Active Directory Federation Service (ADFS) is a Microsoft software element that can run on Windows server operating systems and offers single-sign-on (SSO) access to some web applications that aren’t able to use Integrated Windows Authentication (IWA). ADFS was developed to offer a flexible service that allows organizations to control employee access and improve the user experience by allowing access to multiple applications through SSO with user credentials and approved third-party systems.
For SAML (Security Assertion Markup Language) Authentication, JoinNow MultiOS plays an essential role in designing the self-service certificate-based authentication (EAP-TLS) for any user, allowing organizations to support passwordless security through our PKI by providing digital certificates efficiently.
JoinNow MultiOS can integrate with modern cloud-based SAML IDPs to issue and configure their certificates to the devices for Extensible Authentication Protocol (EAP-TLS) network access for Wi-Fi Authentication. This document will show you how to configure SAML Authentication for WPA2- Enterprise with Active Directory Federation Services.
Using EAP-TLS & SAML Authentication:
EAP-TLS or PEAP( Protected Extensible Authentication Protocol) is an authentication protocol commonly deployed on WPA-2 Enterprise networks that often enables the use of digital certificates instead of passwords for network authentication. However, organizations need a Public Key Infrastructure (PKI) to deploy and manage those digital certificates. While some organizations may choose to deploy their own PKI, a managed PKI service such as SecureW2’s is often more manageable. A managed PKI helps generate public-private key pairs used by Identity Management and Access Control for Network Authentication.
PKIs have some great advantages, like providing secure certificate-based authentication for many platforms. One challenge to PKIs is getting certificates to endpoints, especially unmanaged devices and BYODs. Our JoinNow MultiOS can tie with any SAML IDP to configure unmanaged devices for certificates. SAML is often used during the BYOD enrollment process to verify a user’s identity in the IDP when they enroll for a certificate.
To complete this process, we’ve summarized it to the following overview:
- Download the Metadata from ADFS
- Configure ADFS for SAML Authentication in the Microsoft Management Console
- Configure the Attribute Mapping in ADFS and SecureW2
- Configure the WPA2-Enterprise Network Policy Rules
Prerequisites
To configure SAML authentication with ADFS, make sure you meet the following prerequisites:
- An active SecureW2 account
- An active Cloud Connector subscription
- JoinNow MultiOS Server
Note: The ADFS server must be publicly accessible and signed by a public CA certificate. Also, the metadata from the ADFS server is required to add trust with the SecureW2 servers.
Download The ADFS Metadata
- Access the ADFS server through your ADFS URL and Download and Save the ADFS Metadata
- From your SecureW2 Management Portal, go to Integration Hub > Core Platforms
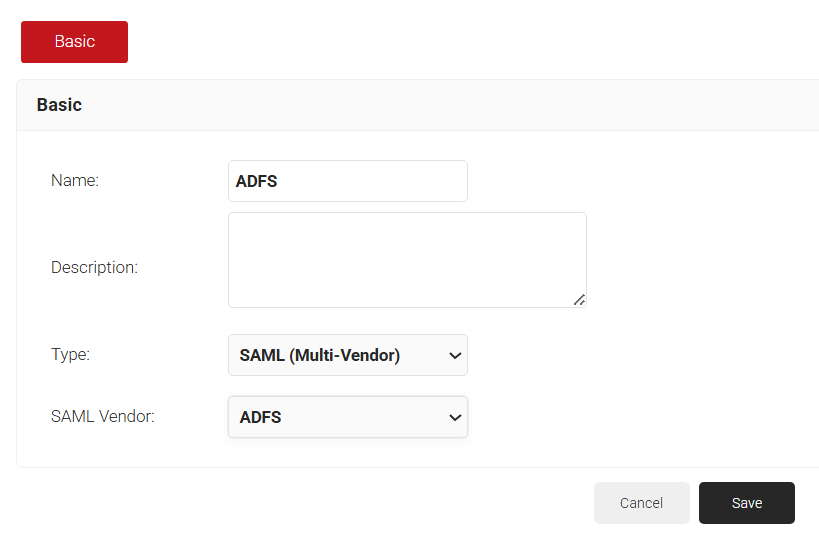
- Enter a Name and Description for the ADFS platform in JoinNow.
- From the Type drop-down list, set the Type to SAML (Multi Vendor), and choose SAML Vendor as ADFS,
- Click Save.
- In the Identity Providers list that appears, click Edit on your newly created IDP
- Select the Configuration tab
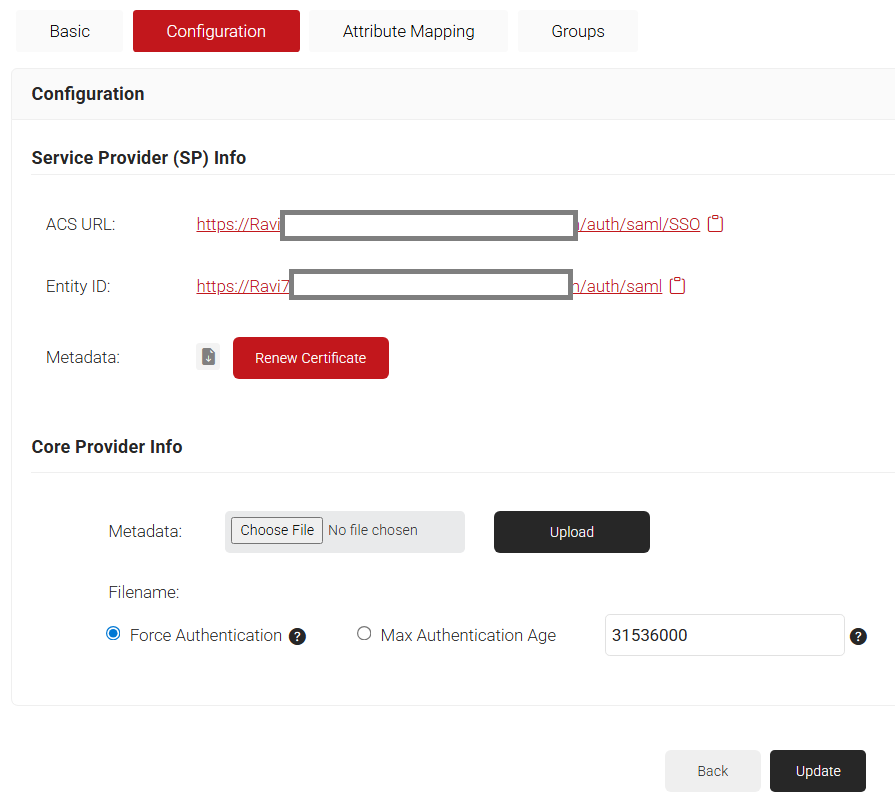
- Under Identity Provider (IDP) Info, click Browse… in the Metadata section and Open the Metadata downloaded previously, and click Upload and Update
- Under Service Provider (SP) Info, the URLs for Configuring Azure Directory are provided. Configure the URLs in the Azure portal to obtain the metadata file.
- Click Choose File to navigate to the file. Choose the file and click Upload.
- Click Update.
Configure ADFS For Security Assertion Markup Language (SAML) Authentication
SAML is a secure authentication protocol often used to enable single sign-on to access multiple applications. It is also used to enroll unmanaged devices/BYODs for certificates that users navigate to our onboarding landing page and enter their credentials, and through the SAML authentication process, we verify who they are in the IDP before issuing them a certificate.
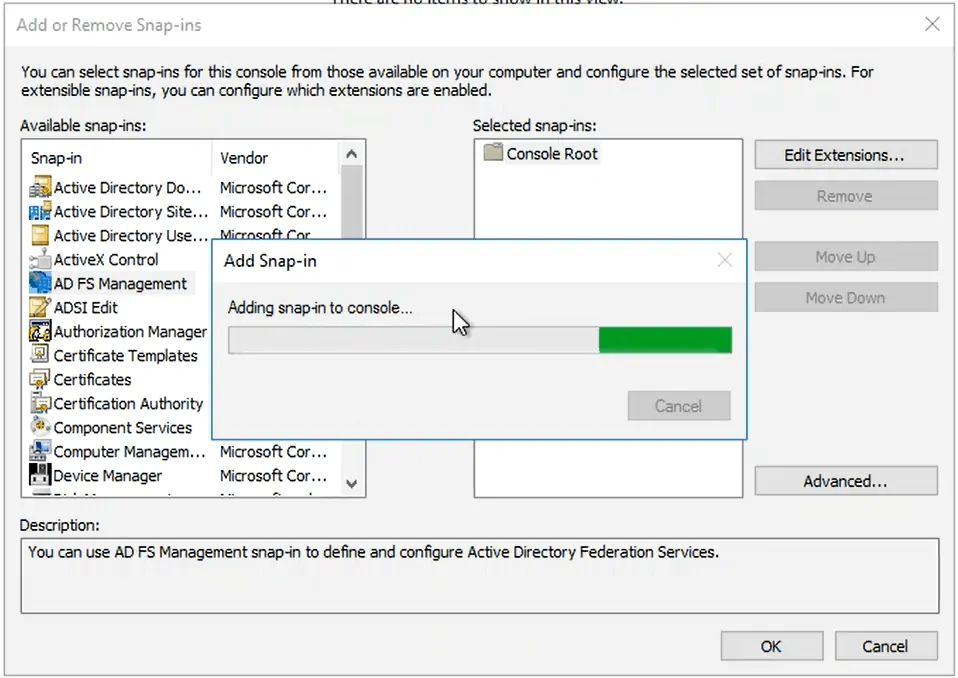
- Run the mmc command to open the Microsoft Management Console
- Click File > Add/Remove Snap-in
- Add the ADFS Management to the Selected snap-ins: and click Ok
- Select the main node ADFS, and in the left pane click Relying Party Trust
- In the right pane under Actions, select Add Relying Party Trust
- Using the Add Relying Party Trust Wizard that appears, click Start (with the Claims aware bubble selected)
- Select Import data about the relying party from a file and click Browse to find and select the previously downloaded metadata, then click Next
- Enter a Display name and click Next
- Under Choose an access control policy, select whether to use a user blacklist or whitelist click Next, and click Next again on the next screen
- Note: If you choose whitelist (Deny all users), you will need to grant access to users/groups at a later time
- To finish, click Close
Configure ADFS Attribute Rules
- Right-click the Relying Party Trust you created and select Edit Claim Issuance Policy
- In the window that appears, click Add Rule
- Ensure the Claim rule template is set to Send LDAP Attributes as Claims and click Next
- Enter a Claim rule name and change the Attribute store to Active Directory
- Configure LDAP to SAML attribute mapping based on your use case and click Finish > Apply > Ok
- This will include the different attribute fields that will be populated with the IDP metadata
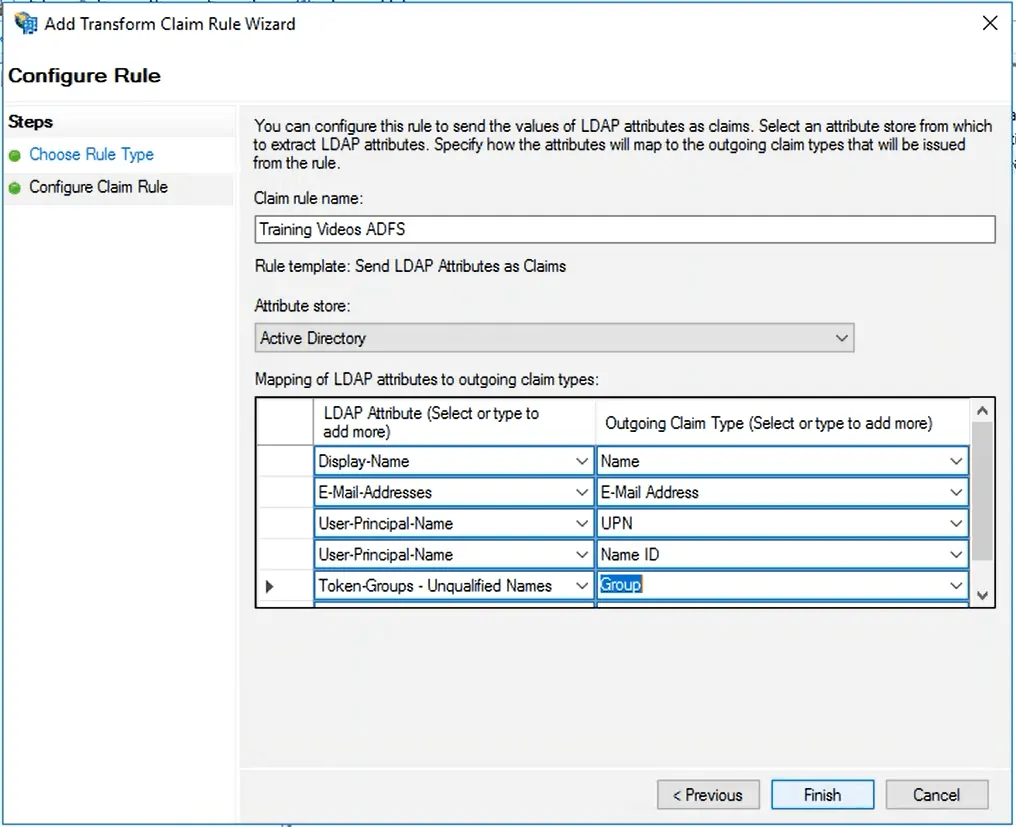
- This will include the different attribute fields that will be populated with the IDP metadata
- Right-click the relying party trust you created, and click Properties
- Select the Advanced tab and in the Secure hash algorithm dropdown, select SHA-1 and click Apply > Ok
- Before beginning the next section, right-click the Relying Party Trust that was previously created and select Edit Claim Issuance Policy
- Select the newly created Rule and click Edit Rule
- Click View Rule Language… to read the attributes you created
- You will make use of these in the SecureW2 Management Portal
Configure Attribute Mapping in SecureW2 with Active Directory Federation services:
Attribute Mapping can regulate the attributes that pass from the IDP to the SAML Application and authenticate directly with SecureW2. Here, these attributes help grant access to the user accounts, as attributes are encoded onto certificates for the user.
To enable SAML Authentication, you need to configure the attribute mapping in Federation Server and in the SecureW2 Management Portal.
There are a few steps to be followed for mapping the attributes that SecureW2 receives from Active Directory Federation Services (ADFS):
- Open the SecureW2 Management Portal and in the Identity Providers screen, select Edit for the ADFS IDP that was previously created
- Click the Attribute Mapping tab and click Add
- Reference the Rules you have open to create the Local and Remote attributes
- For example, an attribute based on a user’s name would read:
- Local Attribute: displayName
- Remote Attribute: USER_DEFINED
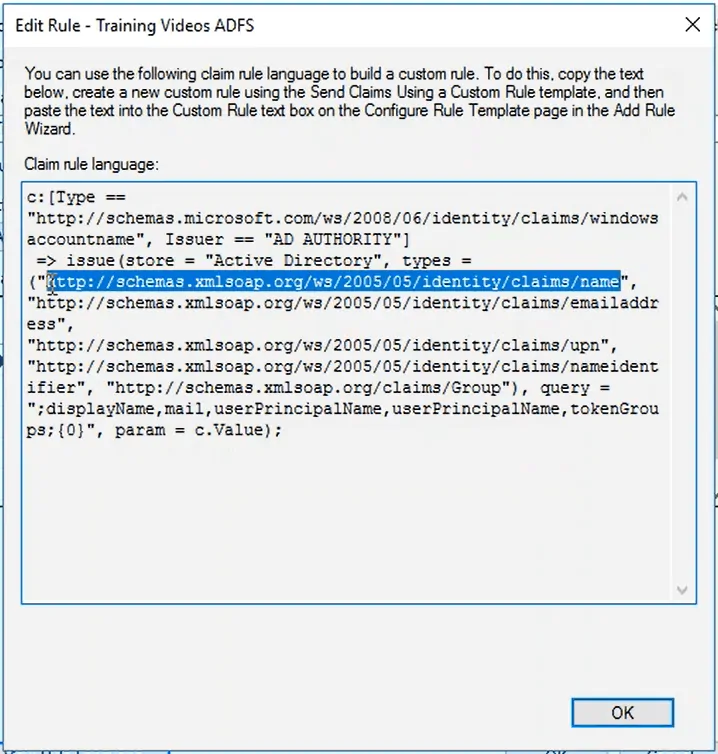
- In the new dialog box: Open the Rule Language in the Microsoft Console and copy the URL relating to the name attribute (See image below)
- Add an attribute for each Rule that was created and when finished click Update
- You can close the Rule Language window that was open in the Microsoft Console
Configure the WPA2-Enterprise Network Policies
- In the SecureW2 Management Portal under the Device Onboarding section, select Network Profiles
- Edit the network profile you have previously created by clicking Profile in the Policy Management section
- Click Add Profile Policy, enter a Name for the profile, and click Save
- Click the Conditions tab, select the profile you created in the Profile dropdown, and click Update
- Under Policy Management, select User Roles
- Click Add Role, enter a Name, and click Save
- Click the Conditions tab, select the Identity Provider you’ve created in the Identity Provider dropdown, and click Update
- Under Policy Management, click Enrollment > Edit on the DEFAULT ENROLLMENT POLICY
- Click the Conditions tab
- Select the User Role you created and the DEFAULT ROLE POLICY in the User Role dropdown (by holding CTRL to select both), and then click Update
- Whenever modifying the Profile Policy, you must Re-Publish the Network Profile after you have completed editing
- Navigate to Network Profiles under Device Onboarding and click Re-publish on the Network Profile you created, and then click Ok
Simplify EAP-TLS Through SecureW2’s Top-Rated Onboarding Technology
SecureW2 offers a seamless and completely passwordless solution that helps to prevent security risks and enhance authentication server performance. Following the steps outlined in this guide, you will have configured Certificate-Based Authentication through Active Directory Federation Services (ADFS).
With managed PKI service, we offer JoinNow MultiOS that helps BYODs quickly enroll the digital certificates by entering your valid credentials once. They are then verified in your IDP through the secure SAML protocol. For more information, click here to see our details.
Active Directory Federation Services is a registered trademark of Microsoft in the United States and/or other countries. Other trademarks, logos and service marks used in this site are the property of SecureW2 or other third parties.