Configuring Google Chromebooks for Certificate Auto-Enrollment for EAP-TLS
An X.509 digital certificate offers better passwordless authentication than legacy credentials as they rely on public-private cryptography, making them phishing-resistant. Organizations like Microsoft and Google have strongly advocated using a digital certificate for better user and device-based network security.
However, certificate management in Google Chromebooks is tedious as Google doesn’t provide native solutions for auto-enrollment of a digital certificate to Chromebooks. Legacy Microsoft certificate enrollment protocol (SCEP) solutions don’t work well on Chromebooks either.
That is where the Simple Certificate Enrollment Protocol (SCEP) comes into place. The Simple Certificate Enrollment Protocol (SCEP) instructs a device to communicate using a Gateway API URL to a PKI. SecureW2’s Managed Device Gateway API solutions automate certificate distribution in Chromebooks.
Switching to Securew2s Managed Device Gateway API solution will help tie your existing infrastructure to use JSON, similar to the Simple Certificate Enrollment Protocol (SCEP), to manage Google devices for superior user and device management.
This document will guide you to configure your Managed device to auto-enroll for a digital certificate for EAP-TLS authentication through the SecureW2s Management Portal.
Prerequisites To Configure Google Managed Devices for Certificate Auto-Enrollment
The first step to configure managed device certificate auto-enrollment is to configure a managed device gateway in SecureW2. To do that, you need to do the following:
- Configure a Google Verified Access Identity Provider and an EAP-TLS Network Profile in SecureW2. This is what managed devices will use to auto-enroll for a certificate, and use it for network connectivity.
- Grant Google Chrome verified access permission to SecureW2s managed support service account to install the required settings.
The second part is to configure Google Workspace to use the Managed Device Gateway API for Chromebook certificate auto-enrollment:
- The SecureW2 support team will create a custom JSON policy, which works similarly to the simple certificate enrollment protocol (SCEP), that the devices will use to communicate to the certificate auto-enrollment gateway.
- Configure the extension ID, which is used to install and push the JoinNow Chrome extension for auto-enrollment of a device, that is provided by the SecureW2 support team.
- Configure and install the appropriate settings so your devices will use the newly enrolled certificate for certificate-based Wi-Fi authentication.
Configure a Google Verified Access IdP
First, we need to create an Identity Provider (IdP) in SecureW2. This is necessary for Google and SecureW2 to securely communicate with each other to validate that users and devices deserve certificates.
Then, we need to create a Network Profile, which is used to determine which EAP method is to be used for authentication. An EAP protocol should be used to obtain a primary mechanism to gain identity without the use of an identity response.
SecureW2 recommends the use of EAP-TLS as it provides a mechanism to determine both user and server identity through digital certificate for your device.
- Log in to the JoinNow Management Portal.
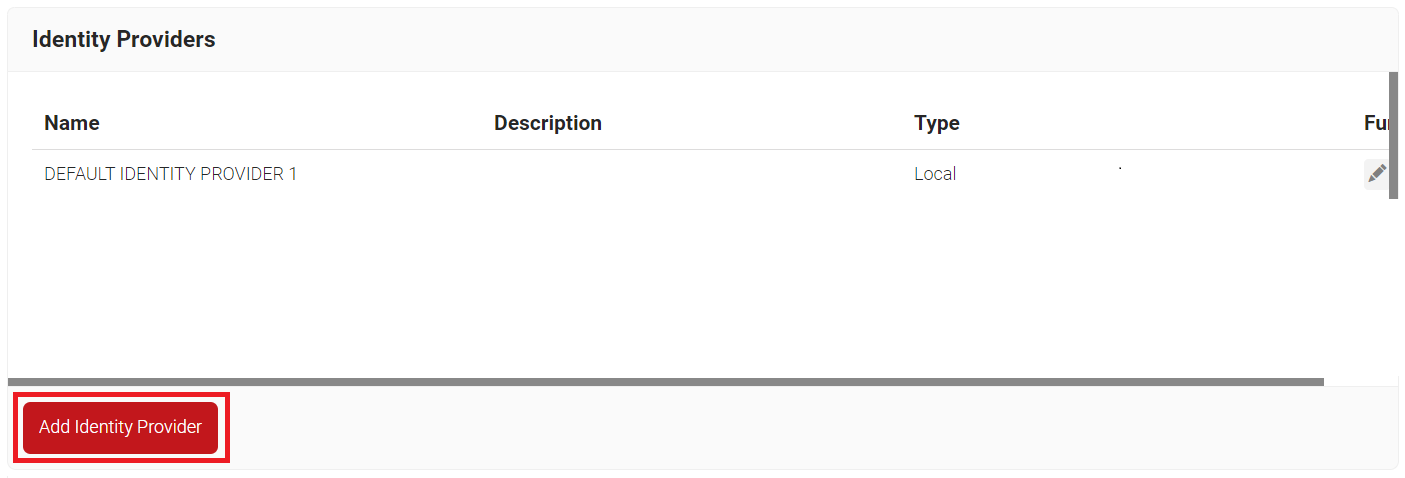
- Navigate to Identity Management > Identity Providers.
- Click the Add Identity Provider button.
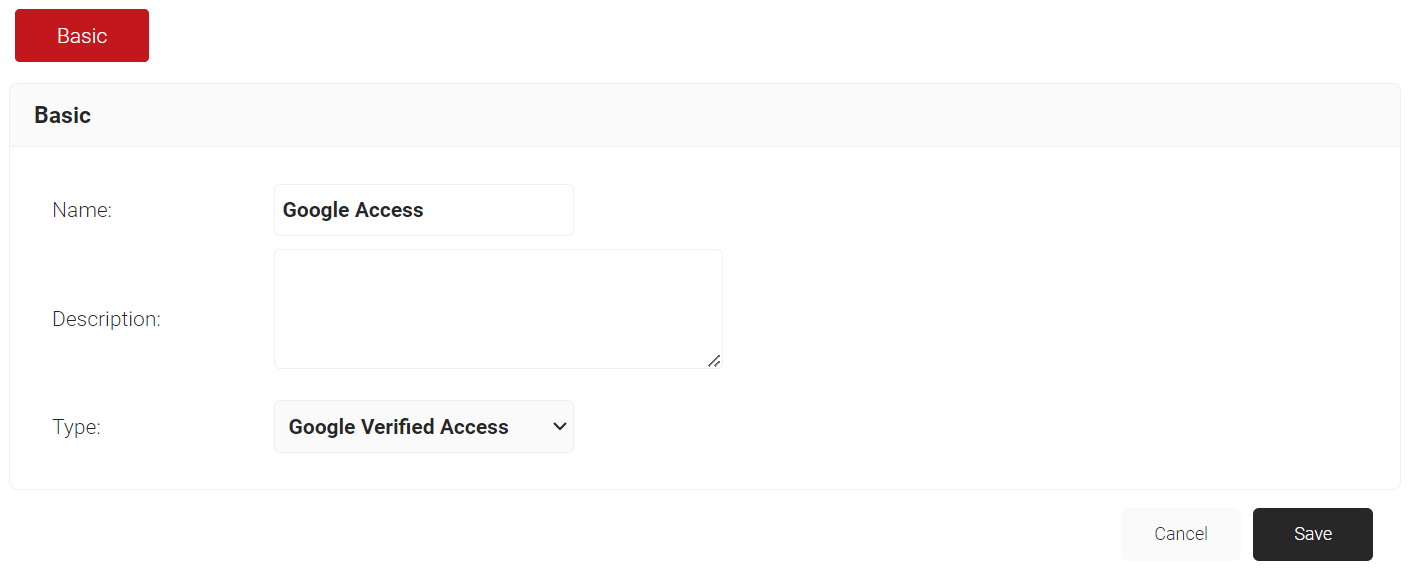
- Under the Basic section, in the Name field, enter the name of the IdP.
- In the Description field, enter a suitable description for the IdP.
- From the Type drop-down-list, select Google Verified Access.
- Click Save.
Configuring a Network Profile for Managed Chromebooks
A Network Profile contains the settings our device will need to use for 802.1x. This will instruct the device to use the certificate that it has recently enrolled for network authentication and also include other important EAP-TLS 802.1x settings.
To create a Network profile, perform the following steps.
- Navigate to Device Onboarding > Getting Started.
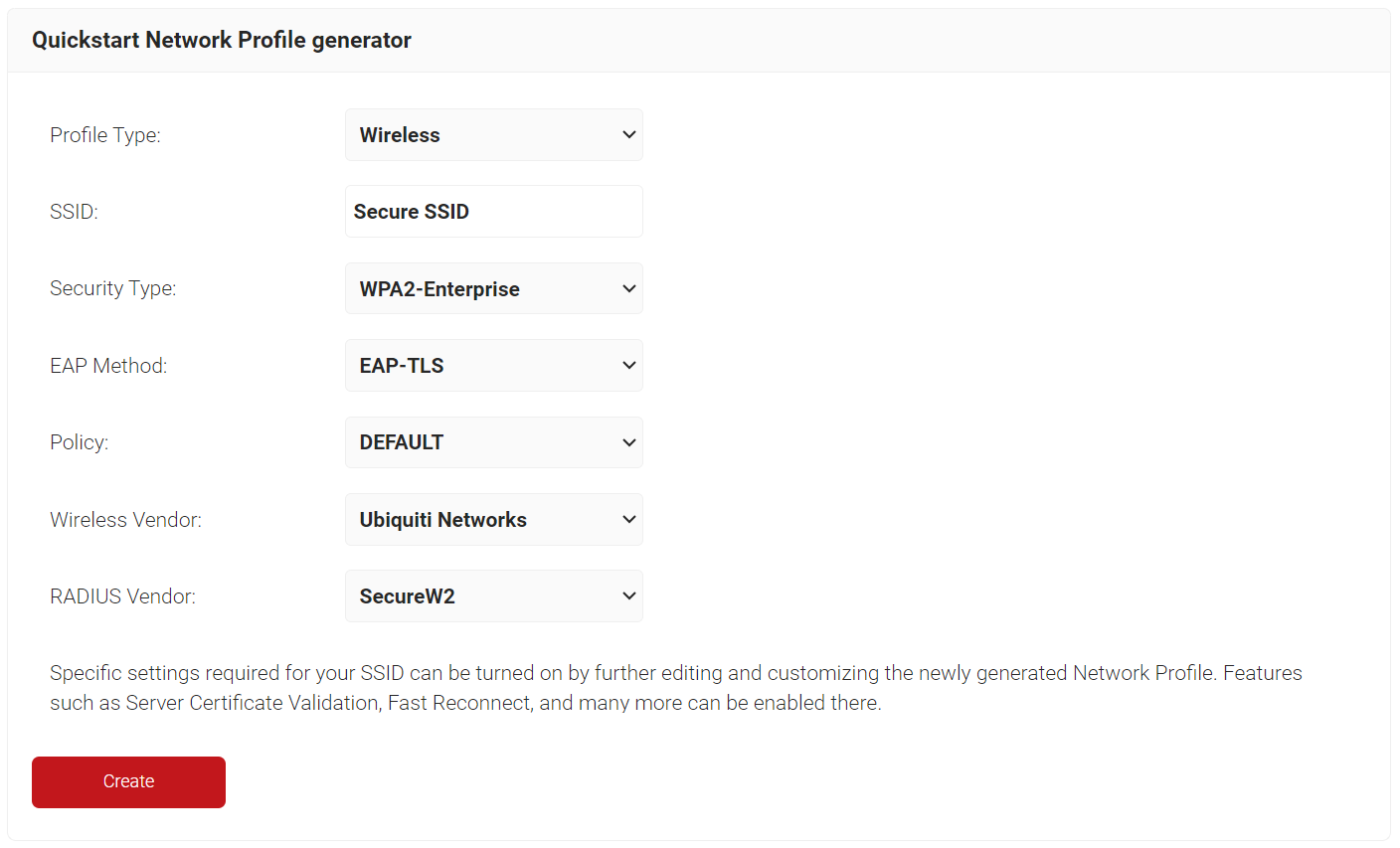
- On the Quickstart Network Profile generator page, from the Profile Type drop-down list, select Wireless.
- In the SSID field, enter a suitable name for the SSID.
- From the Security Type drop-down list, select WPA2-Enterprise.
- From the EAP Method drop-down list, select EAP-TLS.
- From the Policy drop-down list, select Default.
- From the Wireless Vendor drop-down list, select a wireless infrastructure vendor.
- From the RADIUS Vendor drop-down list, select a RADIUS vendor.
- Click Create.
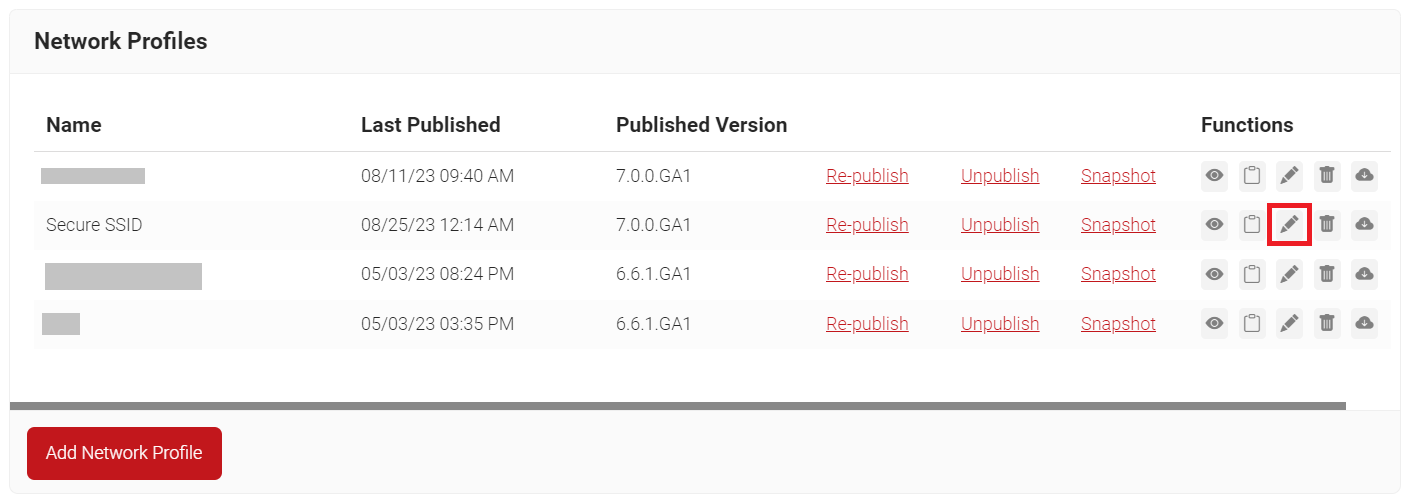
NOTE: The Getting Started wizard will typically take 60-90 seconds to create the profile. - On the Network Profiles page, click the Edit link for the newly created network profile.
- Scroll down to the Networks Settings section and click the Edit link for the newly created network profile.
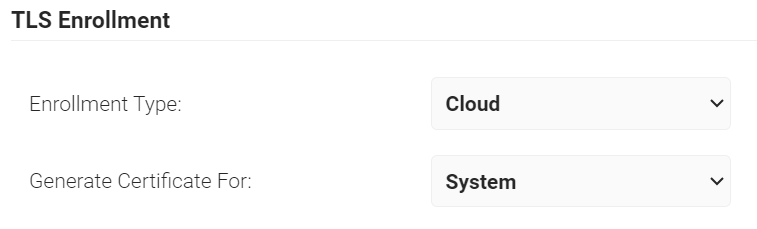
- In the TLS Enrollment section, from the Enrollment Type drop-down list, select Cloud.
- From the Generate Certificate For drop-down list, select:
- System – If you are enrolling systems for certificates.
- User – If you are enrolling individual users for certificates.
- Click Update.
- On the Network Profile page, select the Advanced tab.
- Scroll down to the Workflows section and uncheck the following options.
- Wireless Configuration
- Wireless Connect
- Click Update.
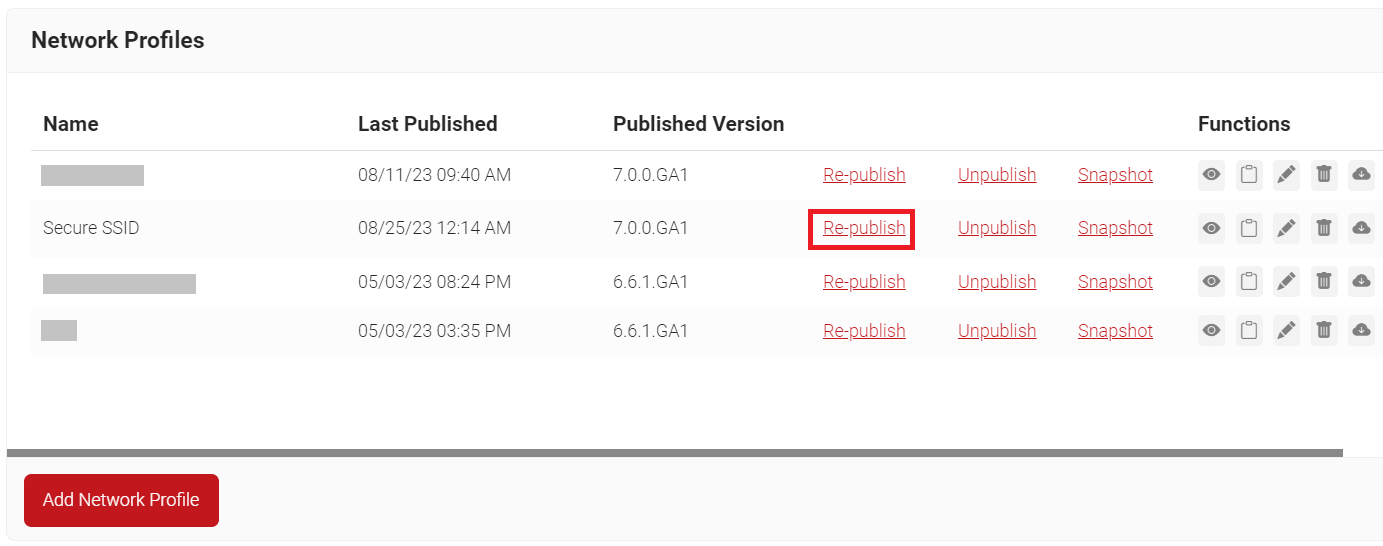
- On the Network Profile page, click the Re-publish link against your network profile.
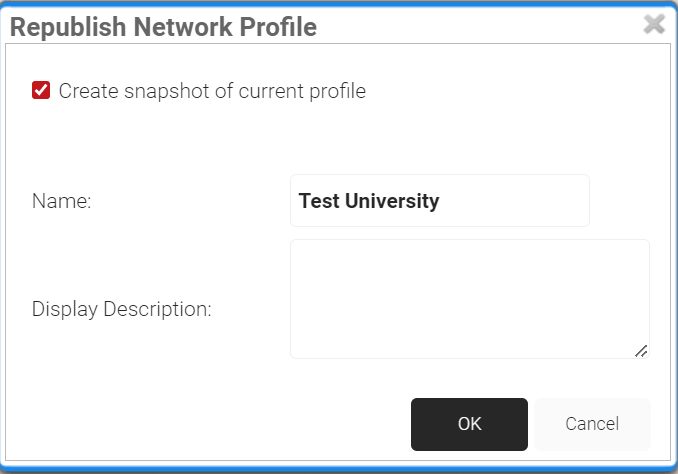
- In the Republish Network Profile pop-up window, type the name of the network profile and click OK.
Configuring Authentication Policy for a Google Device
An Authentication Policy connects an IdP with a Network Profile. This is necessary so only our Google-managed Chromebooks can connect to our network. We will need to configure an Authentication Policy to tie the Network Profile we just created, with the Google Verified Access IdP that we made at the beginning of the document.
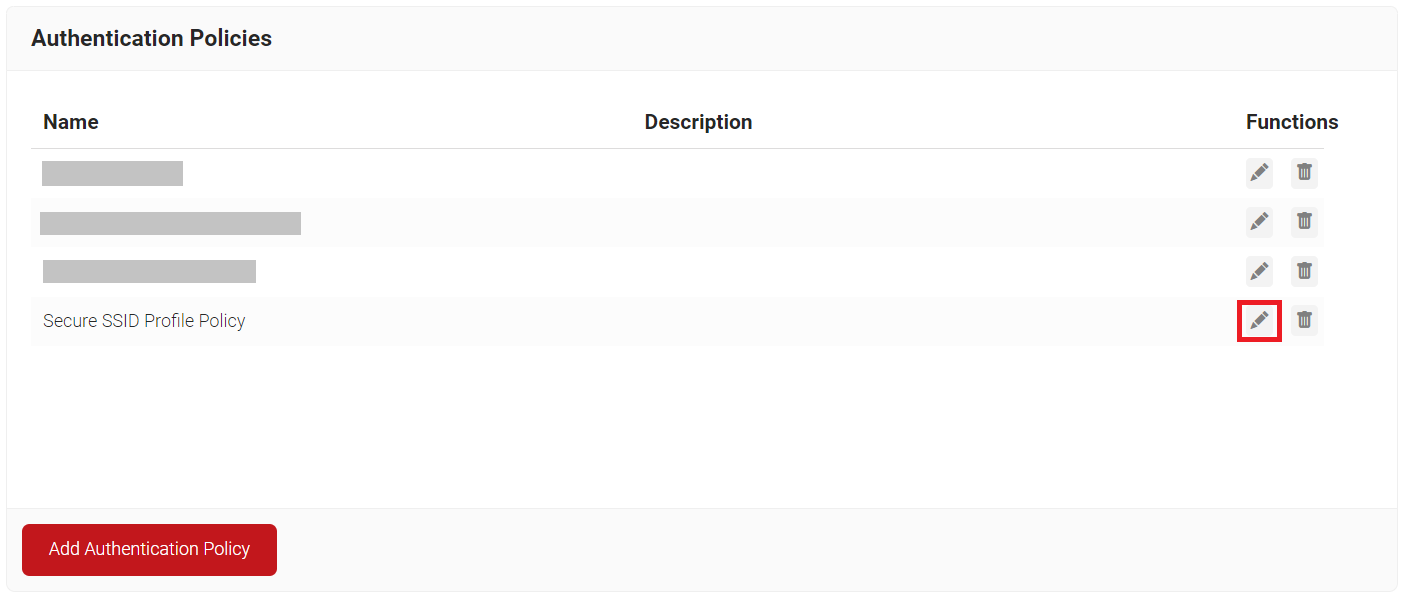
- Navigate to Policy Management > Authentication Policies.
- Click the Edit link for your network profile’s authentication policy.
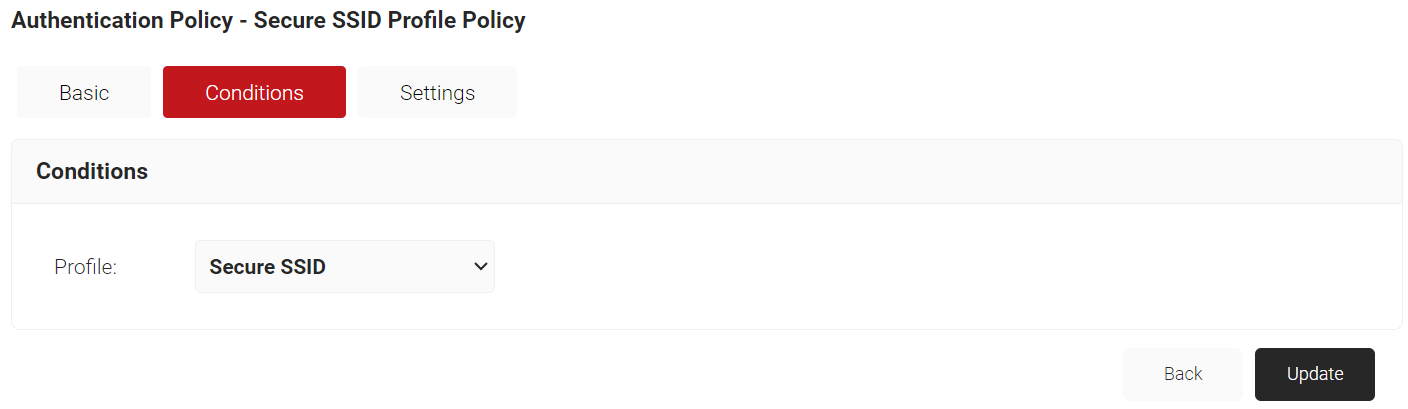
- Select the Conditions tab and make sure that your network profile is displayed in the Profile field.
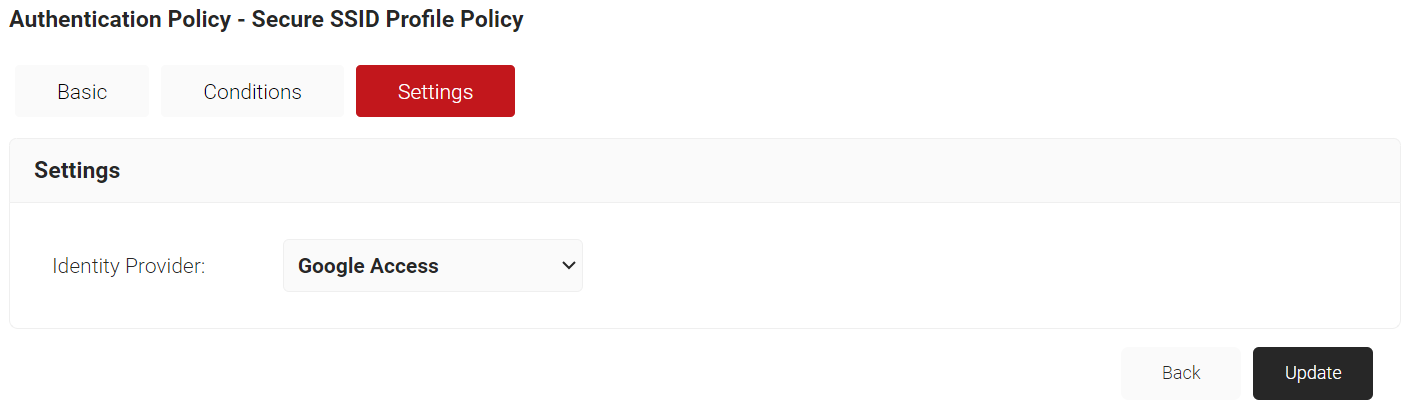
- Select the Settings tab.
- Under the Settings section, from the Identity Provider drop-down list, select the IDP you created earlier (refer to the Create a Google Verified Access IdP section).
- Click Update.
Configuring Role Policies for Managed Chromebook EAP-TLS
We can create specific roles, for users or groups in our Google Workspace, to and then we can assign specific Enrollment or Network Policies to those users and groups. This is necessary to use different Certificate Templates, or Certificate Authorities for our various groups, and to segment users into different Network VLANs.
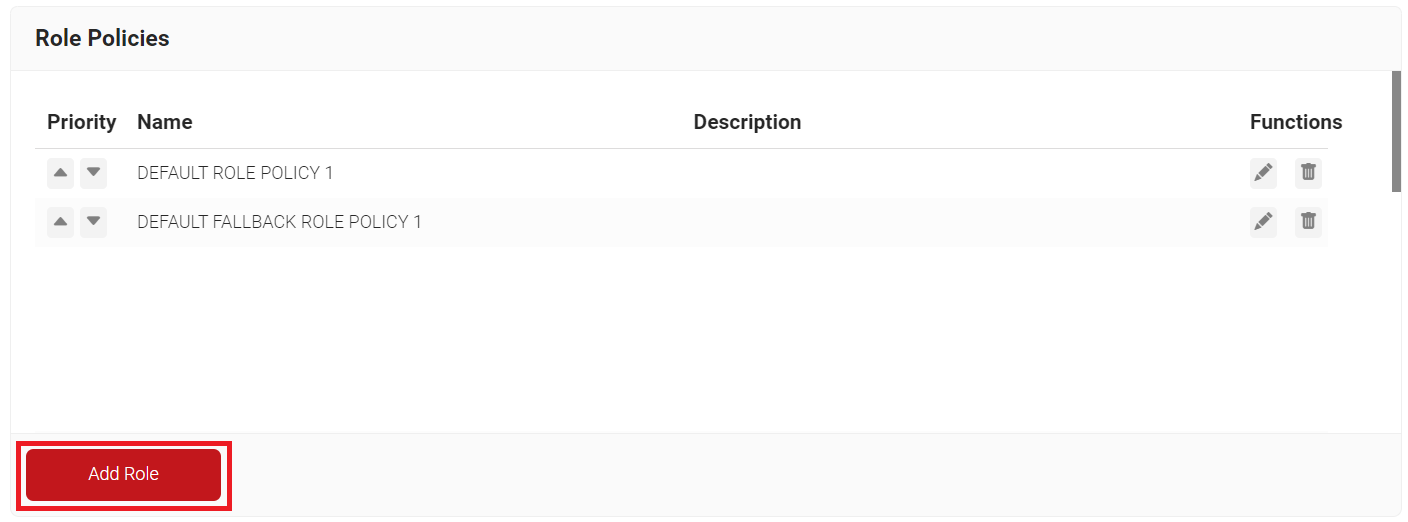
- Navigate to Policy Management > Roles Policies.
- Click Add Role.
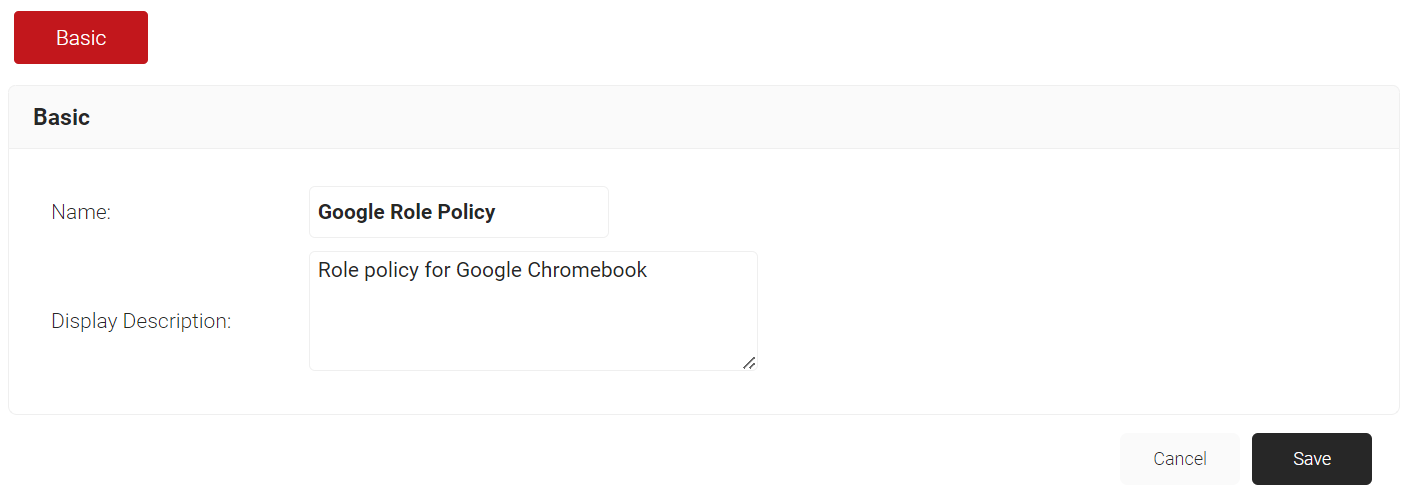
- Under the Basic section, in the Name field, enter the name of the role policy.
- In the Display Description field, enter a suitable description for the role policy.
- Click Save.
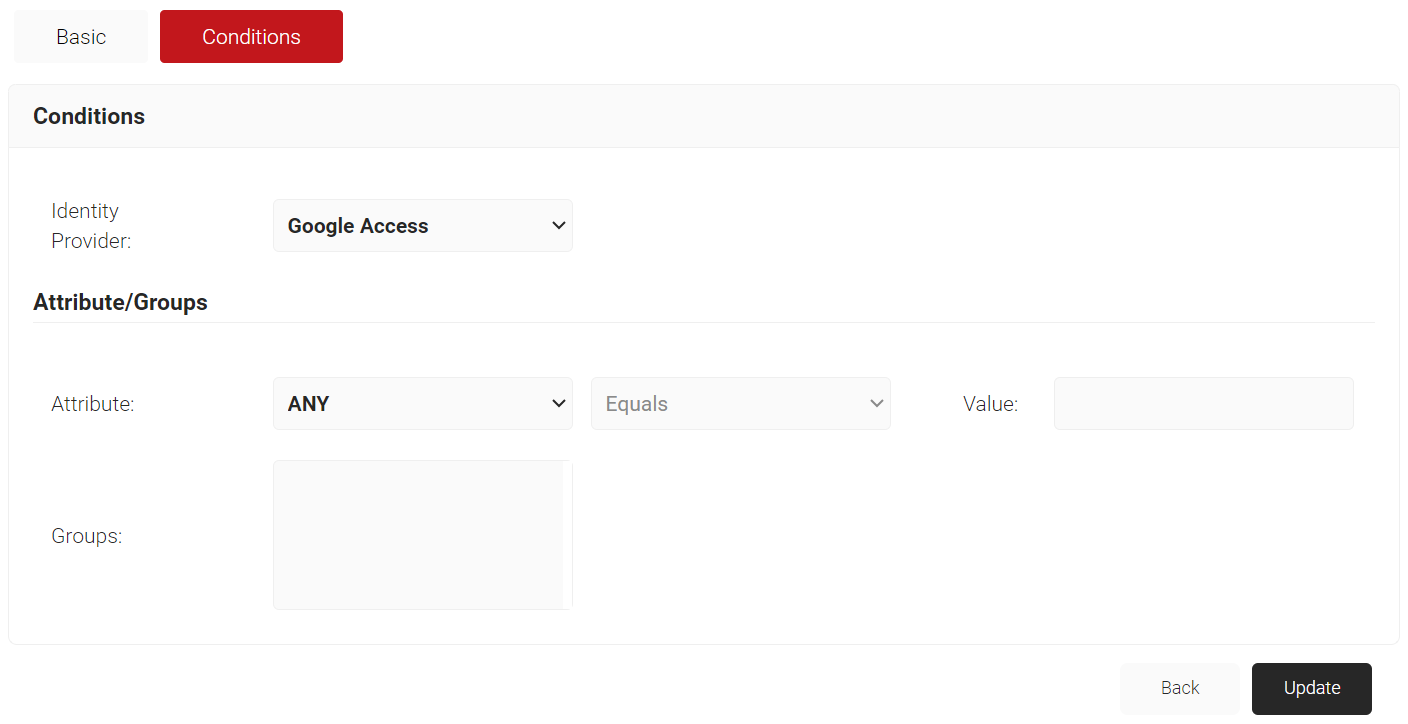
- Select the Conditions tab.
- Under the Conditions section, from the Identity Provider drop-down list, select the IdP you created earlier (refer to the Create a Google Verified Access IdP section).
- Click Update.
Configuring the Google Admin Console For Managed Device
Now we will configure our Google Workspace to push the Network Profile, and the JSON Policy, to our Chromebooks. We need Google Workspace to send these profiles to our Chromebooks, or else they won’t be able to enroll for a certificate, or use the certificate for network access.
Grant Permission for the SecureW2 Service Account for Google Chrome Verified Access
The SecureW2 service account is used to validate the verified access token (sent by the device during enrollment) against Google to confirm if the identity matches the token; based on the results, it proceeds to the next step in enrollment.
- To provide access to the service account for device certificate enrollment:
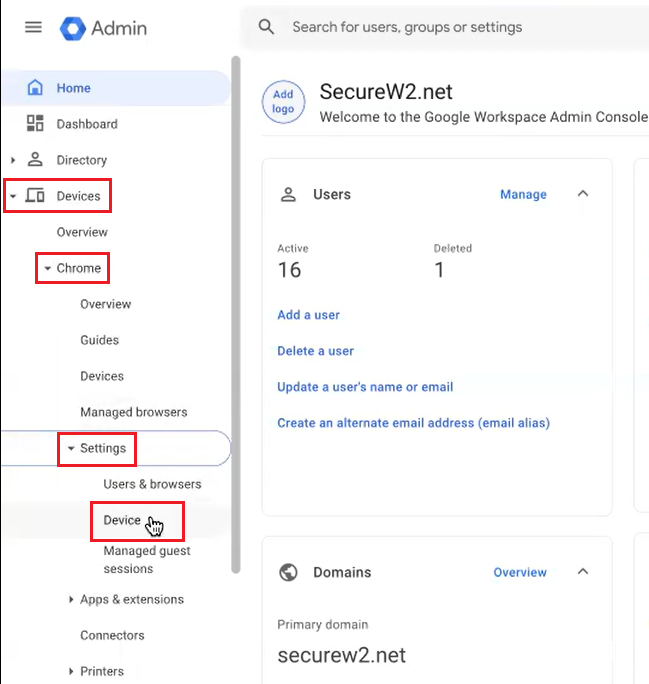
- Log in to the Google Admin Console.
- Navigate to Devices > Chrome > Settings > Device.
- Select the Device Settings tab.
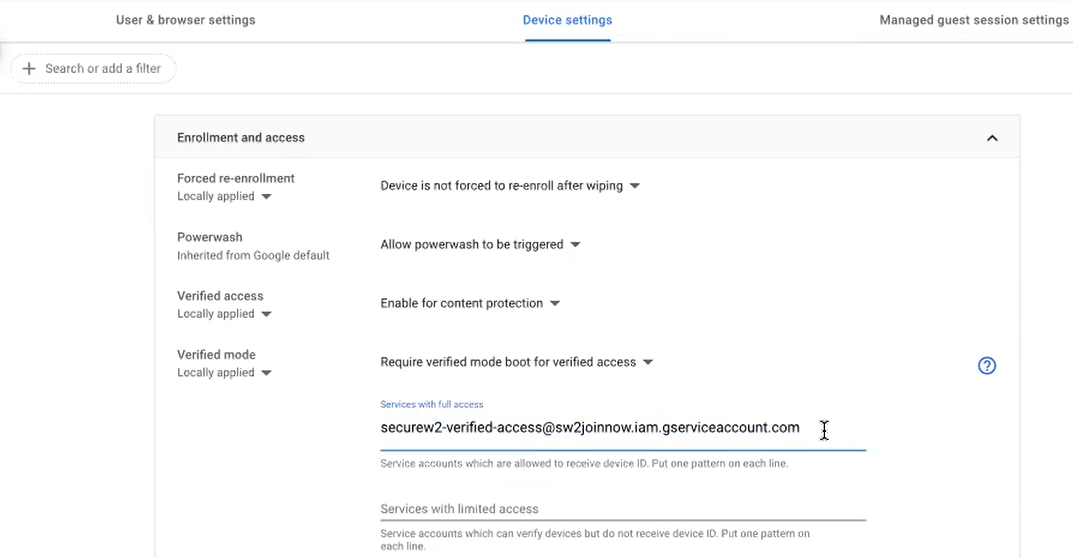
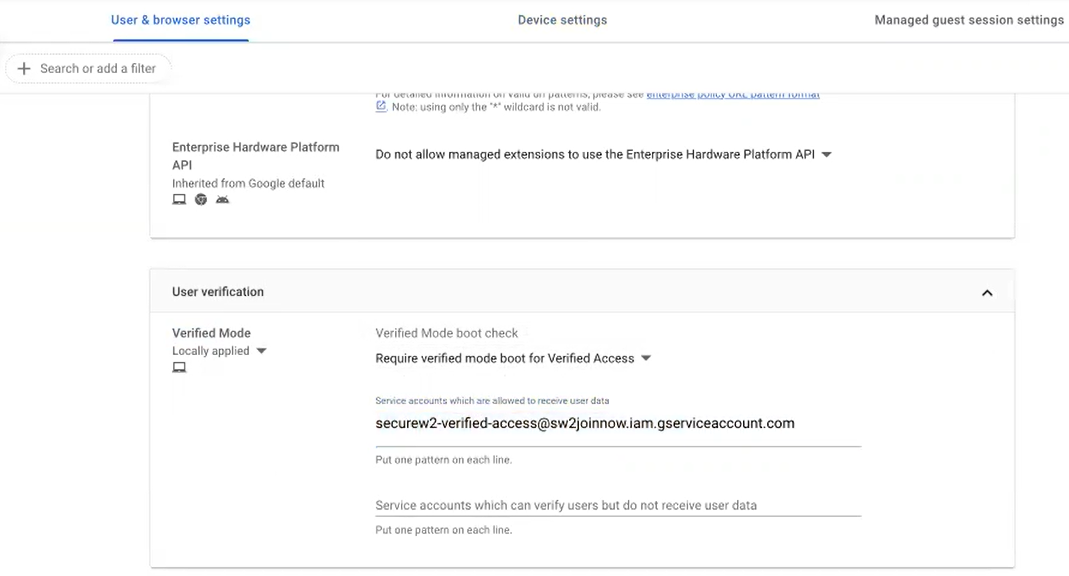
- Under the Enrollment and access section:
- From the Verified access drop-down list, select Enable for content protection.
- From the Verified mode drop-down list, select Require verified mode boot for verified access.
- In the Services with full access field, enter the following email:securew2-verified-access@sw2joinnow.iam.gserviceaccount.com
- Click SAVE.
- To provide access to the service account for user certificate enrollment:
- Navigate to Devices > Chrome > Settings > Device.
- Select the User & browser settings tab.
- Under the User verification section:
- From the Verified Mode boot check drop-down list, select Require verified mode boot for Verified Access.
- In the Service accounts which are allowed to receive user data field, enter the following email: securew2-verified-access@sw2joinnow.iam.gserviceaccount.com
- Click SAVE.
- Navigate to Devices > Chrome > Settings > Device.
Upload the JSON (Similar To Simple Certificate Enrollment protocol) Policy File
In the next section below, you will need to upload a JSON configuration (a certificate enrollment protocol similar to the Simple Certificate Enrollment Protocol) file to the Google Admin Console. Please contact SecureW2 support during this stage, and they will provide you with the required JSON file.
Sample File:
{
"EnrollmentURL": {
"Value": "https://pki-services.securew2.com/enroll/<WORKFLOW_ID>"
},
"DeviceCertificate": {
"Value": true
},
"RenewWindowDays": {
"Value": 30
},
"MetaConfigInfo": {
"Value": {
"organizationId": "<ORG_ID>",
"profileId": “<PROFILE_UUID> “
}
}
} Configure the JoinNow MultiOS Extension from the Google Admin Console
The JoinNow extension must be installed on your device so they can enroll for a digital certificate. Here, we will configure the Google Admin Console to install the extension.
To navigate to the JoinNow MultiOS extension:
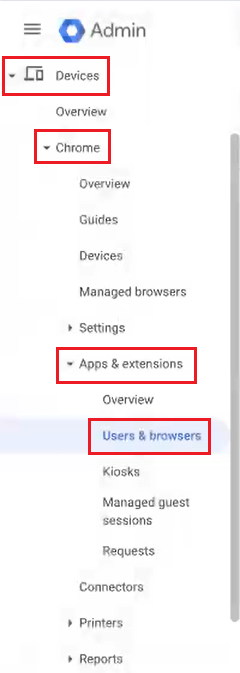
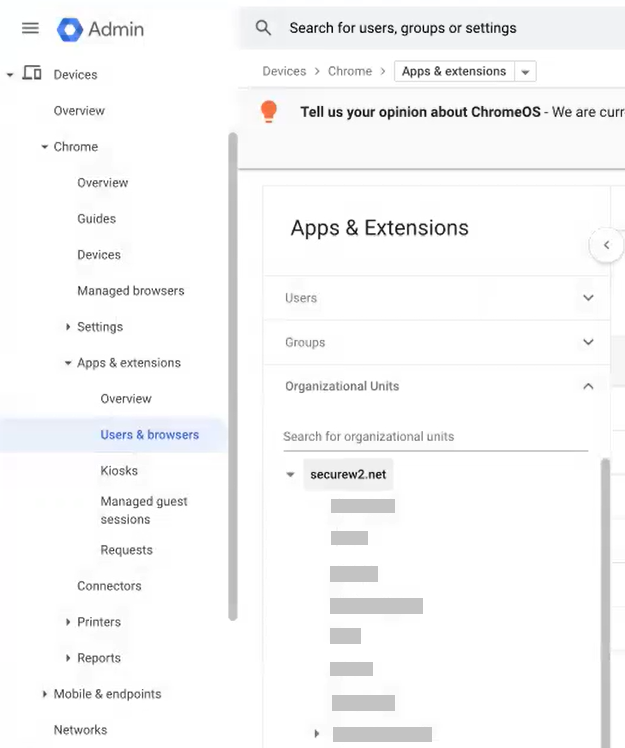
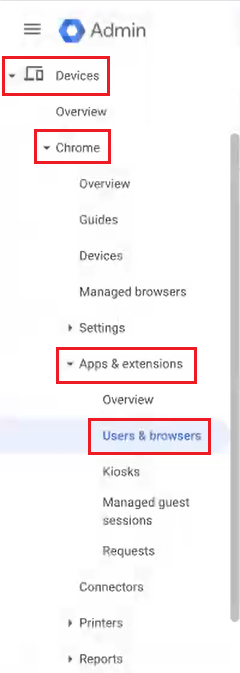
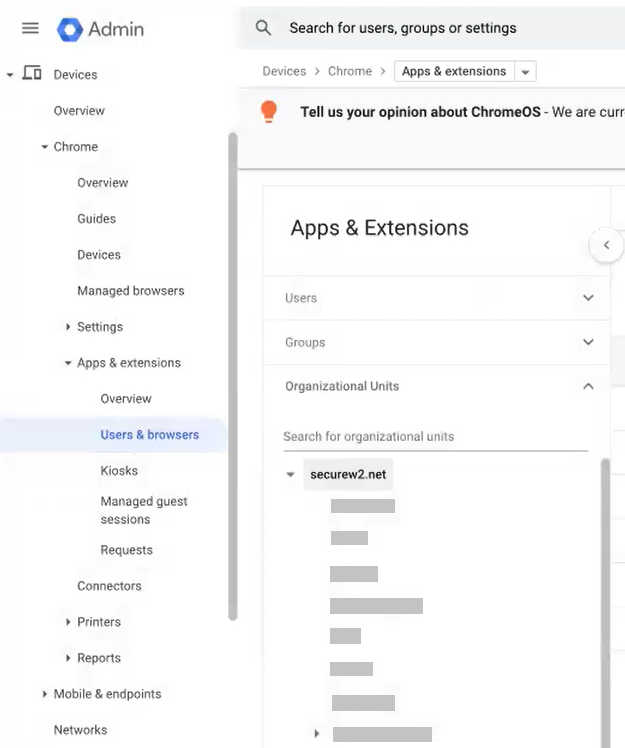
- In the Google Admin Console, navigate to Devices > Chrome > Apps & extensions > Users & browsers.
- On the left pane, from the Organizational Units drop-down-list, select an organization unit.
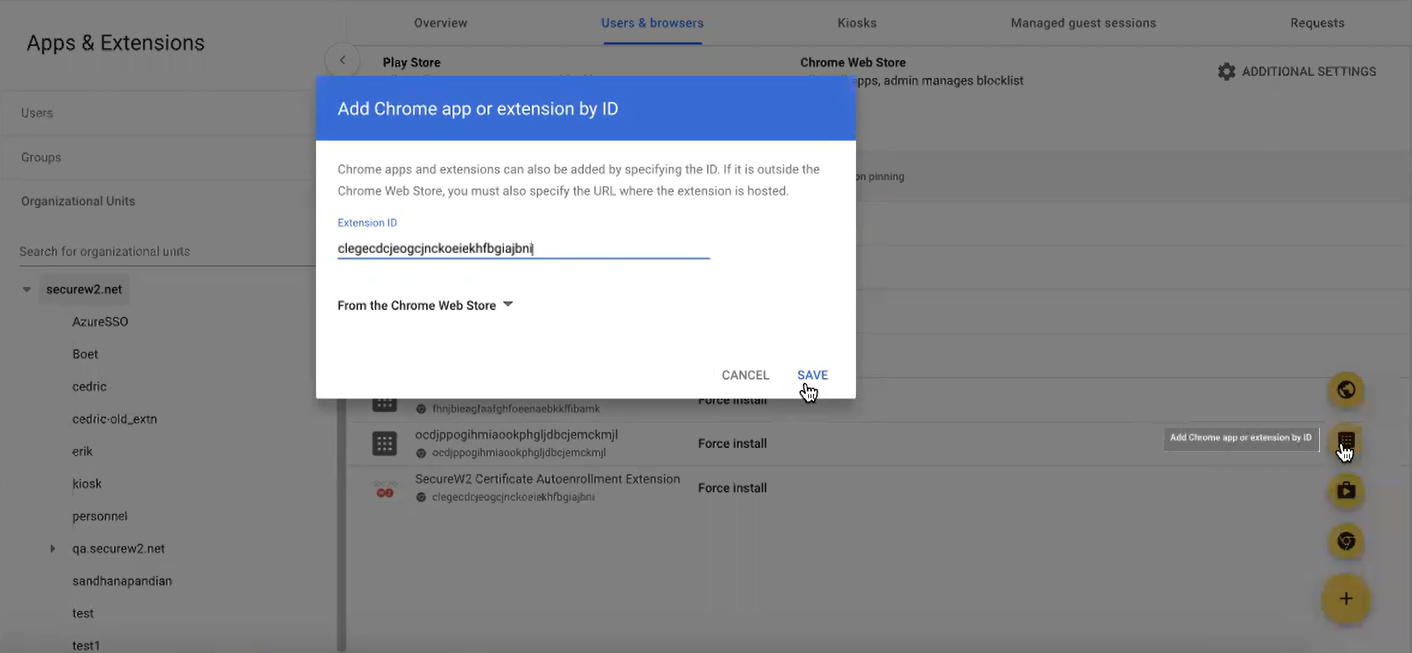
- Under the Users & browsers tab, click the + icon to expand the list of options and select the Add Chrome app or extension by ID option.
- In the Add Chrome app or extension by ID dialog box, enter the extension ID as clegecdcjeogcjnckoeiekhfbgiajbni in the Extension ID field.
- Click SAVE.
NOTE: You can search for the SecureW2 Certificate Auto-Enrollment Extension by using the extension ID: clegecdcjeogcjnckoeiekhfbgiajbni and not from the Chrome Web Store. This was designed for security reasons.
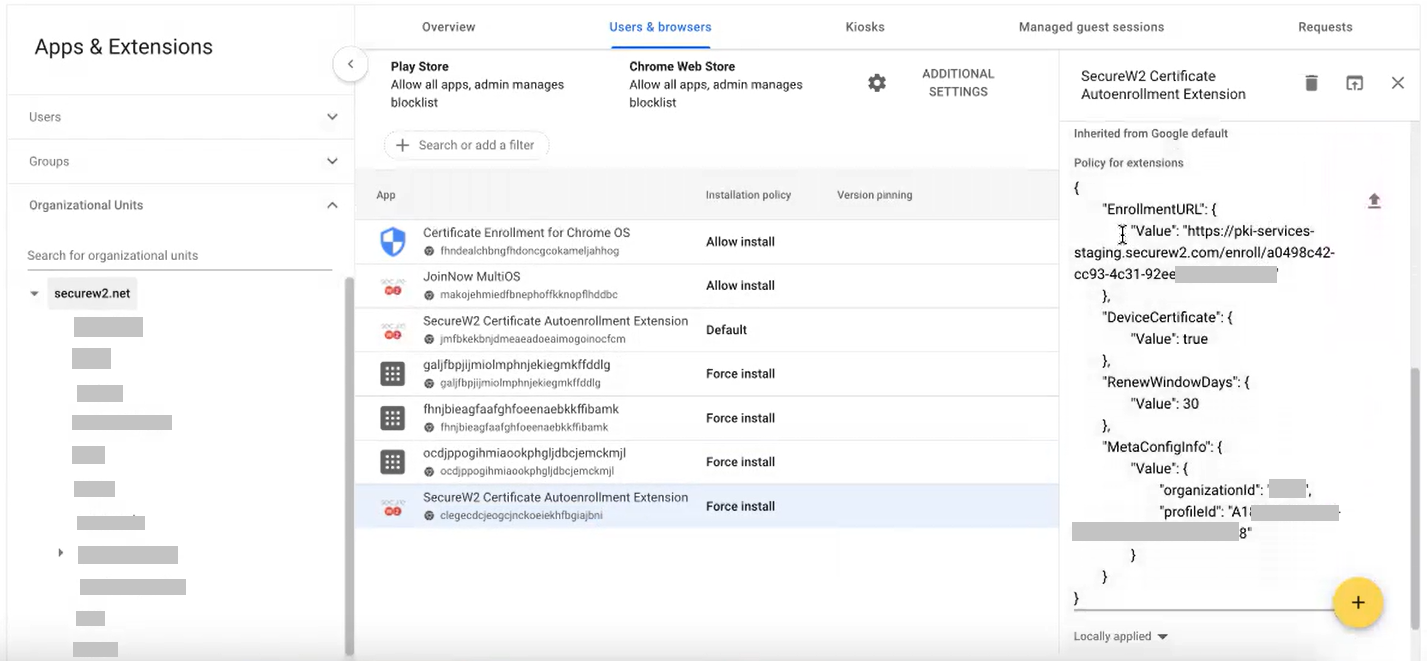
Force SecureW2 Certificate Auto-Enrollment Extension
With the JoinNow MultiOS extension configured on your device, it can auto-enroll itself for a certificate through JSON similar to the Simple Certificate Enrollment Protocol (SCEP).
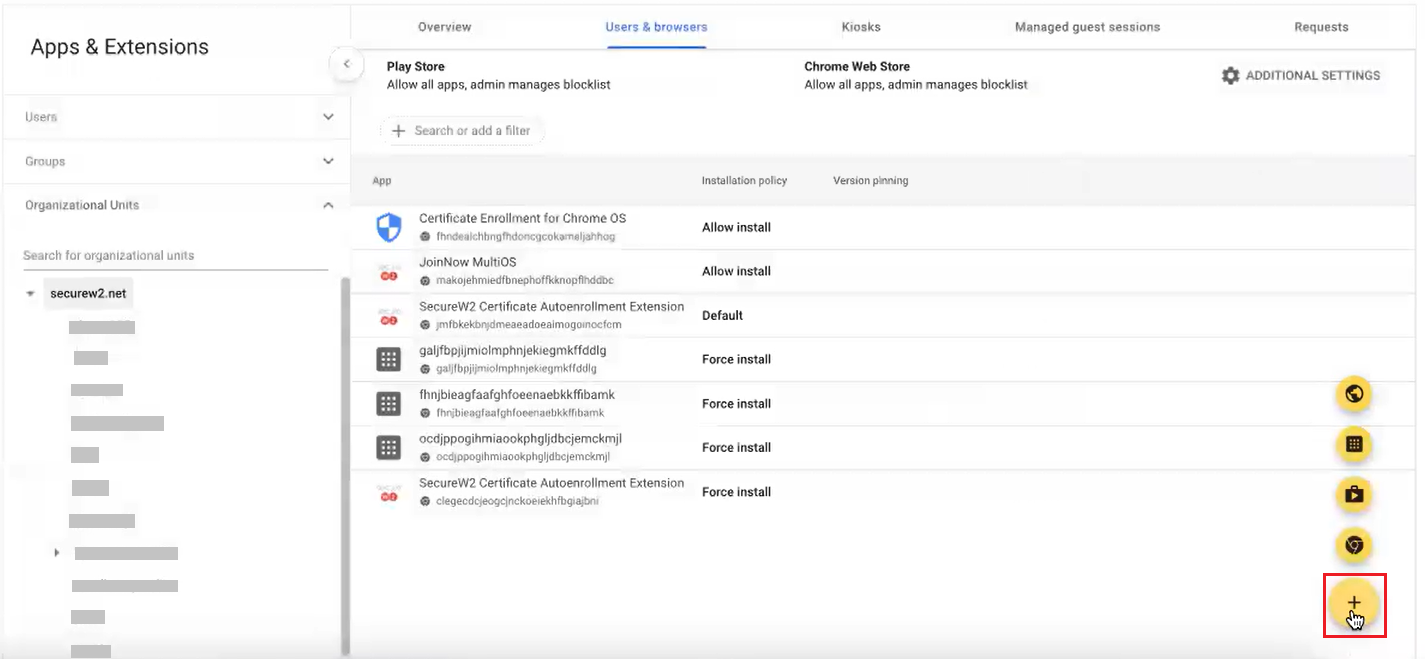
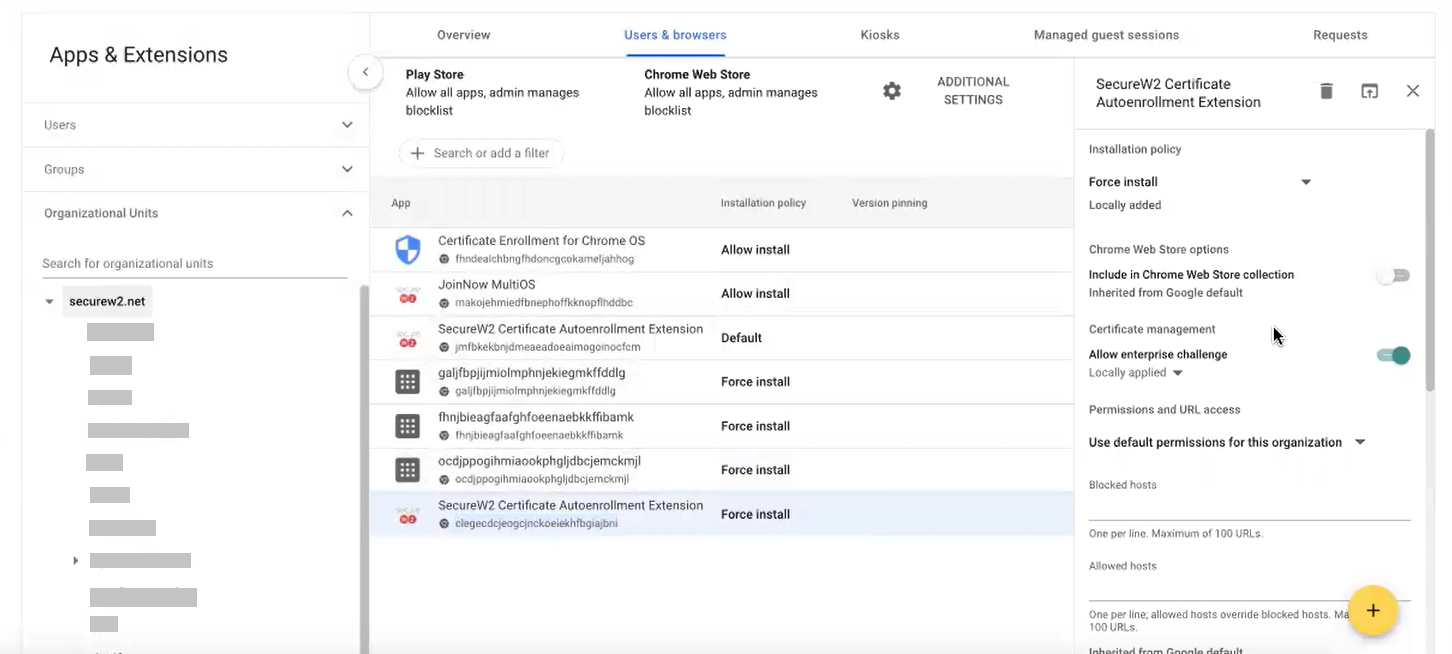
- Navigate to Devices > Chrome > Apps & extensions > Users & browsers.
- On the left pane, from the Organizational Units drop-down-list, select the organization unit where you added the chrome app using the extension ID.
- In the Users & browsers tab, select the SecureW2 Certificate Autoenrollment Extension app and click the Force install link.
- In the SecureW2 Certificate Autoenrollment Extension pop-up window, enable the Allow enterprise challenge option in the Certificate management field.
- In the Policy for extensions section, upload the JSON file shared by the support team.
- Click Save.
Trusted Certificate Profile for RADIUS Server CA
You should configure the Trusted Certificate Profile with the certificate of your RADIUS server certificate’s issuing authority. This is to make the device trust your RADIUS server by validating the RADIUS server certificate. You can achieve this server validation in the profile configuration by adding the Root and/or Intermediate Certificate Authority (CA) certificates that issued the RADIUS server certificate. When you assign this profile, the configured device will receive a trusted certificate.
NOTE: For other RADIUS vendors, other than the SecureW2 RADIUS server, ensure that you have the Root or Intermediate CA that issues a RADIUS server certificate.
Export Trusted Root and Intermediate CA Certificate
SecureW2’s Cloud PKI allows you to create custom root and intermediate certificate authorities for deploying certificate signing requests to ensure that applications are used only by the intended users.
This section lists the steps to export the RADIUS Server Root CA from the JoinNow MultiOS Management Portal.
To export the SecureW2 RADIUS Server Certificate:
- Log in to the JoinNow Management Portal.
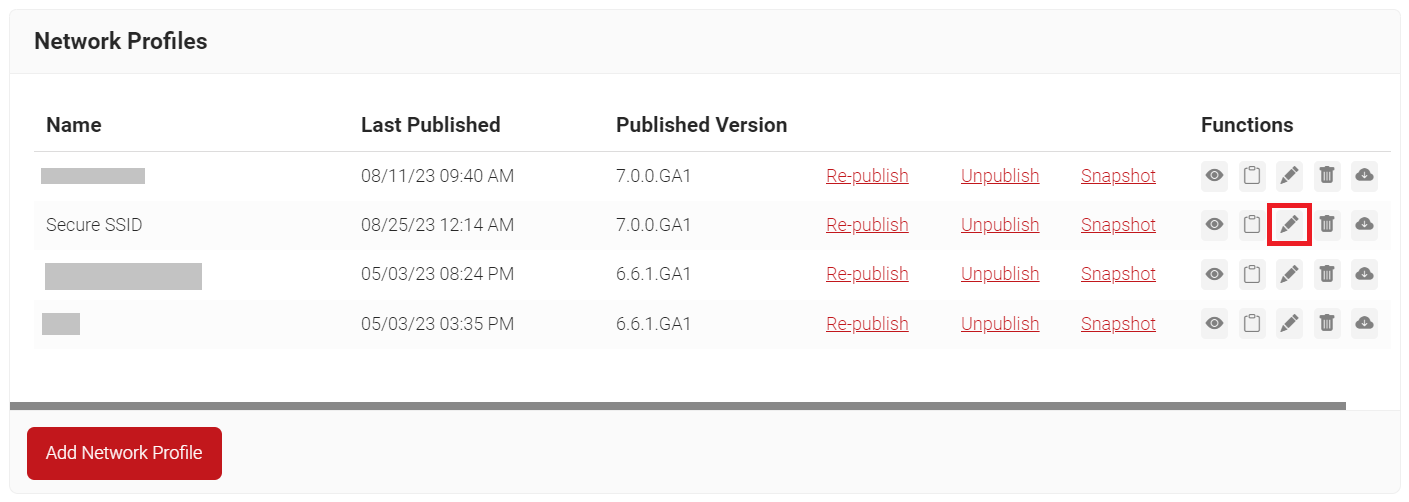
- Navigate to Device Onboarding > Network Profiles.
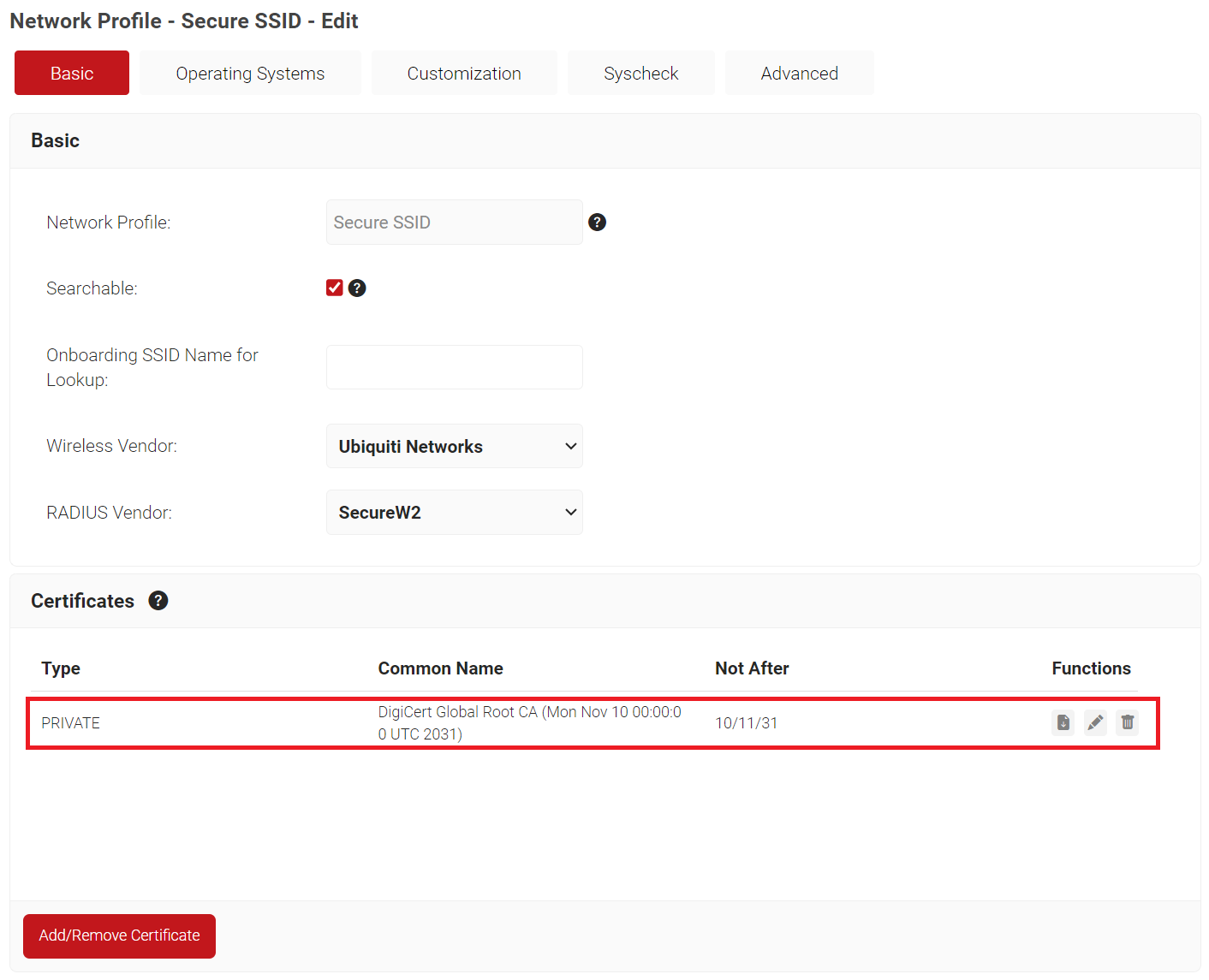
- On the Network Profiles page, click the Edit link of the network profile you created earlier (refer to the Create a Network Profile section).
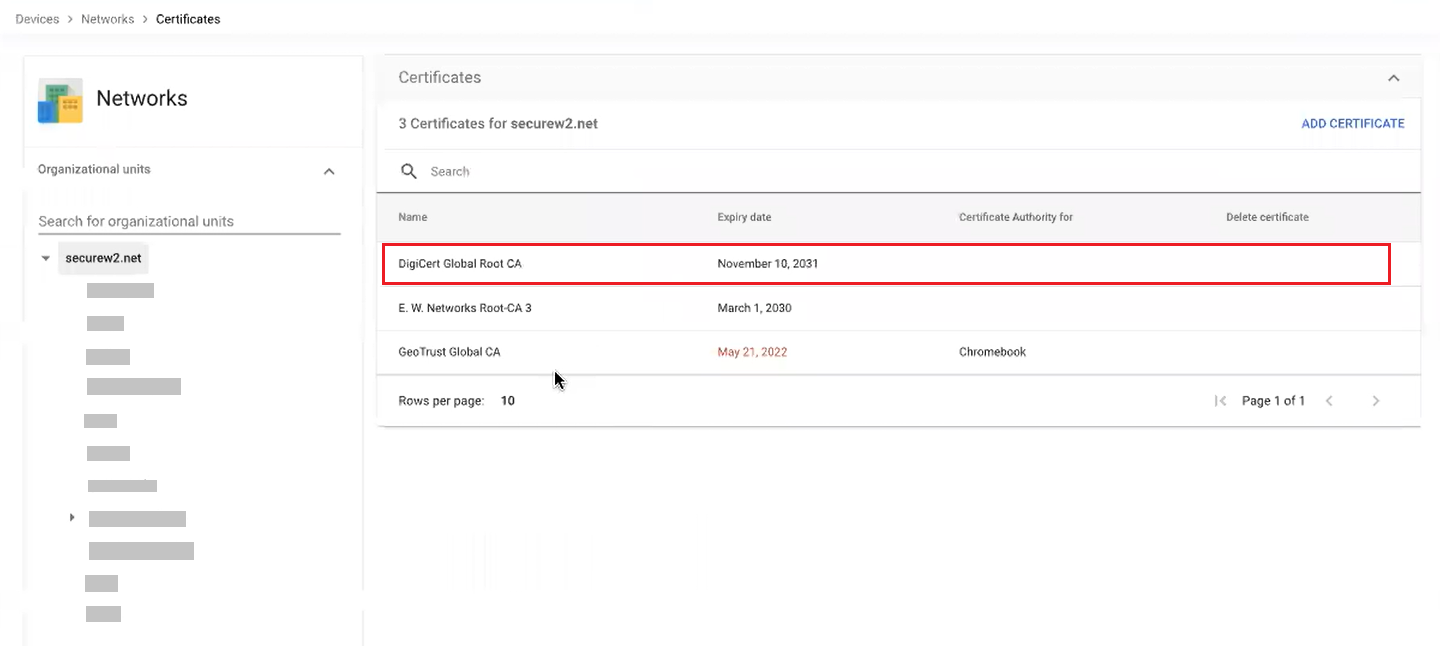
- Scroll down to the Certificates section and click Add/Remove Certificate.
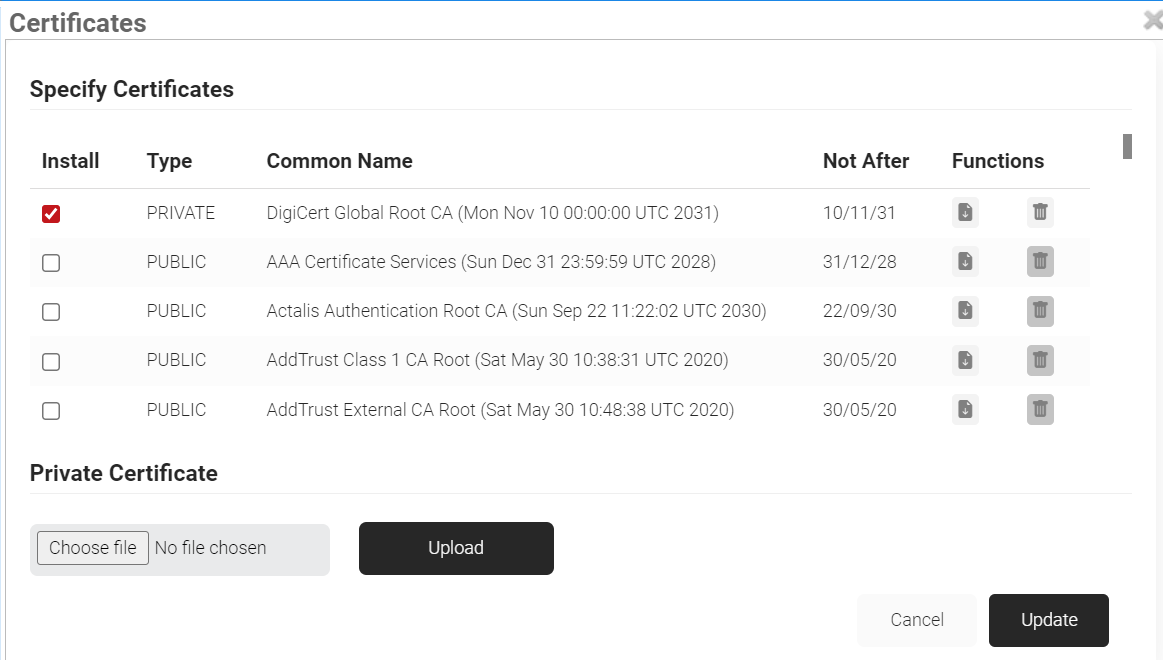
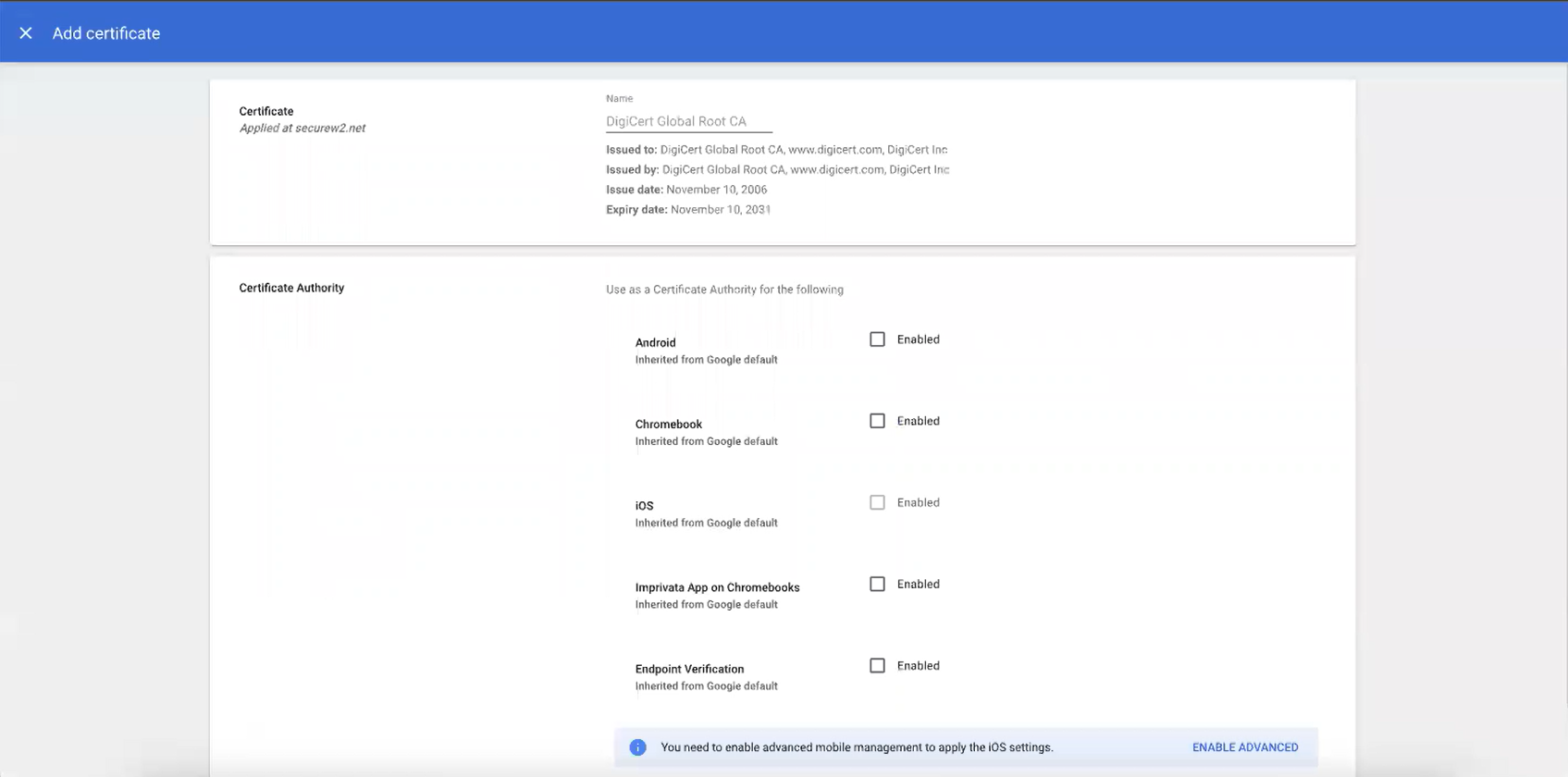
- In the Certificates pop-up window, select the checkbox next to DigiCert Global Root CA (Mon Nov 10 00:00:00 UTC 2031).
- Click Update.
- The certificate is added in the Certificates section.
- Click Download.
Configure the RADIUS Server Issuer CA Chain from the Google Admin Console
WPA2-Enterprise requires installing and configuring the trusted RADIUS Server issuer CA chain to allow the device to securely connect to the Wi-Fi network. This is also handled by the Google Admin Console. You can select the uploaded CA as the trusted CA in the configured Wi-Fi Network, later.
- Log in to the Google Admin Console.
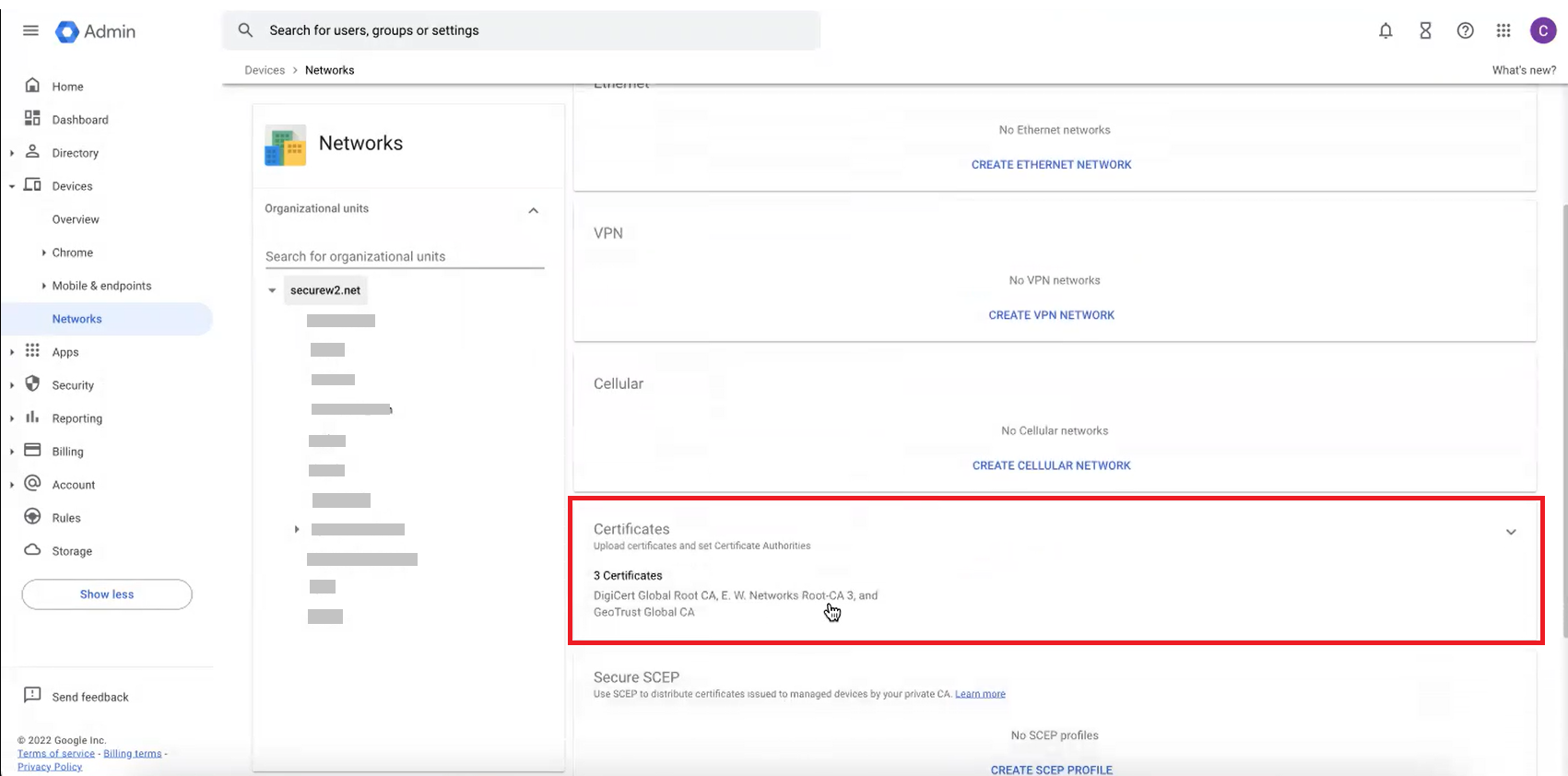
- Navigate to Devices > Networks.
- Scroll down and click Certificates.
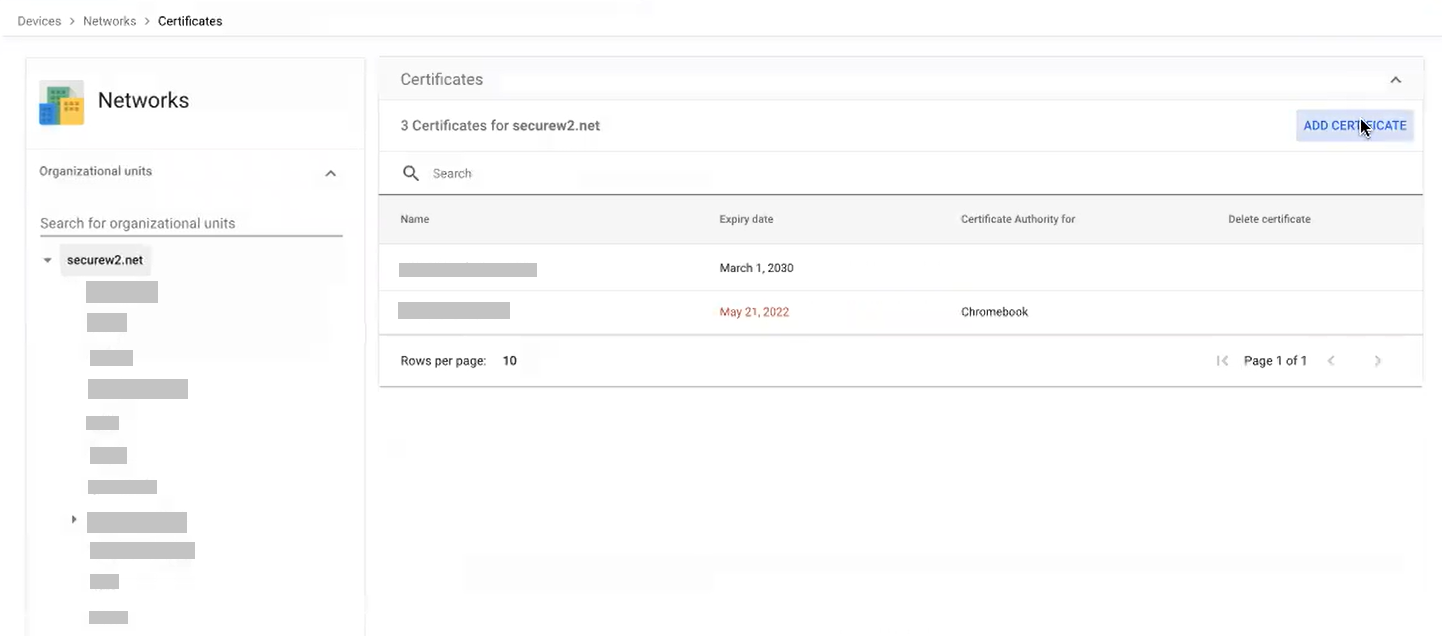
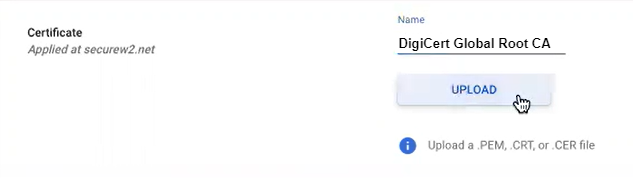
- On the Certificates page, click ADD CERTIFICATE.
- On the Add certificate page, in the Certificate section, in the Name field, enter the name of the certificate.
- Click the UPLOAD button to upload your RADIUS Server issuer CA chain.
- Click ADD.
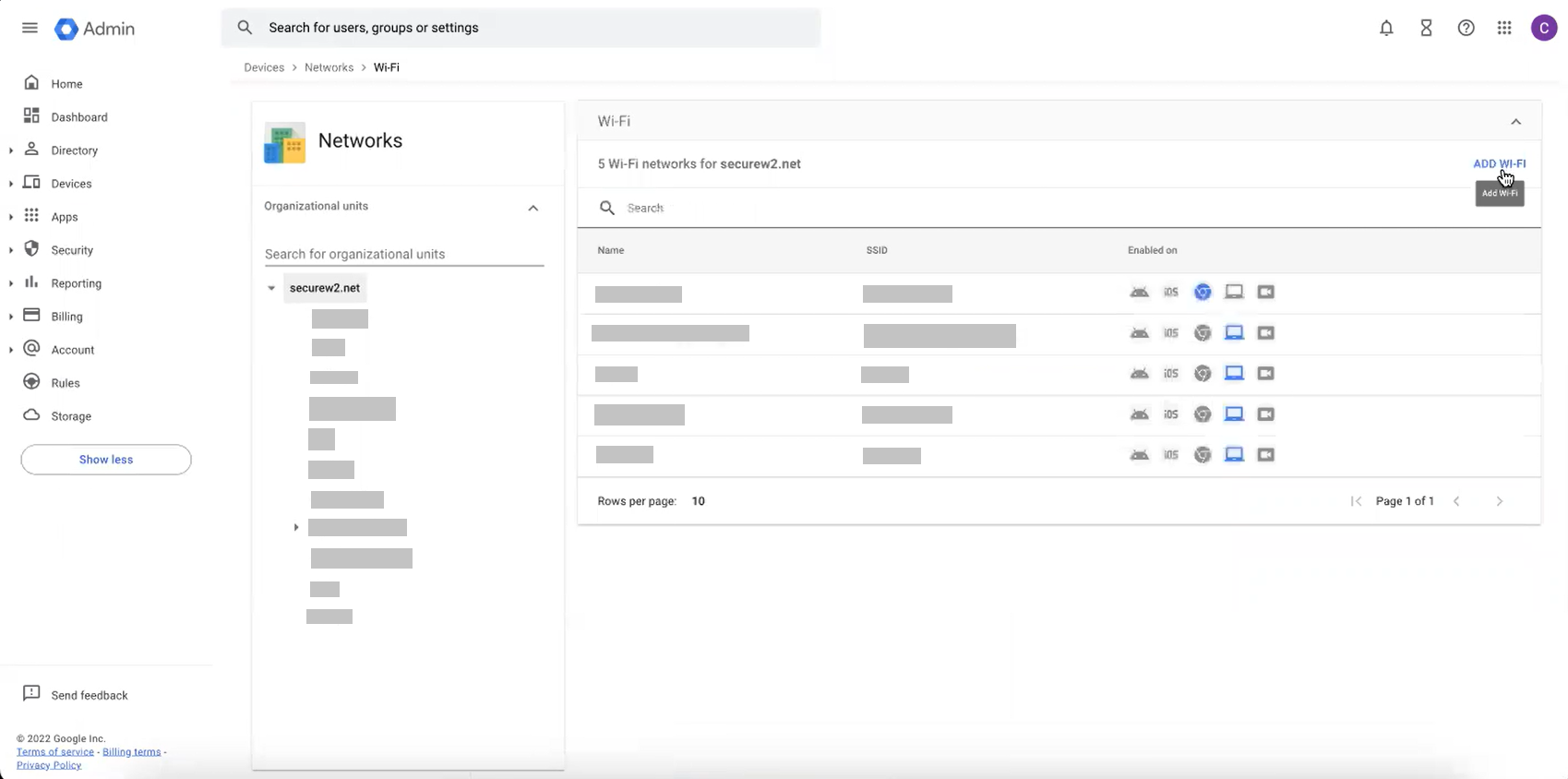
Configure the Wi-Fi Network from Google Admin Console
Finally, configure the network settings that will be pushed to the Chromebooks so that they will authenticate the SSID by using SecureW2 for certificate-based Wi-Fi authentication.
- Navigate to Devices > Networks.
- Select Wi-Fi.
- On the Wi-Fi page, click ADD WI-FI.
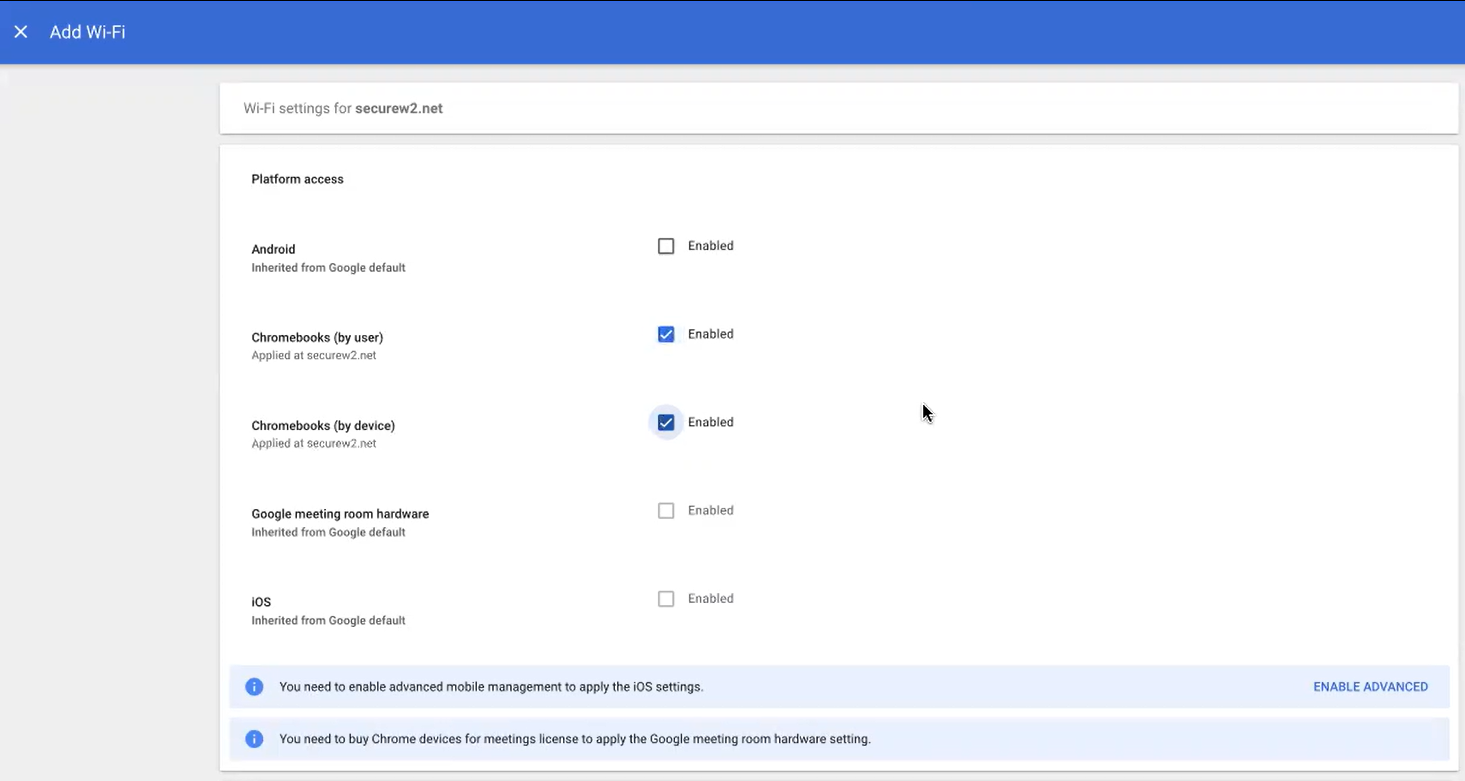
- On the Add Wi-Fi page, perform the following steps:
- Under the Platform access section, select the platform that you want to configure the WiFi.
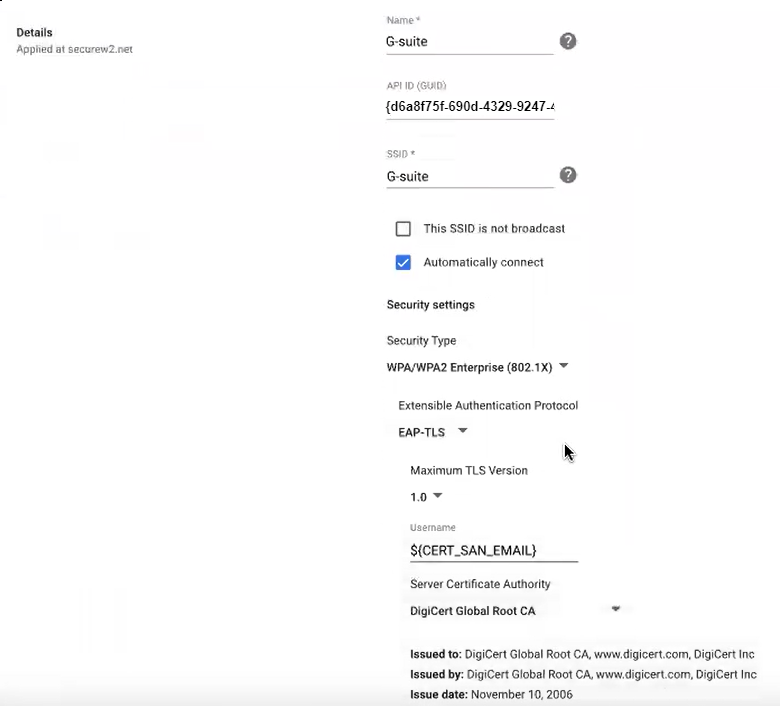
- Under the Details section, type a name and SSID of your Wi-Fi Network.
- Select the Automatically connect option.
- From the Security Type drop-down list, select WPA/WPA2-Enterprise (802.1X).
- From the Extensible Authentication Protocol drop-down list, select EAP-TLS.
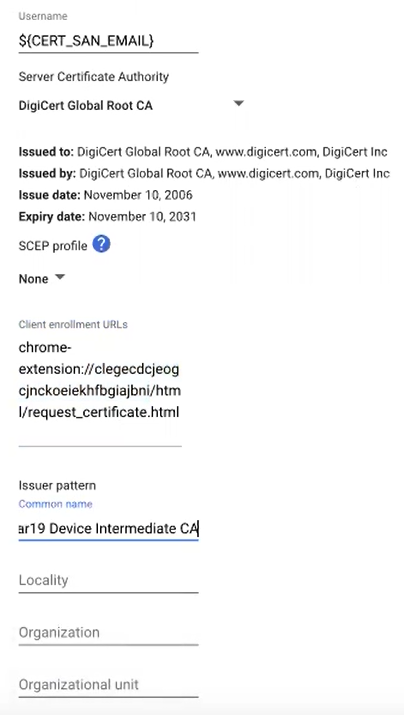
- In the Username field, type ${CERT_SAN_EMAIL} or ${CERT_SAN_UPN}.
- From the Server Certificate Authority drop-down list, select the RADIUS Server Issuer CA chain you uploaded earlier.
- In the Client enrollment URLs field, enter the following URL: chrome-extension://legecdcjeogcjnckoeiekhfbgiajbni/html/request_certificate.html
- In the Issuer pattern field, type the matching variables of the CA that will be using the client certificate (NOT the RADIUS Server Issuing CA).
NOTE: Currently, setting the Organization Name is tested.
- Click SAVE.
NOTE: When moving the devices to the specific OU for enrollment of certificates, ensure that the user also belongs to that specific OU.
- Under the Platform access section, select the platform that you want to configure the WiFi.
Superior Device Management with EAP-TLS Auto-Enrollment
As you click on the last save, your entire network is ready to use a digital certificate for superior security. You may now configure any Google managed device to your network settings and start registering the devices onto the network.
SecureW2s JoinNow will automate certificate issuance through JSON which is similar to the Simple Certificate Enrolment Policy (SCEP) for distributing certificates to all your managed device. You can also manage auto revocation of expired certificates for your device in our management portal.
SecureW2s Cloud RADIUS provides easy passwordless solution to connect your devices to a superior EAP-TLS which provides authentication of users and devices through a digital certificate seamlessly. Move away from legacy protocols and secure your network right now to protect it from phishing and over-the-air data theft
Ready to get started onboarding your own device on your network? SecureW2 is more affordable than you might think. Check out our pricing form to see for yourself.
Frequently Asked Questions On Certificate Enrollment Protocol (SCEP)
Does SecureW2 Use Simple Certificate Enrollment Protocol (SCEP) For Certificate Issuance in Chromebooks?
No, SecureW2 does not use SCEP. However, our Network Profiles and our industry-exclusive Chromebook Extension enables organizations to use JSON. JSON automates the Certificate Lifecycle for just like SCEP.
Why Should I Enroll For Certificates In a Google Chromebook?
Configuring your Google Workspace-managed device for EAP-TLS ensures better network security as EAP-TLS is the only Wi-Fi protocol that supports X.509 digital certificates, which are phishing-resistant.
Using certificates for network authentication also allows devices that might not belong to a specific user to have a secure, identifiable, network connection. For example, many schools use carts of Chromebooks that are shared among several classrooms. With certificates, you can issue a unique device certificate, also known as a machine certificate, that is used by the device when no one is logged into it. This ensures that our Chromebook always maintains a secure, encrypted connection to the Wi-Fi network, which is important because it needs one to validate users and issue them certificates when they sign in to their device.
Does Google Cloud Connector support Certificate enrollment through SCEP?
Google Cloud Connector does support the Simple Certificate Enrollment Protocol (SCEP) which has always been the standard way to auto-enroll managed devices for certificates. However, SCEP has some deficiencies when compared to the SecureW2 solution that uses the JSON protocol.
The SCEP solution that Google provides does not provide automatic updates on event logs of enrollments on the network. Also, an expired certificate cannot be revoked once they are installed on a device. Also, the SCEP solution that Google proposes, requires the use of NDES and Active Directory Certificate Services (AD CS). Most organizations are moving away from using on-premise Windows servers, as they can be costly and cause vulnerabilities on the network. If you are interested in using SCEP with Google Cloud Connector, you can find their documentation here.
Is JSON a better certificate enrollment protocol than SCEP?
Yes and No. For most operating systems, we recommend the use of SCEP. As a widely used standard, almost every MDM supports the use of the SCEP protocol for auto-enrolling managed devices for certificates. There are many advanced SCEP implementation, like the ones provided by Intune and Jamf, that allow us to validate users and devices in real-time to increase security.
However, in our research, we have found that the combination of JSON and our Certificate Extension provides us with some advantages. Our solution provides better clarity on the event log reporting i.e. an admin can see which devices and users are on the network. They can also see how many authentication attempts were made, whether they appsed or failed etc. This information can be added to the event and printing certificates.
How Does Certificate Enrollment Work?
Certificate enrollment begins with the user or device requesting a certificate from a Certificate Authority (CA). It contains a public key and other information before the request is sent to a certificate authority. The CA verifies the information based on an advanced set of rules and policies. Upon verification, the CA creates the certificate, which the device then ties to a Private Key that was generated on the client’s TPM or Secure Enclave.
A Public Key Infrastructure (PKI) is a vital infrastructure to have if you want to use digital certificates to secure your network. It is necessary to create and manage CAs and the client certificates that they issue.
SecureW2s JoinNowConnector PKI offers a variety of ways to enroll devices for certificates. It offers an onboarding application that enables unmanaged devices to self-service themselves for certificates. It also offers Managed Device Gateways, shown in this document integrating with Google Workspace, to help manage the certificate lifecycle for your organization. This enables admins to auto-enroll, revoke or renew certificates seamlessly and in a more secure manner that is up-to-date with the information that exists in their MDM.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing