Key Points
- The internet is inherently insecure, leaving all data transmitted over it vulnerable to interception without a strong encryption protocol like SSL/TLS.
- The SSL/TLS protocol and its use of digital certificates provide a secure solution by encrypting data and verifying the identity of a web server, thus protecting against unauthorized access.
- SecureW2s managed Cloud PKI automates the deployment and management of private certificates, eliminating the need for complex, costly on-premise infrastructure.
Security over the internet has drastically improved in the few decades that the internet has been widely available. The average user doesn’t realize how much goes on behind the scenes to ensure the integrity of their data and browsing experience every time they navigate a website.
Secure Sockets Layer (SSL) is one prevalent protocol used to protect users and web servers through digital certificates. Understanding how SSL certificates work and how to get and manage them is vital to end-users and organizations.
What Is SSL?
Secure Sockets Layer, abbreviated as SSL, is a standard security protocol utilized in web browsers and web servers to encrypt data between them. It ensures data privacy, integrity, and proper identification of network servers. Without it, the data you send or receive over the internet is susceptible to interception by malicious actors. The SSL protocol not only encrypts your data, making it unreadable to those without the correct decryption key, but it also validates the identity of the servers you are communicating with.
Historical Background of SSL
Netscape developed SSL in the mid-1990s to secure transactions over their web browser. The initial versions were flawed and vulnerable, but subsequent improvements have made SSL the bedrock of internet security.
SSL version 1.0 was never released due to serious security flaws. The improved version 2.0 was released in 1995 but still had inherent vulnerabilities. SSL protocol version 3.0 was a complete rewrite and formed the basis for Transport Layer Security (TLS), the successor to SSL. Over the years, several iterations of SSL were developed over the years, each taking strides towards increasing the security of online data exchange. This culminated in the development of SSL 3.0, which solved many of the intrinsic security issues in the earlier versions.
Transition from SSL to Transport Layer Security (TLS)
While SSL remains a prevalent term, its successor, TLS, developed by the Internet Engineering Task Force (IETF), has become the more secure and advanced protocol. Introduced in 1999 as an upgrade to SSL 3.0, TLS offers improved encryption and authentication, advanced cipher suites, and comprehensive security measures. Despite SSL’s widespread use in language, modern web servers and browsers use TLS for secure data transmission. The continuous enhancements in TLS bolster internet communication security, hence the necessity for businesses to transition from SSL to TLS to maintain high data security standards.
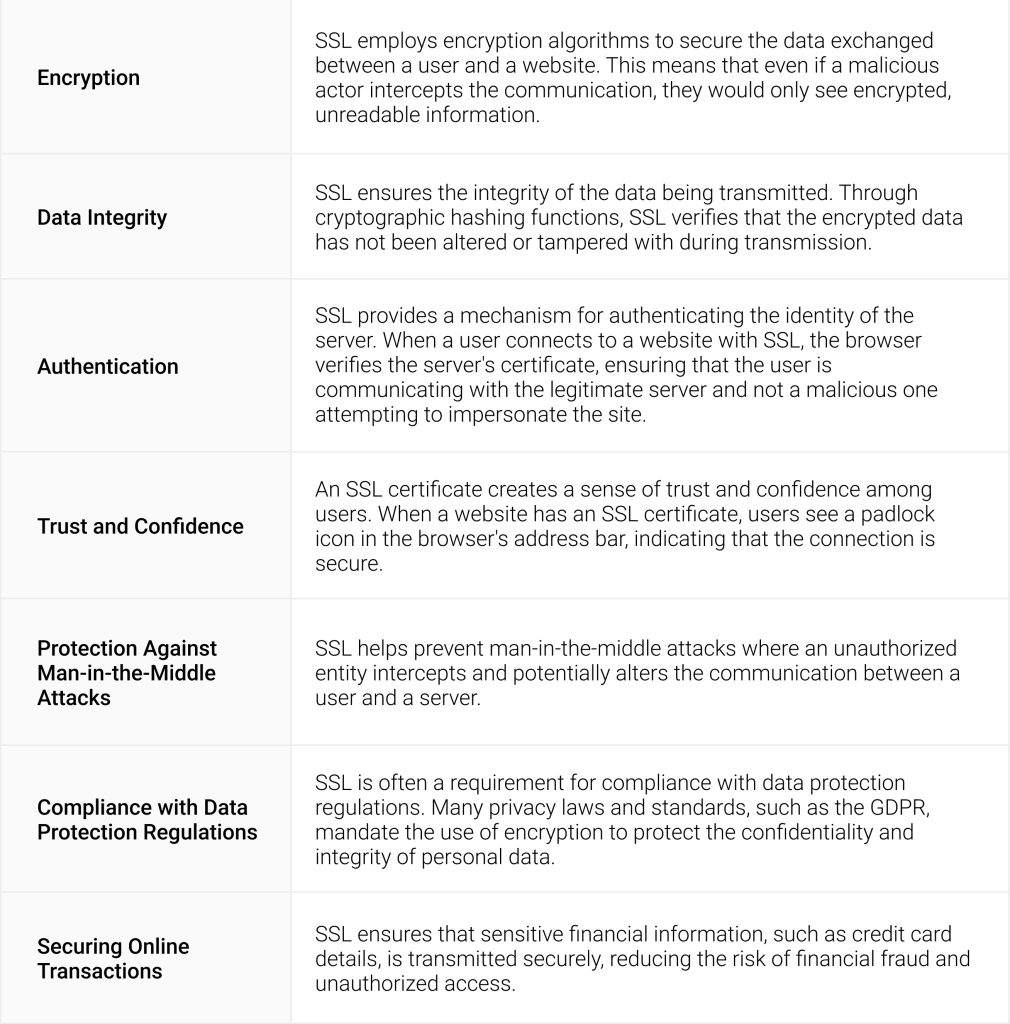
What Is The Role of SSL in Data Security?
SSL plays a crucial role in ensuring data security on the internet. It encrypts the communication between a user’s web browser and the server hosting a website. This encryption is essential for protecting sensitive information such as personal data, login credentials, and financial transactions from unauthorized access and potential cyber threats. Some critical aspects of SSL in data security include:
How Does SSL Work?
Secure data exchange via SSL begins with an ‘SSL Handshake’, where the user’s browser and server agree on the encryption. The server presents its public key and digital certificate, which the browser verifies through the Certificate Authority’s (CA) public key. Once confirmed, the browser generates a symmetric session key, encrypts it with the server’s public key, and transfers it back. Upon successful decryption by the server, an encrypted session is established.
How Do SSL Certificates Work?
An SSL certificate forms the backbone of SSL’s server authentication mechanism. An SSL certificate, a digital file containing the server’s public key and identifying data, validates a server’s identity. The browser checks SSL certificates issued by CAs after rigorous validation for validity, issuer, and server identity match. Post-verification, secure communication begins. Different certificate types offer varying validation levels; extended certificates are used for high-stake transactions.
SSL’s Core Components
Diving deeper into the specifics of SSL, let’s explore its fundamental components further to understand their distinctive roles and operations better:
Handshake Protocol
The Handshake Protocol initiates the secure communication between client and server. It agrees on the SSL connection parameters, including cipher suite selection, random value exchange for symmetric key generation, and identity verification through digital certificates. It’s also responsible for the safe exchange of the shared private key. This protocol is instrumental in creating a secure data exchange channel.
SSL Handshake Protocol Phases Source: geeksforgeeks.org
Record Protocol
Working at a higher layer, the SSL Record Protocol encompasses application data. It partitions data into manageable blocks, compresses, encrypts using the shared key, and applies a MAC for integrity checks. Upon receipt, it verifies, decrypts, decompresses, and delivers the data to the application layer, ensuring secure and efficient data transmission.
Change Cipher Spec Protocol
Often overlooked, the Change Cipher Spec Protocol is critical for SSL operation. It signifies the end of the handshake process and the beginning of secure data transfer, marking the transition from a ‘handshake state’ to an ‘encrypted state.’ It ensures a smooth and secure data transmission process. This protocol consists of a single message which is 1 byte in length.
Alert Protocol
The Alert Protocol communicates security issues between the server and client, sending warnings for potential problems—a system failure or an attempted breach. It differentiates between ‘warning’ and ‘fatal’ alerts, with fatal alerts leading to immediate disconnection. It comes into play when a server’s certificate isn’t authenticated, or a wrong MAC is detected. Each message in the alert protocol contains 2 bytes:
Types of SSL Certificates
SSL certificates can be classified into various types based on the level of domain validation and the number of domains or subdomains they secure. All SSL certificates play vital roles in online data security. The certificate choice should be determined by your website’s specific security needs, budget, and the customer trust you desire to instill. SSL certificates include:
1. Domain Validated SSL Certificates
DV certificates validate that the person applying for the certificate has the right to use the specific domain name. Although they provide encryption, they do not vet or display company information, making them less suitable for e-commerce or financial sites where customer trust is crucial.
2. Organization Validated SSL Certificates
An organization-validated SSL certificate provides a greater level of security than domain-validated certificates. The Certificate Authority (CA) performs a more rigorous vetting process, verifying the organization’s existence, physical address, domain ownership, and other details. These certificates display the verified company information, fostering trust among site visitors.
3. Extended Validation SSL Certificates
An EV SSL certificate offers the highest level of domain validation available. In addition to domain and company verification, the process involves checking the company’s operational and legal existence, making it the most thorough and time-consuming. The reward is the green address bar, which instantly signals that the site is extremely secure, thus boosting customer confidence.
4. Wildcard SSL Certificates
A Wildcard SSL certificate provides versatile protection, enabling users to secure limitless subdomains under a single certificate. For instance, a certificate for ‘***.example.com’ could secure ‘blog.example.com’, ‘shop.example.com’, etc. Despite its cost-effectiveness and efficiency, a potential risk lies in its blanket coverage; if one subdomain gets compromised, it may expose vulnerabilities in others. Hence, sustaining rigorous security practices while using Wildcard SSL certificates is crucial.
5. Single-Domain SSL Certificate
A single-domain SSL certificate is designed to secure a specific domain or subdomain on the internet, providing encryption for data exchanged between users and the web server associated with that particular domain.
6. Multi-Domain SSL certificates
A Multi-Domain SSL certificate, or a Unified Communications Certificate (UCC) or Subject Alternative Name (SAN) certificate, is a type of SSL/TLS certificate that allows multiple domain names to be secured with a single certificate. A multi-domain certificate is particularly useful for organizations or individuals managing multiple websites or services under different domain names.
7. Unified Communications Certificates
Specifically designed for Microsoft Exchange and Office Communication servers, these certificates are similar to Multi-Domain SSL certificates but are tailored to secure all server-hosted communications.
How to Obtain an SSL Certificate
Certificate Authorities issue SSL certificates. To obtain one, you must generate a Certificate Signing Request (CSR) and submit it to a CA.
Validating an SSL Certificate
An SSL certificate is validated by checking its digital signature with the public key of its issuing CA. This ensures the certificate is authentic and trustworthy.
SSL and Encryption
Source: websourcebd.com
Encryption is a fundamental component of SSL/TLS. It involves transforming data into a secure format using an algorithm and a cryptographic key.
Symmetric and Asymmetric Encryption in SSL
SSL uses a combination of symmetric and asymmetric encryption. Asymmetric encryption is used during the SSL handshake to establish a secure connection. Symmetric encryption is then used for the remainder of the session for efficiency.
SSL Encryption Algorithms
SSL and later TLS use encryption algorithms, including DES, 3DES, RC4, AES, and ChaCha20-Poly1305. The choice of algorithm depends on the capabilities of the webserver and the client and security considerations.
Importance of Key Exchange in SSL
Key exchange in SSL is critical for establishing a private key for symmetric encryption. This exchange must be performed securely to prevent man-in-the-middle attacks. As such, SSL often uses secure key exchange algorithms like RSA, Diffie-Hellman, or Elliptic Curve Diffie-Hellman.
SSL Authentication
Authentication in SSL/TLS involves verifying the identities of the communicating entities, typically a client (such as a web browser) and a server. Here are the key aspects of SSL/TLS authentication:
1. Server Authentication:
Digital Certificates: The server presents a digital certificate during the SSL/TLS handshake. This certificate is issued by a trusted Certificate Authority (CA) and contains the server’s public key.
Certificate Verification: The client verifies the server’s certificate to ensure it is valid and issued by a trusted CA. This process helps establish the authenticity of the server.
2. Client Authentication:
Mutual SSL/TLS: While server authentication is standard, SSL/TLS also supports mutual authentication, where the client presents its own certificate to the server.
Use Cases: Mutual authentication is commonly used in scenarios where the client and server must verify each other’s identity, such as in specific financial or sensitive data exchange applications.
3. SSL/TLS Handshake Process:
Hello Messages: The handshake begins with a series of “hello” messages between the client and server, where they agree on parameters for the secure connection.
Key Exchange: During this phase, the server’s certificate is presented, and the parties negotiate encryption keys. The client may also present its certificate in mutual authentication scenarios.
4. Certificate Authorities:
Trusted Third Parties: CAs play a crucial role in SSL authentication by acting as trusted third parties. Browsers and operating systems come preloaded with a list of root CA certificates that are considered inherently trustworthy.
Chain of Trust: The server’s certificate is verified by checking its signature against the public key of the CA that issued it. This process forms a chain of trust, linking the server’s certificate to a root CA.
5. Revocation Checks:
CRLs and OCSP: To enhance security, clients may check the Certificate Revocation List (CRL) or use the Online Certificate Status Protocol (OCSP) to ensure that a server’s certificate has not been revoked since issuance.
6. SSL Indicators:
Browser Indicators: A secure and encrypted connection is often indicated by a padlock icon in the address bar and “https://” in the URL. These indicators signal that the communication is encrypted and the server’s identity has been verified.
Source: znetlive.com
Configuring SSL on Your Web Server
Setting up SSL on your web server involves several intricate steps. First, you need to generate a certificate signing request (CSR) containing your server’s public key and your organization’s specific details. After this, you must choose a Certificate Authority and submit the CSR to obtain an SSL certificate. Once you receive the certificate, install it on your server, then modify your website’s settings to redirect HTTP traffic to HTTPS. Additionally, you’ll need to maintain and renew the SSL certificate regularly while routinely checking for potential vulnerabilities. Each server type has a distinct configuration process; hence, following the best practices specific to your web server platform is crucial.
SSL and Email Security
SSL also secures email communications. It encrypts the data sent via SMTP (for sending mail), POP3 (for retrieving mail from a personal server), and IMAP (for retrieving mail from a remote server), ensuring the privacy of email content.
How SSL Email Encryption Works
SSL email encryption works similarly to how it protects web data. The email server and client establish a secure SSL/TLS connection, through which emails are sent and received encrypted.
SSL vs. TLS in Email Security
Both SSL and TLS can be used to secure email communications. However, TLS is more secure due to its advanced features and is more commonly used. Further, TLS is backward-compatible with SSL, meaning a TLS client can communicate with an SSL server and vice versa.
The Power of JoinNow Connector PKI by SecureW2
Certificate-based security isn’t limited to just the web. SecureW2’s JoinNow Connector, a private Cloud PKI solution, paves a new frontier in digital certificate implementation, ensuring top-tier security in private network authentication. The same kind of certificate-driven authentication that underlies web security can provide security for cloud applications, VPN, and even your wired and wireless networks.
SecureW2 facilitates the seamless management of certificates by offering a centralized platform for digital certificate generation and management. This means that organizations can eliminate the need for additional infrastructure or the hassle of management or maintenance burden for their private SSL operations. All the keys are stored in HSM without any additional cost, ensuring the keys are never compromised.
Our solutions also factor in device onboarding. We provide an automated enrollment API for managed devices and a self-service onboarding platform for unmanaged devices and BYODs that need to be configured for certificate-based authentication.
Contact us today to learn more about how we can assist you in improving your organization’s security posture.
