
Windows Access Control: ACL, DACL, SACL, & ACE
Read this to know more about access control list and its components and the best way to secure your enterprise network.
Stay informed with expert insights, best practices, and the latest developments in network security, identity management, and SecureW2 product updates.

Read this to know more about access control list and its components and the best way to secure your enterprise network.
Securing home wireless networks has never been as important. An increase in remote work requires more people to handle sensitive business data at home. On top of this, our lives, in general, are becoming increasingly digital, conducted through services such ... Read More
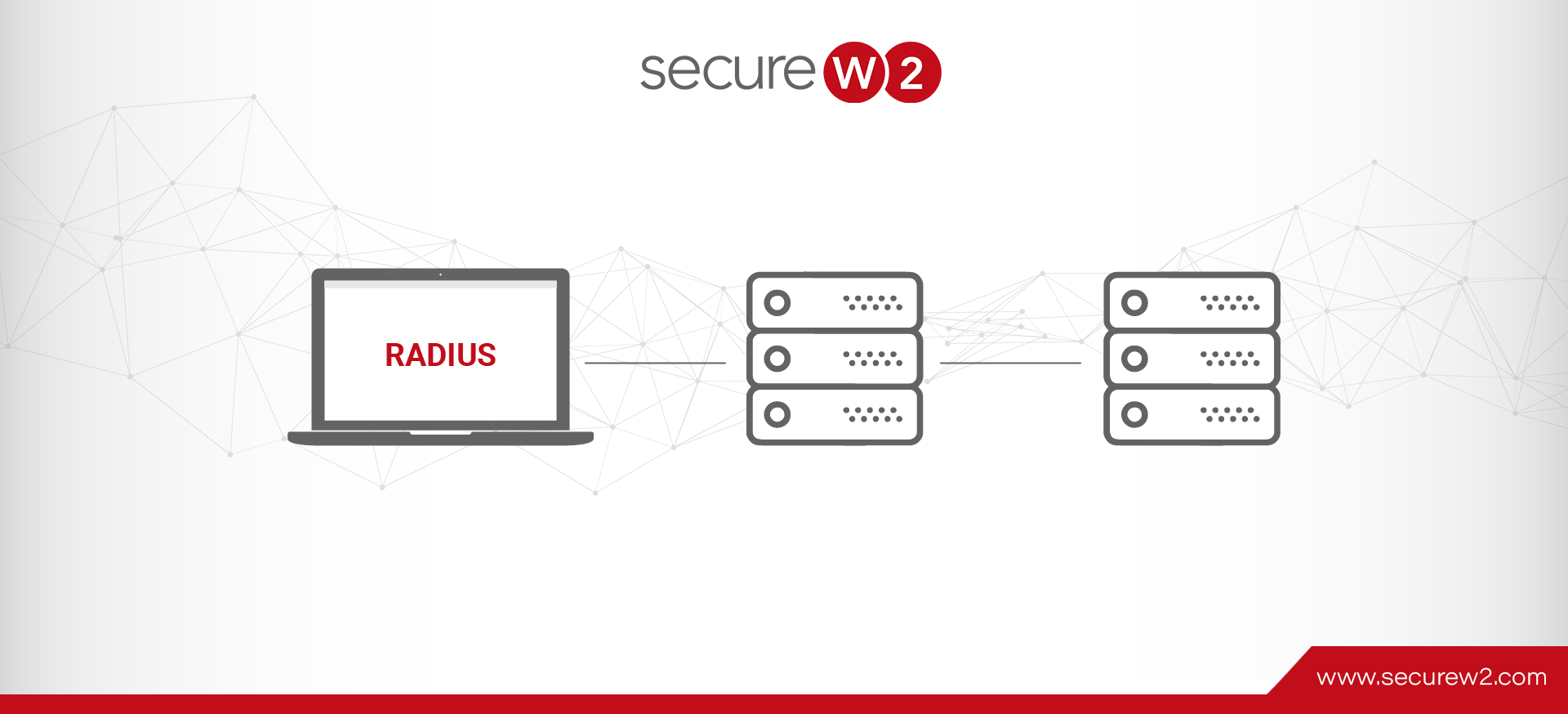
RADIUS is a crucial networking protocol best known for centralized authentication, authorization, and accounting (AAA) administration. The final “A” in AAA signifies accounting, a fundamental aspect of network management. Network Access Servers (NAS) typically function as clients and manage user ... Read More
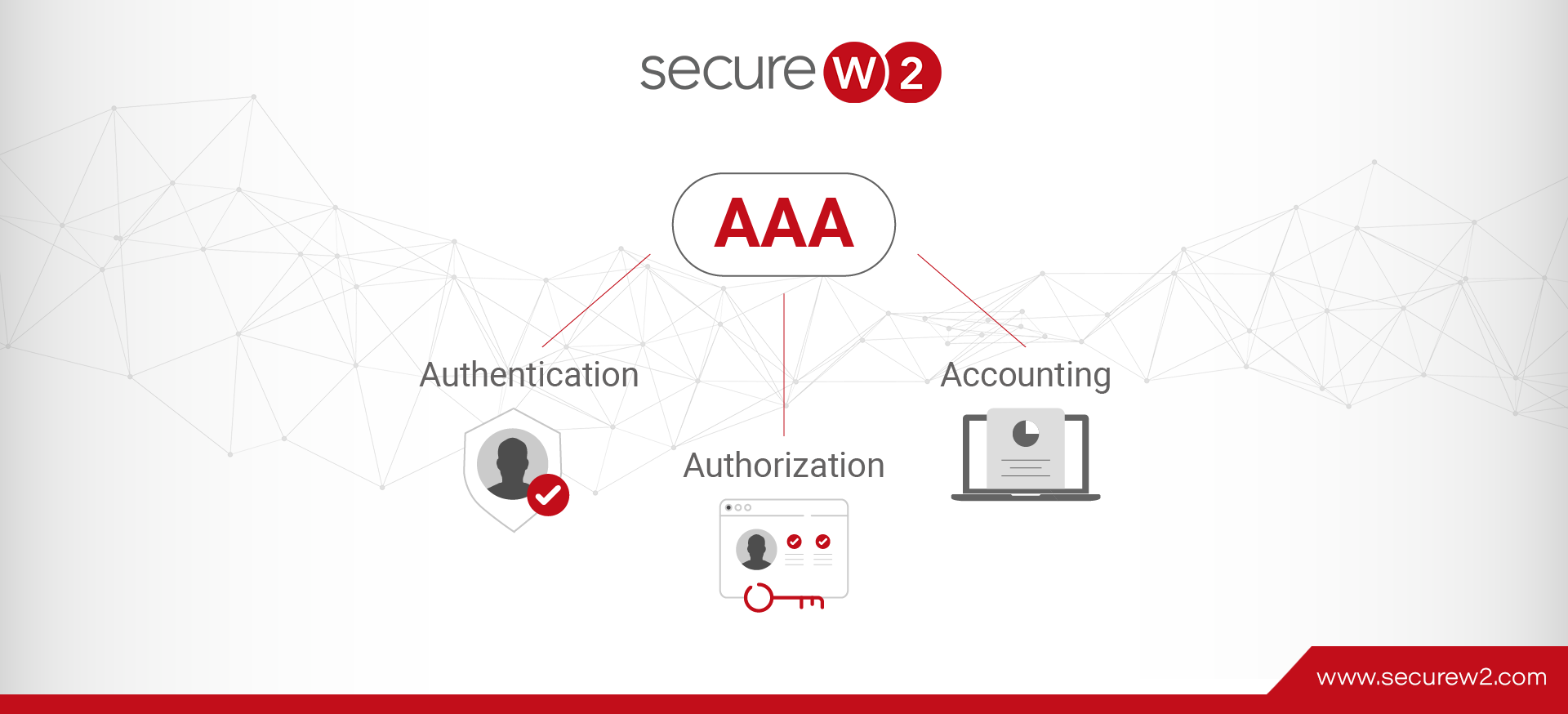
An AAA server processes user requests for access to computer resources and provides an organization’s authentication, authorization, and accounting (AAA) services. The AAA server typically interacts with network access, gateway servers, and user-information-containing databases and directories. One type of AAA ... Read More

Imagine conducting important business online without identifying the person you’re interacting with. It would be like handing sensitive documents to a stranger on the street; every login would be risky. Fortunately, the internet establishes protocols to build trust in the ... Read More

Relying on passwords alone to safeguard access to your resources (including Wi-Fi, applications, and email security) is no longer secure. Cyber attacks designed to harvest credentials become increasingly complex by the day. Stealing a single set of credentials can have ... Read More

Corporate data, social media pages, applications, and user data are crucial assets of an organization, and any theft or misuse of these could lead to huge financial losses. They not only result in loss of business opportunities, but organizations are ... Read More
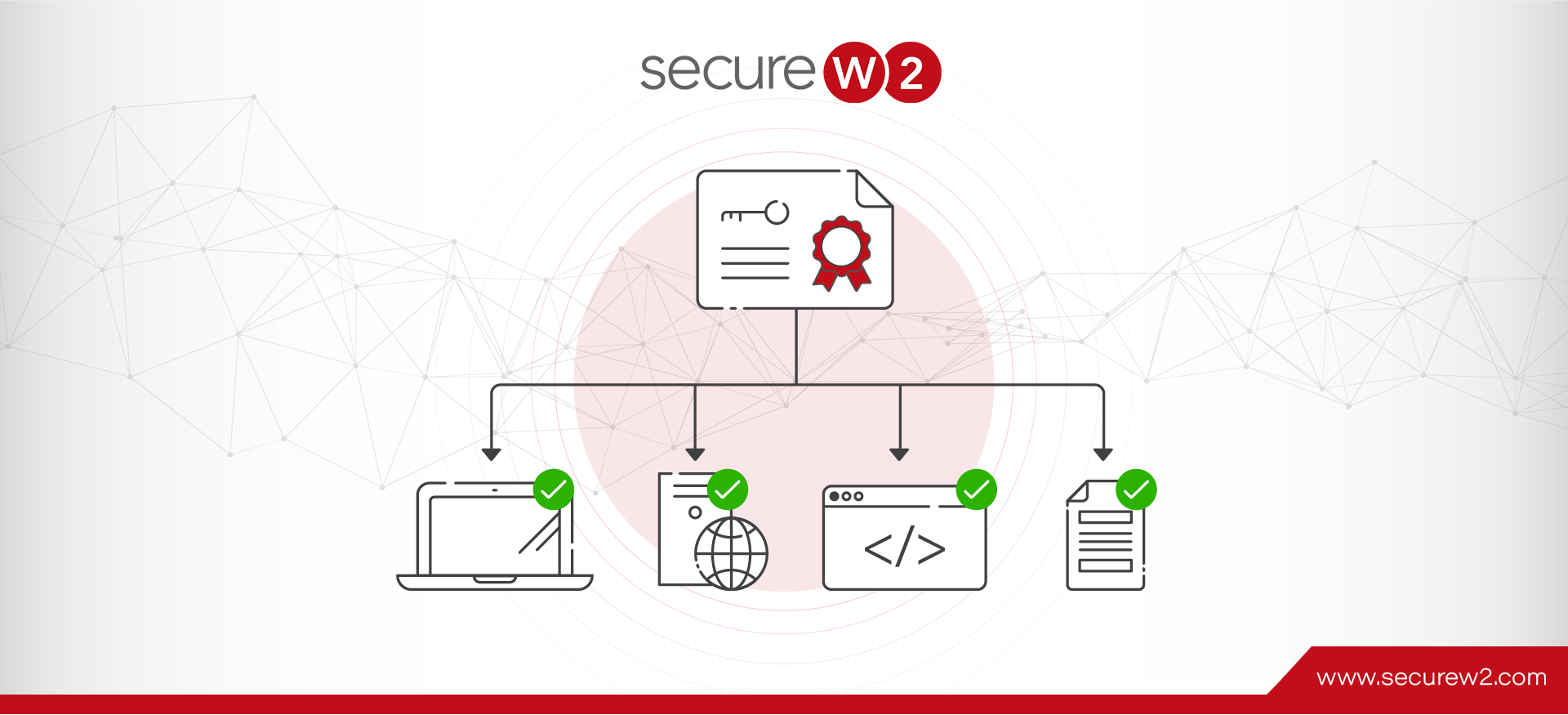
X.509 certificates are forms of identification that leverage public-private key cryptography. They are a secure replacement for passwords.
Do you use Apple devices in your work infrastructure? Then you’ve probably heard of Jamf. Jamf Pro is one of the most robust and feature-dense solutions for managing Apple devices. To fully take advantage of Jamf Pro, you will need ... Read More

Security over the internet has drastically improved in the few decades that the internet has been widely available. The average user doesn’t realize how much goes on behind the scenes to ensure the integrity of their data and browsing experience ... Read More

An enterprise needs a safe, secure, and proper network infrastructure implementation to ensure a functional business environment. The Protected Extensible Authentication Protocol (PEAP) is a form of EAP protocol used by organizations to protect their data over-the-air. The PEAP authentication ... Read More

Everyone uses numerous accounts on the internet these days. Take yourself as an example; you most certainly have a minimum of one social network account, one email address, one for online shopping, and most likely one for online banking. There’s ... Read More