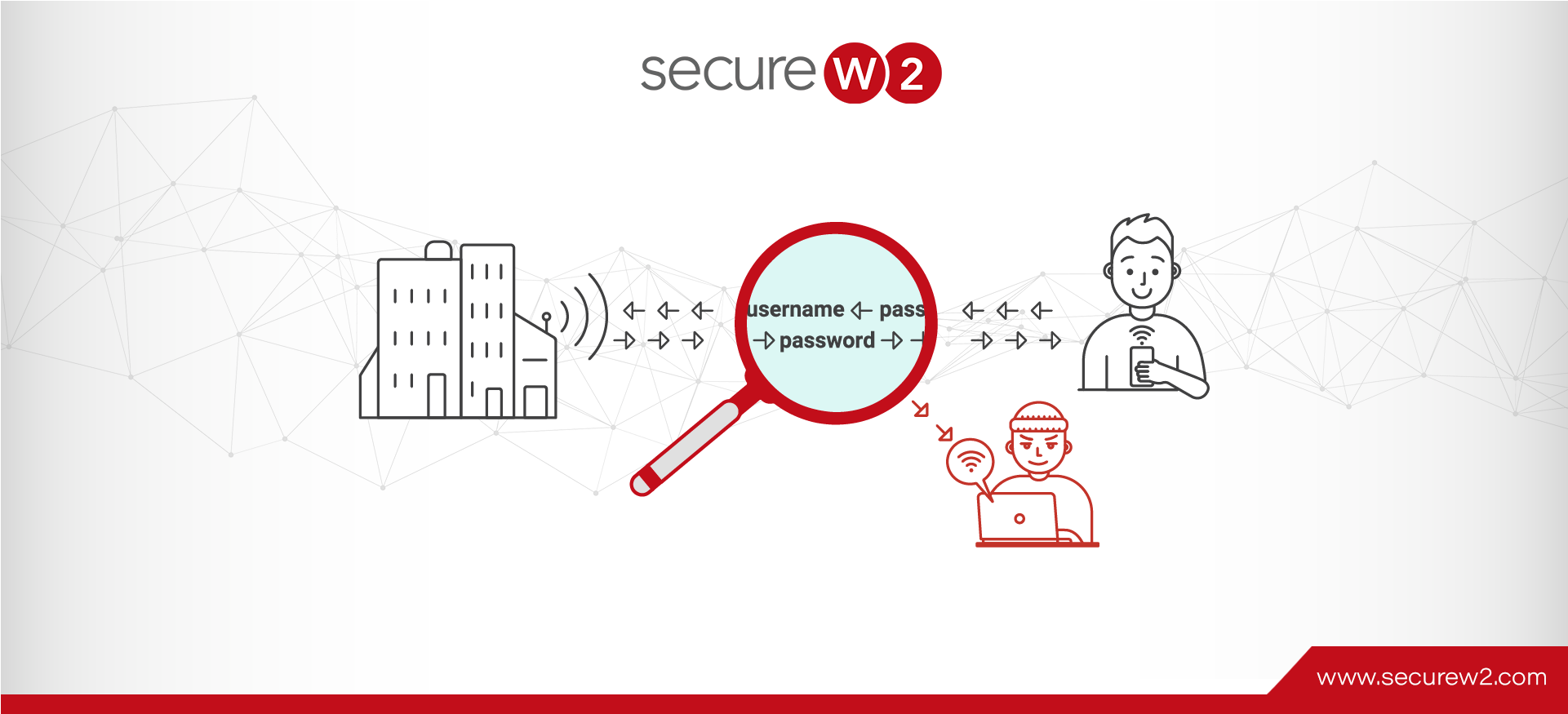
Layer 2 Attacks that Defeat PSK Networks
Move away from traditional PSKs to digital certificates and protect your network from Layer 2 attacks. Know more here!
Stay informed with expert insights, best practices, and the latest developments in network security, identity management, and SecureW2 product updates.

Move away from traditional PSKs to digital certificates and protect your network from Layer 2 attacks. Know more here!

Ensuring the security and integrity of a business’s data and network infrastructure is of utmost importance, and thus safeguarding the local network is imperative. The Wi-Fi network serves as the primary access point to the internet and cloud-based applications and ... Read More

Do you want to move to effective Passwordless authentication solutions? Read to find out how a robust passwordless solution can enhance your network's security.

The cloud presents an enticing opportunity for businesses – it makes important resources available anywhere, allows them to offshore the cost of storage, and can even save them on hardware costs by hosting applications. But the cloud, inextricably tied to ... Read More
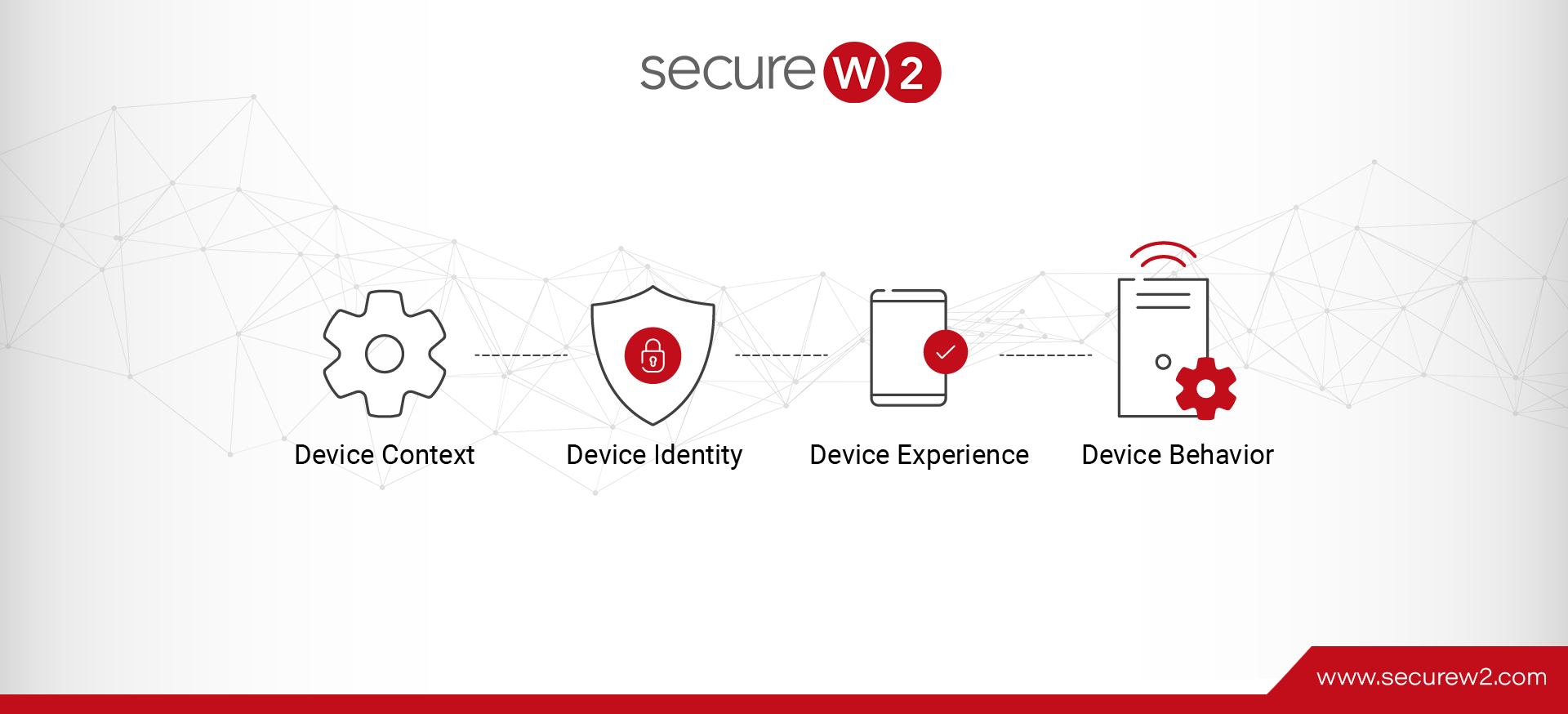
Protect your network from security breach by getting more visibility over your unmanaged and BYOD devices. Device Identity Context can help you improve network security. Continue reading to know more.
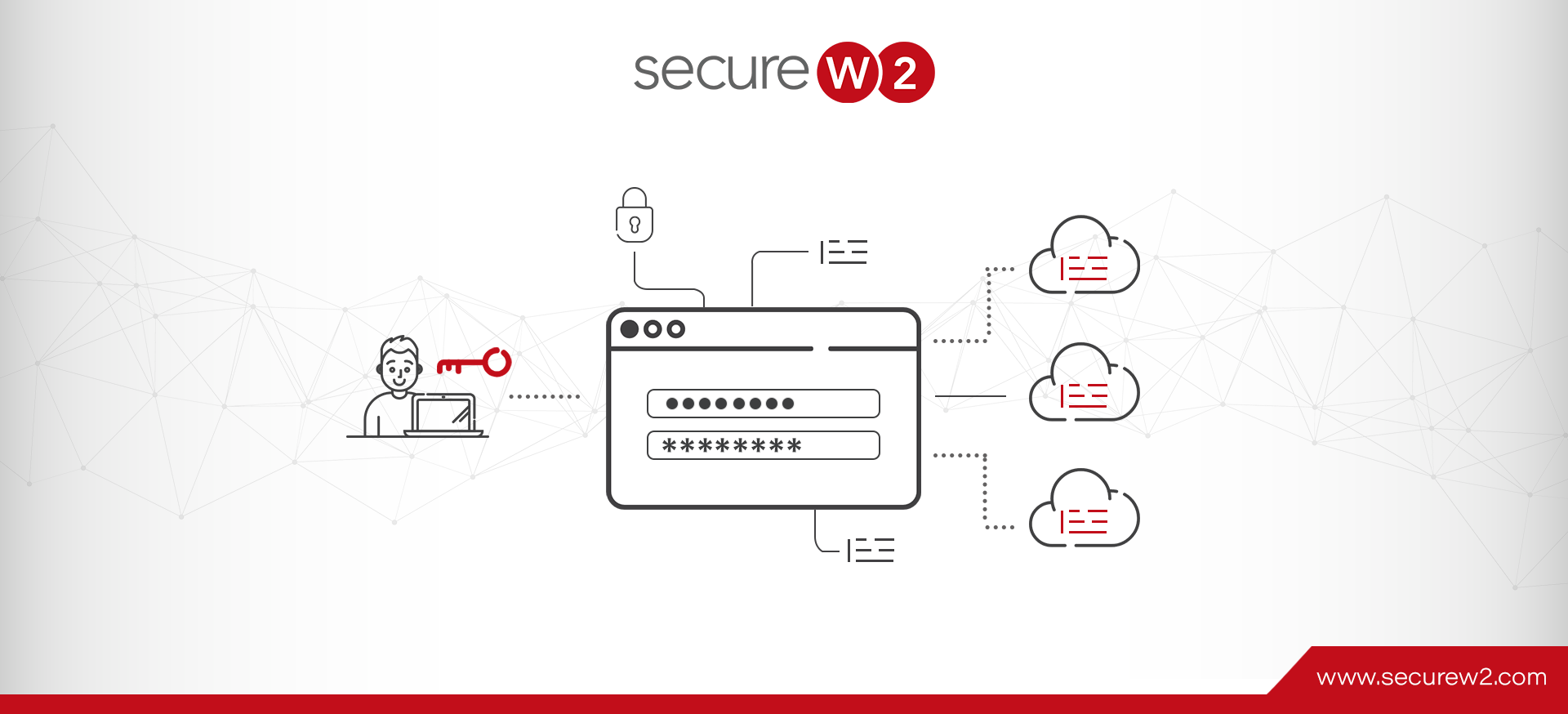
Configure Client Certificate Authentication on OneLogin and enforce Zero Trust Policy and make your network secure.
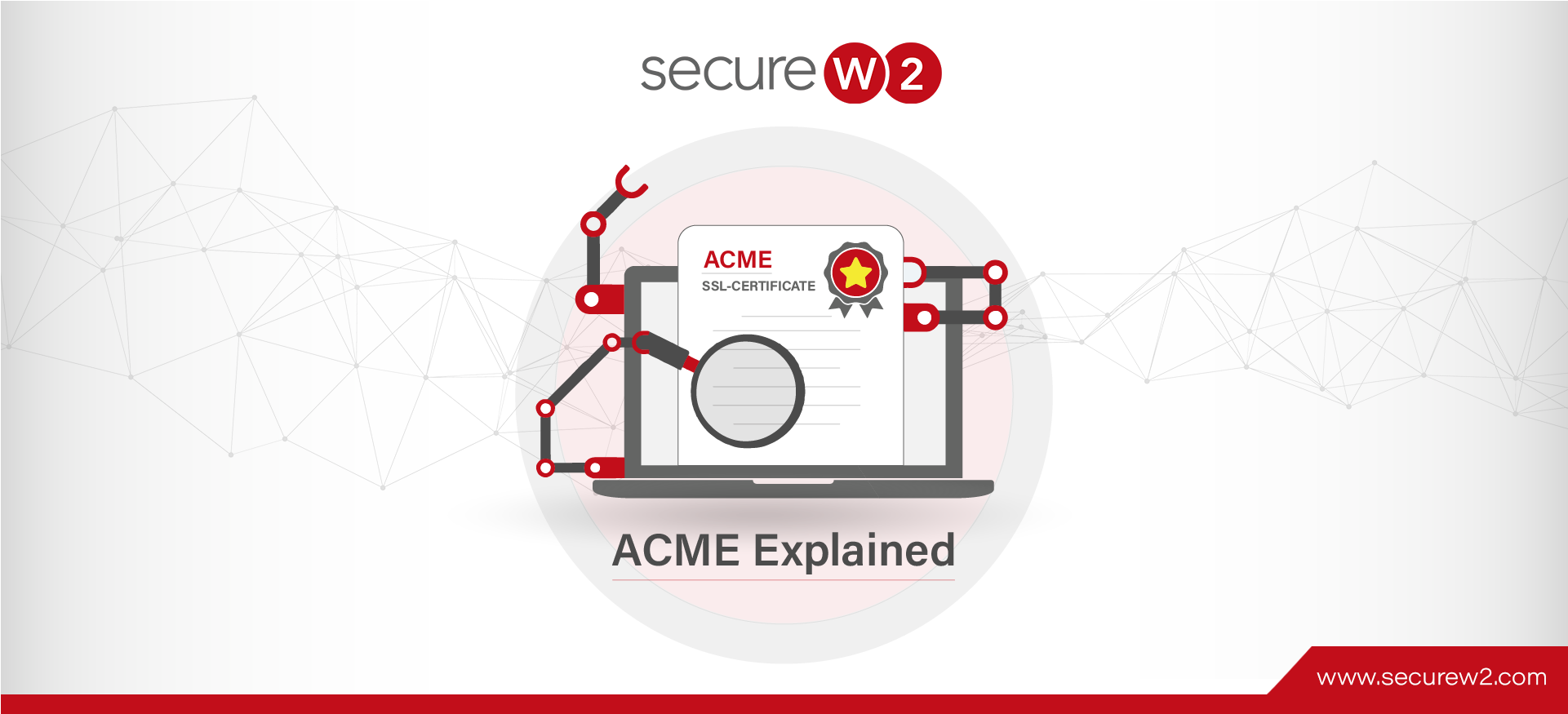
Want to understand what Automated Certificate Management Environment (ACME) Explained is all about? Read this to know more.

Read and compare JAMF and Kandji as Apple MDM solutions here.
Read about two popular NAC solutions ad pick out the best one for your organizational needs.

A survey found that 74% of IT decision-makers whose organizations have been breached in the past say it involved privileged access credential abuse. While Wi-Fi revolutionized networking during the transition from wired to wireless, the challenge is to secure the wireless ... Read More
Wifi is essential in daily life and is critical for any business today. At home, we use a single static password to protect your wifi. This security is called WPA2-Personal. However, organizations are using a more advanced protocol called WPA2-Enterprise. ... Read More