Key Points
- In modern hybrid and remote work environments, organizations face a significant security risk from unmanaged or non-compliant devices.
- Device Trust is the solution, which relies on a multi-layered approach to verify that a device meets specific security standards before being granted network access
- This is primarily established by using an MDM, such as Microsoft Intune, to enforce compliance policies and issuing non-exportable digital certificates to provide a unique, verifiable identity for each device.
- SecureW2 enhances this approach by providing a managed PKI platform that integrates directly with Intune.
Imagine you are a parent working from home, and your child accidentally spills a drink on your work laptop. You have an approaching work deadline, so you finish it on your home computer that your child occasionally uses. What if your home computer has malware you are unaware of? How could it impact your work’s data and applications?
This is where device trust comes into play.
What is Device Trust?
Device trust verifies if the device should be trusted before granting anyone to access sensitive data like enterprise applications or resources. Trust often requires an MDM, such as Intune or Jamf, that can enforce policies and inform other systems that a device is trustworthy and compliant with security policies. Digital certificates play an essential role in creating device trust. Certificates are specific to each device and cannot be readily stolen or shared. When a device uses a specific certificate to access your network or services, you can be confident that it’s a legitimate device, not an unauthorized entity attempting to exploit its credentials.
Microsoft Intune issues certificates that allow only trusted devices to access critical resources.
SecureW2 integrates directly with Intune to verify that a device is enrolled in at the moment of certificate issuance, blocking any attempts to exploit the SCEP URL for unauthorized certificate requests. This additional layer of verification ensures that only genuine and managed devices have access to your workplace environment.
Why is Device Trust Important?

How SecureW2 Enhances Device Trust
SecureW2 works with Microsoft Intune by providing strong certificate-based authentication. It guarantees that only trusted devices and only authorized users can access corporate resources.
Certificate-Based Authentication
SecureW2 uses Public Key Infrastructure (PKI) certificates instead of password authentication. This assigns a certificate to a specific device and user, guaranteeing that access requests come from trustworthy sources. Certificates minimize the risks associated with stolen credentials, significantly reducing the likelihood of credential-based breaches.
Integration with Intune for Enhanced Security
SecureW2 integrates with Intune to automate certificate issuance, enrollment, and lifecycle management. It improves compliance procedures by securely provisioning certificates for Wi-Fi, VPNs, and business-critical apps. This connection enables organizations to link certificate-based authentication with Intune’s Granular Access controls.
Tailored Solutions for Modern Workforces
SecureW2 is designed to meet the challenges of hybrid work environments and BYOD initiatives. It supports self-enrollment for unmanaged devices, allowing users to set up them with minimum IT intervention. SecureW2 works with Intune’s device compliance regulations, ensuring secure access management for various device types.
The Role of Microsoft Intune in Establishing Device Trust
Microsoft Intune is an MDM technology critical in building device trust inside an organization. Intune guarantees that only secure devices may access company resources by controlling personal devices and enforcing compliance requirements.
Device Management and Compliance
Intune allows administrators to create and enforce compliance standards tailored to their organization’s security needs. These policies guarantee that mobile devices meet critical security standards like encryption, password enforcement, and the latest software patches. Intune applies these compliance rules based on device ownership (BYOD or corporate-owned), kind, or department, enhancing both organizational and device security.
Enable Device Trust for Secure Access
Intune works with Microsoft Entra (formerly Azure Active Directory) to enforce Conditional Access Policies. These policies restrict access to programs and resources unless the device is marked as compliant. For example, users can only access Microsoft 365 apps if their personal devices meet specified encryption and security health standards. This approach strengthens security while supporting productivity.
Streamlining Hybrid Work Environments.
Intune simplifies managing many devices in hybrid or remote work environments while ensuring consistent security across corporate and personal endpoints. It is the foundation of device trust in todaysIT environments..
Streamlining Device Trust with Intune and SecureW2 Certificate Integration
Setting up device trust in Microsoft Intune with SecureW2 enables safe, certificate-based authentication for compatible devices. This streamlines certificate management by automating procedures like issue, renewal, and revocation, lowering administrative costs and increasing security.
To get started, you must create an app in Entra ID, set up a SCEP Certificate Authority (CA), establish the CA partner in Intune, and implement suitable policies. These configurations guarantee that only managed and compliant devices can access company resources.
For complete, step-by-step instructions, see the SecureW2 Intune Integration Guide. This strategy adheres to zero trust security, improving your organization’s and device’s security posture.
How Intune Integrates with SecureW2’s Device Trust Solution
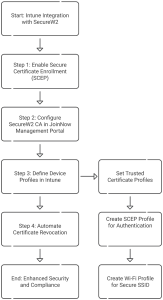
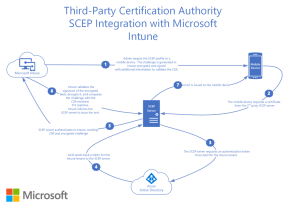
Microsoft Intune integrates with SecureW2 to streamline certificate management and ensure security for managed devices. This integration uses SecureW2’s third-party CA and the Simple Certificate Enrolment Protocol (SCEP) to generate and auto-enroll certificates for Intune-managed devices.
- Enabling Secure Certificate Enrolment with SCEP
Organizations can configure the SCEP protocol to enable Intune-enrolled devices to request and receive digital certificates automatically. These certificates are critical for authenticating devices and controlling access to resources like Wi-Fi networks, VPNs, and workplace applications. Administrators can use SecureW2’s CA in the JoinNow Management Portal to streamline certificate issuance, renewals, and revocations.
- Configuring device profiles in Intune.
To ensure secure connectivity, administrators must define and assign specific device profiles inside Intune, which include:
- Trusted Certificate Profiles: Deploy certificates for SecureW2’s Root CA, Issuing CA, and RADIUS Server Root CA to ensure devices trust the SecureW2 infrastructure for user authentication.
- SCEP Profile: Enable devices to request certificates dynamically through SecureW2’s SCEP gateway for seamless authentication.
- Wi-Fi Profile: Automates the creation of secure SSID setups using user-based certificates.
- Automated Revocation for Device Lifecycle Management.
When a device is moved into a particular smart/static group in Intune, SecureW2’s integration automatically revokes its associated certificates through the JoinNow Management Portal.
By merging Microsoft Intune’s device management features with SecureW2’s certificate-based authentication, businesses can enforce device trust, improve security, and simplify compliance across various contexts.
Advantages of SecureW2 + Intune for Device Trust
Our platform complements existing tools, such as Microsoft Intune, allowing organizations to expedite certificate issuance, enforce device trust, and trigger additional security measures without reworking their existing infrastructure. Here’s what makes our integration stand out:
Improved Device Trust with Verified Enrollment
SecureW2 guarantees that only devices validated as compliant and managed within Intune are eligible for certificate enrolment. This additional layer of device trust process goes beyond standard tests, to ensure stronger security and prevent unauthorized access.
Automated Certificate Revocation
Our technology communicates with Intune regularly to detect devices reported as non-compliant or removed from active supervision. Certificates for these devices are automatically revoked, significantly reducing the probability of ongoing access issues.
Vendor-Neutral Flexibility
SecureW2 supports various device ecosystems, allowing organizations that manage devices across several MDM platforms to operate smoothly. This flexibility guarantees that certificate-based security is uniform across all device management solutions.
Securing the Future with Device Trust
Integrating Microsoft Intune with SecureW2 automates the digital certificate lifecycle, ensuring only compliant, managed devices can access corporate resources. Using SecureW2’s SCEP gateway, organizations can enforce rigorous compliance requirements, streamline enrollment, and automate certificate revocation for non-compliant or removed devices. Trusted certificate profiles and SCEP settings offer a scalable way to deliver certificates across many platforms.
Ready to improve your device trust strategy? Schedule a demo to learn how SecureW2’s modern device trust solution can enhance your organization’s security architecture.
