Key Points
- Traditional password-based Wi-Fi security is vulnerable to credential theft and unauthorized access
- Wi-Fi certificate authentication replaces passwords with cryptographic Digital Certificates to safeguard network access.
- Wi-Fi certificate authentication validates server certificates using a RADIUS server and PKI to secure connections
An IBM study says that stolen or compromised passwords are the most common reason for a data breach. Let’s be honest, usernames and passwords aren’t a good way to prove who you are anymore, especially for large companies.
With the risk of a potentially misconfigured “Bring your own device” (BYOD) accessing professional networks and the growing threat of rogue machines, many people in IT are wondering how they can ensure that only authorized users and devices can connect to an organization’s networks and systems. Digital certificates are helpful because both people and machines can use them. This article goes into detail about certificate-based authentication and explains the certificate lifecycle process, from the request for authentication to the certificate issue. It aims to clarify the complexity of configuration, security benefits, and easy access management for this advanced authentication technique.
Introduction to Certificate-Based Authentication
At its most basic, certificate-based authentication (CBA) uses a digital certificate based on cryptography to verify a person’s identity, computer, or other device before letting them access a network or resource. In contrast to authentication solutions specifically designed for human users, such as one-time passwords (OTP) and biometrics, certificate-based authentication applies to all endpoints, encompassing Internet of Things (IoT) classified devices, personal computers, servers, and electronic passports.
CBA is a safer option than the usual username and password. It can also be used with conventional methods for stronger user authentication that isn’t vulnerable to scams. The digital certificate and private key are stored on a person’s device or computer. This lets the user’s browser or client instantly log into different systems. It only requires a little extra work from the user, as the certificate can be authenticated automatically.
Understanding Public-Private Key Cryptography
Digital certificates are built on the concept of key pairs. A key is a piece of information used in cryptography to scramble data so it looks random. This is usually a long number or a line of numbers and letters. When unprotected data, known as plaintext, is fed into a cryptographic algorithm with a key, it emerges as random data. However, anyone with the right key can turn the information into plaintext.
In public key cryptography, two keys are used to secure data. One is made public so anyone can use it; the other key is a “private key.” The private key is the only way to recover data protected by the public key. Asymmetric cryptography is another name for public key cryptography. This is because it uses two keys instead of one. These keys are commonly used for TLS/SSL, which makes HTTPS possible.
One could see the public key as an unlocked device readily available to anyone who wants to transfer a confidential message. The private key, however, is unique to this lock and possessed solely by the designated recipient. The user’s device generates an authentication request consisting of both a public and private key. The public key is then publicly disseminated, serving as a signifier for any encrypted correspondence.

This is when digital certificates come into play. They’re issued by a reputable Certificate Authority (CA), which establishes a link between the user’s public key and their identity. A digital certificate functions as an electronic passport, certifying the credibility of both the user and the public key. The recipient can validate the sender’s authenticity when an authentication request is received by cross-referencing the digital certificate with the trusted CA database.
Configuring Certificates on Devices
Managed Devices
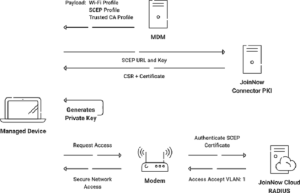
In managed settings, providing seamless certificate distribution is critical for retaining centralized control. The most common technique is to use mobile device management (MDM) systems. This means the enrollment process is assisted by existing protocols, such as the Simple Certificate Enrollment Protocol (SCEP).
MDM systems are crucial in this process since they automate certificate enrollment for managed devices. Organizations can develop a faster workflow by utilizing protocols such as SCEP, which allows devices to request and receive digital certificates securely. This solution simplifies certificate distribution while ensuring that the procedure is efficient and suited to the individual security requirements of managed devices. The integrity of the communication channel is protected due to this proficient approach, meaning organizations benefit from a safe and centralized certificate enrollment procedure.
BYODs
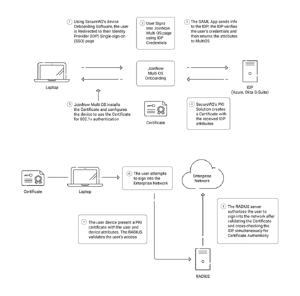
Bring Your Own Device (BYOD) scenarios introduce greater complexity to the technical environment. It involves many devices with diverse configurations, operating systems, and functionalities. In response, organizations adopt technological measures, including utilizing self-enrollment portals and email-based certificate distribution.
JoinNow MultiOS from SecureW2 revolutionizes BYOD security by offering a simple, self-service onboarding solution for unmanaged devices. This simple solution minimizes the possibility of end-user misconfiguration, a typical issue in BYOD situations. End-users can easily set up their devices with JoinNow MultiOS with just a few clicks. It assures proper configurations the first time and compatibility with all major operating systems. The solution’s features include pushing unique network profiles concurrently and enrolling certificates. This allows for safe and hassle-free authentication.
Certificate-Based RADIUS Authentication and 802.1X
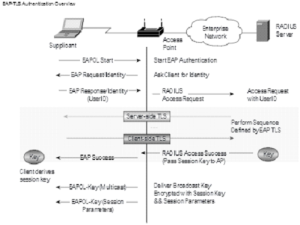
The main difference between 802.1X and the basic pre-shared key Wi-Fi many people have at home is the addition of a Remote Authentication Dial-In User Service (RADIUS) server that allows individuals to access the network with their own unique credentials or certificates. When it comes to 802.1X authentication, combining digital certificates and a RADIUS server strengthens the authentication procedure and guarantees a reliable and secure communication channel.
This 802.1X authentication is an IEEE standard that manages port-based network access controls, emphasizing the significance of authentication for network-connected devices. Certificates elevate this process by offering a more secure and dependable way of authenticating compared to older methods. Extending this conversation to EAP-TLS, a sophisticated EAP architectural extension, Transport Layer Security (TLS), is added as an additional layer of security. In this case, the RADIUS server configuration includes carefully selecting and defining cryptographic methods to provide a safe authentication procedure.
In this configuration, the RADIUS server enables authentication communications between the client and the authentication server. The effectiveness of 802.1X authentication is based on the dynamic allocation of cryptographic keys. These keys will then strengthen the security of the communication channel. Certificates will also provide an even more robust authentication mechanism when combined with a RADIUS server.
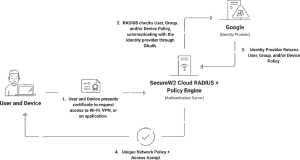
When a user attempts to authenticate, the RADIUS server runs several checks on the certificate issued. It examines the Certificate Revocation List (CRL) to see whether the certificate has expired or been revoked. The RADIUS server decides whether to give or refuse access based on these tests. SecureW2’s Cloud RADIUS goes above and beyond by including the Identity Lookup feature. This feature consults the Identity Provider (IDP) during authentication, assuring the execution of the most recent rules connected to the user’s or device’s information in the IDP, in addition to expiry and CRL checks. This comprehensive technique improves security authentication processes by adding an extra layer of protection against potential security risks.
How Real-Time Attribute Lookup Works
Real-time attribute lookup relies on strong protocols to retrieve and update attributes efficiently. Organizations frequently use the RADIUS and Lightweight Directory Access Protocol (LDAP). RADIUS ensures efficient attribute retrieval by allowing smooth communication between the network access server and the authentication server. As a directory service protocol, LDAP enables the storage and retrieval of attribute data in a hierarchical structure.
Organizations can create a dynamic and responsive access control environment by integrating these protocols into their authentication infrastructure. This technological solution guarantees that changes in user roles, device statuses, or any other attribute are detected and updated in access policies as soon as possible.
SecureW2’s Cloud RADIUS Real-time lookup capability is a notable addition to real-time attribute lookup capabilities. This feature is intended to elevate access control to new heights by providing various capabilities tailored to the needs of current cybersecurity landscapes. It enables organizations to enforce access controls by dynamically searching user attributes against common identity providers (IDPs) such as Azure, Okta, and G-Suite in real time. This guarantees that access rights are consistent with the most recent user information.
Adding Server Certificates Validation
Implementing server certificate validation is a significant step in strengthening network security. Server certificates received from credible Certificate Authorities (CAs) are critical in authenticating the RADIUS server’s identity. A server certificate assures that the server is genuine and not a possible threat, in addition to enabling a secure communication channel.
The significance of server certificate validation cannot be underemphasized. It is a strong safeguard against possible man-in-the-middle attacks and assures that the RADIUS server authenticates devices in a secure environment. This concept extends beyond RADIUS authentication. In general, server certificates are essential for web servers to protect connections by encrypting data in transit. Administrators must carefully set up the RADIUS server, providing server certificates received from a trustworthy CA and creating a safe chain of trust. This caution in server certificate validation adds significantly to the overall security posture, protecting against unauthorized access and malicious actors attempting to undermine the authentication process.
Managing Access with Certificate-Based Authentication
Authorization Based on Attributes
At the heart of access management is attribute-based authorization, a granular approach that allows organizations to specify access controls accurately. Attribute Value Pairs (AVPs) are crucial in this procedure since they serve as the language used to transfer attributes between the authentication server and the network access server.
AVPs contain information such as user roles, device categories, and other contextual characteristics generated from the user’s digital certificate in a certificate-based authentication environment. This extensive information helps administrators customize access policies, ensuring that users are permitted access that is appropriate for their responsibilities and the security posture of their devices.
Consider scenarios in which specific user groups are provided access to different Virtual Local Area Networks (VLANs) or cloud apps, all handled seamlessly via attribute-based authorization. Organizations can boost access control in a way that perfectly fits their specific security and operational objectives; they can then leverage what’s provided by certificate-based authentication and AVPs. This method strengthens security and simplifies administrative tasks by guaranteeing that access restrictions change in response to the landscape of user roles and device features.
Certificate Revocation Methods
A certificate-based authentication system’s security depends on the prompt revocation of compromised or invalidated certificates. Technical methods of certificate revocation, such as Certificate Revocation Lists (CRLs) and the Online Certificate Status Protocol (OCSP), are critical to the integrity of the authentication infrastructure.
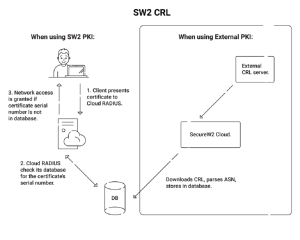
CRLs are a tried-and-tested way to maintain a record of revoked certificates. This list is updated regularly and given to network entities, such as RADIUS servers. It prevents the RADIUS server from having to scan an increasingly lengthy CRL as more certificates are revoked over time. An abbreviated CRL of the most recently revoked certificates called a delta CRL, is provided to the RADIUS periodically.
By letting the client check the validity of a certificate directly with the issuing CA, OCSP provides real-time certificate validation. The technological execution of these approaches guarantees that compromised certificates are quickly recognized and that possible attackers are denied access.
Why Use Certificate-Based Authentication?
Enhanced Security
Traditional username and password authentication methods are among the least secure. These passwords are easy to guess and not stored securely. For example, they’re commonly found on sticky notes. Certificate-based authentication is a considerably more secure method of authentication that does not use insecure passwords. By removing passwords, hackers are less likely to conduct phishing or brute-force attacks.
Streamlined Authentication
Users may be authenticated using certificates without memorizing several username and password combinations. When there are a lot of passwords to remember, users frequently spend a lot of time guessing and changing them. Certificate-based authentication reduces user friction while enhancing workforce productivity.
Ease of Deployment
Unlike other authentication techniques, such as one-time passwords (OTP) or biometrics, certificates are kept locally on the device and may be applied without additional hardware. Certificate-based authentication also simplifies access control. Most systems include a cloud management platform that enables administrators to quickly issue certificates to recruits, renew certificates, and revoke certificates when they are no longer required.
Securing Networks with SecureW2’s Managed PKI and Cloud RADIUS
SecureW2’s innovative approach to network security combines a managed Public Key Infrastructure (PKI) and Cloud RADIUS, revolutionizing the authentication environment. As organizations move away from password-based identification, SecureW2 offers a solid alternative, such as an all-encompassing PKI solution. Managed PKI securely authenticates users via digital certificates and ensures a simplified and centralized certificate lifecycle management procedure.
Organizations can benefit from a managed PKI while maximizing its security using Cloud RADIUS with modern, password-less authentication. Whether you’re a school, a business, or an organization, SecureW2 enables you to improve network security, simplify authentication, and embrace a future where passwords are no longer the weak link. Contact us now to learn how SecureW2’s Managed PKI and Cloud RADIUS can improve network security and reinvent the authentication experience.