Extreme Networks Integration
Introduction
Maximize your Extreme wireless network by integrating with SecureW2’s onboarding solutions. Integration takes hours, not days, and requires no forklift upgrades of existing infrastructure to deploy a WPA2-Enterprise network with EAP-TLS authentication. By utilizing certificates, organizations can gain the security benefits of certificate-based authentication, as well as configure them for SSL inspection, VPN, wired security, and much more.
This setup will demonstrate how to integrate with existing Extreme APs to configure a certificate-based 802.1x authentication network for secure Wi-Fi access.
To complete this setup, you will need to have configured:
- Extreme Networks Access Points and Controller
- A SecureW2 Network Profile
Configuring SecureW2 RADIUS
- In the Extreme Networks dashboard, click Configuration > Network
- To create a new AAA Policy, click AAA Policy > Add
- Add a name to the policy and click Continue
- In the RADIUS Authentication tab, click Add to create a new RADIUS Server
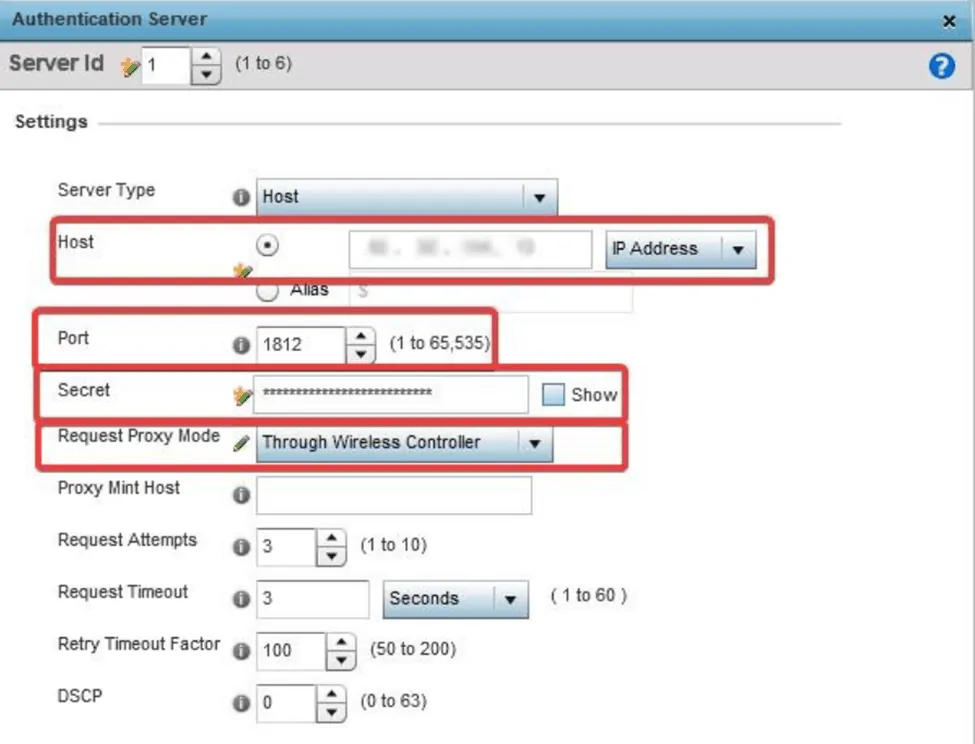
- In the Authentication Server window, update the following settings with information from the SecureW2 Management Portal under AAA Management > AAA Configuration
- Update Host with the Primary IP Address
- Update Port with the Port
- Update Secret with the Shared Secret
- Update Request Proxy Mode to Through the Wireless Controller
Configuring Captive Portal
The captive portal configuration must include a DNS whitelist of SecureW2 servers that a client is allowed to go to while still in the captive state.
- In the Extreme Networks dashboard, click Configuration > Services
- To create a new configuration, click Captive Portals > Add
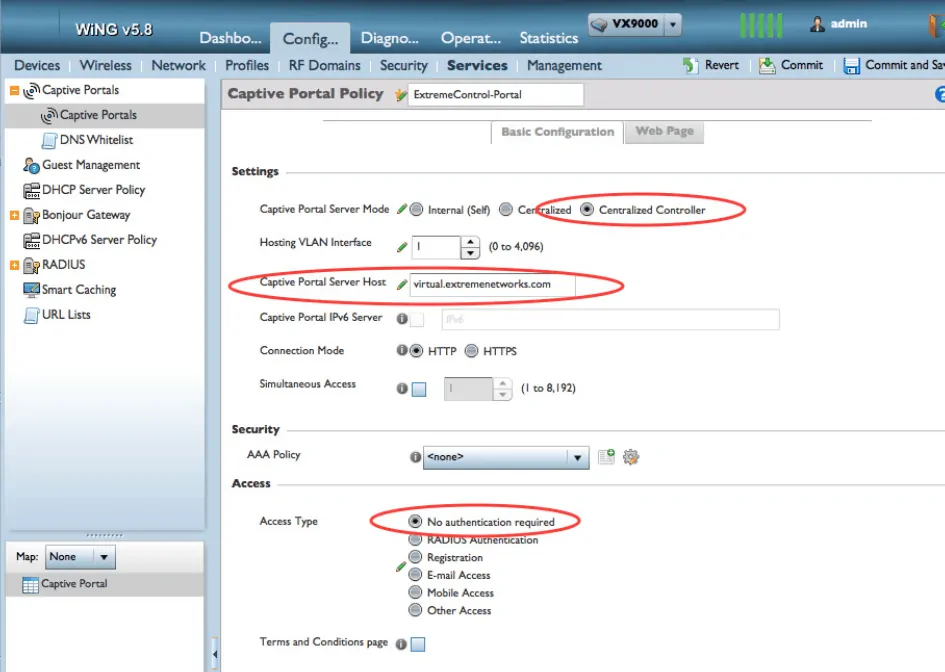
- For the Captive Portal Server Mode, select Centralized Controller
- In the Captive Portal Server Host field, specify a non-existent server host where the web request would typically sent
- In the Access field, as the Access Type, select No authentication required
- Click Ok to save the new policy
- While still in the new Captive Portal Policy, scroll down to DNS Whitelist and click Add
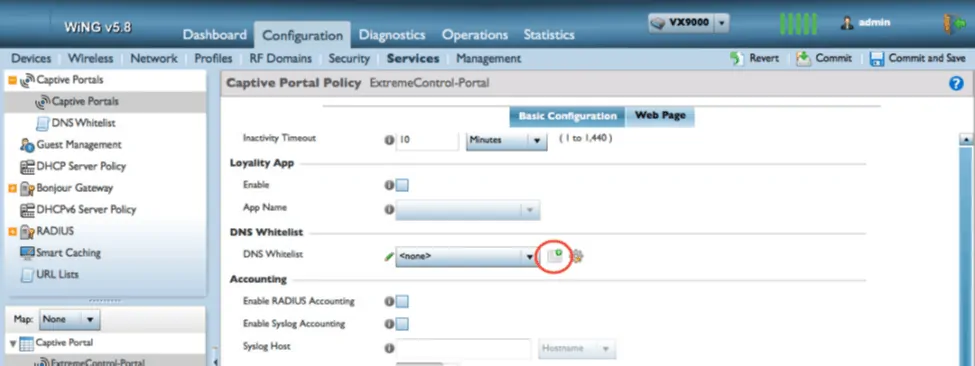
- Create entries in the DNS Whitelist for both the IP address and hostname of the SecureW2 servers used on the network
- Click Ok > Exit
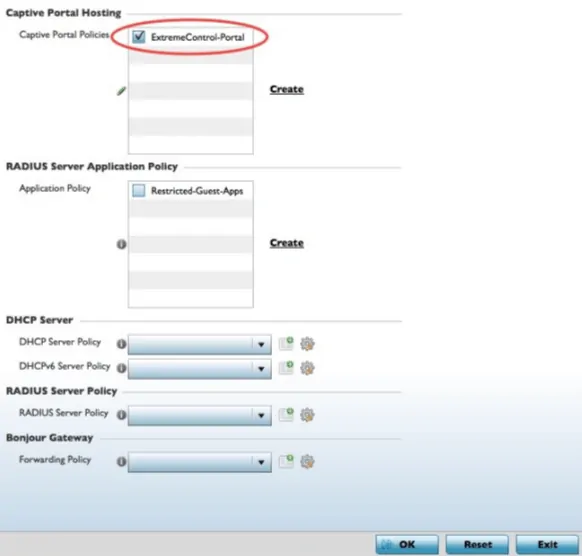
- In the Captive Portal Policy, select the newly created DNS Whitelist from the dropdown menu
- Click Ok > Commit
- The final step is to assign the new policy to the Device Profiles in use
- Navigate to Configuration > Profiles and navigate to the profile being modified
- Select the Services tab of the profile, then select the checkbox next to the new Captive Portal Policy
- Click Ok > Commit
Concluding Thoughts
A network secured with certificate-based authentication protects against all types of attacks from malicious outside users. Also, by eliminating passwords, connecting to the network is streamlined and you can say goodbye to password-expiration policies that disconnect everyone from the network. Our onboarding solution allows users to easily connect, keeps all connections secure, and puts significantly reduces the number of IT tickets related to wireless connections. So if you’d like to try out SecureW2, or have any questions about how we integrate with Extreme Networks, drop us a line! We are happy to introduce a network professional with an Extreme expert to facilitate a free trial and show how easy it can be to deploy certificate-based authentication.
ExtremeControl and Extreme Networks are either registered trademarks or trademarks of Extreme Networks in the United States and/or other countries. Other trademarks, logos, and service marks used in this site are the property of SecureW2 or other third parties.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing