Configuring Dynamic RADIUS with Azure to Support WPA2-Enterprise
Introduction
Azure customers have had a difficult time implementing a RADIUS solution because Azure is more limited than Active Directory (AD) in supporting WPA2-Enterprise and 802.1x. Luckily, SecureW2 offers a PKI solution that integrates with Entra ID. Users can use their AD credentials for 802.1x authentication, but we can take it one step further. Azure customers no longer need to be shackled to password-based authentication methods now that SecureW2 offers the first Azure passwordless solution.
SecureW2 has rolled out Dynamic RADIUS, which introduces a revolutionary way to authenticate users and enforce policies to create and strengthen a WPA2-Enterprise network. Once configured in Azure, Dynamic RADIUS can perform enhanced certificate-based authentication, runtime-level policy enforcement, and security redundancies.
This article covers how to implement Dynamic RADIUS in Azure. We also published documentation on How to Set Up Passwordless WPA2-Enterprise and Tie Azure AD to Network Security
Registering a New App
To register a new application in Azure, perform the following steps:
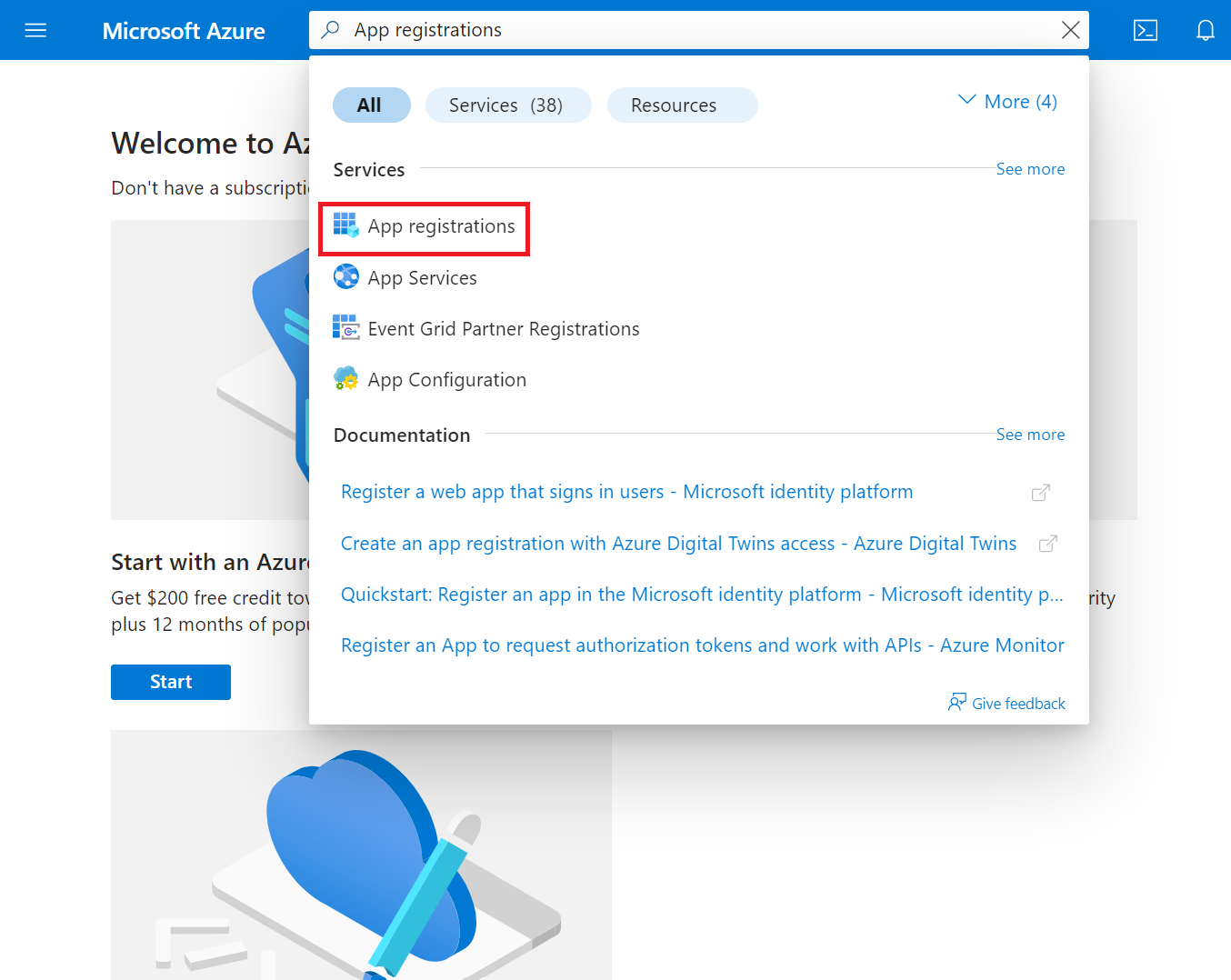
- Log in to the Microsoft Azure portal.
- Type App registrations in the search box and click App registrations.
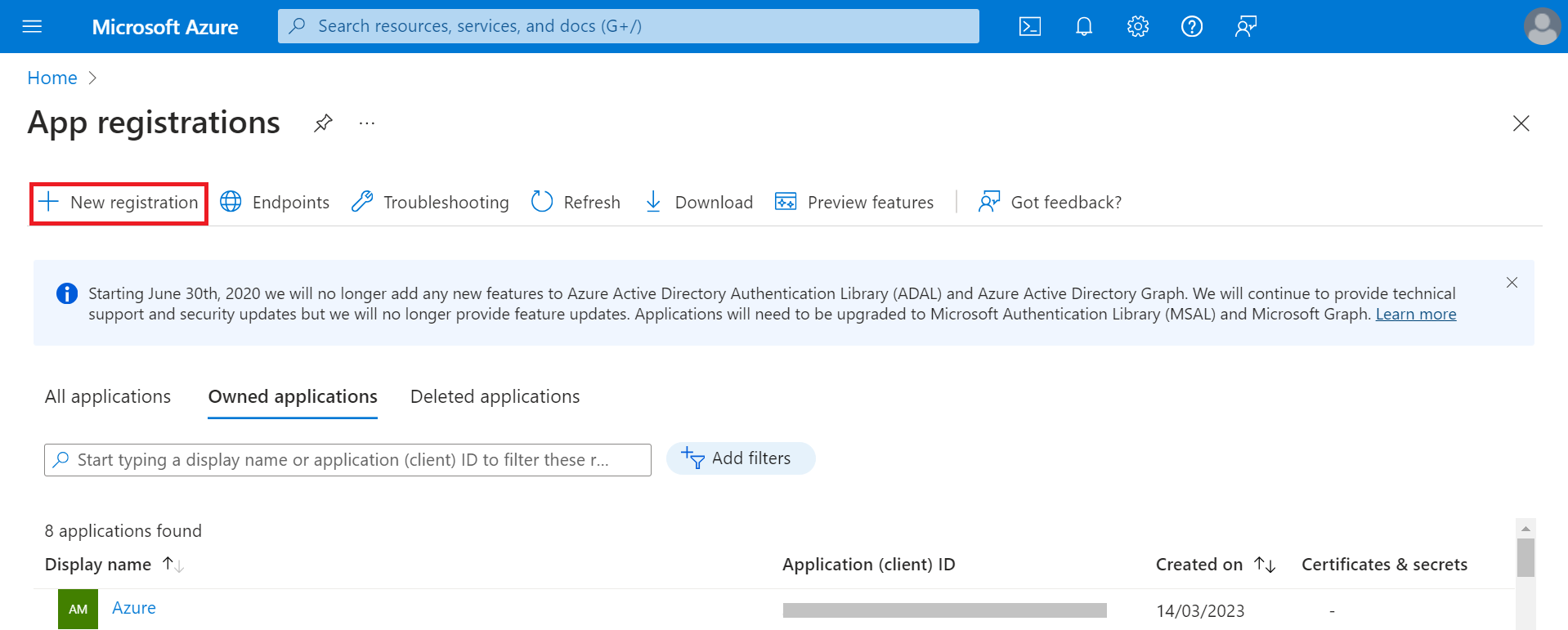
- On the App registrations page, click New registration.
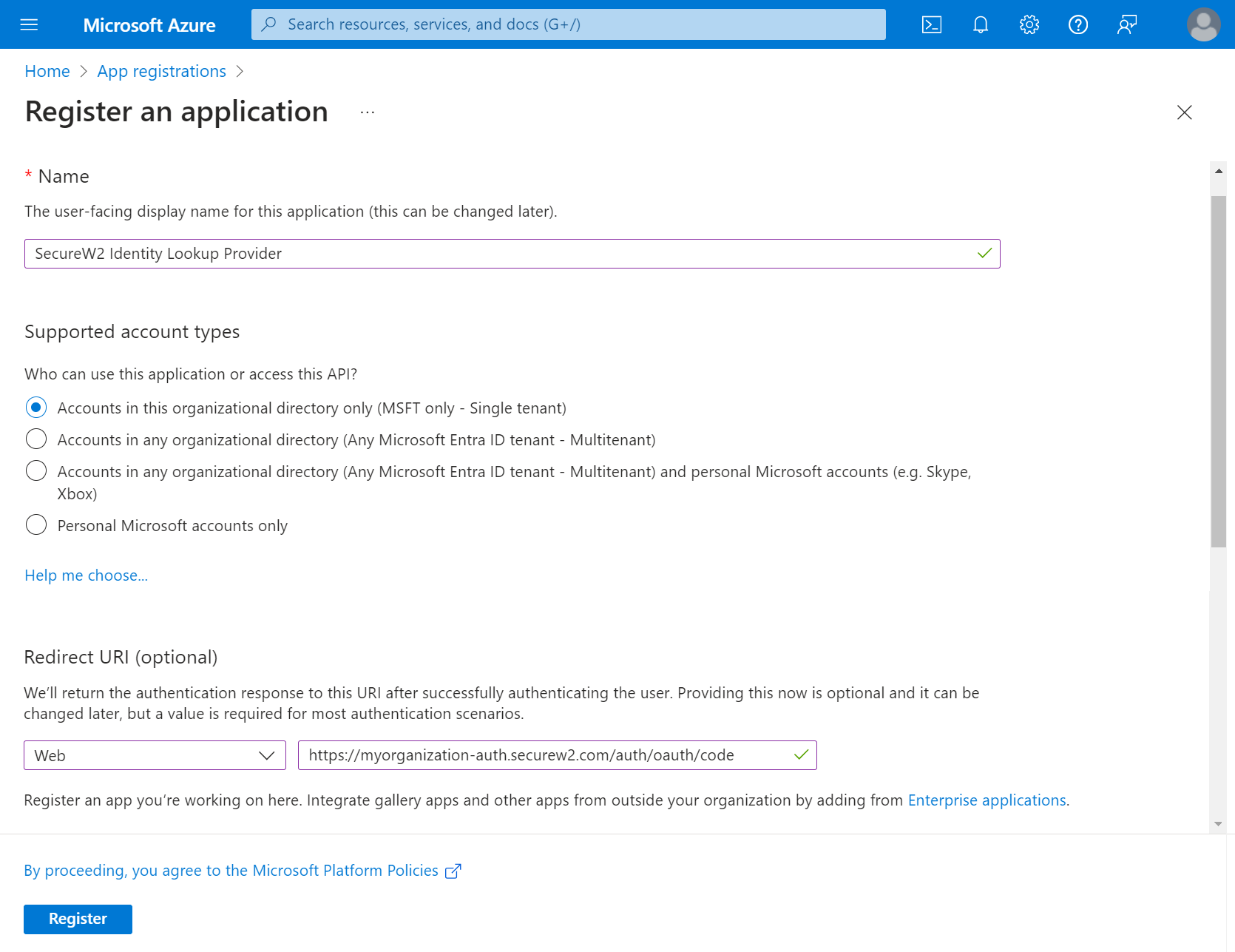
- On the Register an application page, enter the name of the application in the Name field.
- In the Supported account types section, specify who can use the application by selecting any one of the following options:
- Accounts in this organizational directory only (MSFT only – Single tenant)
- Accounts in any organizational directory (Any Microsoft Entra ID tenant– Multitenant)
- Accounts in any organizational directory (Any Microsoft Entra ID tenant– Multitenant) and personal Microsoft accounts (e.g., Skype, Xbox)
- Personal Microsoft accounts only
- In the Redirect URI (optional) section, from the Select a platform drop-down list, select Web, and in the URL field, enter a unique SecureW2 Organization URL such as https://myorganization-auth.securew2.com/auth/oauth/code
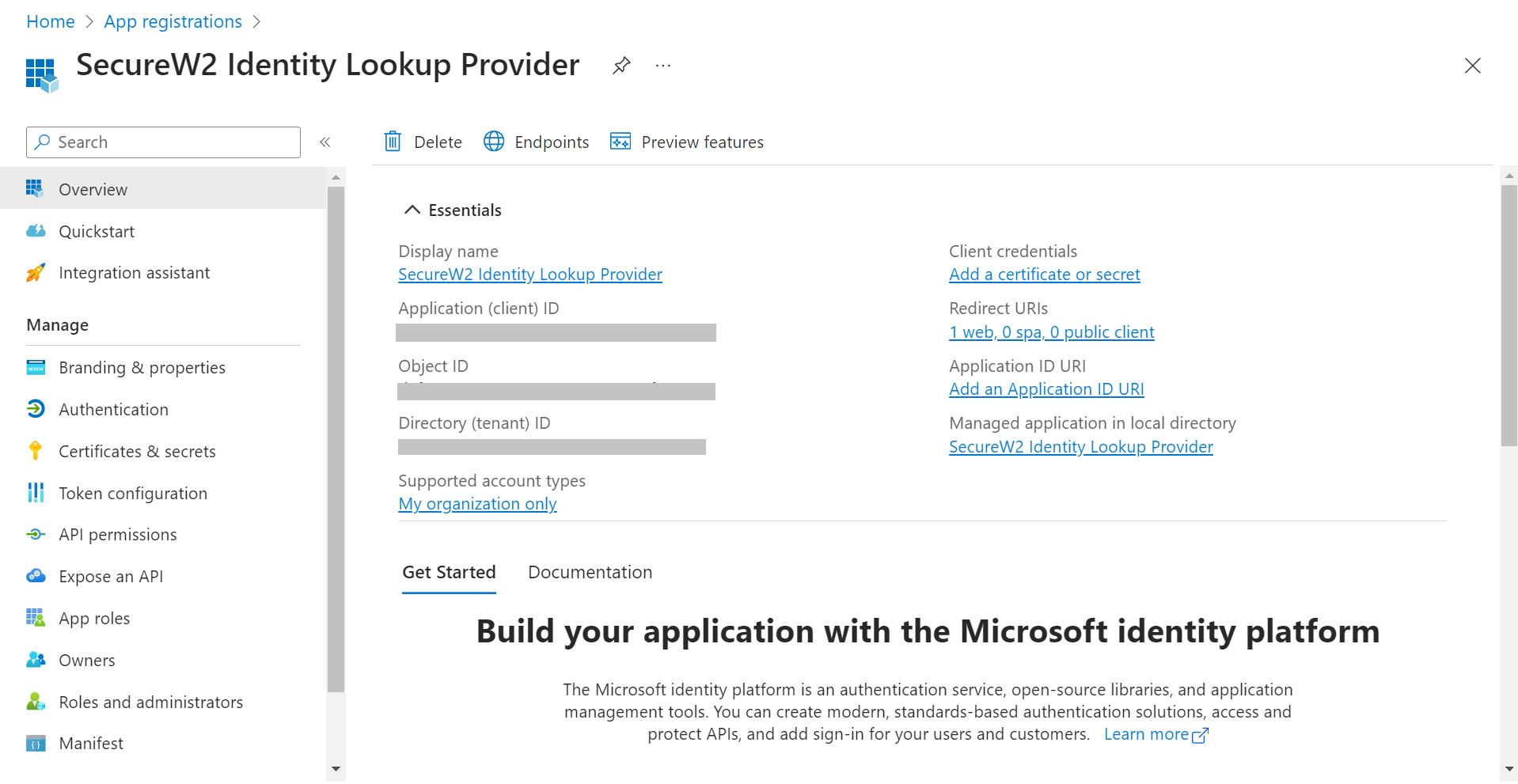
- Click Register. The following screen is displayed.
- Copy the Application (client) ID, Object ID, and Directory (tenant) ID values to your console.
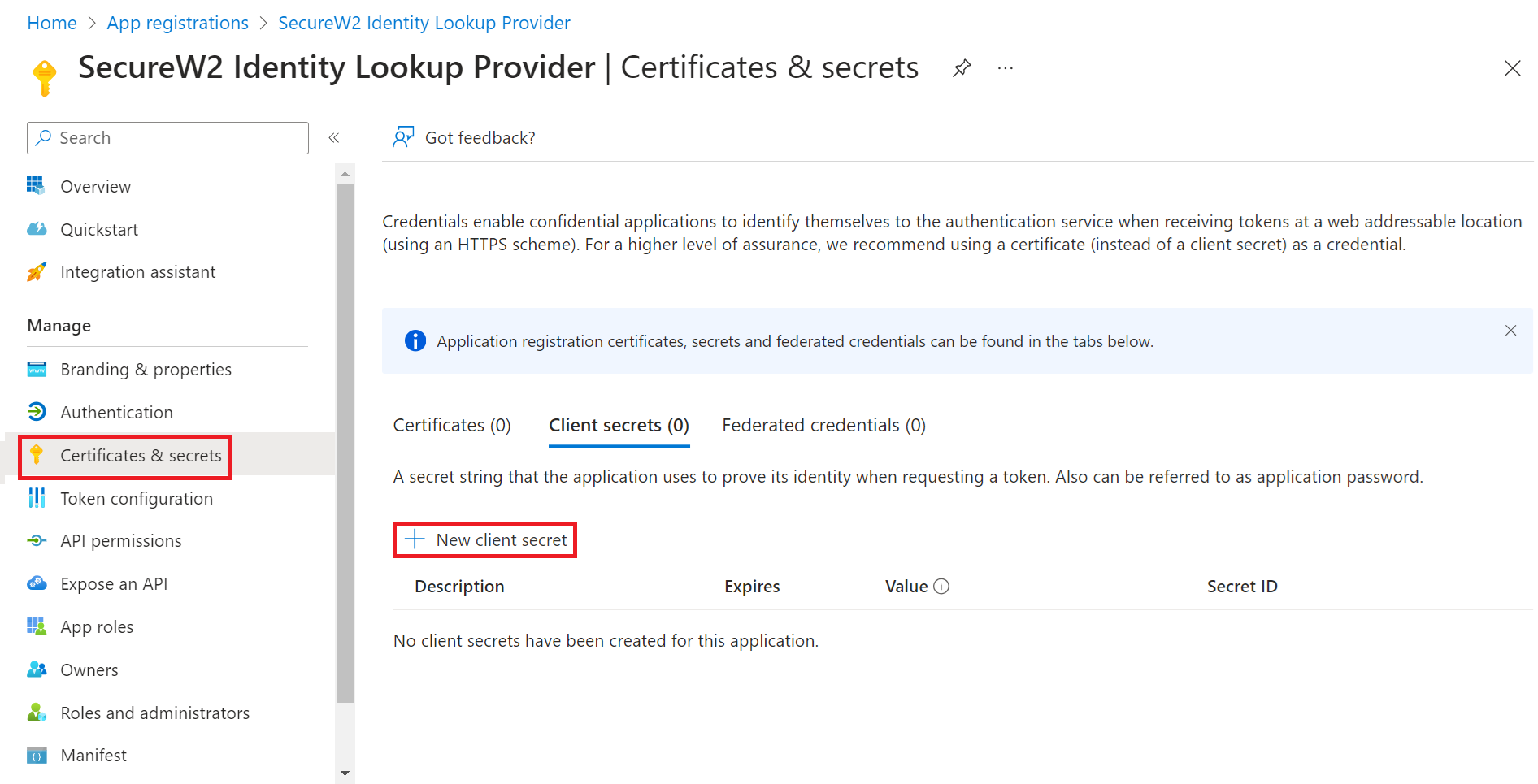
Creating a Client Secret
To create a client secret, perform the following steps:
- On the left pane, go to Manage and click Certificates & secrets.
- Click New client secret.
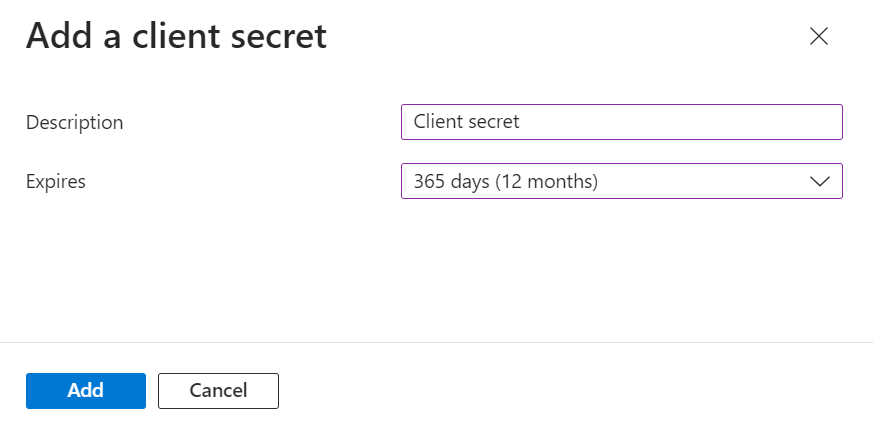
- In the Add a client secret pop-up window, enter a description for the client secret in the Description field.
- From the Expires drop-down list, select the expiration date of the client secret.
- Click Add.
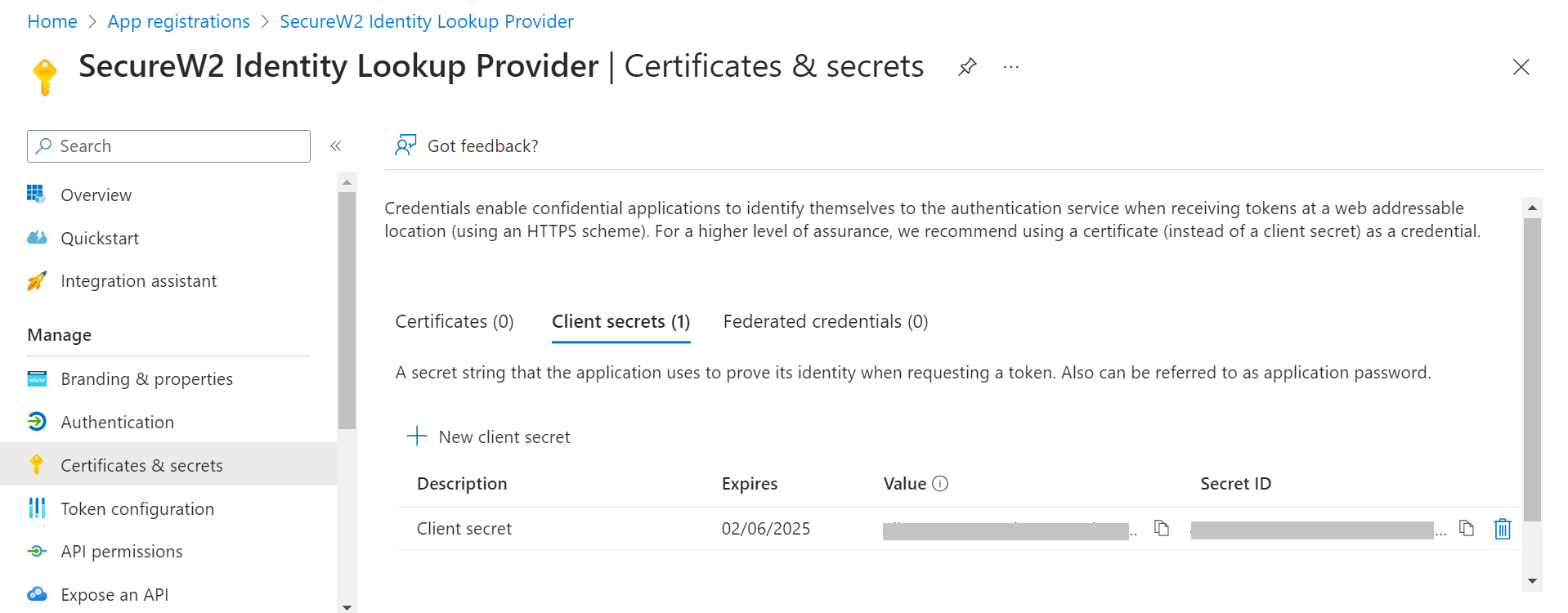
- The client’s secret is displayed under the Value column.
NOTE: Ensure that you save the client secret on your console properly, as this secret is non-recoverable.
Creating a Provider URL and Client ID
To create a provider URL and client ID, perform the following steps:
- Navigate to the Overview section.
- Copy the Application (client) ID and Directory (tenant) ID values to your console.
- Insert it into the following URL: https://login.microsoftonline.com/{Directory (tenant) ID}. This should look like this: https://login.microsoftonline.com/561bc66f-1d86-4244-8bc4-5eb12cba45ac
- Save this for later.
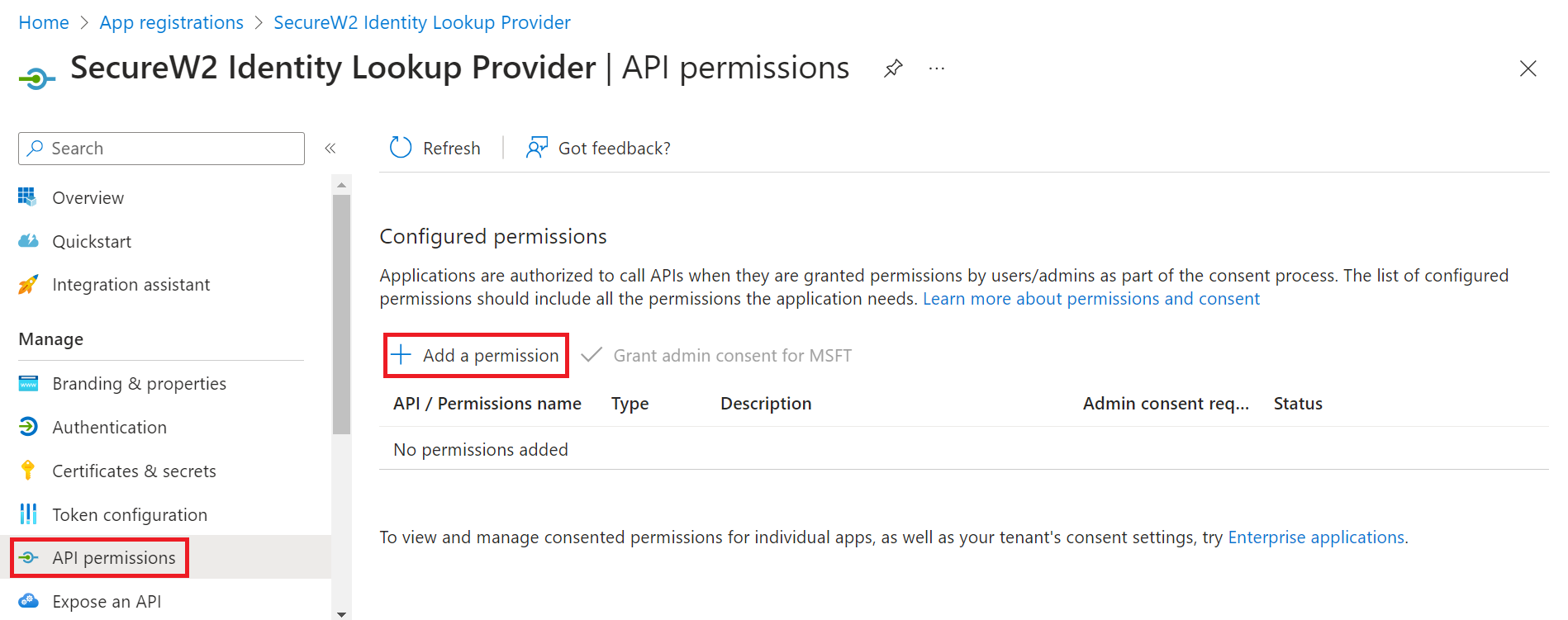
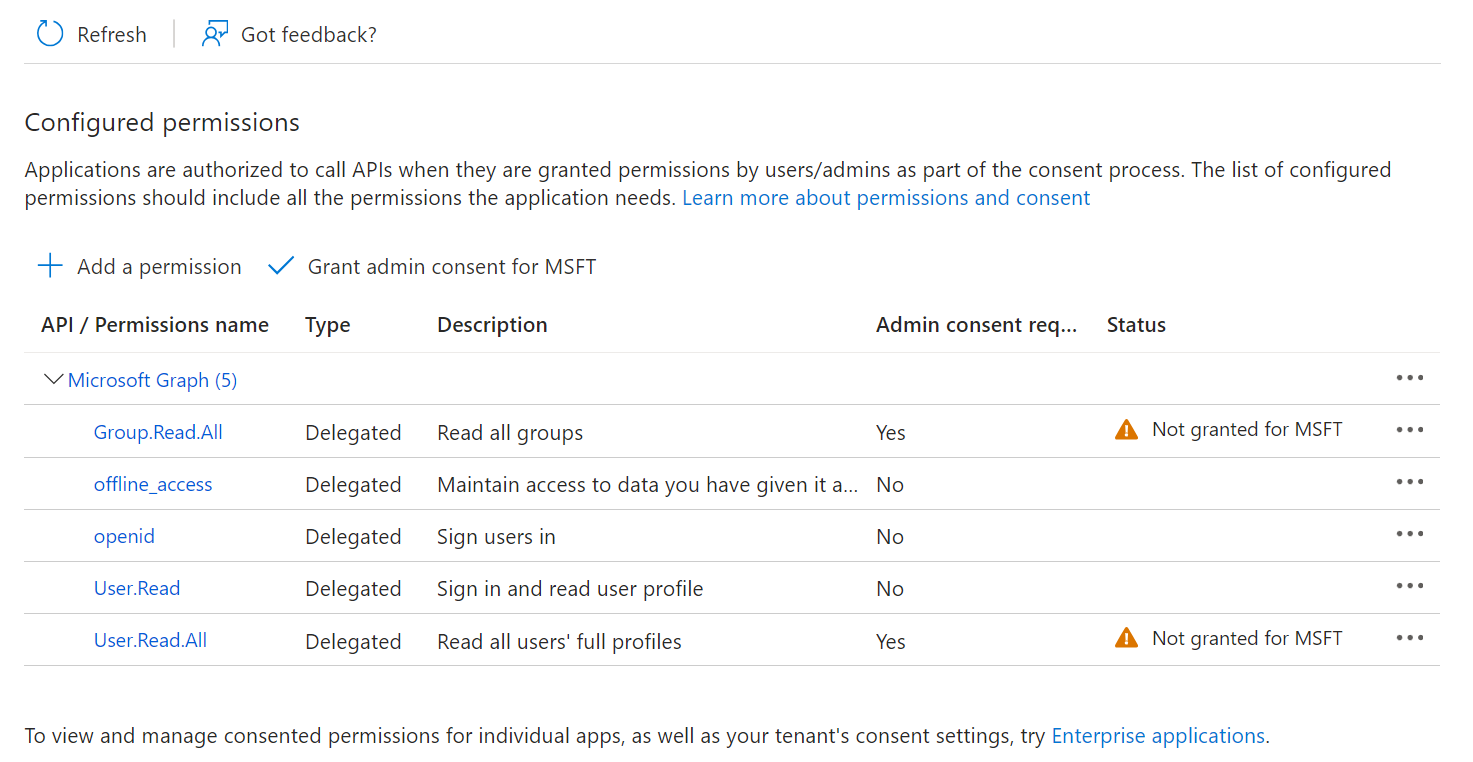
Providing API Permissions
Finally, provide this application permission to access the data in our Entra ID.
- On the left pane, go to Manage and click API permissions.
- Click Add a permission.
- After adding the permissions, the configured APIs are displayed under the Configured permissions section.
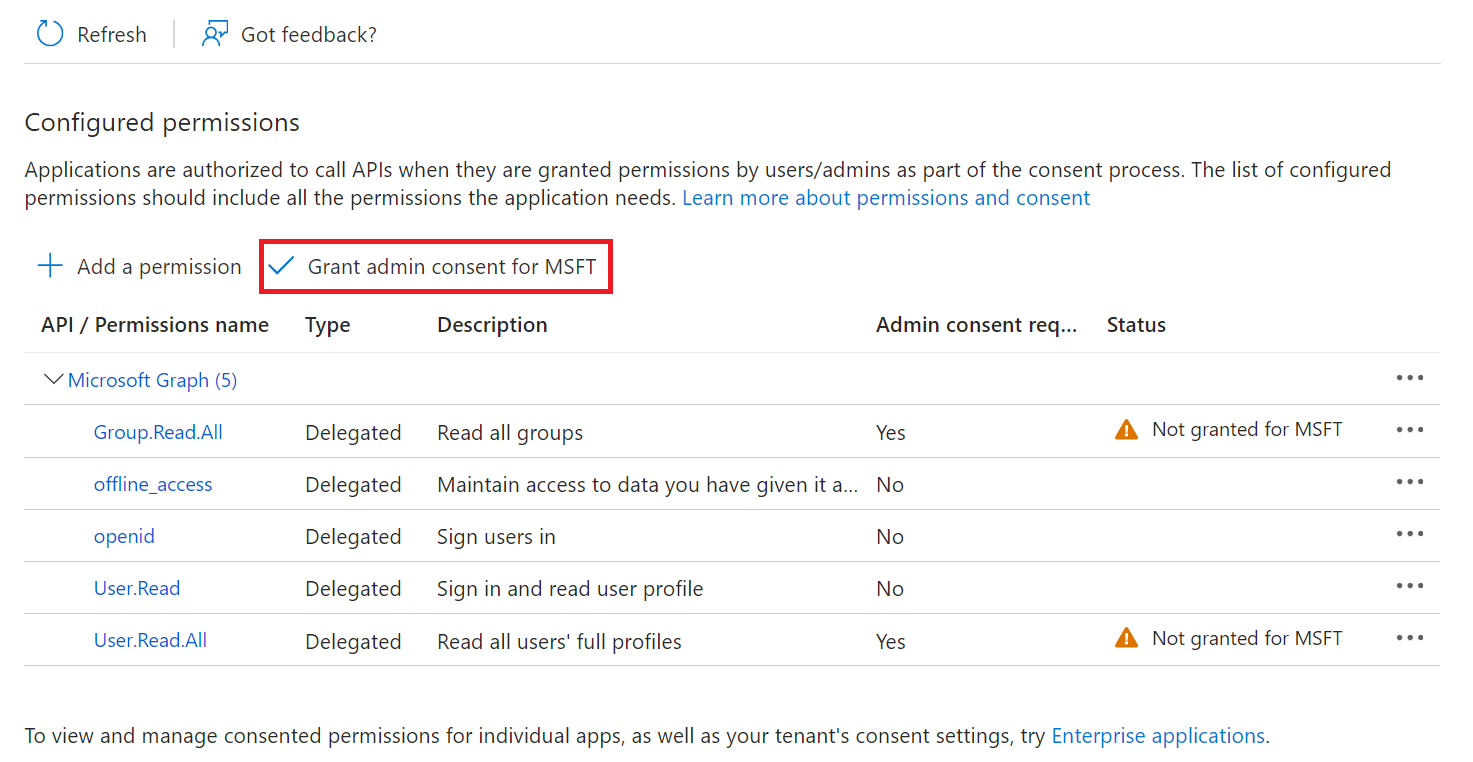
- Click Grant admin consent for {your organization} to grant consent for the requested permissions.
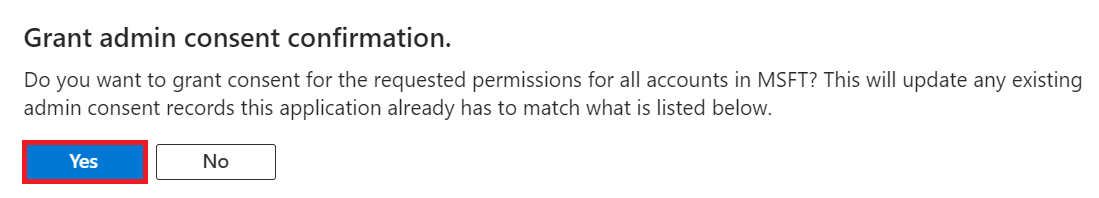
- In the Grant admin consent confirmation pop-up window, click Yes.
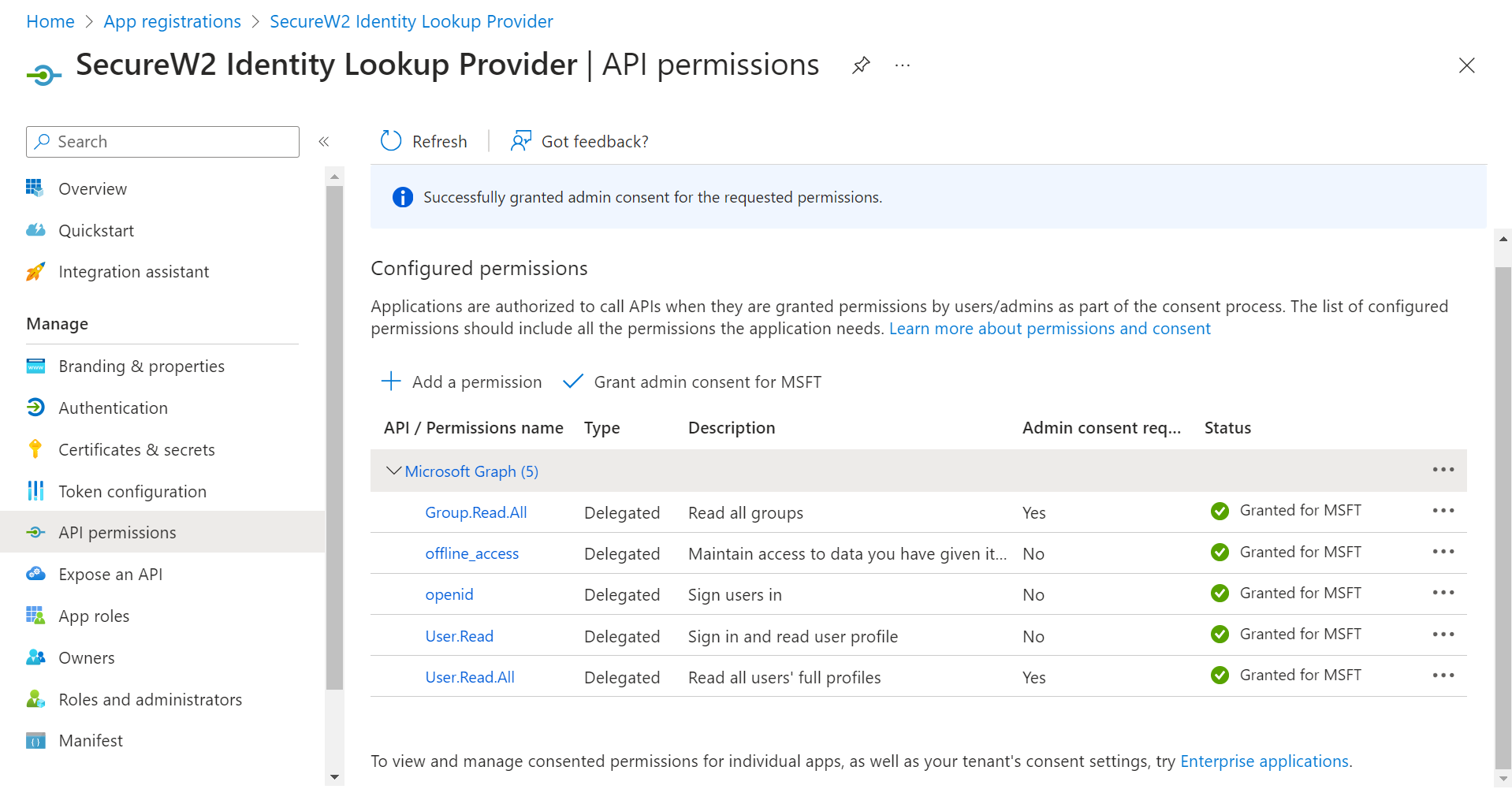
- The configured APIs are granted consent, and the following screen is displayed.
The Azure IDP Lookup Attributes allow you to specify how to map a user’s identity from Entra ID to the user in the JoinNow Management Portal.Attribute Description accountEnabled The accountEnabled attribute indicates whether the user account is enabled or disabled. If the account is enabled, the value is set to “True”; otherwise, it is “False.” The default value is “True.” The attribute supports the $filter with operators such as eq, ne, not, and in. Only callers with the Global Administrator or Cloud Device Administrator role can set this attribute. alternativeSecurityIds The alternativeSecurityIds attribute indicates a single user identity or a collection of user identities from one or more external identity providers. This is a mandatory attribute and supports the $filter with operators such as eq, not, ge, and le. approximateLastSignInDateTime The approximateLastSignInDateTime attribute indicates the timestamp type in ISO 8601 format and UTC time for both date and time information. This is a read-only attribute and supports the $filter with operators such as eq, ne, not, ge, le, $orderBy, and eq on null values. complianceExpirationDateTime The complianceExpirationDateTime attribute indicates the timestamp when the device is no longer compliant. Using the ISO 8601 format, the timestamp type shows date and time information always in UTC time. This is a read-only attribute. createdDateTime The createdDateTime attribute indicates the creation date of the user object. This is a read-only attribute. deletedDateTime The deletedDateTime attribute indicates the date and time when the user object was deleted, or null if the object has not been deleted. deviceCategory The deviceCategory attribute is a user-defined attribute set by Intune. This attribute automatically adds devices to groups and makes device management easier. deviceId The deviceId attribute is the unique identifier that the Azure Device Registration Service assigns to the device when it registers. You can use this identifier as an alternate key to reference the device object. This attribute supports the $filter with these operators such as eq, ne, not, and startsWith. deviceMetadata A device metadata package contains multiple XML documents, each explaining the various components of the device attributes. deviceOwnership The deviceOwnership attribute indicates the device’s ownership. This attribute is set by Intune. Possible values are unknown, company, and personal. deviceVersion This attribute indicates the version of the device. displayName The displayName attribute indicates the display name for the device and supports the $filter with these operators such as eq, ne, not, ge, le, in, startsWith, $search, $orderBy, and eq on null values. This is a mandatory attribute. domainName The domainName attribute indicates the on-premises domain name for devices joined to Hybrid Entra ID. This attribute is set by Intune. enrollmentProfileName The enrollmentProfileName attribute indicates the enrollment profile applied to the device. This attribute is set by Intune. Examples of enrollment profiles are Apple Device Enrollment Profile, Device enrollment—Corporate device identifiers, and Windows Autopilot profile name. enrollmentType The enrollmentType attribute indicates the device’s enrollment type. This attribute is set by Intune. Possible values are unknown, userEnrollment, deviceEnrollmentManager, appleBulkWithUser, appleBulkWithoutUser, windowsAzureADJoin, windowsBulkUserless, windowsAutoEnrollment, windowsBulkAzureDomainJoin, and windowsCoManagement. extensionAttributes The device has 1-15 extension attributes. You cannot select the individual extension attributes and these attributes are stored in the cloud. You can set them when you create or update a device object in Entra ID and support the $filter with these operators such as eq, not, startsWith, and eq on null values. id The id attribute is the device’s unique identifier. It is inherited from directoryObject and is a key that cannot be null. This attribute is read-only and supports the $filter with operators such as eq, ne, not, and in. isCompliant The isCompliant property indicates whether the device is compliant with a Mobile Device Management (MDM) app. The value is “True” if the device is compliant or “False” if not. This can only be updated by Intune for any device OS type or by an approved MDM app for Windows OS devices. It supports the $filter with operators such as eq, ne, not, and in. isManaged The isManaged attribute indicates whether the device is managed by a Mobile Device Management (MDM) app. The value is “True” if the device is managed, or “False” if not. This can only be updated by Intune for any device OS type or by an approved MDM app for Windows OS devices and supports the $filter with operators such as eq, ne, not, and in. isRooted The isRooted attribute indicates whether the device is rooted if the value is “True” or jailbroken if the value is “False.” This value can only be updated by Intune. managementType The managementType attribute indicates the device’s management channel. This attribute is set by Intune, and its value can be one of the following: eas, mdm, easMdm, intuneClient, easIntuneClient, configurationManagerClient, configurationManagerClientMdm, configurationManagerClientMdmEas, unknown, jamf, or googleCloudDevicePolicyController. manufacturer The manufacturer attribute specifies the device manufacturer. This is a read-only attribute. mdmAppId The mdmAppId attribute specifies the application ID that registers the device in MDM. This is a read-only attribute and supports the $filter with operators such as eq, ne, not, and startsWith. model The model attribute indicates the device model. This is a read-only attribute. onPremisesLastSyncDateTime The onPremisesLastSyncDateTime attribute indicates the last time that the object synchronized with the on-premises directory. The attribute uses the Timestamp type, which represents date and time information in UTC time and ISO 8601 format. For example, 2014-01-01T00:00:00Z is midnight UTC on January 1, 2014. This is a read-only attribute and supports the $filter with operators such as eq, ne, not, ge, le, and in. onPremisesSyncEnabled The onPremisesSyncEnabled attribute specifies whether the object synchronizes from an on-premises directory. The value is “True” if the object synchronizes from an on-premises directory, “False” if the object used to synchronize from an on-premises directory but no longer does, or “Null” if the object has never synchronized from an on-premises directory. The default value is “Null”. This is a read-only attribute and supports the $filter with operators such as eq, ne, not, in, and eq on null values. operatingSystem The operatingSystem attribute specifies the device’s operating system type. It is mandatory and supports the $filter with operators such as eq, ne, not, ge, le, startsWith, and eq on null values. operatingSystemVersion The operatingSystemVersion attribute specifies the device’s operating system version. It is mandatory and supports the $filter with operators such as eq, ne, not, ge, le, startsWith, and eq on null values. physicalIds The physicalIds attribute specifies the unique values that identify the device. This is a mandatory attribute and supports the $filter with these operators such eq, not, ge, le, startsWith, /$count eq 0, /$count ne 0. profileType The profileType attribute indicates the device profile type. The possible values are RegisteredDevice (default), SecureVM, Printer, Shared, or IoT. registrationDateTime The registrationDateTime attribute specifies the date and time that the device registered. The attribute uses the timestamp type, which represents date and time information in UTC time and ISO 8601 format. For example, 2014-01-01T00:00:00Z is midnight UTC on January 1, 2014. This is a mandatory read-only attribute. systemLabels The systemLabels attribute indicates the list of labels that the system applies to the device. This attribute supports the $filter with these operators such as /$count eq 0, /$count ne 0. trustType The trustType attribute specifies the trust type for the joined device. This is a read-only attribute and can have one of the following values: Workplace (for personal devices), AzureAd (for cloud-only joined devices), or ServerAd (for on-premises domain joined devices that are also joined to Entra ID).
Configuring JoinNow Management Portal
Now that we’ve created an App in Azure, we need to create an Identity Lookup Provider in the JoinNow Management Portal to communicate with Azure, and, lastly create the various policies we want to implement for segmenting the users/devices and for network authentication accordingly.
Configuring an Identity Lookup Provider
An Identity Lookup Provider is a system that proves a user’s or device’s identity. Configuring an IDP in the JoinNow Management Portal helps in integrating to your Azure user database for verification during certificate issuance and wifi authentication.
During the authentication process, the identity lookup configuration validates that a user or device is active within the organization by checking the identifying information against the existing entities in the Identity Provider.
Creating an Identity Lookup Provider
To create an Identity Lookup Provider, perform the following steps:
- Navigate to Identity Management > Identity Providers.
- Click Add Identity Provider.
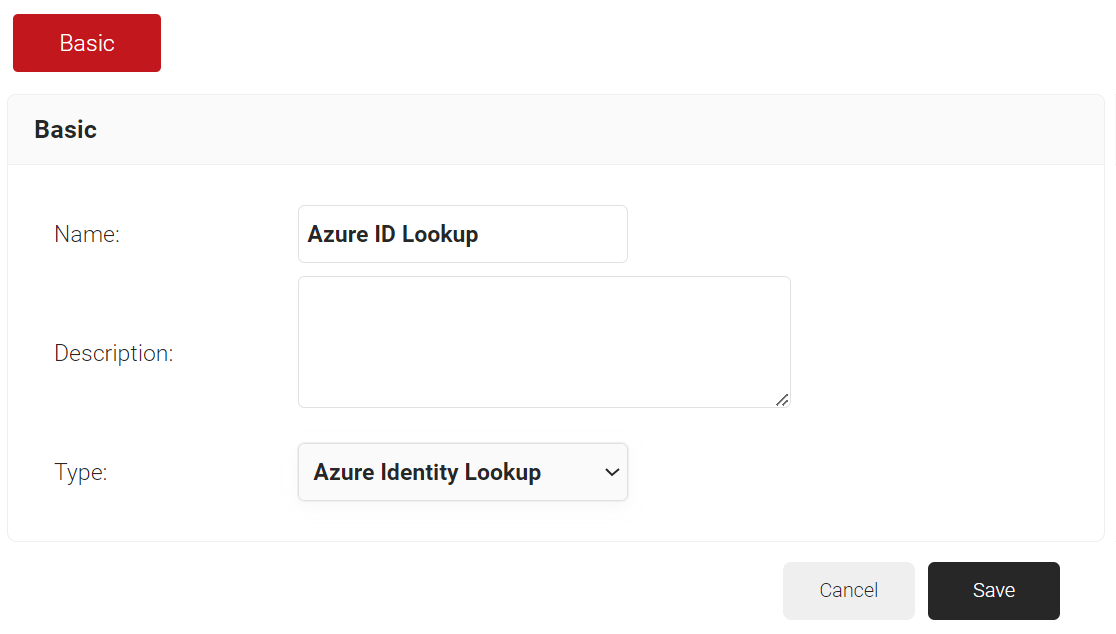
- In the Name field, enter the name of the identity lookup provider.
- In the Description field, enter the suitable description for the identity lookup provider.
- From the Type drop-down list, select Azure Identity Lookup.
- Click Save.
- The page refreshes and displays the Configuration, Attribute Mapping and Groups tabs.
- Select the Configuration tab.
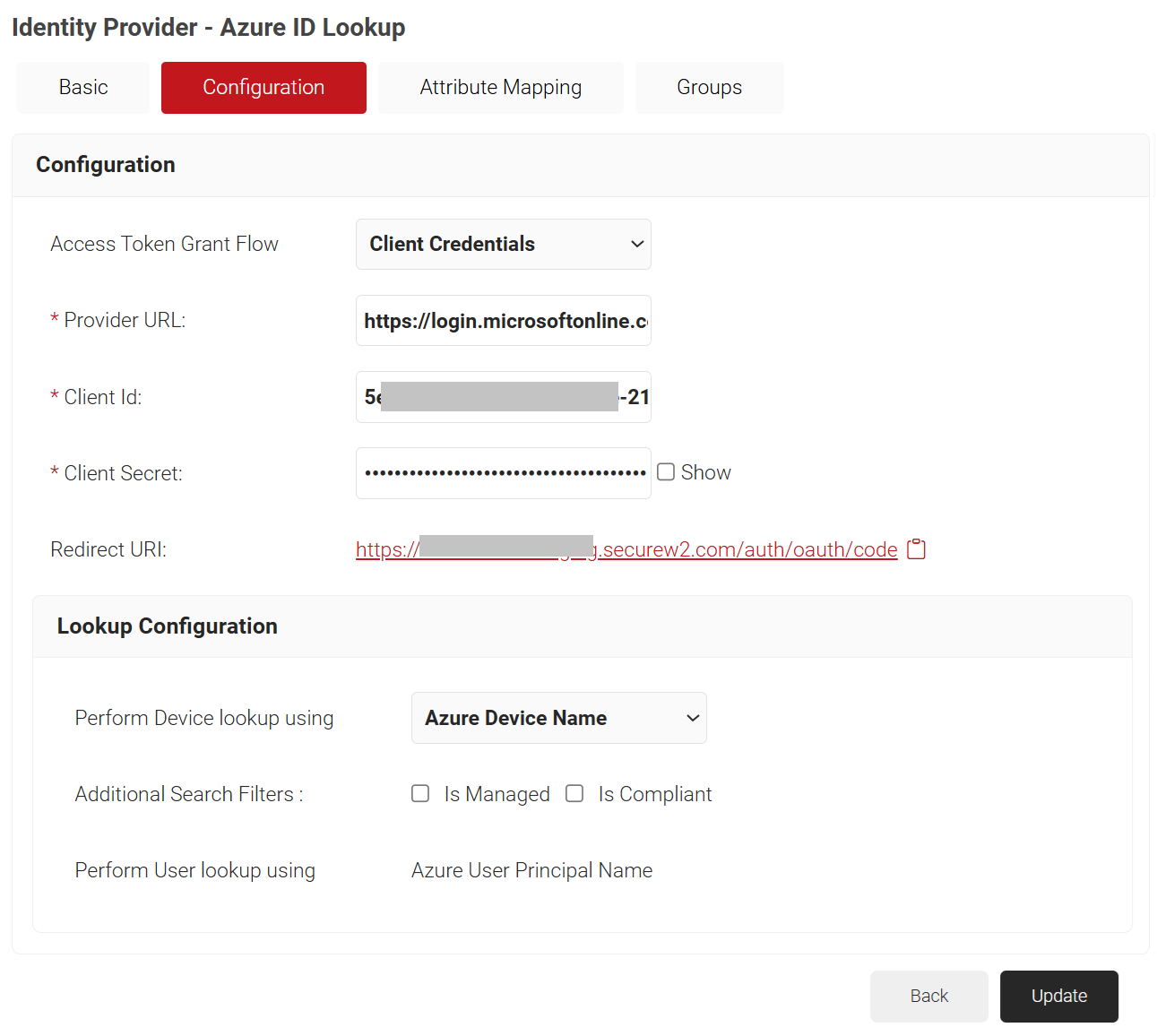
- Under the Configuration section, provide the following information.
- From the Access Token Grant Flow drop-down list, select one of the following options.
- Client Credentials—The Client Credentials option doesn’t require frequent authorization of token updates from the Azure portal. This is the recommended method.
- Authorization Code – The Authorization Code option requires authorization of token updates from the Azure Portal every 90 days.
- In the Provider URL field, enter the URL you created earlier using the Directory (tenant) ID: https://login.microsoftonline.com/{Directory (tenant) ID}. This should look like this: https://login.microsoftonline.com/561bc66f-1d86-4244-8bc4-5eb12cba45ac
- In the Client Id field, enter the Application (client) ID that you retrieved from Azure Portal earlier (refer to the Registering a New App section).
- In the Client Secret field, enter the Client secret you generated in Azure Portal earlier (refer to the Creating a Client Secret section).
- Under the Lookup Configuration section, from Perform Device lookup using drop-down list, select the required device lookup attribute from the options listed below:
- Azure Device ID – Lookup is performed using Azure ADID
- Azure Device Name – Lookup is performed using the device name. For Additional Search Filters, check the required checkbox for:
- Is Managed – Checks if the device is managed
- Is Compliant – Checks if the device is compliant
- From the Access Token Grant Flow drop-down list, select one of the following options.
After updating the Identity Provider, the client secret will not be retrievable. Therefore, make sure that you save it in a secure place.
- Click Update.
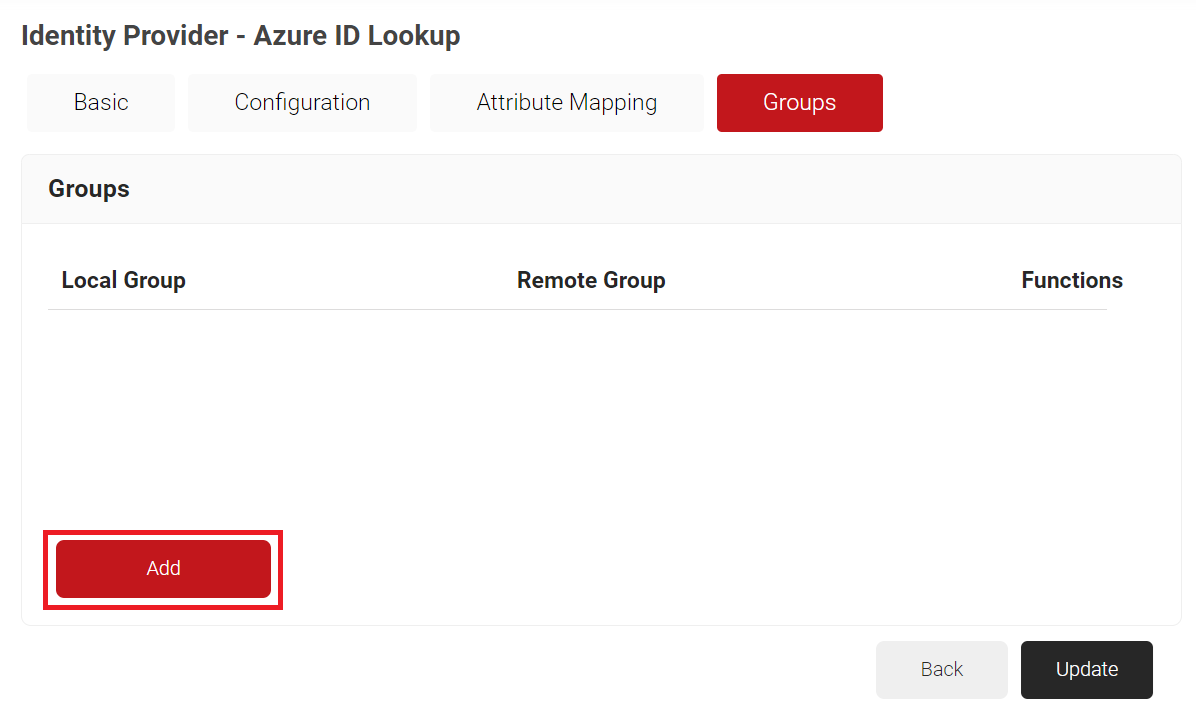
Configuring Groups
Finally, Cloud RADIUS can perform a User Group Lookup, allowing you to create network access policies based on a user’s group membership.
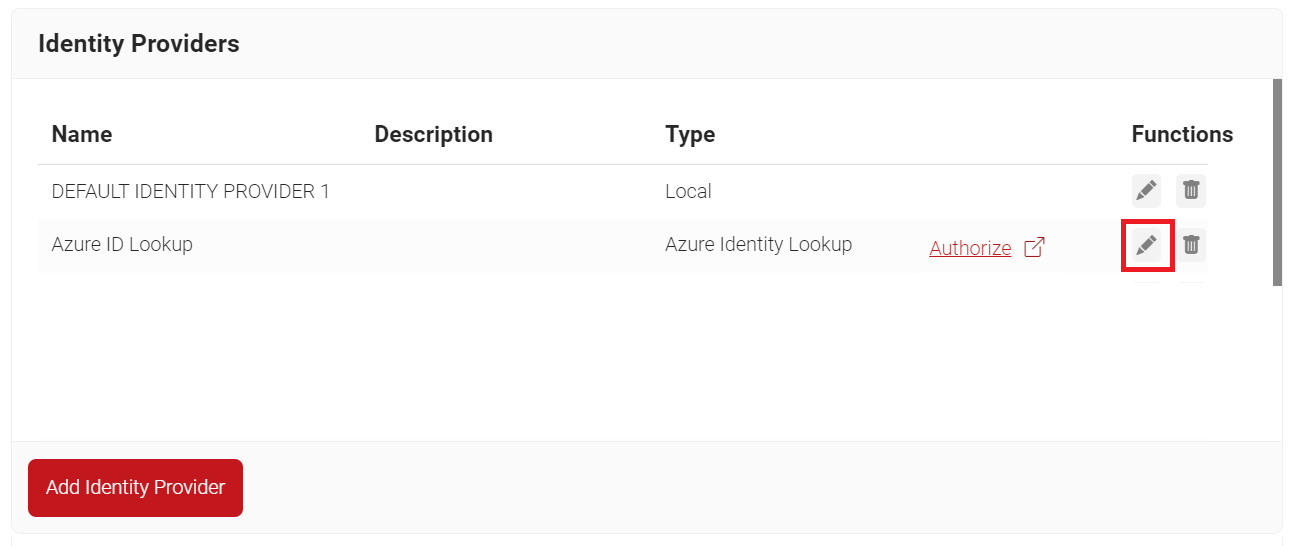
- Navigate to Identity Management > Identity Providers.
- Click the Edit link on the Identity Lookup Provider created earlier (refer to the Creating an Identity Lookup Provider section).
- Select the Groups tab.
- Click Add.
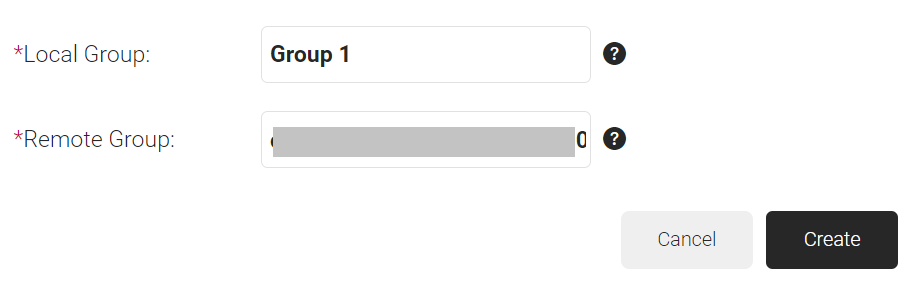
- On the displayed page, in the Local Group field, enter the name of the group. This group name can be used to configure the Network Policies.
- In the Remote Group field, enter the Object ID that you retrieved from Azure Portal earlier (refer to the Registering a New App section).
- Click Create.
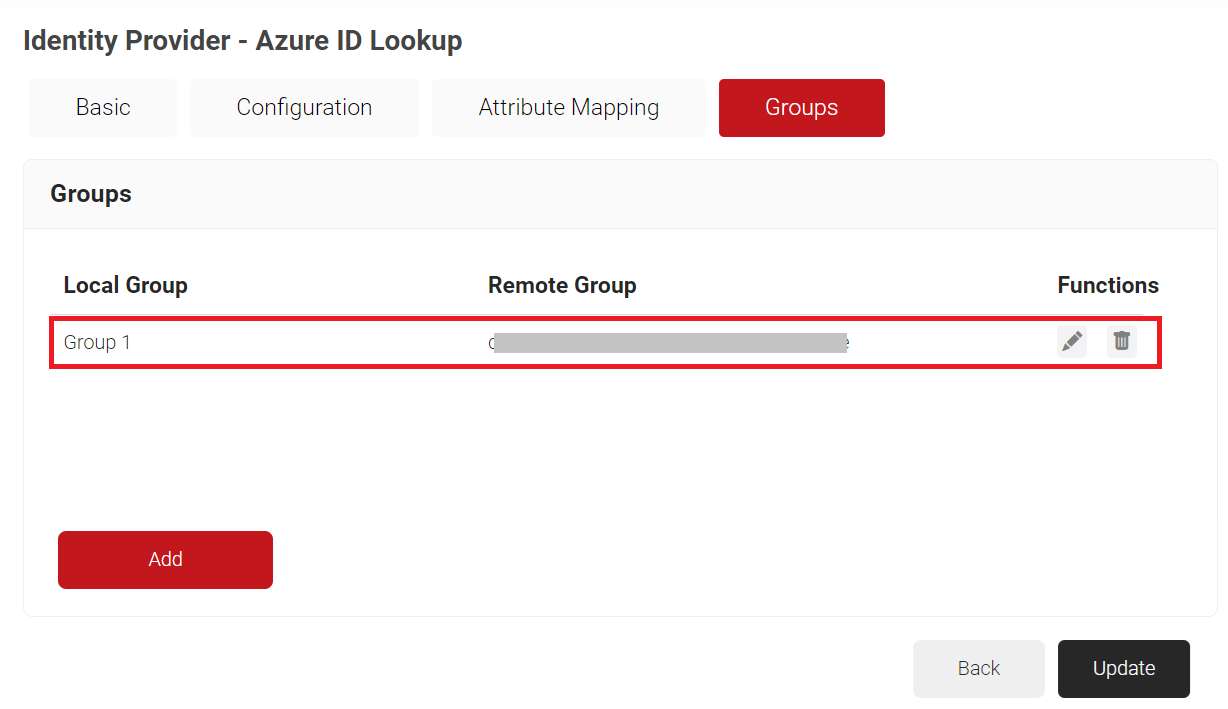
- Click Update.
- Repeat all the steps above as needed to create as many groups as required.
Configuring Policies
Dynamic RADIUS allows the RADIUS to segment users and restrict/allow resources based on information stored in their directory entry. Since enforcement occurs at runtime, changes made to a user’s permissions are propagated throughout the system immediately rather than a day or two later, as is typical with most RADIUS servers.
The following policies need to be configured:
Configuring Account Lookup Policy
The Account Lookup policy is used for user or device lookup during RADIUS authentication.
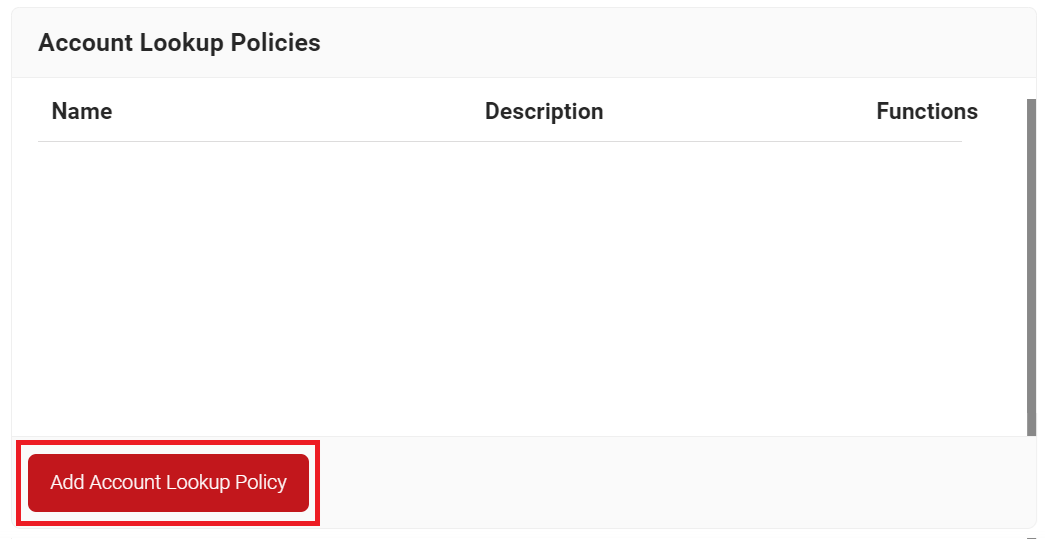
To configure an Account Lookup Policy, perform the following steps:
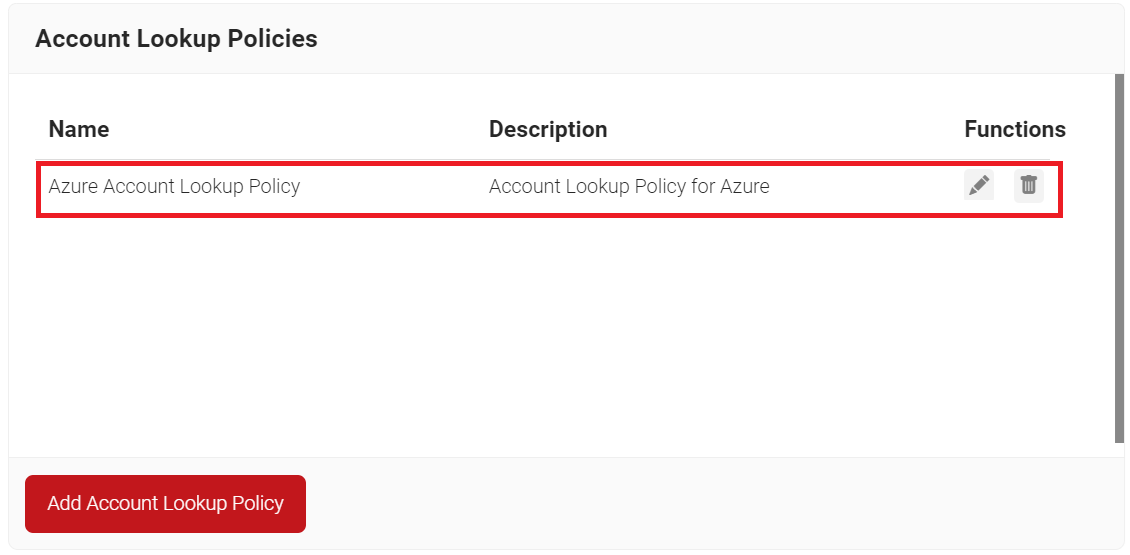
- Navigate to Policy Management > Account Lookup Policies.
- Click Add Account Lookup Policy.
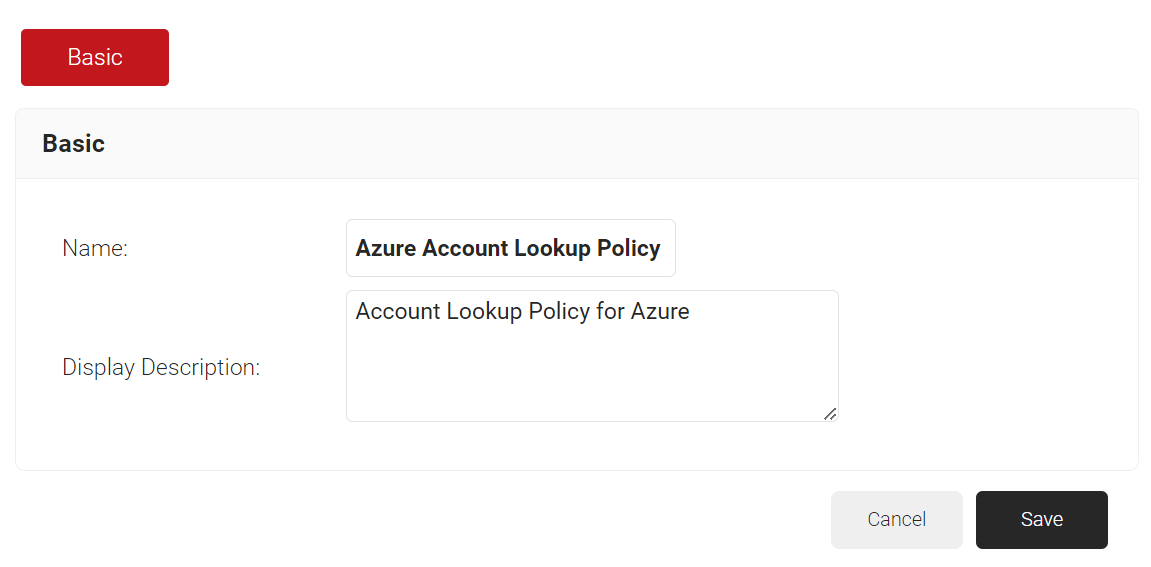
- In the Name field, enter the name of the account lookup policy.
- In the Display Description field, enter a suitable description of the account lookup policy.
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
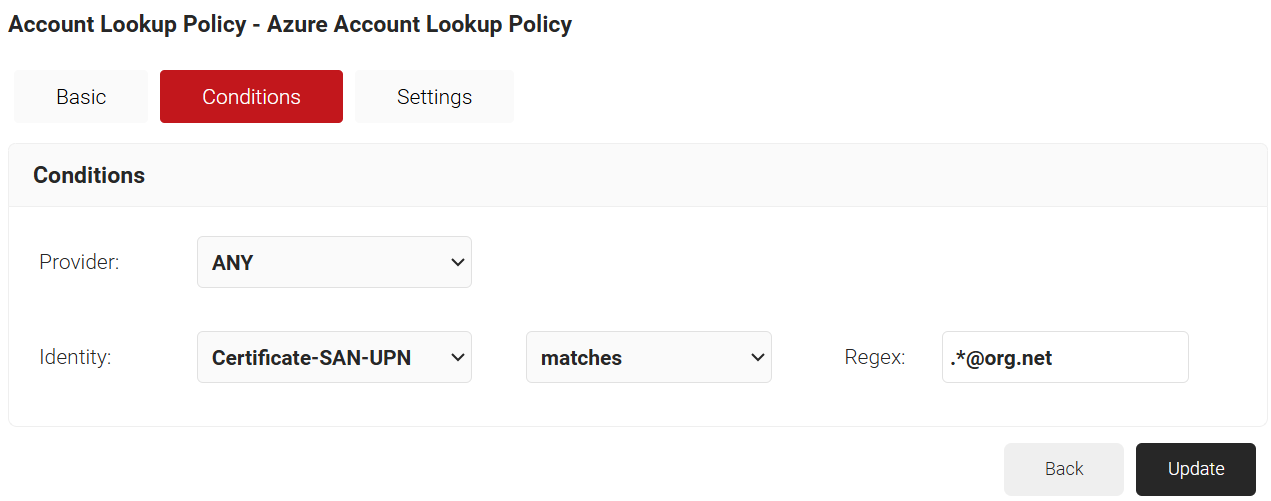
- Select the Conditions tab.
- Under the Conditions section, from the Provider drop-down list, select the Identity Provider used for authentication during certificate issuance.
- From the Identity drop-down list, select any one of the following options as per requirement:
- Username
- Certificate-CommonName
- Certificate-SAN-UPN
- Certificate-SAN-Email
- Configure Regex to match the values of your devices configured in the Identity field.
- Click Update.
Configuring Device Lookup
You need to make a few changes to the Account Lookup Policy to configure the JoinNow Management Portal to lookup Device Identity during RADIUS authentication.
- Navigate to Policy Management > Account Lookup Policies.
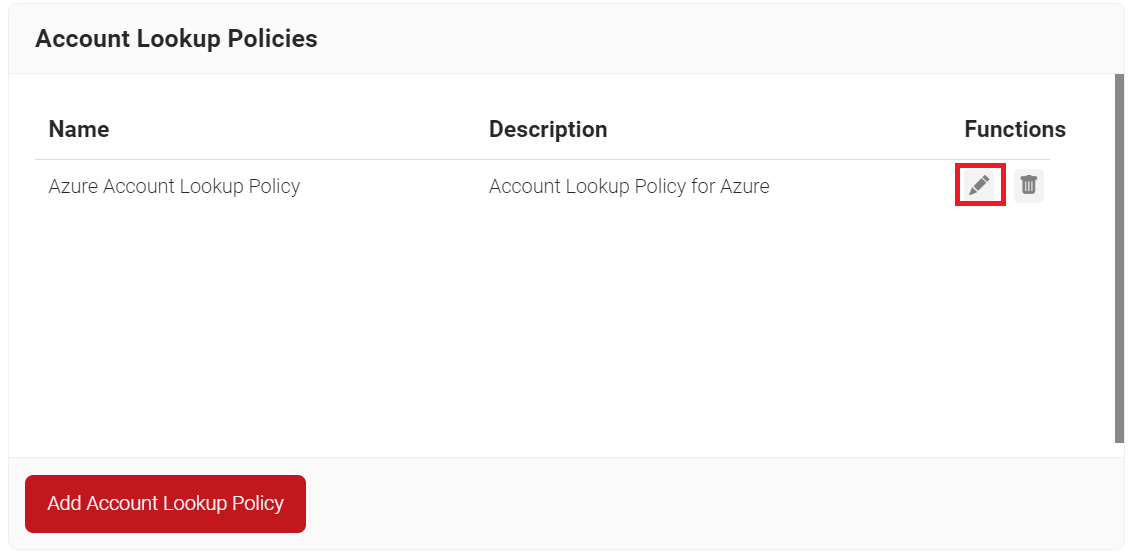
- Click the Edit link on the Account Lookup Policy created earlier (refer to the Configuring Account Lookup Policy section).
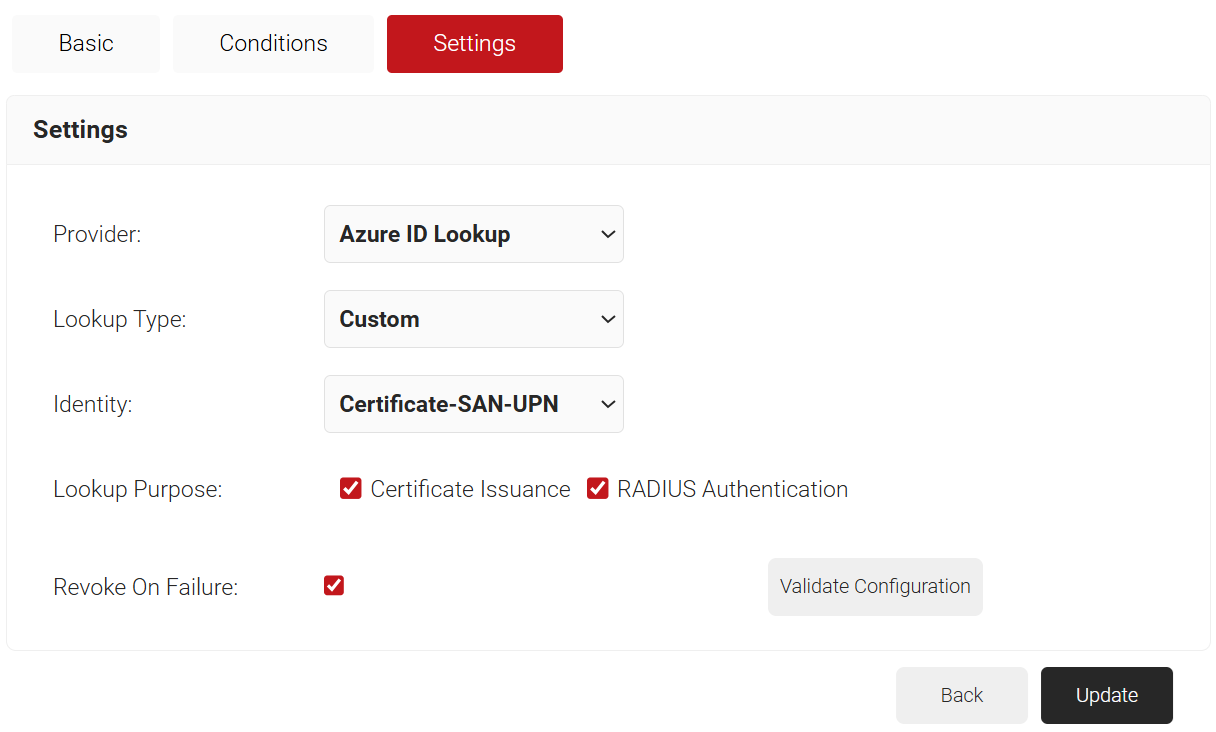
- Select the Settings tab.
- Under the Settings section, from the Provider drop-down list, select the Identity Lookup Provider created in the previous section (refer to the Creating an Identity Lookup Provider section).
- From the Identity drop-down list, select any one of the following options based on your requirements:
- Certificate-SAN-DNS
- Client ID
- Computer Identity
- In the Lookup Purpose field, check the required checkbox:
- Certificate Issuance – To lookup user/device accounts during Certificate Issuance.
- RADIUS Authentication – To lookup user/device accounts during RADIUS Authentication.
- Select the Revoke On Failure checkbox to automatically revoke a certificate if an account lookup fails, if necessary.
- Select the Revoke On Failure checkbox to automatically revoke a certificate if an account lookup fails, if necessary.
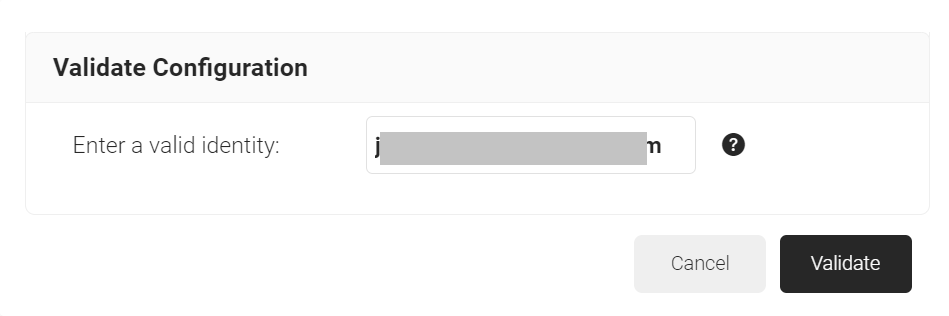
- Click the Validate Configuration button to check if the lookup configuration is valid.
- On the Validate Configuration pop-up window, in the Enter a valid identity field, enter the identity (user/device) to validate the lookup configuration and click Validate.
- After the successful validation, the associated attributes and groups of the Identity Provider Lookup are displayed on the Lookup Details prompt. The admin can use this information to configure the network policies and verify the user’s validity.
- When the Admin enters an invalid identity on the Validate Configuration pop-up window, the following error message is displayed: “Account lookup failed.”
- Click Update.
Configuring Policy Engine Workflow
Policy Engine Workflow can segment users and devices based on defined criteria or attributes. These segmented groups can then be assigned specific network access configurations according to organizational requirements or privileges. Once the Policy Engine Workflow is established, Cloud RADIUS can dynamically enforce the configured Network Policies, which will be set up in the subsequent steps.
To create Policy Engine Workflow, follow these steps:
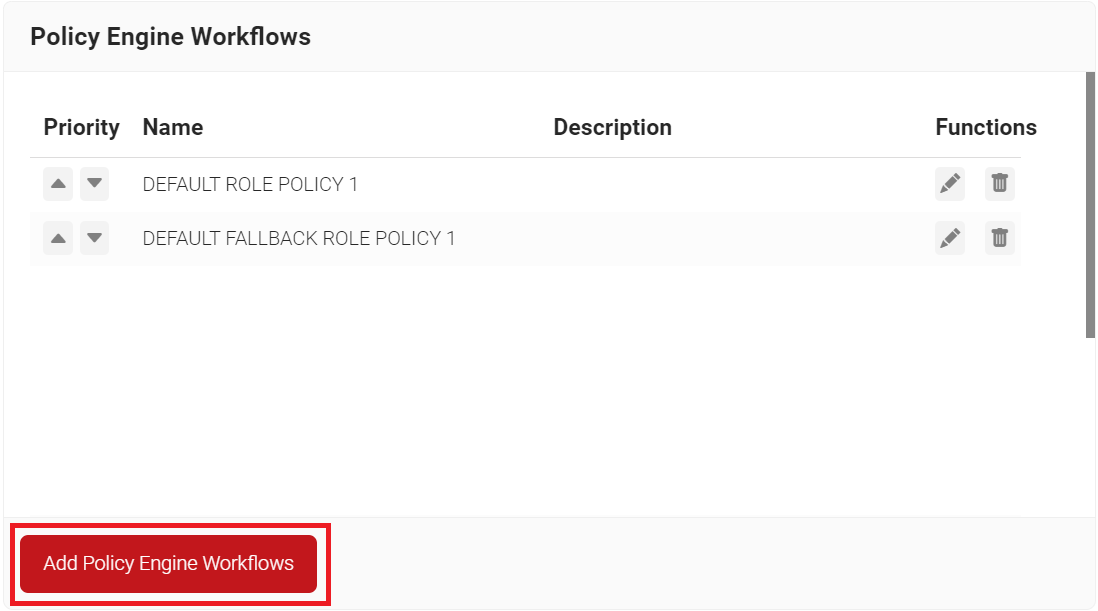
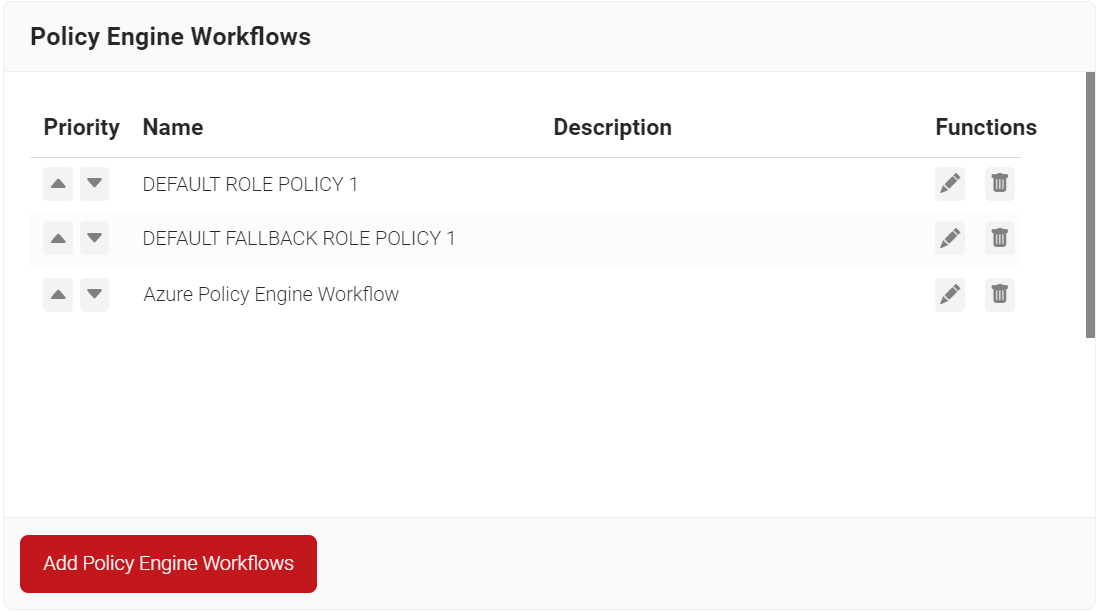
- Navigate to Policy Management > Policy Engine Workflows.
- Click Add Policy Engine Workflows.
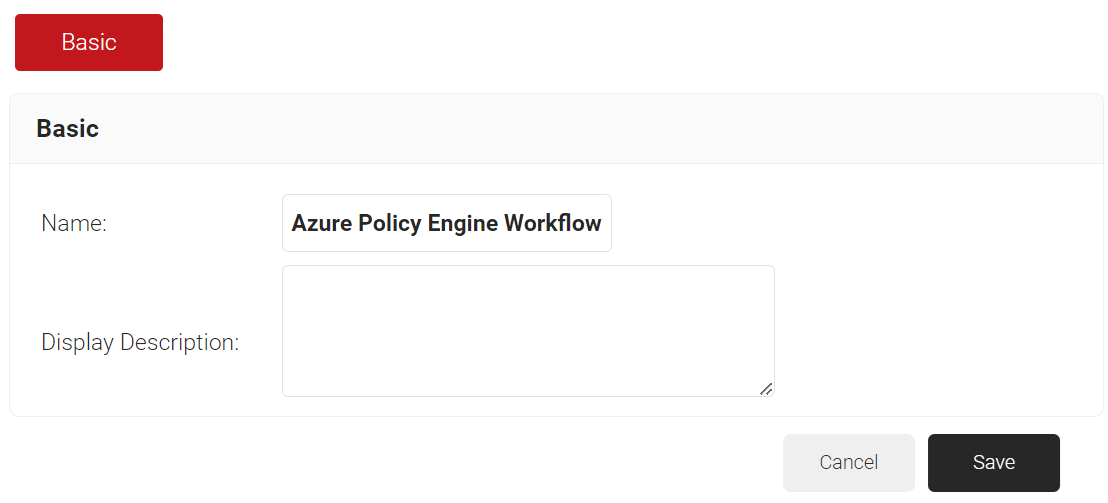
- In the Name field, enter the name of the Policy Engine Workflow.
- In the Display Description field, enter the suitable description for the Policy Engine Workflow.
- Click Save.
- The page refreshes and displays the Conditions tab.
- Select the Conditions tab.
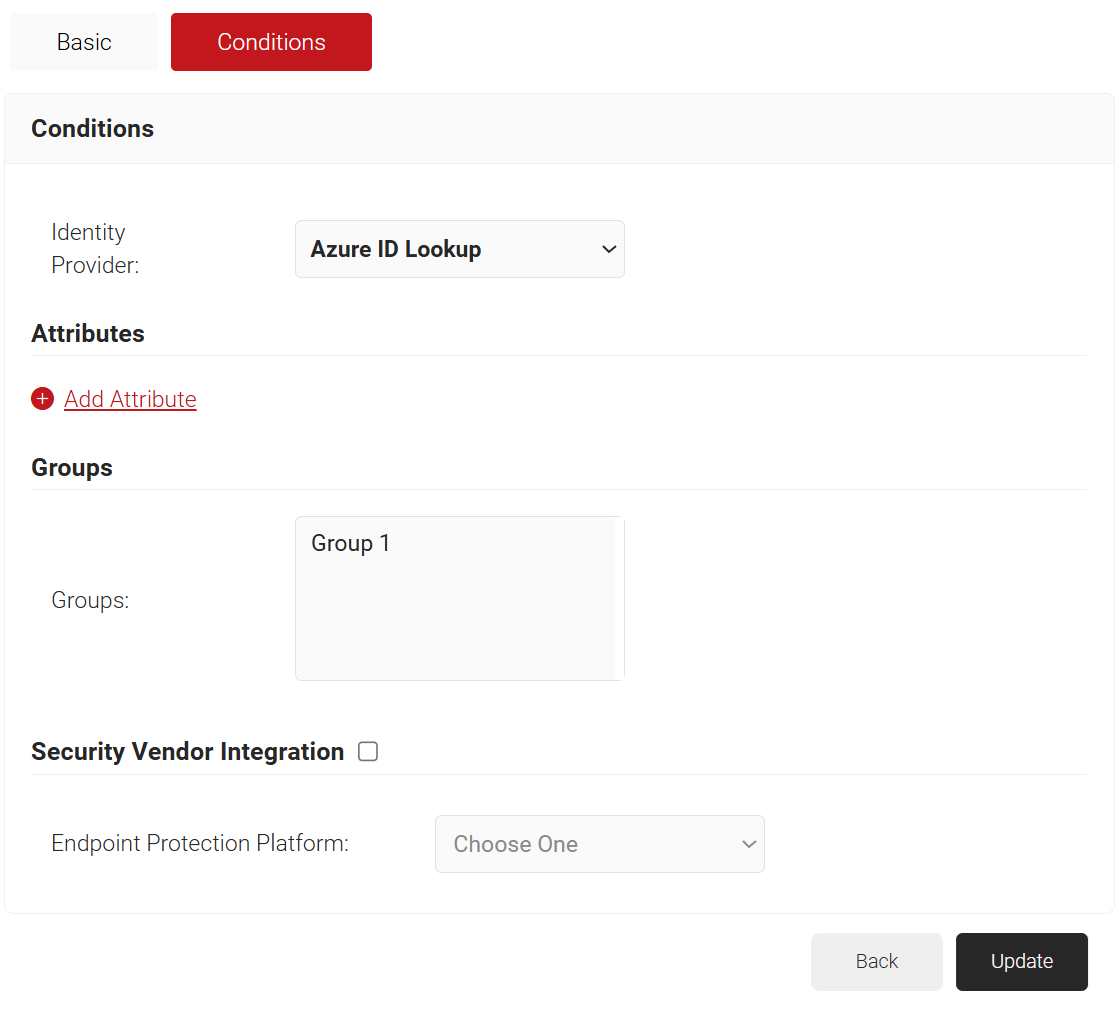
- From the Identity Provider drop-down list, select the Azure Identity Lookup Provider created in the previous section (refer to the Creating an Identity Lookup Provider section).
- Click Update.
Configuring Network Policy
The purpose of a Network Policy is to specify how Cloud RADIUS will authorize access to a particular User Role. A typical Network Policy would say, “If User Role = Staff, authorize access and assign them to VLAN 2”. You can configure any RADIUS Attribute to be sent to the wireless controller. If you leave the attribute section blank, it will just send Access Accept.
To create and configure the Network Policy, perform following steps:
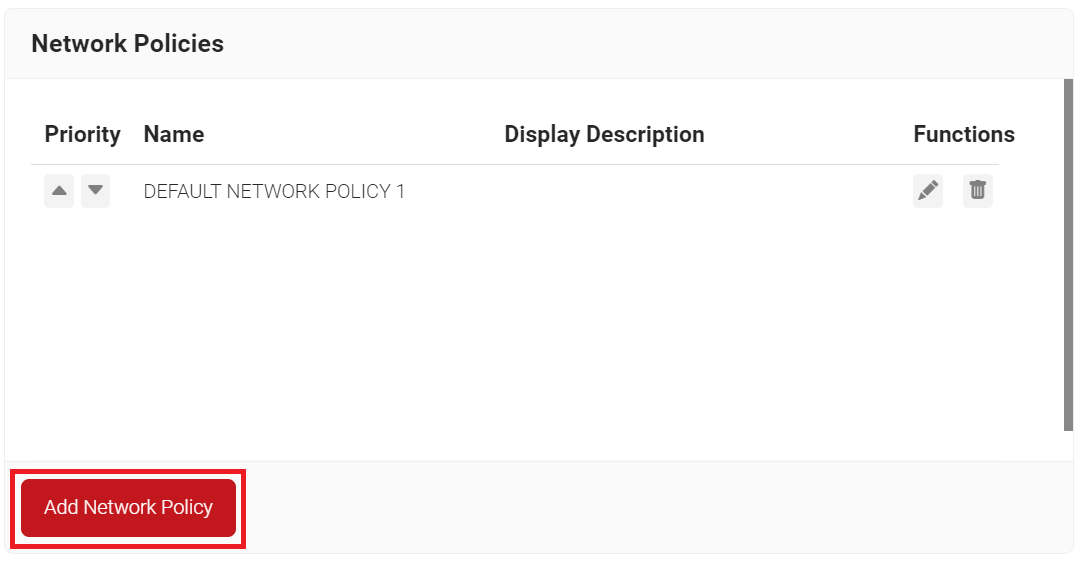
- Navigate to Policy Management > Network Policies.
- Click Add Network Policy.
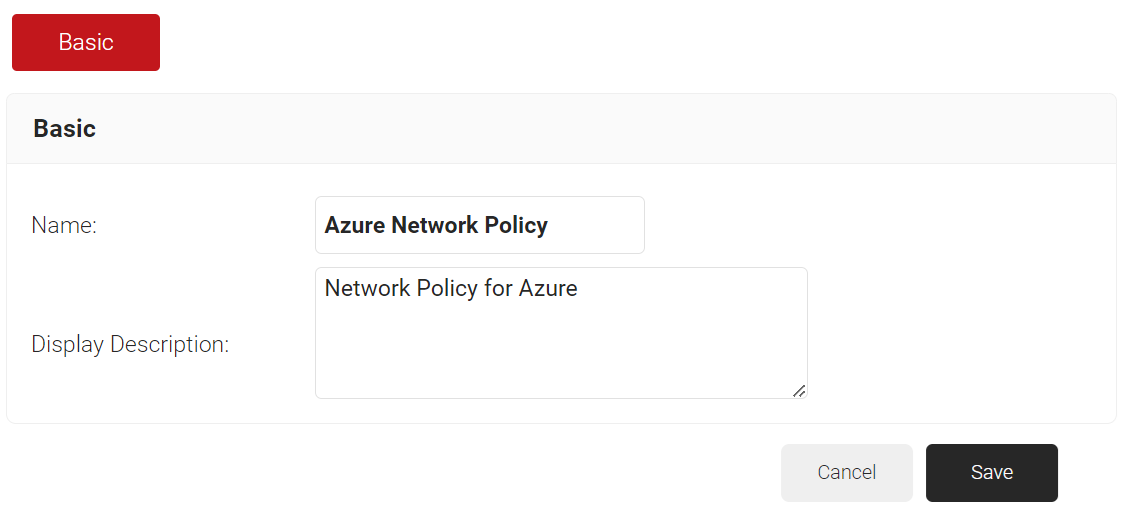
- In the Name field, enter the name of the network policy.
- In the Display Description field, enter the suitable description for the network policy.
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
- Select the Conditions tab.
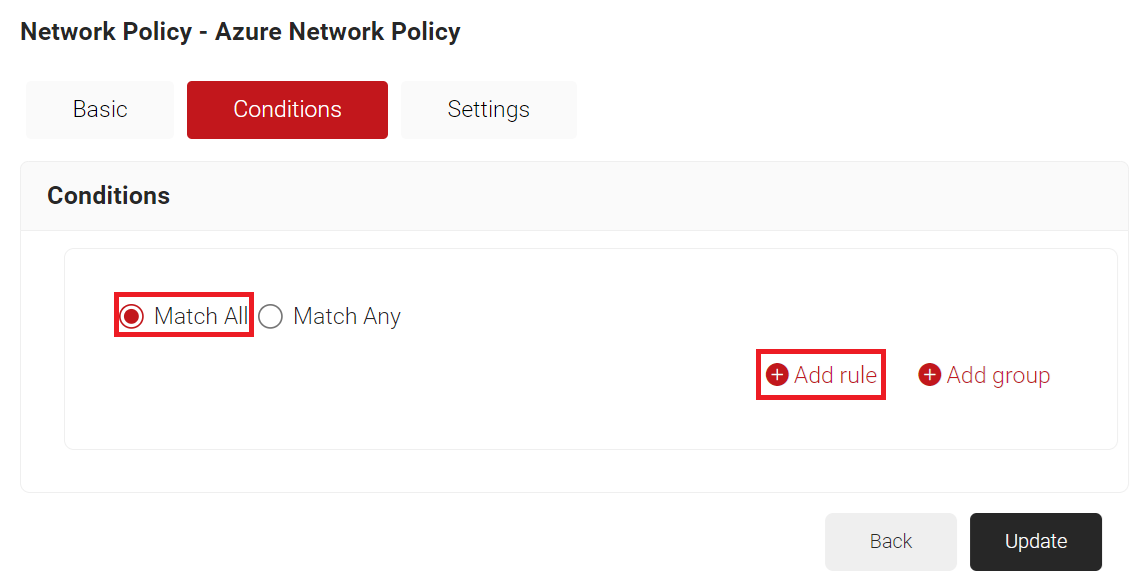
- Select Match All or Match Any based on your requirement to set authentication criteria. In the case explained here, we are selecting Match All.
- Click Add rule.
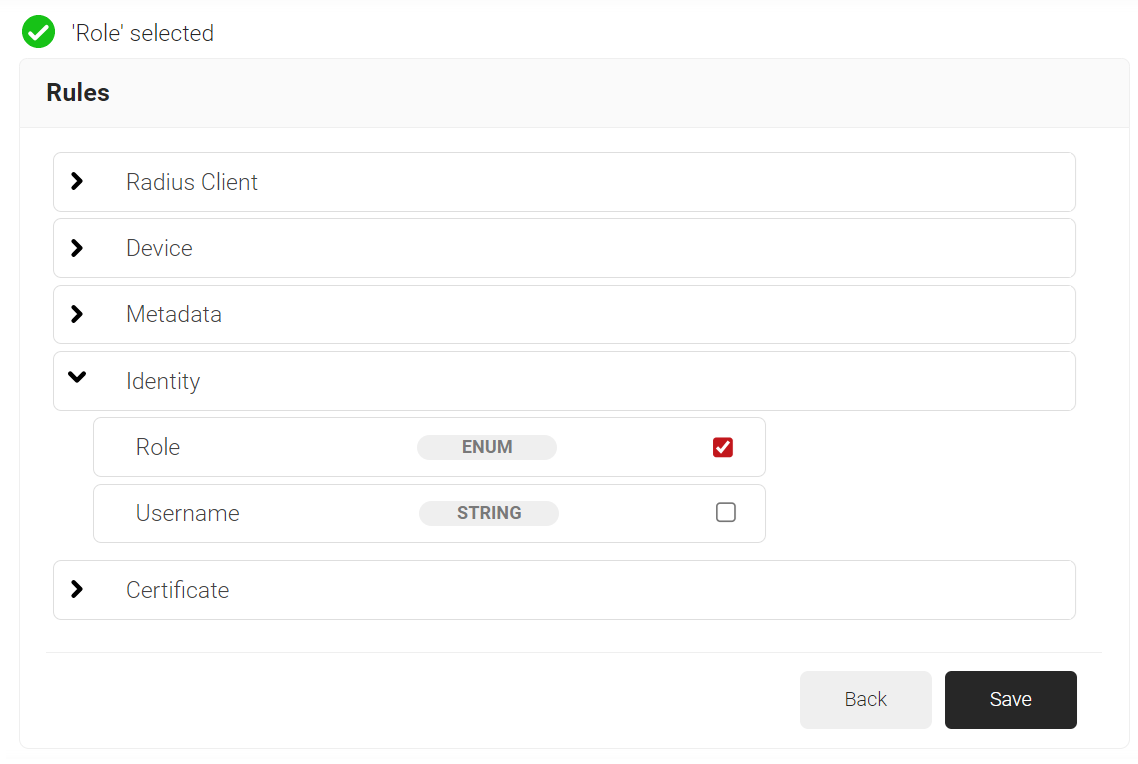
- Expand Identity and select the Role option.
- Click Save.
- The Role option appears under the Conditions tab.
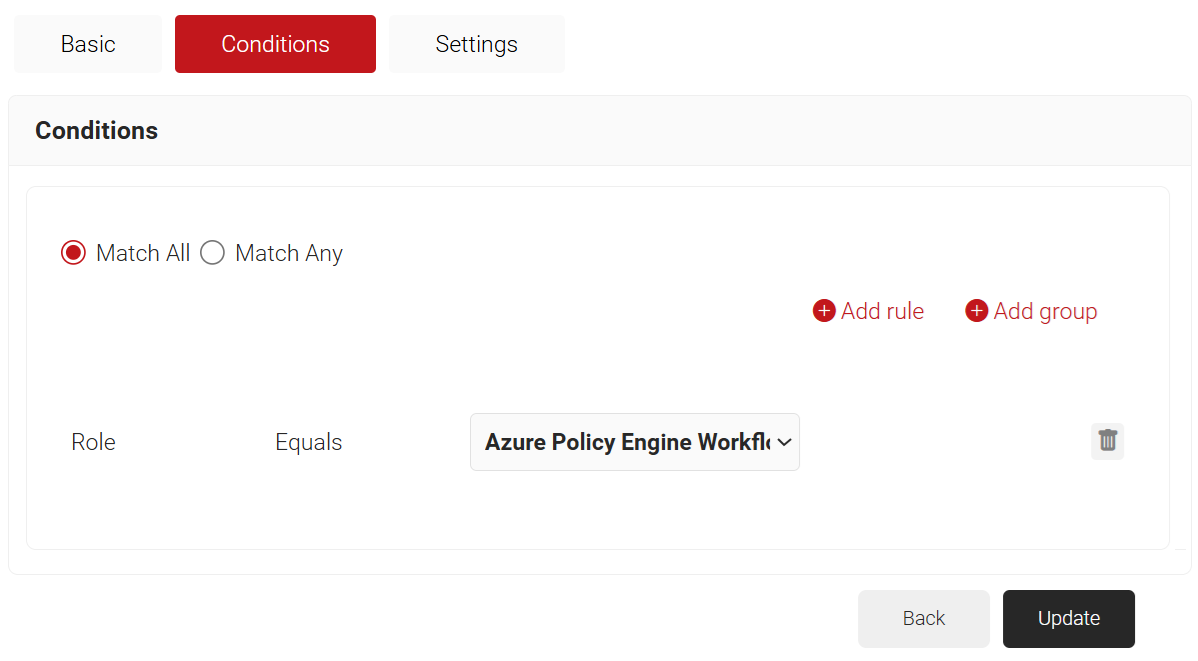
- From the Role Equals drop-down list, select the Policy Engine Workflow you created earlier (refer to the Configuring Policy Engine Workflow section). You can select multiple Policy Engine Workflows to assign to a Network Policy.
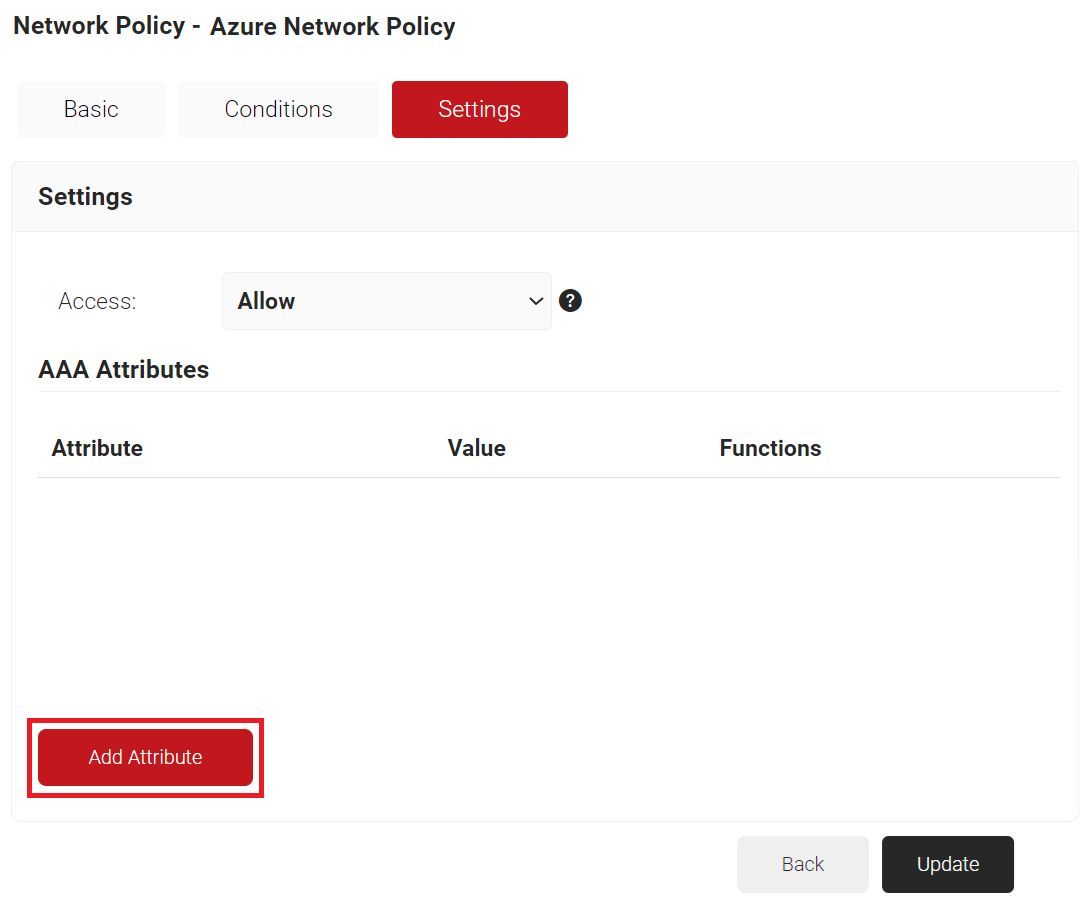
- Select the Settings tab.
- Click Add Attribute.
- From the Dictionary drop-down-list, select an option: Radius:IETF or Custom.
- From the Attribute drop-down-list, select any of the following options based on your requirements:
- Framed-Protocol
- Framed-IP-Address
- Framed-IP-NetMask
- Framed-Routing
- Filter-Id
- Framed-MTU
- Framed-Compression
- Reply-Message
- Framed-Route
- Framed-IPX-Network
- State
- Class
- Session-Timeout
- Tunnel-Type
- Tunnel-Medium-Type
- Tunnel-Private-Group-ID
- Framed-Pool
- In the Value field, enter the appropriate value for the attribute.
Repeat as necessary for all the attributes you want to send for your User Role.
- Click Save.
This completes all the necessary configurations to enable the Dynamic RADIUS solution in your infrastructure.
Conclusion
Dynamic RADIUS will revolutionize the way certificate-based WPA2-Enterprise networks are run. Azure customers implementing certificate-based authentication no longer need to worry about certificate management and will benefit from runtime-level policy enforcement and security redundancies. Overall, the user experience will be vastly improved on all fronts.
SecureW2 has affordable options for organizations of all sizes. Click here for further details.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing