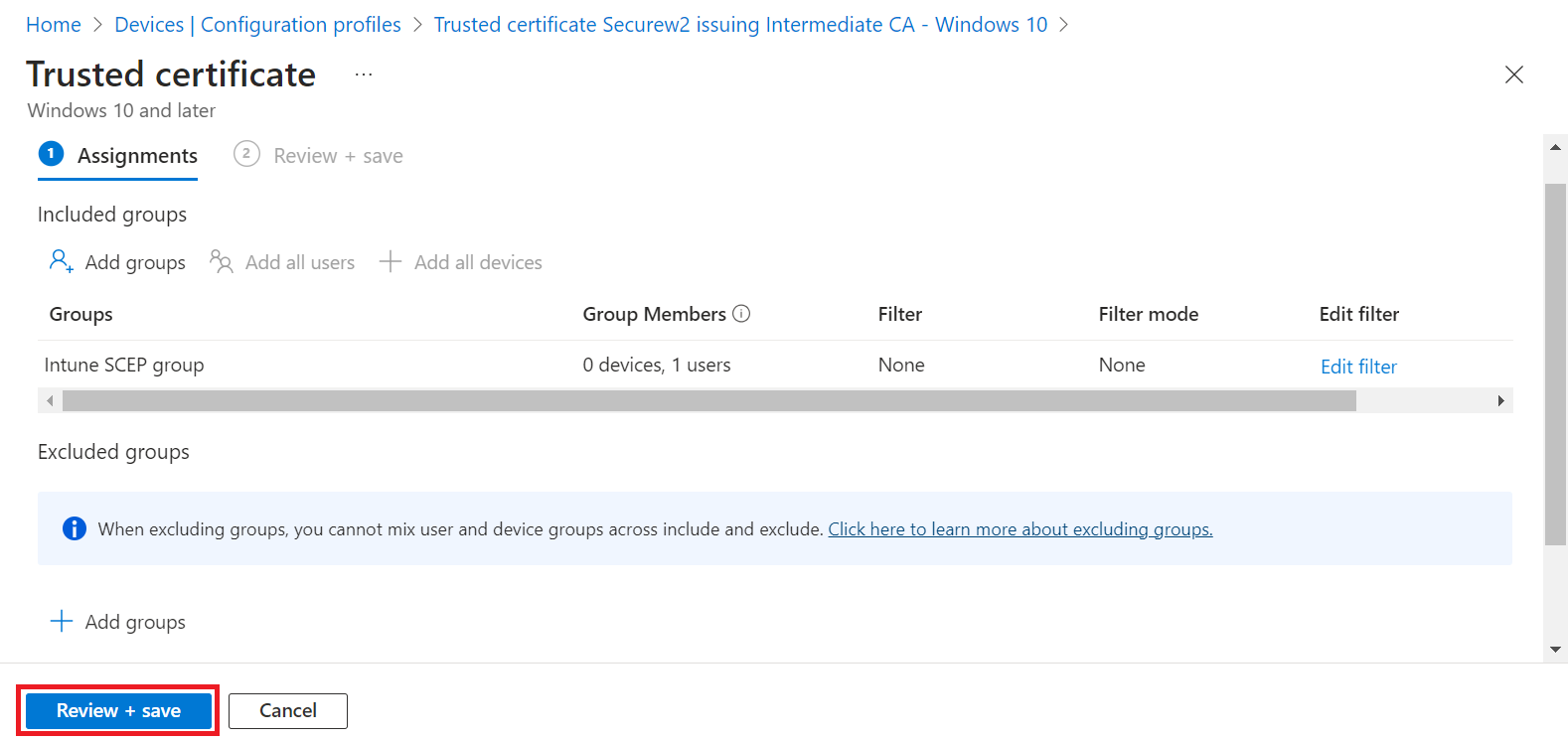
- Click Save.
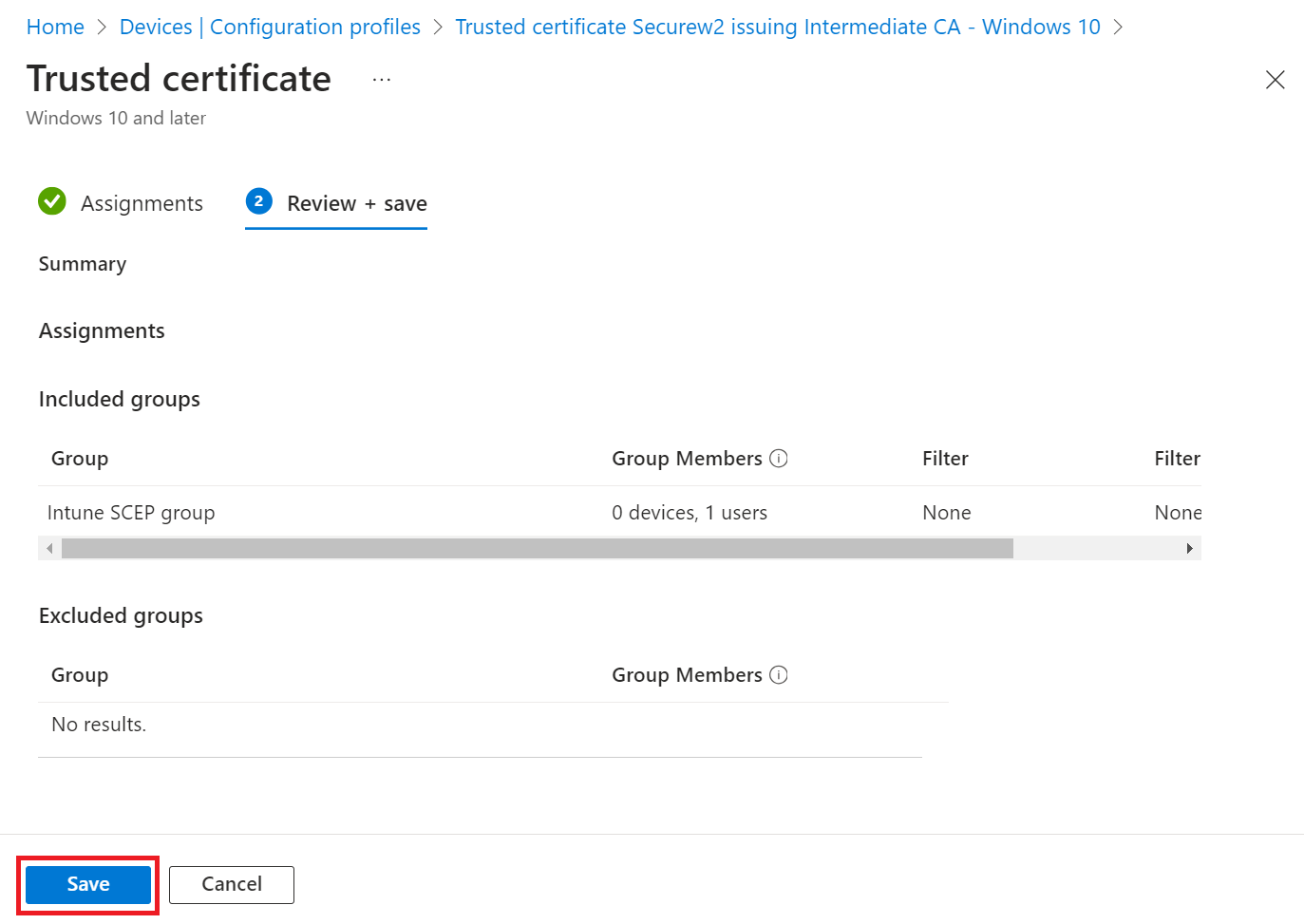
Add Wi-Fi Settings for Devices Running Android
You can create a profile with specific Wi-Fi settings and then deploy this profile to your Android devices.
| Setting Name | Configuration Step |
|---|---|
| Wi-Fi type | Select Enterprise. |
| Network name | Enter a name for your reference. |
| SSID | This setting is the real name of the wireless network that devices connect to. |
| EAP type | Select the Extensible Authentication Protocol (EAP) type to authenticate secured wireless connections. Select EAP-TLS.
|
NOTE: Retain the default values for the Connect automatically, Connect to this network and even when it is not broadcasting its SSID attributes.
After you have configured the Wi-Fi settings, select Next and then click Create. The profile is created and displayed in the profiles list.
Add Wi-Fi Settings for iOS Devices
You can create a profile with specific Wi-Fi settings and then deploy the profile to your iOS devices.
| Setting Name | Configuration Step |
|---|---|
| Wi-Fi type | Select Enterprise. |
| Network name | Enter a user-friendly reference name for this Wi-Fi connection. |
| SSID | This setting is the actual name of the wireless network that devices connect to. |
| EAP type | Select the Extensible Authentication Protocol (EAP) type to authenticate secured wireless connections. Select EAP-TLS. |
| Server Trust – Certificate server names | Add one or more common names used on your RADIUS server certificates issued by your trusted CA. For the SecureW2 RADIUS, it is: radius01.securew2.com |
| Root certificate for server validation | Select an existing trusted Root certificate profile, created in the Creating a Trusted Certificate Profile – RADIUS Server Root CA Certificate section. This certificate is presented to the server when the client connects to the network and is used to authenticate the connection. Select OK to save your changes. |
| Client Authentication – Client certificate for client authentication (Identity certificate) | Select the SCEP client certificate profile created previously in the Creating a SCEP Certificate Profile section. This certificate is the identity presented by the device to the server to authenticate the connection. Select OK to save your changes. |
NOTE: Retain the default values for the Connect automatically, Connect to this network, even when it is not broadcasting its SSID, and Proxy settings attributes.
After you have configured the Wi-Fi settings, select Next and then click Create. The profile is created and displayed in the profiles list.
Add Wi-Fi Settings for macOS Devices
You can create a profile with specific Wi-Fi settings, then deploy this profile to your macOS devices.
| Setting Name | Configuration Step |
|---|---|
| Wi-Fi type | Select Enterprise. |
| Network name | Enter a user-friendly reference name for this Wi-Fi connection. |
| SSID | This setting is the actual name of the wireless network that devices connect to. |
| EAP type | Select the Extensible Authentication Protocol (EAP) type to authenticate secured wireless connections. Select EAP-TLS. |
| Server Trust – Certificate server names | Add one or more common names used on your RADIUS server certificates issued by your trusted CA. For the SecureW2 RADIUS, it is: radius01.securew2.com |
| Root certificate for server validation | Select an existing trusted Root certificate profile, created in the Creating a Trusted Certificate Profile – RADIUS Server Root CA Certificate section. This certificate is presented to the server when the client connects to the network and is used to authenticate the connection. Select OK to save your changes. |
| Client Authentication – Client certificate for client authentication (Identity certificate) | Select the SCEP client certificate profile created previously in the Creating a SCEP Certificate Profile section. This certificate is the identity presented by the device to the server to authenticate the connection. Select OK to save your changes. |
NOTE: Retain the default values for the Connect automatically when in range, Connect to this network, even when it is not broadcasting its SSID, and Company Proxy settings attributes.
After you have configured the Wi-Fi settings, select Next and then click Create. The profile is created and displayed in the profiles list.
Add Wi-Fi Settings for Windows 10 and Later Devices
You can create a profile with specific Wi-Fi settings, then deploy this profile to your Windows 10 and later devices.
| Setting Name | Configuration Step |
|---|---|
| Wi-Fi type | Select Enterprise. |
| Wi-Fi name (SSID) | This value is the actual name of the wireless network that devices connect to. |
| Connection name | Enter a user-friendly reference name for this Wi-Fi connection. |
| EAP type | Select the Extensible Authentication Protocol (EAP) type to authenticate secured wireless connections. Select EAP-TLS.
|
After you have configured the Wi-Fi settings, select Next and then click Create. The profile is created and displayed in the profiles list.
NOTE: Retain the default values for the Connect automatically when in range, Metered Connection Limit, Single sign-on (SSO), Enable Pairwise Master Key (PMK) caching, Enable pre-authentication, and Company proxy settings attributes.
Troubleshooting
This section lists the common issues and the steps to resolve them. Common issues that you may encounter after the configuration is done:
- Certificate fails to enroll.
- Connection to the secure SSID fails.
- Error messages are displayed:
- The “Device Creation Failed” error message is displayed on the Events page (Log in to the JoinNow Management Portal, navigate to Data and Monitoring > General Events).
- The “SCEP enrollment failed” error message is displayed in the Intune portal.
- Users not assigned to the application in Microsoft Intune.
To resolve them:
- Check if the attributes have values and are mapped correctly. For more information, see the Creating an Intermediate CA for Intune SCEP Gateway Integration section.
- Make sure that the SCEP profile (in the Intune Portal) is configured to send values in the SAN attribute using Email address (RFC822). The common attributes configured are DeviceName and AAD_Device_ID. For more information, see the Creating an Intermediate CA for Intune SCEP Gateway Integration section.
- Confirm if the Policy Engine Workflow is mapped to the Intune API Token as an Identity Provider. Similarly, ensure the Enrollment Policy is mapped to the User Role and default Device Role. For more information, see the Configuring a Policy Engine Workflow section.
- Ensure that the SCEP profile is configured accurately. For more information, see the Creating an Intermediate CA for Intune SCEP Gateway Integration section.
- Check if the Trusted Root CA of the RADIUS server certificate is mapped in the Wi-Fi profile. For more information, see the Creating a Wi-Fi Profile section.
- Remove the SCEP profile and push any other profile, like the Trusted Root CA profile, to confirm if the user is successful with the configuration. For more information, see the Exporting the SecureW2 Root, Intermediate, and RADIUS CA section.
- An administrator manually adds the users to Microsoft Intune via Microsoft 365 admin center or the Microsoft Intune admin center and assigns the license to the user accounts. For more information, see: Add users and grant administrative permission to Intune