Integrating Kandji with EAP-TLS for Certificate Auto-Enrollment
The Simple Certificate Enrollment Protocol (SCEP) can be used by MDMs to automate the certificate life cycle for Managed devices. This saves administrators time compared to manually enrolling managed devices for certificates.
Kandji is an MDM platform that works for Apple devices like MacOS, iOS, iPadOS, and tvOS. It also supports security and productive global work with the help of an advanced automation system. When it comes to certificate enrollment with SCEP, Kandji provides the SCEP URL and key, which the device can use to request a certificate from the PKI.
In this document, we will show you how to configure SecureW2 SCEP Gateway API to auto-enroll Kandji-managed devices for certificates and configure the user device for Certificate-Based Wi-Fi authentication.
Prerequisites
For using any of the following two options, you must have the following subscriptions:
- Active SecureW2 Cloud Connector License
- Active SecureW2 Managed Device Gateway License
- Active Kandji License
- Enterprise-grade Access Points (They Support WPA2-Enterprise)
- iOS or macOS Devices Actively Managed in Kandji
SecureW2 Custom .mobileconfig for SCEP and Wifi Configuration:
- Name of SSID Devices that requires authentication.
- RADIUS Server Root CA.
- Required Certificate Attributes:
- Subject Field
- Subject Alternative Name Type
- RFC 822 Name
- Key Size
- Key Usage
After you’ve received the custom .mobileconfig file from the support team, you will need to insert the SCEP URL and Challenge that is generated from the JoinNow Management Portal.
Generate a SCEP URL and Secret
To generate a SCEP URL and secret:
- Log in to the JoinNow Management Portal.
- Navigate to Identity Management > API Tokens.
- Click Add API Token.
- In the Basic section, enter the name of the API token in the Name field.
- In the Description field, enter a suitable description for the API token.
- From the Type drop-down list, select SCEP Enrollment Token.
- From the SCEP Vendor drop-down list, select Kandji.
- From the Certificate Authority drop-down list, select a CA created in the JoinNow Management Portal.
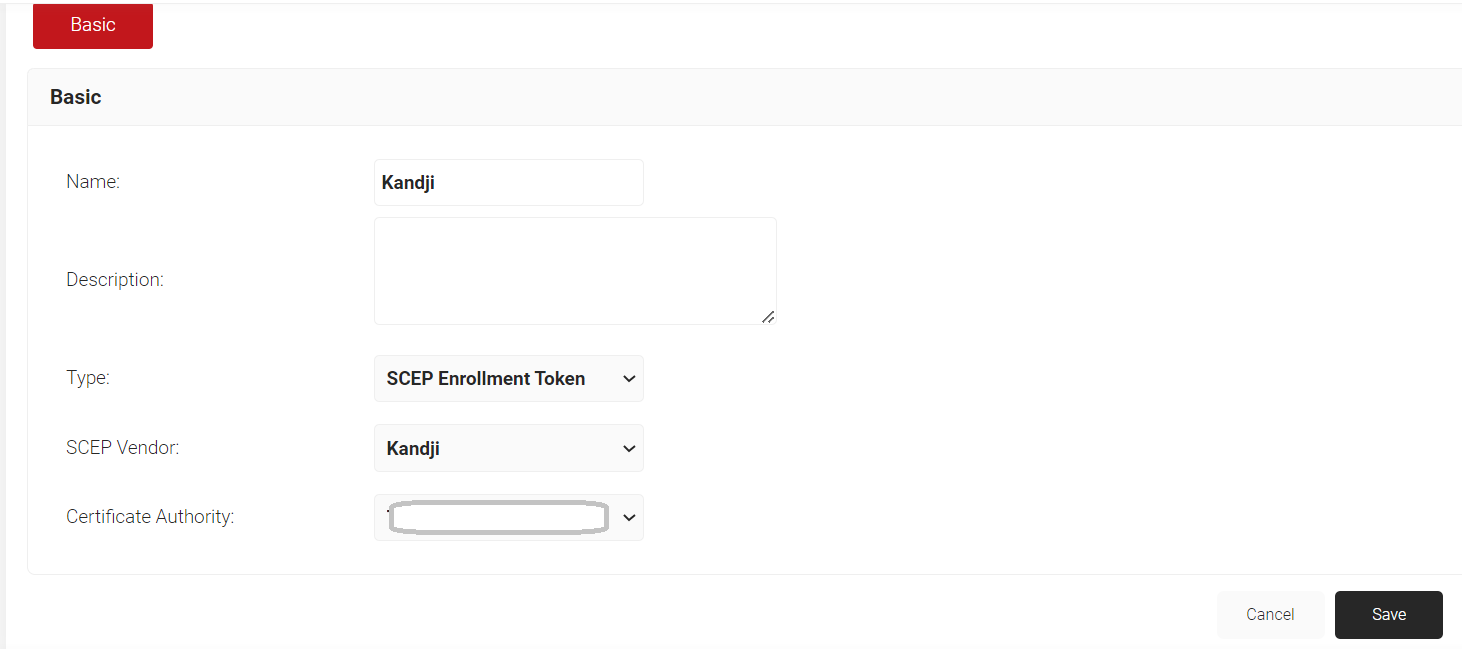
- Click Save.
- A .csv file will download that contains your SCEP URL and Secret Key.
- Paste the SCEP URL into the URL field in Kandji.
- Paste the Secret Key into the Challenge field in Kandji.
Create a new BluePrint by navigating to Library > Add Custom profile and upload the profile that has been shared. This should configure the device to get a certificate from the JoinNow Management portal and connect it to the secured SSID.
Native Kandji SCEP Configuration + Custom Wi-Fi .mobileconfig
The second option is that you can create a SCEP configuration using the Kandji Library. However this will still require a custom .mobileconfig to be uploaded for the Wi-Fi configuration. Creating a Blueprint lets you specify a set of behaviors and library items to be deployed to a group of devices.
- Create a new Blueprint or use an existing Blueprint.
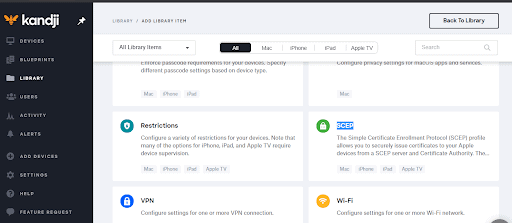
- Navigate to Library > Add a New Library.
- Select SCEP and then click Add & Configure.
Here you could add the SCEP URL and the shared Key that you have received from SecureW2 Management portal and assign it to the Blueprint that was created from the previous step.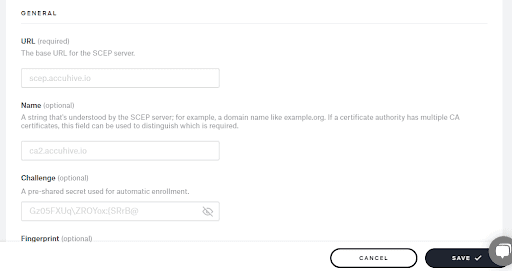
First we need to generate a SCEP URL and Challenge from JoinNow Management Portal
- Navigate to Identity Management > API Tokens.
- Click Add API Token.
- In the Basic section, enter the name of the API token in the Name field.
- In the Description field, enter a suitable description for the API token.
- From the Type drop-down list, select SCEP Enrollment Token.
- From the SCEP Vendor drop-down list, select Kandji.
- From the Certificate Authority drop-down list, select a CA created in the JoinNow Management Portal.
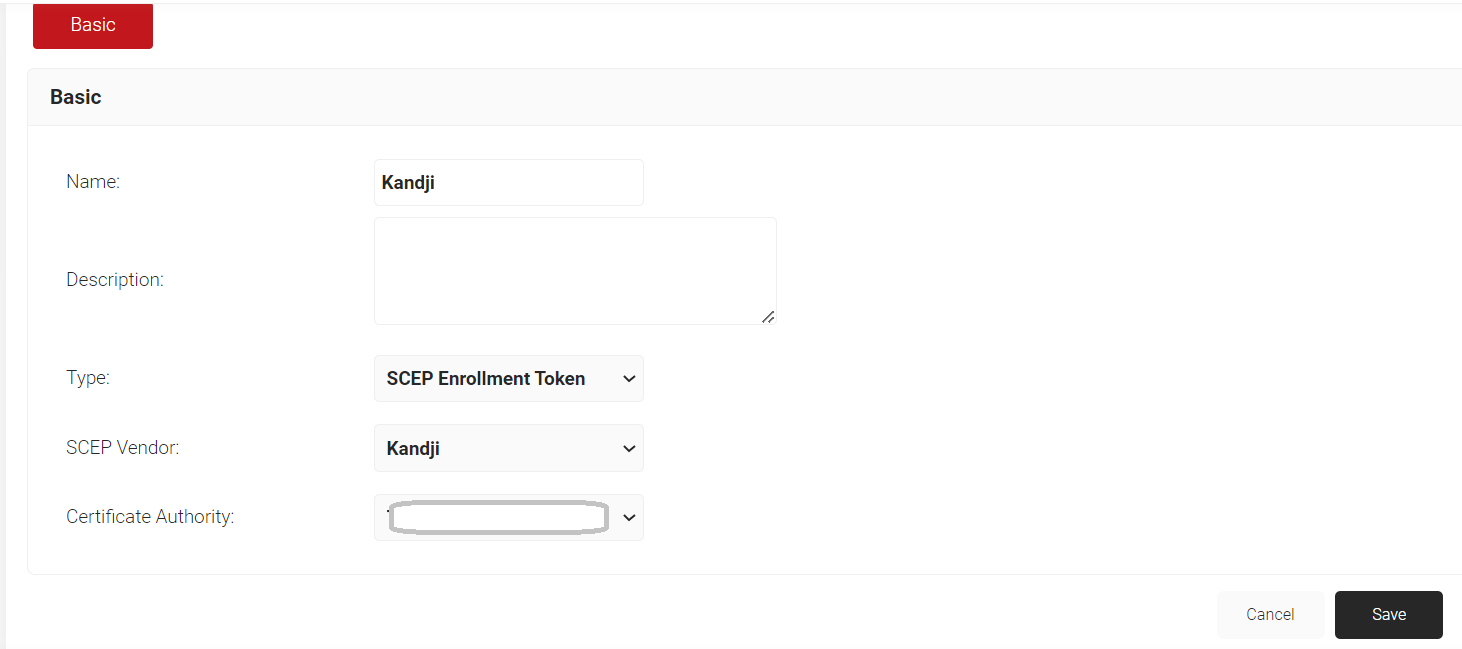
- Click Save.
- A .csv file will download that contains your SCEP URL and Secret Key.
- Paste the SCEP URL into the URL field in Kandji.
- Paste the Secret Key into the Challenge field in Kandji.
Now navigate back to the Kandji portal to populate the other settings required for a SCEP Profile.
- Subject Field: This field can have any variable that is desired, typically we populate this with the email.
- Subject Alternative Name Type: Enter RFC 822 Name. This field is mandatory.
- RFC 822 Name: Enter $SERIAL_NUMBER.
Note: The $SERIAL_NUMBER will be used to encode on the certificate and would create an entry in the JoinNow Management Portal for a device. You can enter multiple values sent using RFC 822 Name separated by a semicolon. - NT Principal Name: Optional field and can be left blank.
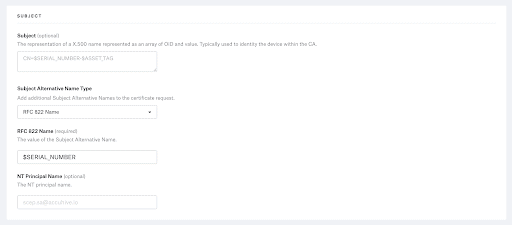
NOTE: RFC 822 Name is a mandatory field that needs to be sent from Kandji to encode the SAN values in a certificate. - Key Size: 2048(Mandatory field).
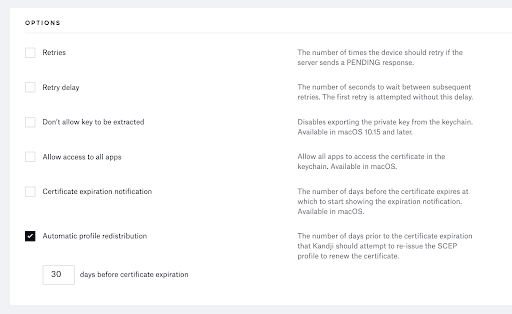
- Key Usage: Both Signing & Encryption.
NOTE: We set Key Usage as Both Signing & Encryption, but in our test lab we found that it works without selecting any option. - Scroll down to the Options section. Enable Automatic profile redistribution. This field is mandatory. We suggest you set the redistribution 30 days before certificate expiration.
Secure EAP-TLS Authentication with Kandji and SecureW2
With our SCEP API gateways configured, your organization can use Kandji to automatically enroll your Kandji-managed devices for certificates. It’s an elegant solution that uses our gateways to issue a SCEP URL and Key to your managed devices, allowing them to request certificates from our PKI with no end-user input.
SecureW2 PKI offers a better user experience and and a PKI that can seamlessly integrate with Kandji for SCEP certificate enrollment.This leads to faster and simpler certificate distribution so your administrators can focus on other tasks.. For more information, click here to see our pricing details.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing