Azure AD CBA is Microsoft’s tool to enable your users to authenticate to any Azure AD application using an X.509 digital certificate instead of a username and password. This allows organizations to mitigate the risk of MFA Fatigue and Credential Theft attacks while providing an improvement in end-user experience.
Once it’s properly configured, organizations can then create policies in Microsoft Defender for Cloud Apps, so users are prompted by their browser to present a certificate in order to access an application. This provides the foundation to apply zero-trust principles for Azure SSO and Application Access.
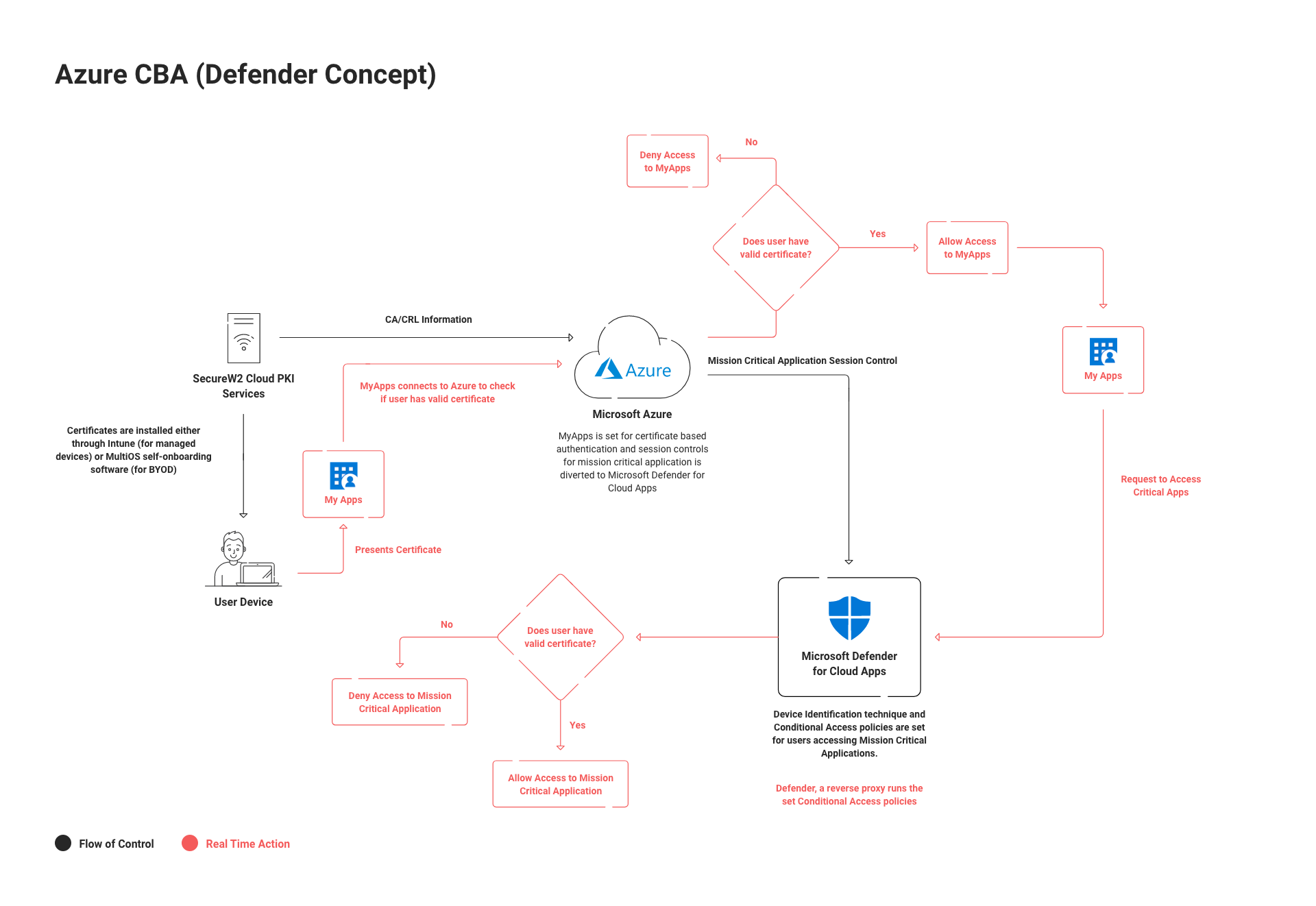
SecureW2 provides a turnkey cloud platform for issuing and managing certificates, that works natively with Microsoft environments. Organizations can integrate any MDM (such as Intune) to automate the issuance and management of certificates to Managed Devices. SecureW2 also provides a self-service Certificate enrollment client that can authenticate users using an SSO with any modern Cloud Identity Provider.
In this document, we will walk through how to configure Azure CBA for passwordless SSO, and how to set up certificate-based application access policies in Microsoft Defender for Cloud Apps.
Prerequisites
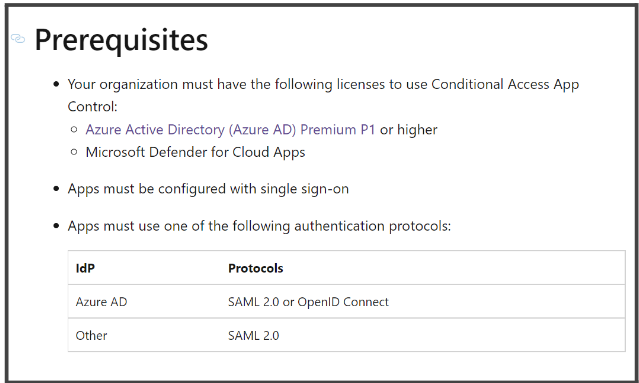
To set up certificate-based authentication using Azure conditional access, the following license privileges and conditions are necessary:
- Global Admin or Security Admin access in Azure portal.
- Azure P1 license in Azure Active directory.
- M365 E5 or EMS E5 license to access Microsoft Defender for Cloud Apps.
- The cloud application to be allowed access to must be configured with a single sign-on. They must use one of the following as authenticating protocol:
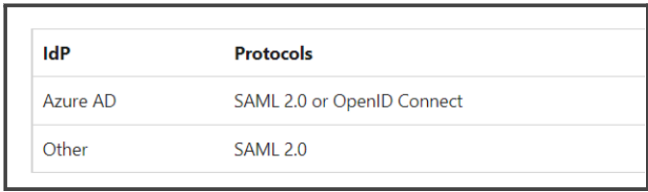
- It is recommended to have the applications in My Apps for a level up security.
High-level Methodology:
The following are the high-level methodologies/steps to set up Azure certificate-based conditional access for your applications:
- Configure Certificate-Based Authentication (CBA) in Azure Authentication Methods.
- Create a Conditional Access policy in Azure with the applications and users/groups for which we want to secure with certificates.
- Setup CBA in Microsoft Defender for Cloud Apps.
- Set Device Identification Policy as certificates and upload a Certificate Authority
- Connect the applications that are sensitive and need certificates to decide for access
- In Conditional Access Policy – create relevant access policies
- Now the application is ready to be used in certificate authentication mode.
Set up Certificate-Based Authentication in Azure
Azure AD CBA allows organizations to adopt passwordless SSO. This helps reduce the risk of Phishing and MFA Fatigue attacks. The following are the high-level steps you will need to cover to set up Azure AD CBA:
- Exporting and/or Creating a SecureW2 Certificate Authority
- Uploading your CAs (both Root and Intermediate) and CRL to Azure
- Creating a CBA Authentication Policy in Azure
- Issuing client certificates to Users and Devices.
To learn more about Azure CBA, and how to configure it, read the article we worked on here.
Set up MyApps
MyApps is a Microsoft web-based portal that is used for managing and launching enterprise applications in Azure Active Directory. It is separate from the Azure portal and is where users will go when they want to access their work applications. In this document, we will detail how to create policies that will require users to present a certificate to access certain applications in their MyApps. Below is the browser prompt triggered by our policy.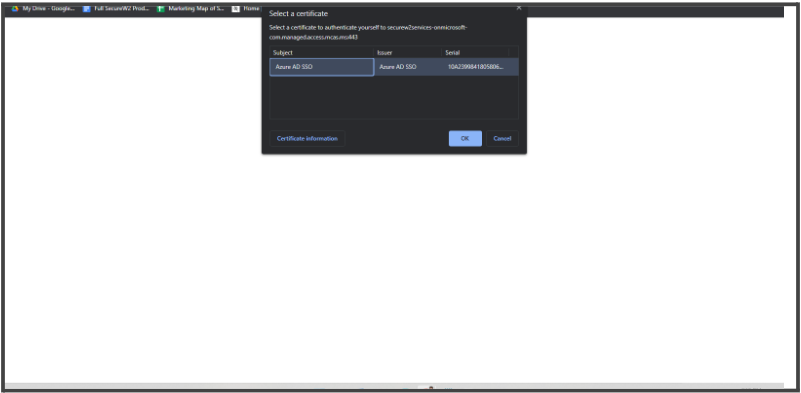
For more information on MyApps and ways of implementing it in your environment check out the below link
https://learn.microsoft.com/en-us/azure/active-directory/manage-apps/myapps-overview
Setting up Conditional Access Policy in Azure AD (Microsoft Entra ID)
Azure’s Conditional Access Policy in simple terms are if-then statements. These policies form a base for identity driven control plane. Here, we’re creating a policy that says if a set of users try to access an application, then, move its session control to Microsoft Defender for Cloud Apps.
To set up a conditional access policy in Azure AD:
- Log in to your Microsoft Azure tenant as a Global/Security Admin.
- In the search box, type “Azure AD Conditional Access” and select it or navigate via Azure Active Directory > Security > Conditional Access.
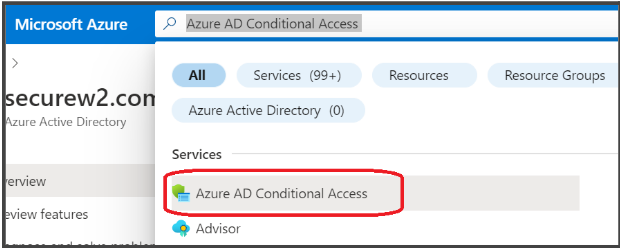
- Click on New Policy.
- In the Name field, enter a name suitable to the conditional policy being created.
- Under Assignments, click on Users or workload identities. In the widget that opens to the right, under What does this policy apply to? select Users and groups in the drop down option.
- Toggle the Include tab, check the Users and groups check-box and click on desired users to be included in the application. In case you want to exclude users, toggle to the Exclude tab and select the Users and Groups to be excluded.
- Under Cloud apps or actions > Select what this policy applies to drop-down, select Cloud apps.
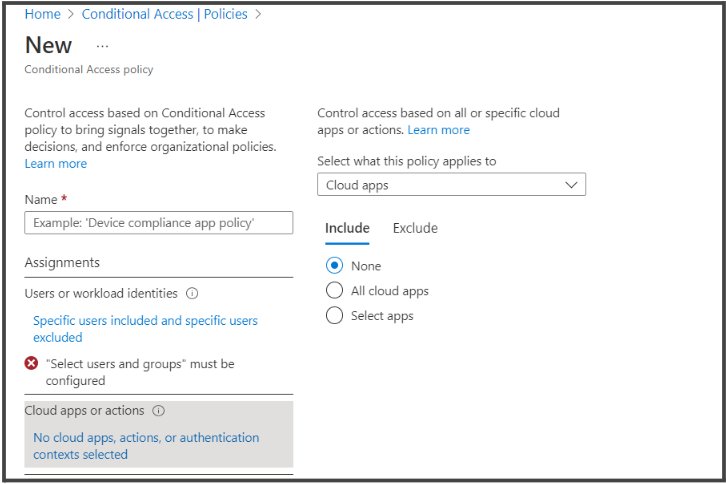
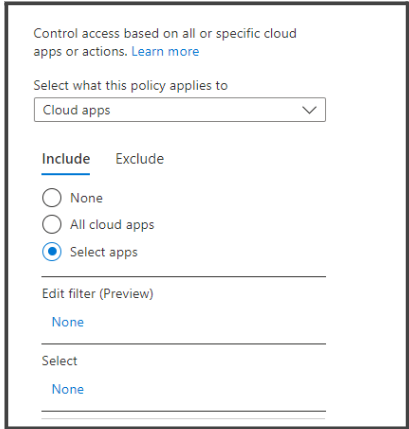
- In the widget that opens to the right, toggle to Include tab, check the Select apps option and click on the required cloud app which you want the conditional policy to be applied on. Please check that the application is already set for SSO capability, if not make use of this article here.
- Under Access Controls > Sessions, click on Use Conditional Access App Control
- On the Session widget opening on the right side, check the Use Conditional Access App Control check-box. From the drop-down below, select Use custom policy.
- Enable the Policy by toggling to On.
- Click Save.
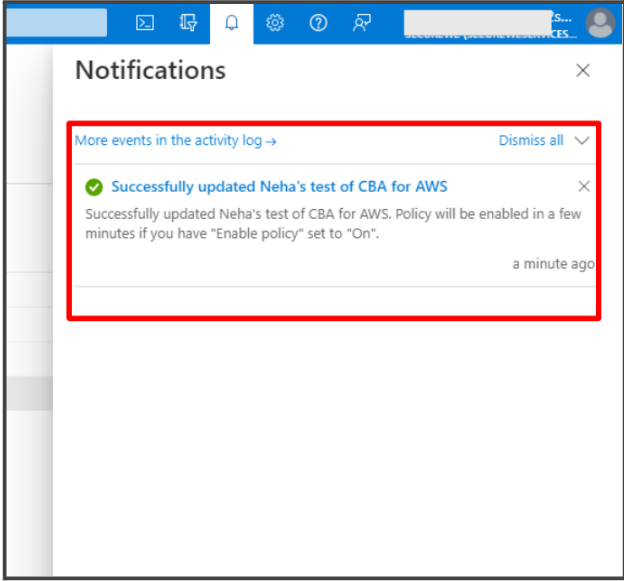
NOTE: Though not always the case always, Microsoft cautions that Conditional access policies might take about 24 hours for activation.
https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/concept-continuous-access-evaluation
Configuring Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is a CASB(Cloud Access Security Broker) solution where you can create security policies, monitor threats and set a baseline for compliance for a Cloud environment. In our use case, we are using Azure’s Conditional Access policy to direct the Session control of an Azure Application to Defender for Cloud Apps. Here, Defender for Cloud Apps behaves as a reverse proxy, user requests and responses go through Defender for Cloud Apps rather than directly to the app.
In Microsoft Defender for Cloud Apps, we will upload the Certificate Authority that we will use to issue the client certificates, our users will need to access their applications. Then in the next section, we will create policies for our applications requiring certificates to access them. This creates
- Log into Microsoft Defender for Cloud Apps portal.
- Click on the Gear Icon on the Top-Menu bar and click Settings.
- Select Device Identification from the side-widget that appears on your left.
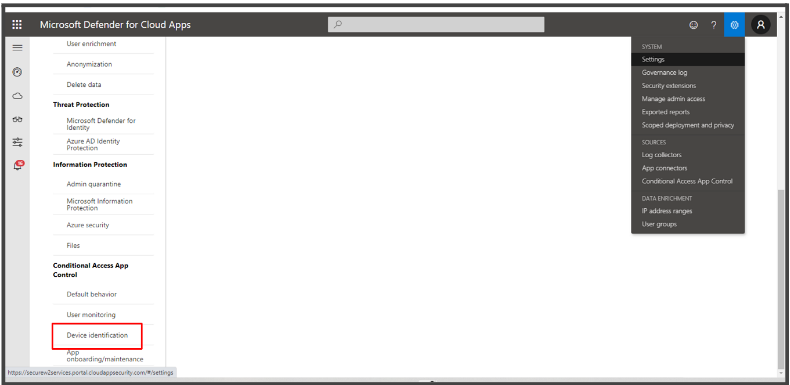
- In the Device Identification page, click on Add a root certificate.
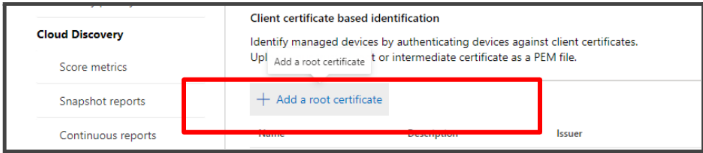
- To obtain the root certificate, log in to SecureW2’s JoinNow MultiOS Management Portal and navigate to PKI > Certificate Authorities. Select the root certificate you want to upload in Microsoft Defender for Cloud Apps and click Download. Make sure that the certificate format is PEM.
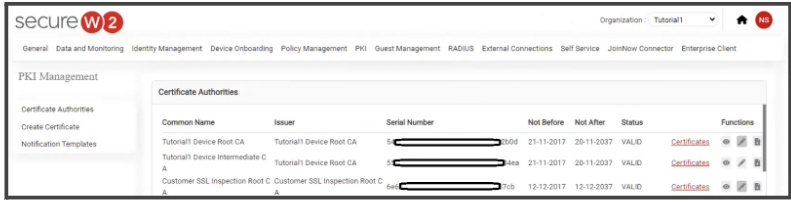
- Choose the downloaded certificate from your local and upload it on the Microsoft Defender for Cloud Apps.

- Go to Connected Apps to check if the app you set in Azure Conditional Access reflects here. This will happen only when a user configured in the policy signs in at least once with their credentials and the below prerequisites are matched.
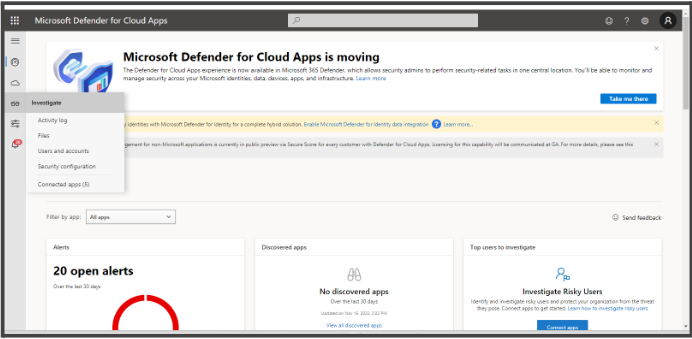
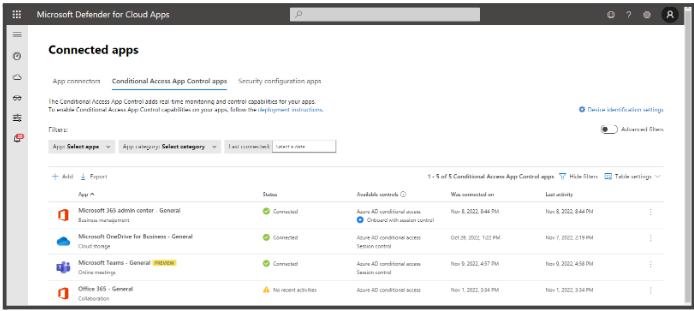
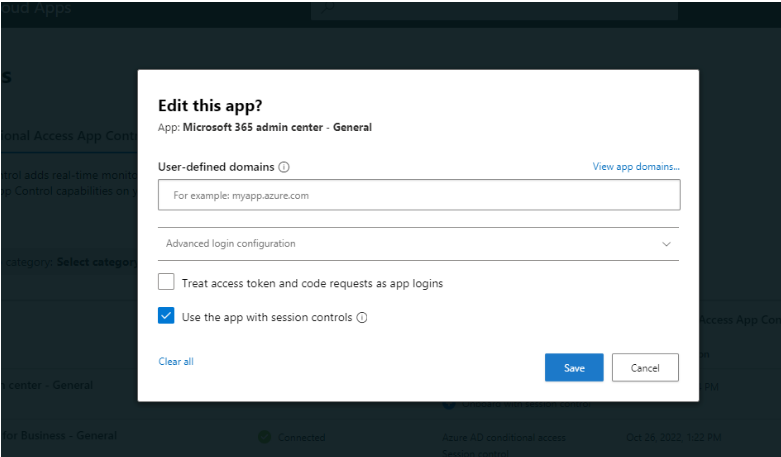
- Click the small + icon below the ‘Azure AD Conditional Access’ and set the ‘Onboarding with Session Control’.
- Click only ‘Use the apps with session control’ and Save the setting.
Create Access Policy In Microsoft Defender for Cloud Apps
To create a Access policy in Microsoft Defender for Cloud Apps:
- Under Controls, click Policies.
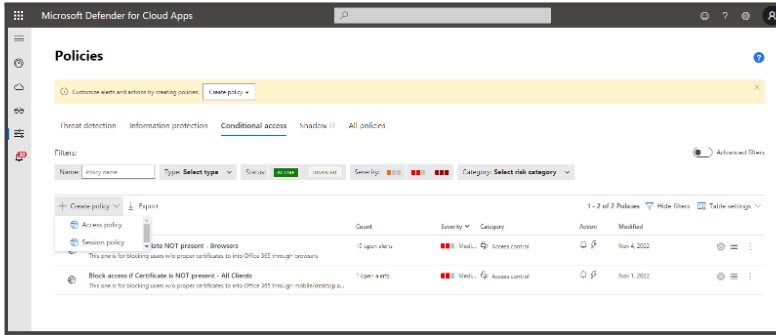
- Click on the Conditional access tab.
- Click on Create Policy and select Access Policy.
- In the Create access policy page, in the Policy Name field, enter a suitable name for your policy.
- In the Policy severity select the severity level of your policy.
- In the Description field, enter a description for your policy.
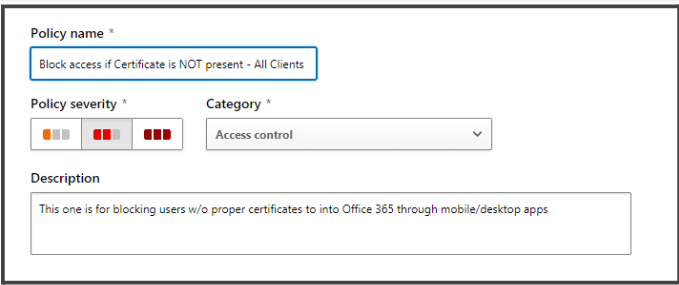
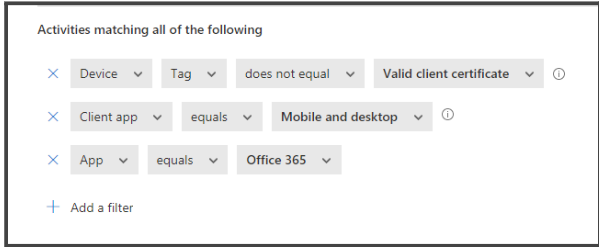
- In the Activities matching all of the following field, set up the filters as shown in the below image:NOTE: This will block a user from accessing a sensitive application in its mobile/desktop version without a valid certificate. We have taken Office 365 as an example for a sensitive application in this case.
 You can also follow the same method as mentioned in step 7 to create BLOCK policies for Browser version of the application. Example is given below:
You can also follow the same method as mentioned in step 7 to create BLOCK policies for Browser version of the application. Example is given below: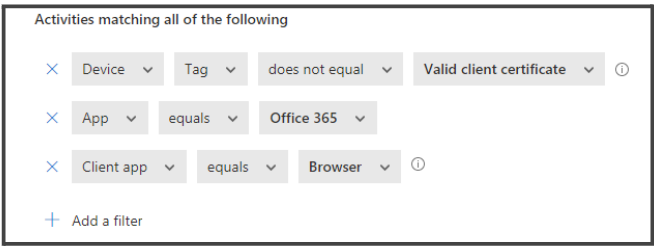
- Under Actions, check the Block radio button. You can also create a custom block message. Check the Customize block message box and enter your message in the field provided below.
- Check the box under the Alerts section to receive an alert for each matching event. You may further customize the settings according to your needs.
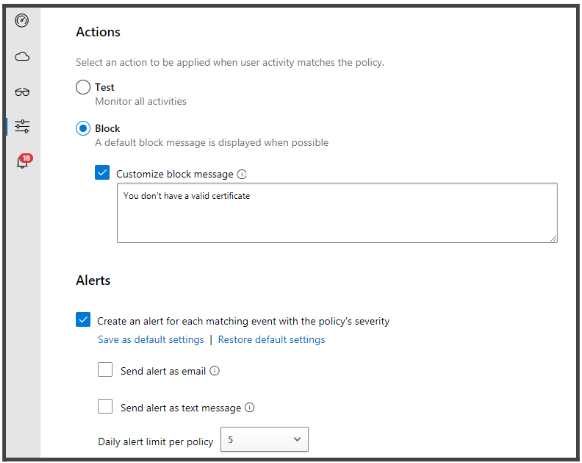
- Click Create.
A policy to block a user from accessing a sensitive application in its mobile/desktop version without a valid certificate is created.
FAQs
No. Binding a certain Root/Intermediate CA to a certain conditional access policy, hence to a certain application is NOT possible from the articles published by Microsoft. This was also confirmed by us with Microsoft Support.
Being a product limitation, we have to live with this until Microsoft comes with a work around.
We suggest that you use certificates from only one CA for all of your sensitive applications, i.e. as a best practice make sure that the users who need access to your mission critical applications are provided by with only certificates from a single CA, which also make management of your Privileged Accounts easier.
We'd also advice that you make a mindful decision of listing down what your mission critical applications are so that they get all the benefits of a layered certificate authentication. This is to ensure that NOT everyone gets certificates from the same CA, which if happens would give rise to a privileged escalation situation enabling non-essential users getting access to critical applications.
Yes. The same certificate could be used.
As a matter of fact, we recommend you do this for maintaining a tight application access control while using certificates, as Microsoft Defender does NOT validate the attributes in client certificates Authentication. This is in contrast to Azure CBA which is used to authenticate to MyApps. While setting up Azure CBA, one provides user name binding information against the certificate, this mechanism validates that the client certificate being produced while signing into MyApps belong to that user or not.
If you're using multiple certificates for others authentication purposes, be sure to select the right one when the browser/application prompts you.
No, it cannot. In Fact, we have tested multiple times, and we're able to login with one user account, and use a client certificate issued to another user. With Azure CBA, you can specify which attribute you want to lookup to verify a user, and which SAN field the attribute will be in.
With Microsoft Defender, no such lookup capability exists. It only verifies the certificate is valid, and belong to the uploaded CA.
Note on licensing requirements
Global Admin or Security Admin Access in Azure portal to set up conditional access policies in Azure and Defender for Cloud Apps.
Azure P1 license in Azure Active Directory - each user to whom conditional access policy must be applied to. Ref: Microsoft Q&A community forum
Microsoft Defender for Cloud Apps can be licensed as a standalone product or as part of several different licensing plans3
M365 E5 or EMS E5 license to access Microsoft Defender for Cloud Apps.