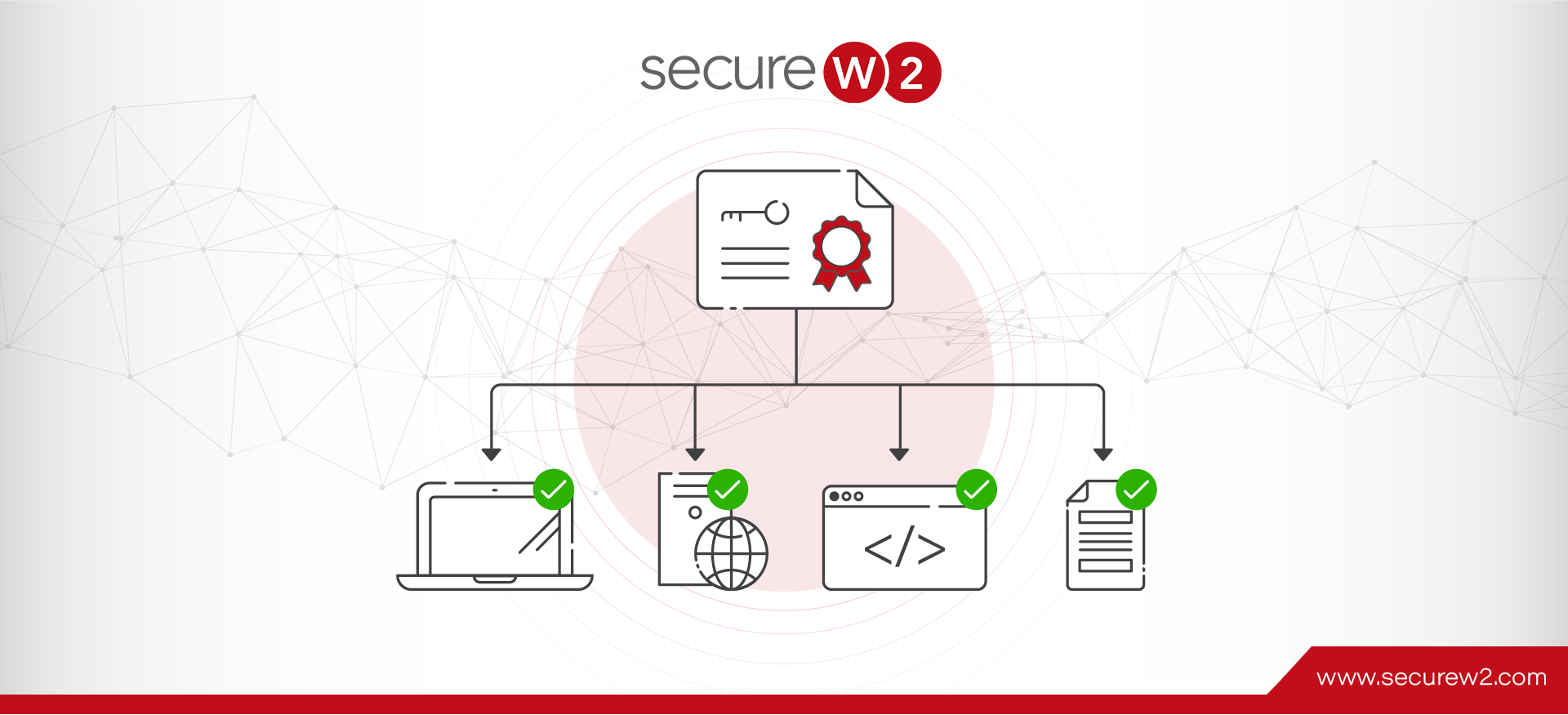
What is an X.509 Digital Certificate?
X.509 certificates are forms of identification that leverage public-private key cryptography. They are a secure replacement for passwords.
Stay informed with expert insights, best practices, and the latest developments in network security, identity management, and SecureW2 product updates.

X.509 certificates are forms of identification that leverage public-private key cryptography. They are a secure replacement for passwords.

Man-in-the-middle attacks (MITM) or on-path attacks are becoming common and complex. Organizations are putting in a lot of effort to mitigate these risks to no avail. Phishing kits are freely available, enabling on-path attackers to utilize tools to launch an ... Read More
Certificates are far superior to credentials and mitigate many vulnerabilities associated with pre-shared keys. They enhance the user experience by facilitating network access and removing password-related friction induced by password reset and complexity policies. Certificates also grant identity context by ... Read More
Do you use Apple devices in your work infrastructure? Then you’ve probably heard of Jamf. Jamf Pro is one of the most robust and feature-dense solutions for managing Apple devices. To fully take advantage of Jamf Pro, you will need ... Read More

Public Wi-Fi is any network other than your home or work network and is commonly found in places such as airports, malls, coffee shops, hotels, and restaurants. It allows users to connect to an unknown network for free. People extensively ... Read More
Continuous Access Evaluation (CAE) is an essential security feature in Azure Active Directory (Azure AD) that constantly monitors and evaluates user access to resources. Through CAE, Azure provides a proactive approach to maintaining a secure environment and safeguarding sensitive data ... Read More

Conditional Access Policies, the If-Then statements available in Microsoft Azure AD (Entra ID), enable a much more granular level of access control over the resources managed with Azure AD / Entra ID. It can be used to assess a user’s ... Read More

An IBM study says that stolen or compromised passwords are the most common reason for a data breach. Let’s be honest, usernames and passwords aren’t a good way to prove who you are anymore, especially for large companies. With the ... Read More

Cryptography is a cornerstone of securing information systems. It involves encoding data to ensure only authorized parties can access it. By converting data into an unreadable format, cryptography protects sensitive data from being exposed in the event of security breaches. ... Read More

Security over the internet has drastically improved in the few decades that the internet has been widely available. The average user doesn’t realize how much goes on behind the scenes to ensure the integrity of their data and browsing experience ... Read More
Imagine you are a parent working from home, and your child accidentally spills a drink on your work laptop. You have an approaching work deadline, so you finish it on your home computer that your child occasionally uses. What if ... Read More
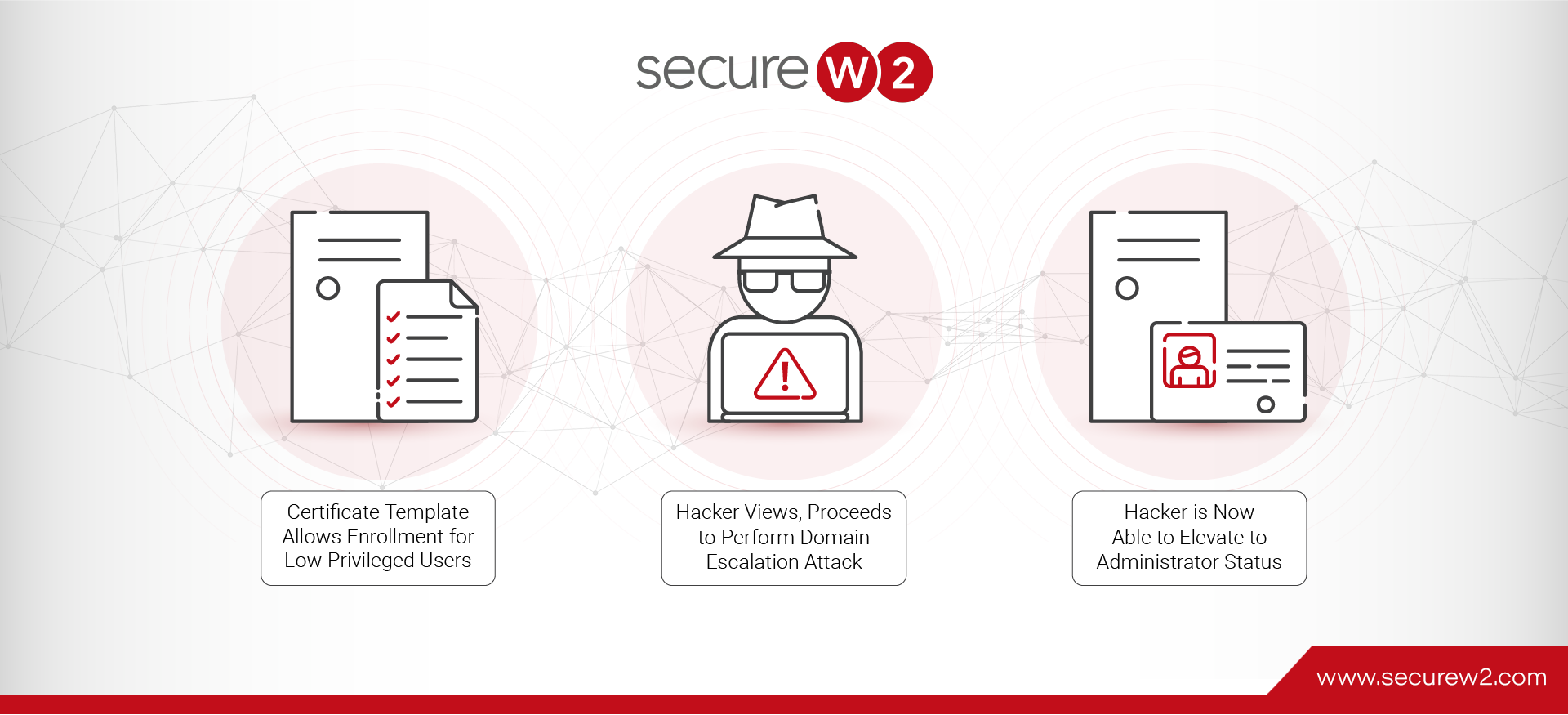
Active Directory Certificate Services (AD CS) is an essential tool for domain administrators to enhance network security, ensuring secure communication, code signing, and user authentication. Organizations can leverage the 802.1x network protocol and a certificate enrollment policy. Authenticated users can ... Read More