If you manage devices using Meraki MDM (Mobile Device Management), you may improve network security by pushing certificates to them via a Meraki SCEP (Simple Certificate Enrollment Protocol) CA certificate. SCEP is a protocol that automates the issuing of digital certificates to managed devices, which can be used to replace credentials in different uses, including for Wi-Fi, VPN, and application security. This setup dramatically improves network security and user experience. However, adopting Meraki’s default certification settings may expose your network to threats such as credential theft.
In this article, we’ll show you how to configure certificates in Meraki Systems Manager to build a robust and secure network environment. You can automate certificate deployment across all major operating systems, including Windows, iOS, and Linux, using Cisco Meraki Solutions and engineering Meraki technologies. The setup process includes generating an onboarding SSID, setting the SCEP server, and pushing certificates to endpoints managed by the Meraki Systems Manager. This solution protects your wireless LAN networks from unauthorized access, offering a solid security layer for your implementation.
Meraki Systems Manager can efficiently manage certificates by carefully configuring and deploying them, improving security for all connected devices in your network. This method strengthens your network and simplifies the process of ensuring safe access to controlled devices.
Using Meraki’s Default SCEP CA is a Security Risk
Meraki Systems Manager offers users a free trial that enables them to download certificates immediately. This situation is due to Meraki’s default settings, which means the RADIUS server is configured to accept any device with access to the Meraki CA.
Utilizing default Meraki Systems Manager settings is not recommended due to the risk of credential theft. Meraki’s default settings don’t utilize certificate signing requests (CSR), enabling the CA to approve certificates on your network. Without CSR, your RADIUS server will accept any Meraki Systems Manager device. To gain access, all that is needed for a rogue device is to avail itself of Meraki’s free trial, download a Meraki certificate, and configure the device to access the network.
EAP-TLS and Meraki Integrations with SecureW2
EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) is safe since it authenticates users and devices through digital certificates. This solution avoids the hazards associated with password-based authentication, including credential theft and brute force attacks. Digital certificates issued by a trustworthy Certificate Authority (CA) ensure that only authorized devices may access the network, adding extra protection.
In addition to better security, EAP-TLS provides the benefit of reciprocal authentication. This implies that the client and server verify one another, guaranteeing that devices only connect to valid network resources. This reciprocal trust considerably lowers the likelihood of man-in-the-middle attacks. EAP-TLS further improves the user experience by eliminating the need to memorize complicated passwords; their devices automatically authenticate using the loaded certificates.
SecureW2’s integration possibilities go beyond just providing certificates. We also enable a seamless connection with Meraki Access Points, which offers a complete network security solution. Integrating SecureW2 with Meraki Access Points ensures safe and efficient network access throughout your organization. Our JoinNow Management Portal simplifies distributing and managing certificates, allowing you to maintain a strong security posture. SecureW2’s solutions are adaptable and can interact with various suppliers, ensuring your network is safe and efficient.
Using Meraki’s default SCEP CA for certification might cause security concerns owing to its setup, which allows any device access to the Meraki CA. This configuration might result in unauthorized network access if a rogue device receives a Meraki certificate via the free trial. To reduce this risk, we’ll walk you through setting the SecureW2 PKI and RADIUS server and connecting it with your Meraki MDM (Mobile Device Management) configuration. This technique will allow you to maintain certificates reliably and securely while protecting your network from attacks.
Configuring the SecureW2 PKI and RADIUS Server
To configure a wireless network profile, perform the following steps:
- Log in to the JoinNow Management Portal.
- Navigate to Device Onboarding > Getting Started.
- On the Quickstart Network Profile generator page, from the Profile Type drop-down list, select Wireless.
- In the SSID field, type the name of a profile.
- From the Security Type drop-down list, select WPA2-Enterprise.
- From the EAP Method drop-down list, choose EAP-TLS.
- From the Policy drop-down field, retain DEFAULT.
- From the Wireless Vendor drop-down list, choose Cisco Meraki.
- From the RADIUS Vendor drop-down list, select a RADIUS vendor.
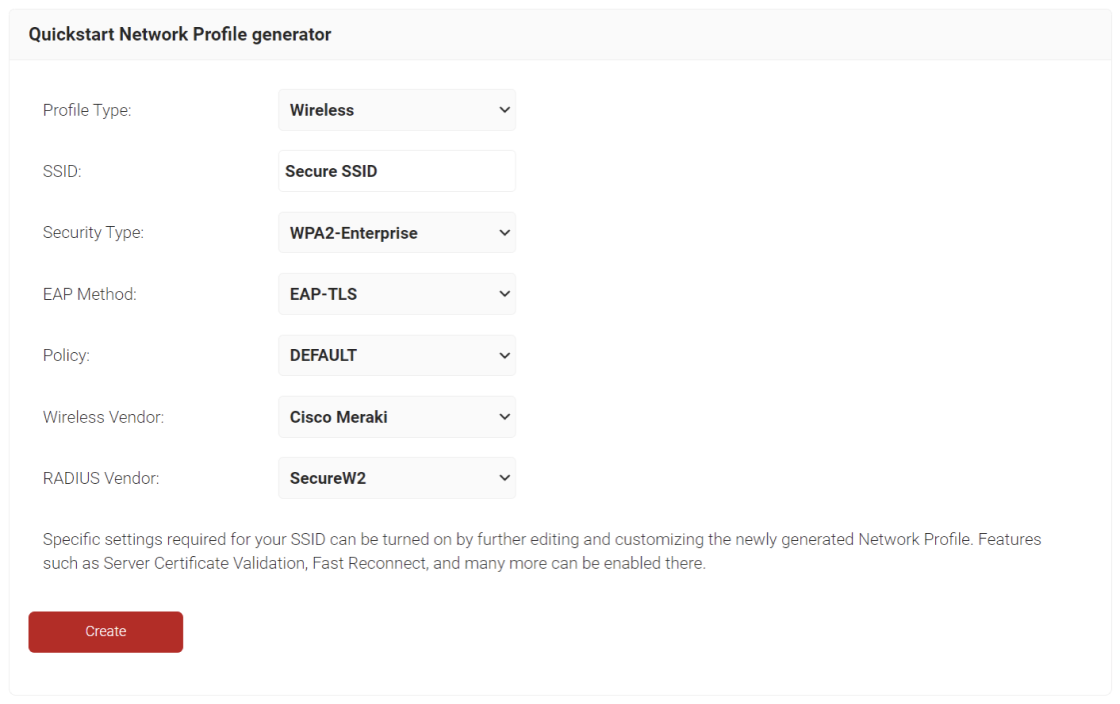
- Click Create.
To access the RADIUS details, follow the below steps.
- Navigate to RADIUS > RADIUS Configuration.
- Copy the Primary IP Address, Authentication Port and Shared Secret of your subscribed region to your console.
Setting Up SecureW2 as RADIUS Server in Meraki
Follow the below steps to configure the RADIUS server in Cisco Meraki.
- Log in to the Meraki Dashboard.
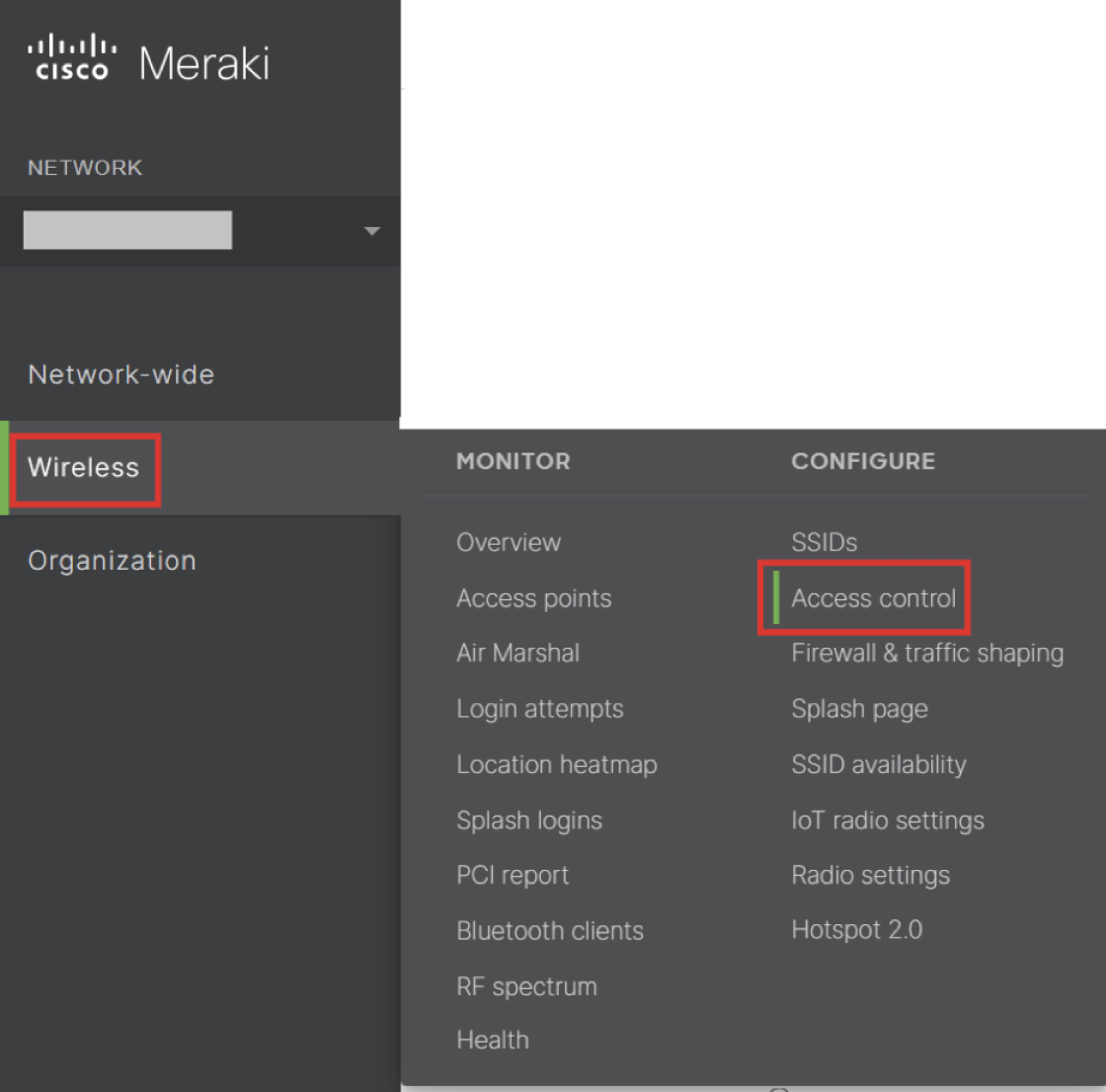
- Navigate to Wireless > Access control.
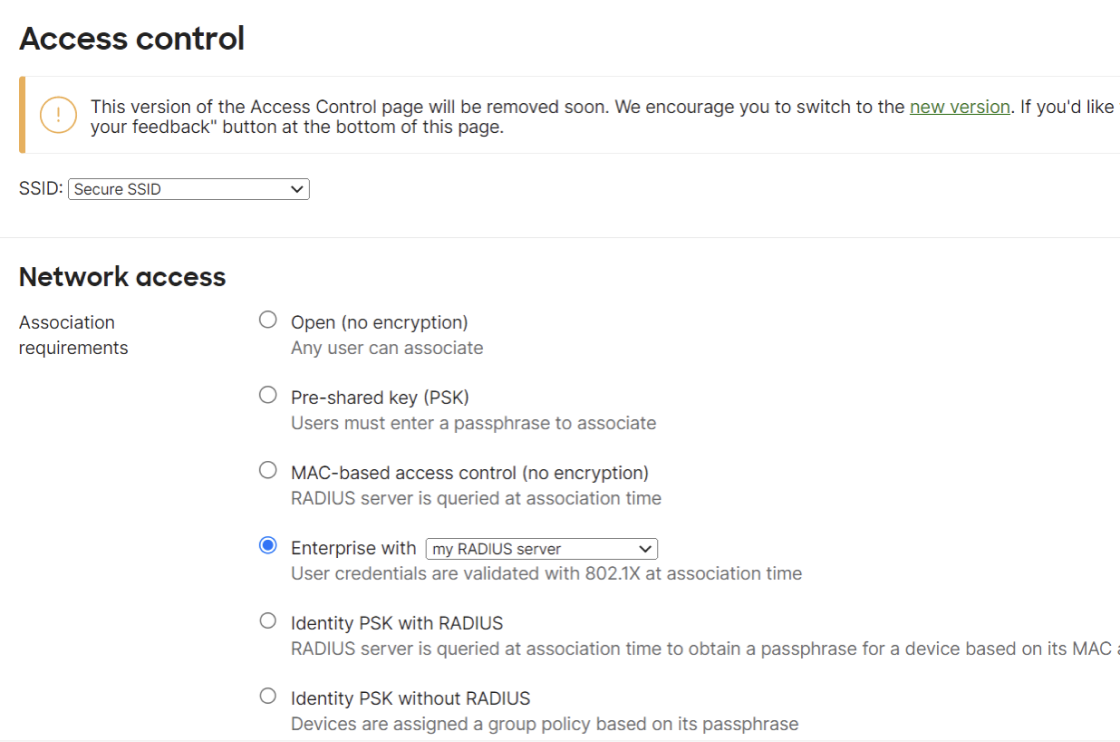
- In the Network access section, for Association requirements, from the Enterprise with a drop-down list, select my RADIUS server.
- From the WPA encryption mode drop-down list, select WPA2 only (recommended for most deployments).
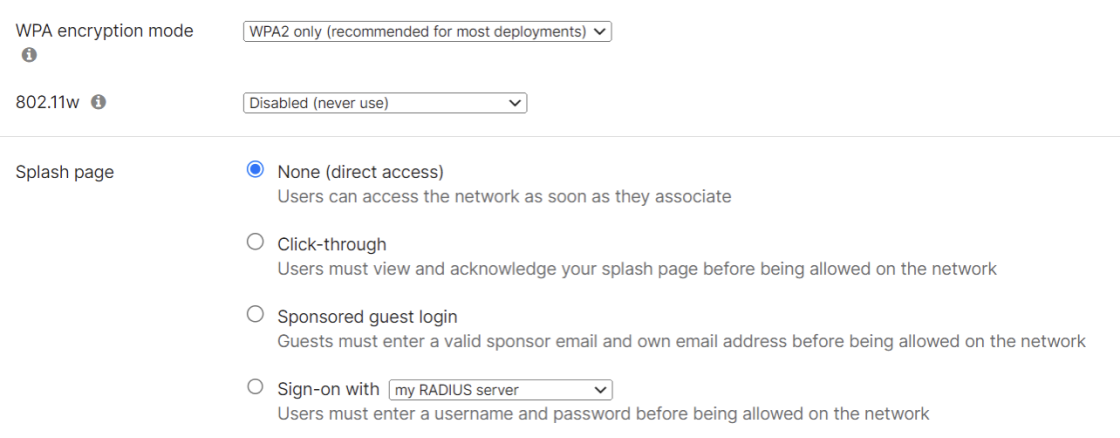
- Under the Splash page, select None (direct access).
- In the RADIUS servers section, click Add a server.
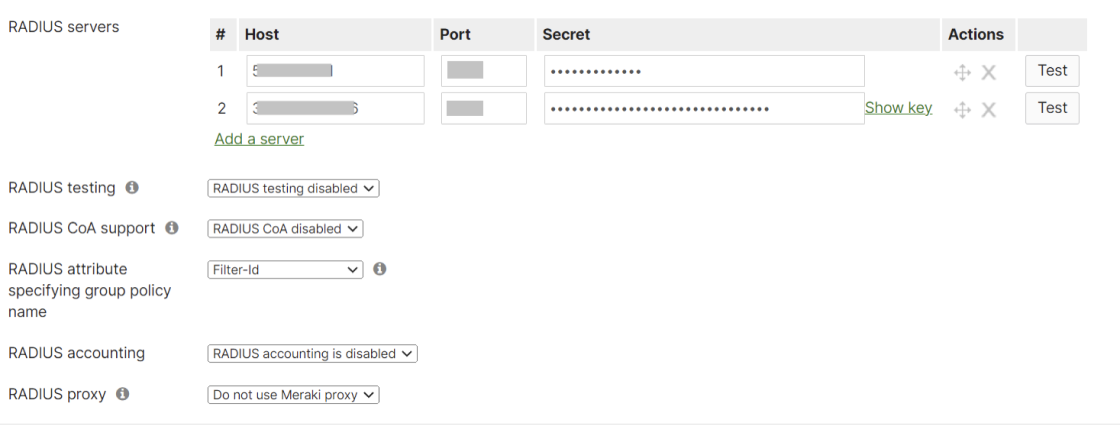
- From the JoinNow Management Portal (navigate to RADIUS > RADIUS Configuration), copy the Primary IP Address, Authentication Port, and Shared Secret and paste them into the Host, Port, and Secret fields in the Meraki.
- In the RADIUS servers section, click Add a server again.
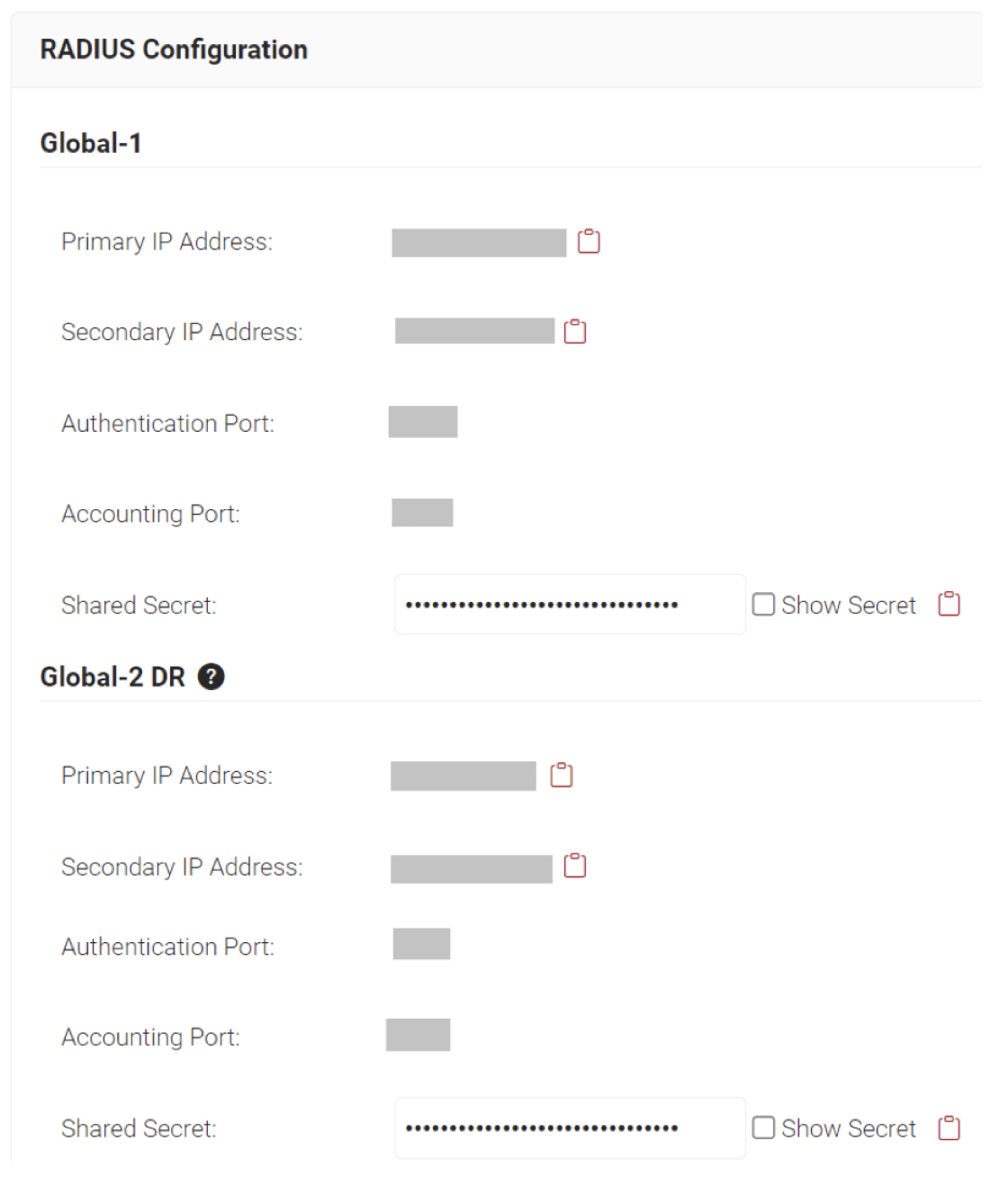
- From the JoinNow Management Portal (navigate to RADIUS > RADIUS Configuration), copy the Secondary IP Address, Authentication Port and Shared Secret and paste them in the Host, Port, and Secret fields in the Meraki.
- Click Save Changes.
Configure Access Point to use Splash Page
Follow the steps below to configure the access point.
- Log in to the Meraki Dashboard.
- Navigate to Wireless > Access Control.
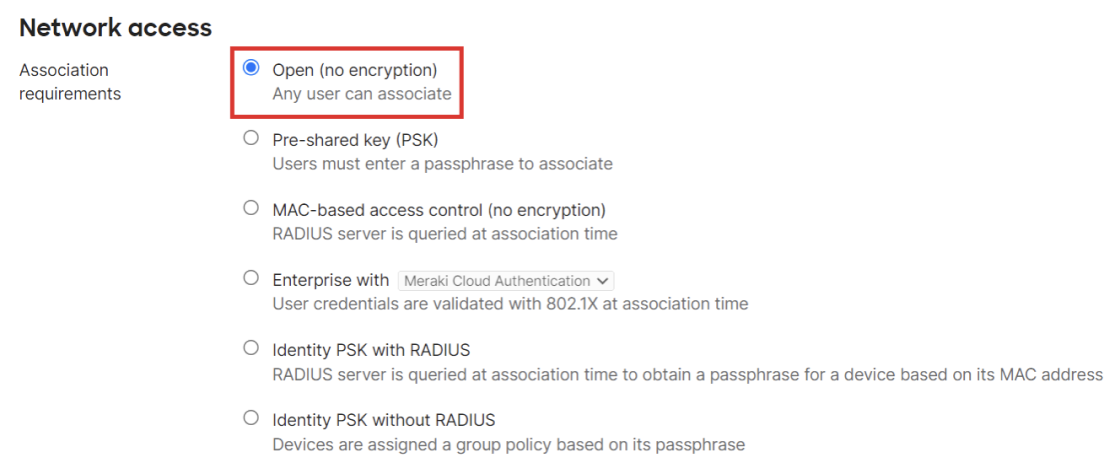
- Under Network access, select Open (no encryption) in the Association requirements section.
- Under the Splash page, select Click-through.
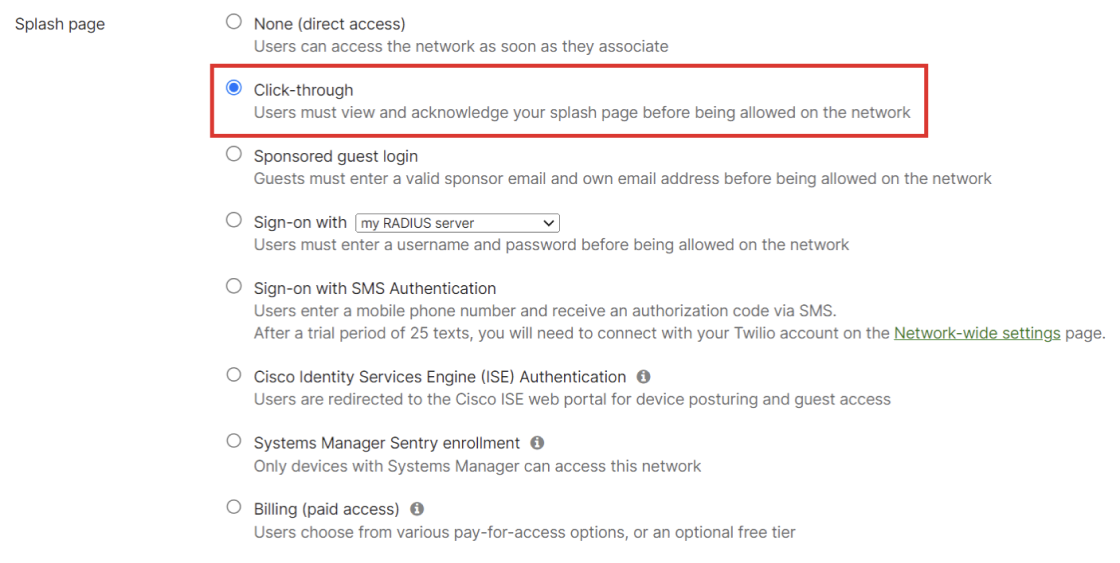
This process redirects to the SecureW2 landing page.
Creating a Certificate Authority with a Meraki Certificate Signing Request
- To set up your own CA:
- Open the System Manager.
- Click MDM under Organization.
- Scroll down to the SCEP configuration section.
- Download the CSR.
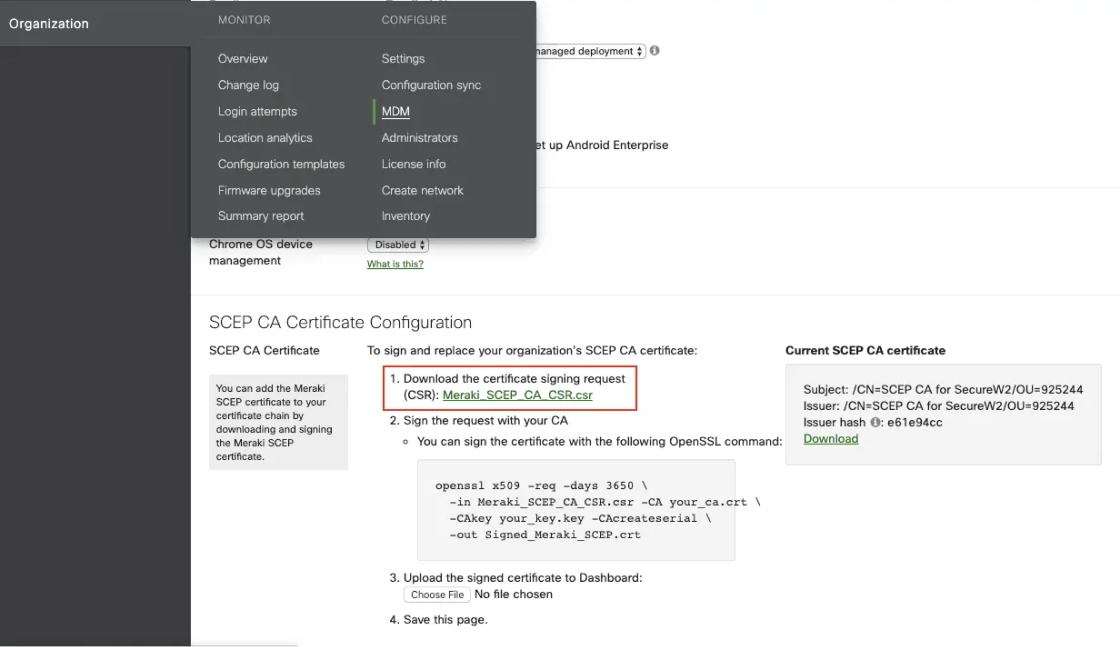
You’re now able to use this downloaded CSR file and generate a customCA. We did this by using SecureW2’s management portal to create a new certificate authority using Meraki’s CSR and generate a new certificate authority.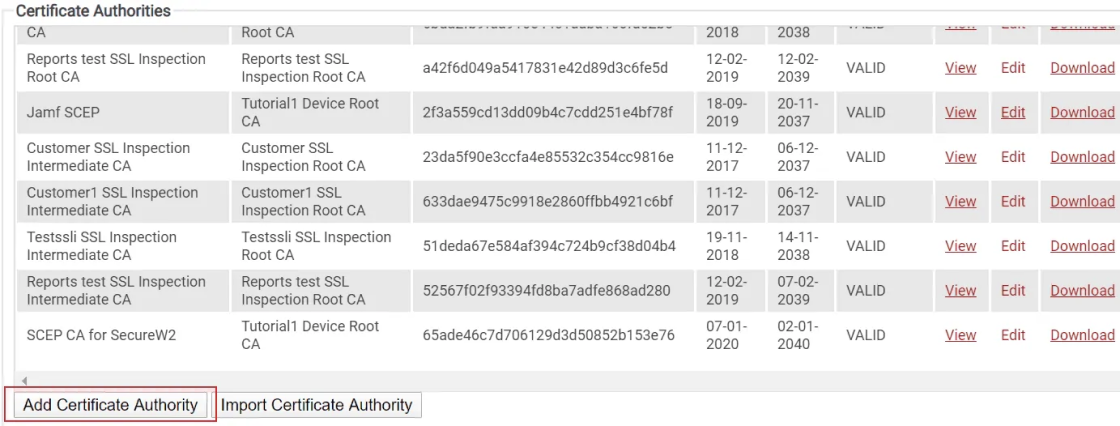
Here’s how to create a Custom CA with a Certificate Signing Request in SecureW2:
- Under Certificate Authorities:
- Click “Add Certificate Authority”.
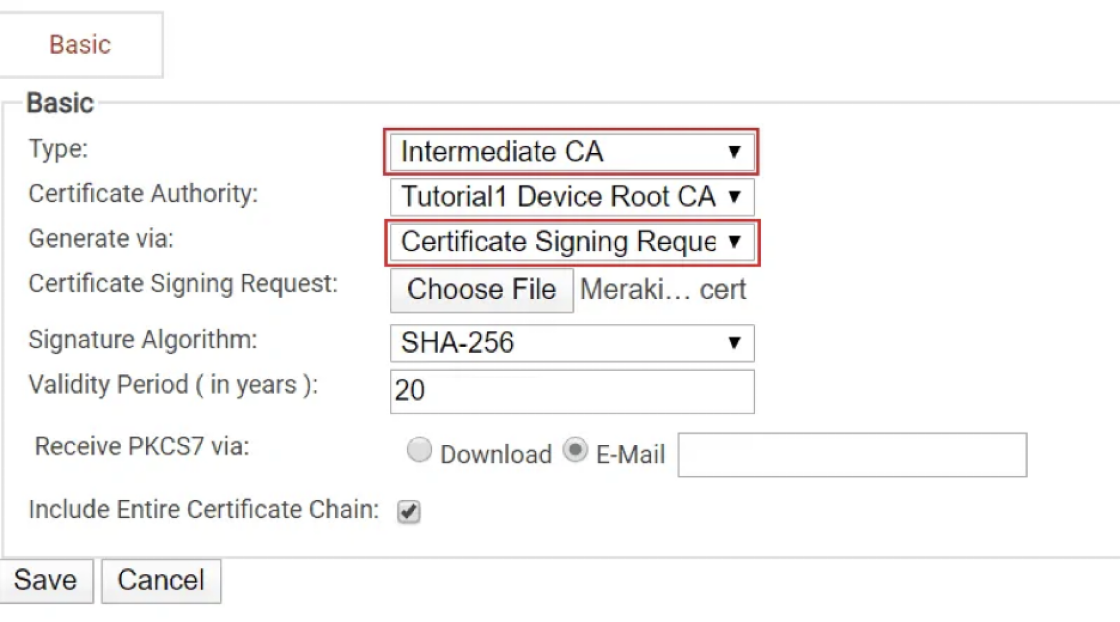
- Configure the settings to create a customCA:
- Under Type, choose Inter CA.
- Generate via Certificate Signing Request.
- A new option will pop up, allowing you to upload the CSR we got from Meraki.
- Leave the other options as the default.
- you can now download a signed certificate after creating the custom CA.
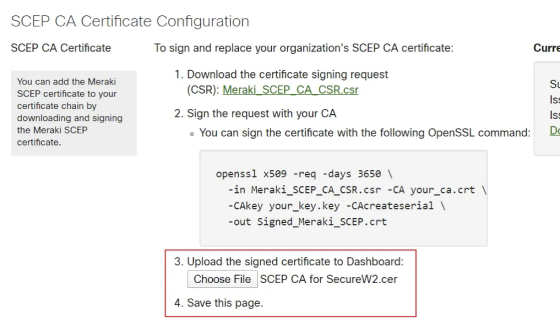
- After creating your custom CA, you can download a signed certificate:
- Go back to Certificate Authorities.
- Download your custom CA certificate.
- Head back to Meraki Systems Manager to upload your new certificate:
- Go back to SCEP settings under MDM.
- Upload the new signed certificate.
- Save the page.
How to Configure Cloud RADIUS for X.509 Certificate Authentication
Configuring your managed devices for X.509 certificate authentication consists of three significant steps: integrating a Public Key Infrastructure (PKI), such as SecureW2, with your Identity Provider (IDP); using a Cloud RADIUS service that is linked to your infrastructure; and integrating your PKI with your Mobile Device Management (MDM) system. The process varies slightly based on your infrastructure, so in the example steps below, we’ll demonstrate how you can set this up if your organization uses Azure AD/Entra ID.
Step 1: Configure SecureW2 PKI Services and Certificate Attribute Mapping
Configure Attribute Mapping in SecureW2.
In the SecureW2 Administration Portal, go to Identity Management > Identity Providers. Here, you may map properties such as “upn,” “email,” and “displayName.” To set these properties, edit the IDP and navigate to the Attribute Mapping tab. Local and remote groups can be mapped using Object ID values obtained from the Microsoft Azure Portal.
Update the profile policy in SecureW2.
To amend the profile policy, navigate to Policy Management > Profile on the Administration dashboard. Edit the policy settings and choose the Identity Provider (IDP). After making your changes, click the Update button.
Update the user role policy in SecureW2.
Navigate to Policy Management > User Roles. Choose the desired IDP from the dropdown menu on the Conditions page of the DEFAULT ROLE POLICY 1. Click Update to save the changes.
Create a User Role Policy in SecureW2.
In the User Roles sub-menu, select Add Role, name the role, and save it. Select an IDP from the Conditions tab and click Update to finalize the new position.
Create an Enrollment Policy in SecureW2.
Under the Enrollment section, select Add Enrollment Policy. Name the new policy, choose the relevant user and device role policies from the Conditions tab, and click Update.
Republish your network profile.
In Device Onboarding > Network Profiles, click Publish or Republish next to the profile you wish to alter. Wait around 60-90 seconds for the modifications to take effect. To access the Wi-Fi wrapper package, click View and then JoinNow. Download and run the file, sign in with your Azure credentials, and confirm successful registration and connection.
Step 2: Integrate With Your Identity Provider (IDP) by Creating an App in Azure for RADIUS Lookup
SecureW2 interacts seamlessly with various SAML and LDAP IDPs, including Azure AD. Here’s how to set it up if you’re using Azure AD.
New App Registration
In Azure, navigate to App Registrations and create a new app. Fill out the required information for the latest app registration.
Create a client secret.
In the Manage menu, select Certificates & Secrets. Create a new client secret, name it, choose an expiry date, and add it. Then, take down the client’s secret value.
Create a Provider URL and Client ID.
The application (client) ID and provider URL are on the Azure Overview page. Please take note of your tenant ID and replace it in the URL syntax https://login.microsoftonline.com/{tenantID}.
API Permissions
In the Manage tab, choose API Permissions to allow the app access to your Azure directory. Add the required permissions and provide admin access to your organization.
Step 3: Enroll Users for Certificates
Create an onboarding SSID.
Use SecureW2’s JoinNow suite to generate an Open SSID for onboarding managed devices.
Apply Gateway APIs for Managed Devices.
Use SecureW2’s Managed Device Gateway APIs to automate the certificate enrollment process for managed devices. These APIs integrate smoothly with typical MDM applications for registering machine and user certificates.
Install intermediate and root CA certificates on a RADIUS server.
Install the Root and Intermediate CA certificates from SecureW2’s PKI on the RADIUS server. Set up a secure SSID using certificate authentication and WPA2-Enterprise. Integrate SecureW2’s PKI with the RADIUS server by including the Root and Intermediate CA certificates in the trusted list. On the RADIUS server, define the authentication protocol (EAP-TLS) and set up permission policies.
Fast SCEP Certificate Issuance to All Your Meraki MDM Endpoints
Implementing a secure Meraki MDM system that includes SecureW2’s PKI and RADIUS server improves network security and guarantees that only authorized devices can access your resources. By avoiding the problems of Meraki’s default certification settings and implementing SecureW2’s comprehensive solutions, you can safeguard your network from possible attacks while improving the overall user experience. SecureW2 provides cost-effective, simple-to-implement solutions that interact smoothly with Meraki MDM and other vendors, resulting in a holistic approach to network security.
Contact us today to learn more or get started.