Key Points
- MITM is a common cyber threat where an attacker secretly intercepts and relays communications between two parties, often by creating a rogue access point to exploit the channel.
- EAP-TLS is the most effective protocol for eliminating MITM attacks because it uses mutual certificate validation between the client and server, removing the need to send vulnerable credentials over the air.
- SecureW2’s Managed PKI simplifies certificate deployment across all devices, automates 802.1X onboarding, ensuring full protection against MITM attacks while reducing admin workload.
Man-in-the-middle attacks (MITM) or on-path attacks are becoming common and complex. Organizations are putting in a lot of effort to mitigate these risks to no avail. Phishing kits are freely available, enabling on-path attackers to utilize tools to launch an MITM attack. They steal MFA tokens to attack browser sessions, user credentials, or cookies, calling for more robust authentication, like phishing-resistant digital certificates that can’t be stolen or duplicated.
Network administrators must also be aware of securing their LAN network to prevent layer attacks like MITM and secure their network effectively.
What is a Man-in-the-Middle Attack?
A typical cyber attack tactic, the MITM allows an on-path attacker to listen to communication between targeting parties.
Here, an attacker puts himself between a user and a server so that all conversations travel through him. The attacker can also play both sides, stealing the information a user sends to a server (such as login credentials, account details, and credit card numbers) and sending corrupted packets (such as malware or HTTP requests in a DDoS attack) to an innocent third party.
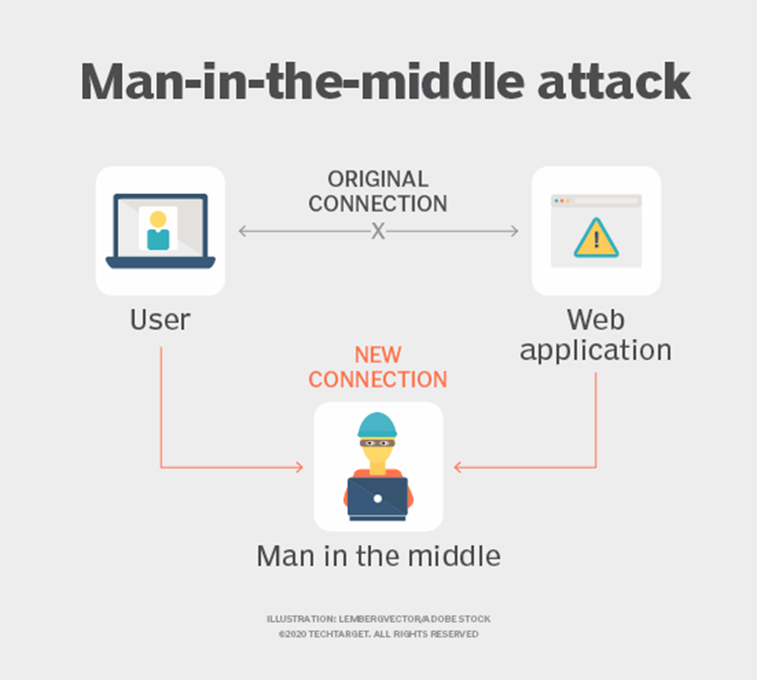
Image Courtesy: Techtarget.com
An impostor or man-in-the-middle targets online sites requiring secure authentication through a public and private key.
Common Types of Man-in-the-middle Attack
Though the concept of MITM remains uniform throughout, the execution mode varies. A description of the various types of MITM attacks can be found here:
- IP Spoofing
- ARP Spoofing
- Session hijacking
- Rogue Access Points
- DNS Spoofing
- HTPPS Spoofing
- Man-in-the-browser attacks
IP Spoofing
IP spoofing creates Internet Protocol (IP) packets with a modified source address. The modified source address helps hide the sender’s identity and impersonate another device. Bad actors use this technique to invoke denial of service (DDoS) attacks.
An IP packet contains a header before the body with all the routing information and source address. The standard packet contains the sender’s IP address, but a spoofed packet will have a forged source address. An attacker can spoof the IP of the user and server to snoop between to and fro communication.
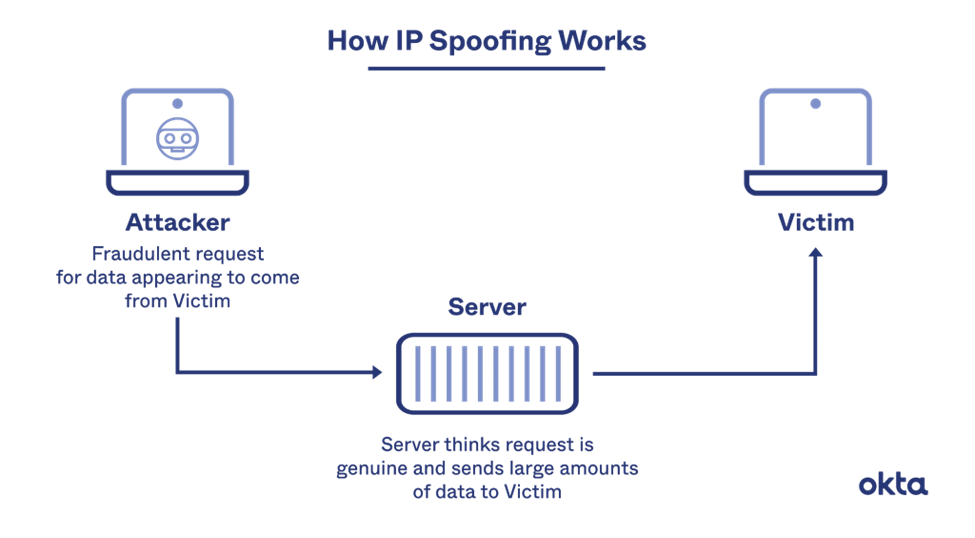
Image Courtesy: Okta
Address Resolution Protocol (ARP) Spoofing
Address Resolution Protocol (ARP) helps network communication travel to a device on a network. ARP converts the IP to a Media Access Control (MAC) address and the other way around. A device uses ARP to speak to the router or a gateway to connect to the internet.
A forged ARP message allows the attacker to use his MAC address to steal cookies and intercept any traffic between the user and server. The ARP protocol does not verify the integrity of an ARP request, making it a weak link and opening the doors to ARP attacks.
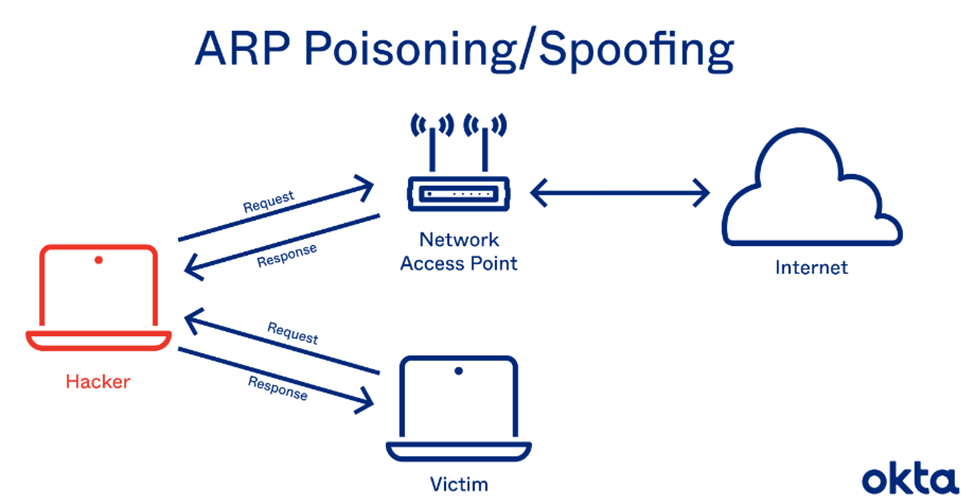
Image Courtesy: Okta
Session Hijacking
A TCP session hijacking on a user session takes place over a protected network when authentication is typically done at the start of a session. An attacker uses a sniffer to perceive the device’s communication and snoop into the data transmitted between the server and the device. Some common ways of session hijacking are
Packet sniffing:
Packet sniffing involves capturing data across computer networks. Hackers use it to gather information on activities over a network, like sending and receiving emails, the subject and contents of emails, site sessions, and download history. They can also intercept sensitive information like passwords and credit card numbers and misuse them.
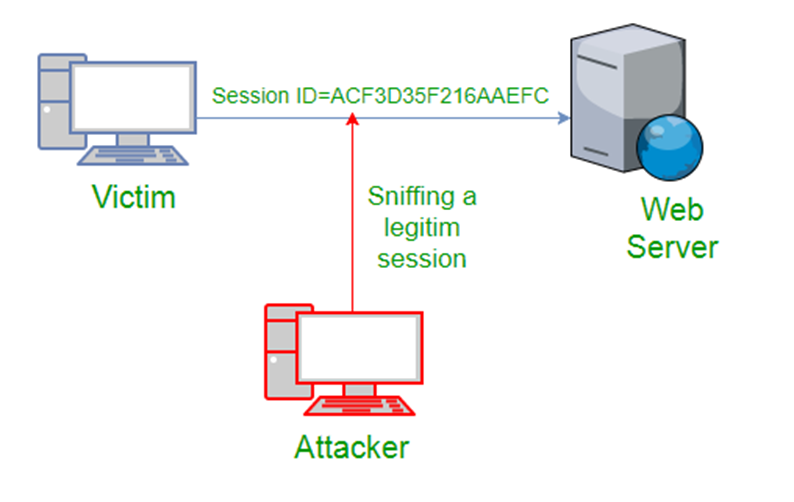
Image Courtesy: Geekforgeeks.com
XSS Attack (Cross-Site Scripts)
Using Javascript, an attacker can intercept a victim’s session ID with an XSS attack. The attacker can then send a malicious Javascript to the victim, and if the victim runs the script, the attacker can gain full access to his data.
Rogue Access Points:
Any device with wireless cards tries to auto-connect to an access point with the strongest signal. This allows attackers to set their access points so devices are tricked into joining malicious connections with those malicious access points. If a victim joins an attacker’s network, his session can be manipulated.
A Rogue Access point is elementary because an attacker only needs proximity and nothing else to access a user’s device.
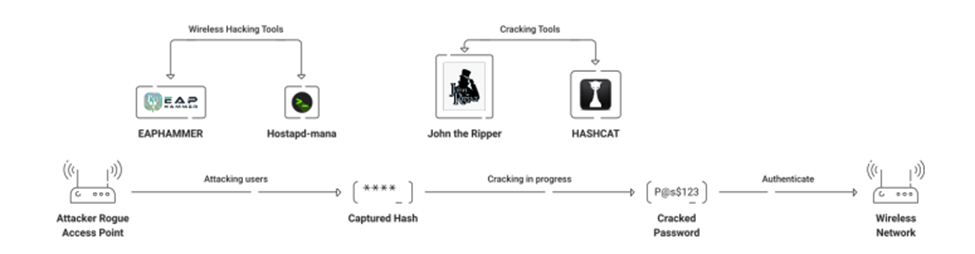
DNS Spoofing
The Domain Name System acts as an index for the internet. It is used to regulate websites all over the globe. In a DNS Spoofing attack, an attacker uses a Domain Name System (DNS) and redirects a user to a fake website that looks legitimate. Once a user goes to a fraudulent page, he enters his credentials into the page visible to the attacker, who can take advantage of the information.
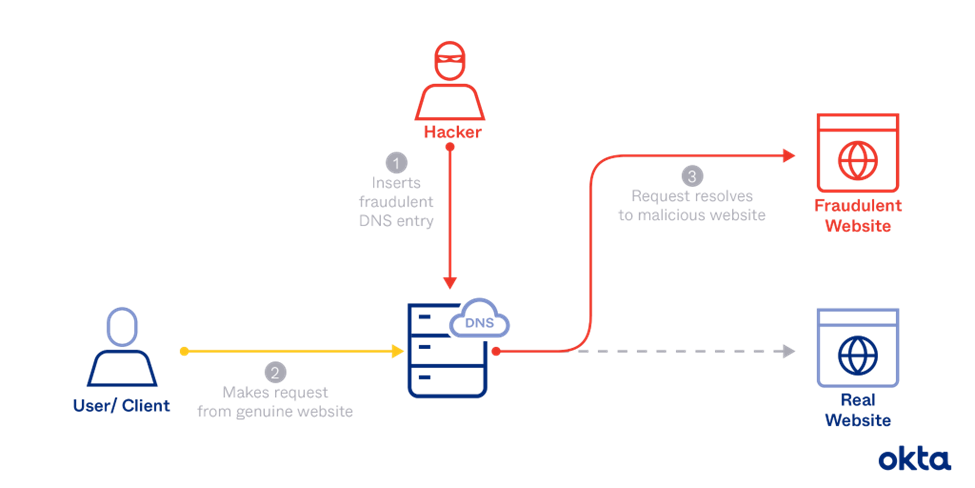
Image Courtesy: Okta
HTTPS Spoofing
A standard method to ensure that sites are DNS spoof-proof is to use HTTPS instead of HTTP. An HTTPS uses TLS (SSL) to encrypt any HTTP request, providing more security than an HTTP. An SSL certificate protects the web server’s identity, making it harder to spoof than an HTTP website.
However, an attacker can work around it by using non-ASCII characters like Turkish or Cyrillic that cannot be differentiated from other characters.
Man-in-the-browser Attacks
If an attacker has successfully installed a trojan horse on a user’s device, they can observe all online actions and exfiltrate that data to perform attacks. This attack is called a man-in-the-browser attack since it relates explicitly to web browser communications. As malware is the culprit here, a good antivirus can be the best man-in-the-middle attack prevention for this type of threat.
Four Ways To Prevent MITM Attacks in a Network
- Stronger Protocols for Access Points
- Using VPN to direct access to sensitive information
- Use HTTPS instead of HTTP for authentication
- Stronger Authentication
More robust security Protocols on Access Points
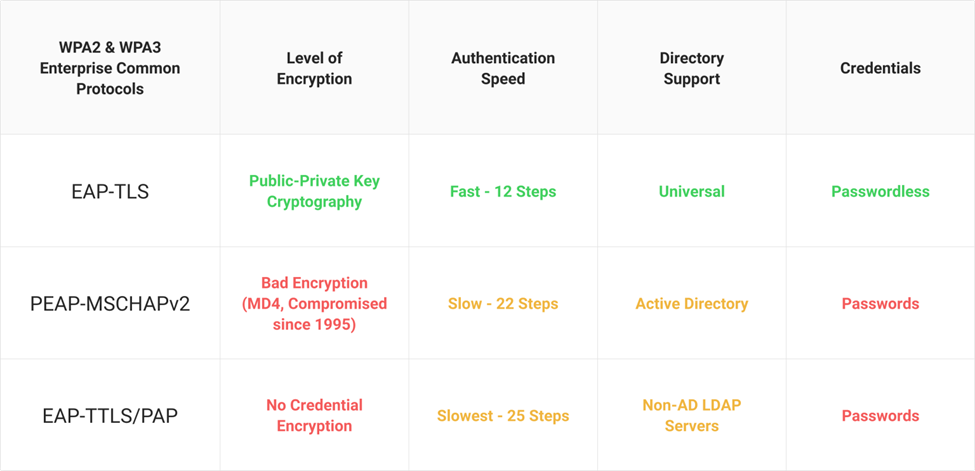
An access point communicates through a WEP key for encrypting and decrypting radio signals. When intruders get the required packets with the same WEP key, they can perform simple calculations to deduce the key and gain access to your network. WEP protocols like PEAP-MSCHAPv2 have been compromised since the 1990’s. But it is still one of the most popular Wi-Fi authentication protocols used by enterprises.
A more robust authentication system, like the Extensible Authentication Protocol (EAP), provides 802.1X security to protect your access points and limit access to the intended users and devices only.
VPN For Limited Access To Sensitive Information
Virtual Private Networks (VPNs) make a private and protected network connection through a public network. This helps hide your identity and encrypts network traffic. A VPN masks the IP address by a remote server operating system hosted by the VPN service provider.
A VPN helps you create a secure environment for your data in a LAN. VPN uses key-based encryption and makes a subnet for more secure data transmission in a network. An intruder will fail to decipher your private traffic, making it secure for any sensitive information.
Use HTTPS instead of HTTP for Authentication.
The Hypertext Transfer Protocol Secure (HTTPS) is a more secure form of the Hypertext Transfer Protocol (HTTP) that transmits data between a browser and a website. HTTPS is encrypted, secures confidential data, and protects sensitive information.
This prevents attacks like packet sniffing, as encrypted data will present as gibberish when an intruder tries to intercept data. A website should use HTTPS, force users to use browser plugins and connect with HTTPS on request.
Stronger Authentication with Digital Certificates For Network Security
Many cyberattacks stem from weak, stolen passwords, giving an attacker full network access. Robust authentication mechanisms, like digital certificates, are phishing-resistant. X. 509-based digital certificates use asymmetric cryptography and help a device prove its authority through the TLS protocol.
Digital certificates can be used in various layers to ensure a device is what it says it is and communication is secure, thus preventing MITM attacks.
Deploy Certificate-Based Authentication to Avoid MITM Attacks On Your Network
Password-based authentication continuously fails to protect the network from MITM and Layer 2 attacks in the age of cyber-engineered threats. A single layer of security is no longer a viable option to protect networks that run with sensitive data and applications transmitted by the minute every day. Security organizations like CISA have repeatedly urged organizations to adopt robust mechanisms like MFA and Two-factor authentication to secure their network.
However, digital certificates prevent unauthorized and malicious attacks on your network more effectively. Implementing digital certificates on your network may seem daunting, as it requires a PKI, which is known to be a complex setup. SecureW2’s Managed PKI is easy to set up and deploy in no time. Our Cloud RADIUS also provides passwordless authentication for your digital certificates and helps you onboard devices securely to your network.
Click here to learn more about implementing passwordless security for your organization.