Key Points
- Manual certificate enrollment and renewal is error-prone, time-consuming, and increases the risk of expired or mismanaged certificates.
- ACME automates certificate issuance and renewal through standardized protocols, ensuring seamless lifecycle management and stronger security.
- SecureW2 extends ACME with Dynamic PKI + Cloud RADIUS, enabling policy-driven certificate automation across all devices and identity platforms.
Using X.509 digital certificates to authenticate is the most secure option and an excellent way to provide context for identity and role-based access management. Certificates cannot be stolen or replicated, providing significant assurance that you are connected to the correct network and that the user and machine logging in is indeed authorized to access the network. These are just a few reasons the use of certificates for authentication is gaining popularity in network security.
Certificate management, however, can often become a significant challenge without proper infrastructure. The lack of a certificate inventory in a central place, lack of automation for certificate renewal, and lack of overall visibility of the certificate life cycle are some of the major challenges one faces at the time of deploying certificates. This disorganization makes it easy to miss certificate expiration dates. . An expired certificate can have a significant impact on your business, some of the most common ones being:
- Security risks
- Outages leading to loss of productivity
- Potential security breaches
- Negative publicity
- Loss of customer trust
- Fines from regulatory bodies
It has, therefore, become necessary to look at a solution that automates the handling of certificate management. In this article, we will look at the solution Automated Certificate Management Environment (ACME), how it works, and how it helps with certificate management by providing better visibility and management of the certificate life cycle by eliminating manual management.
Automated Certificate Management Environment (ACME)
Automated Certificate Management Environment, or ACME, is a protocol that enables automation of the issuance and renewal of certificates, removing the need for human interaction in the process.
ACME protocol was designed by the Internet Security Research Group (ISRG) for their SSL certificate service, Let’s Encrypt. Let’s Encrypt is an open certificate authority (CA) that issues domain-validated (DV) certificates and is free of charge. Recently other CAs, PKI vendors, and browsers have started using ACME for various other types of certificates like X.509.
The ACME protocol can be implemented by installing a certificate management agent for a web server.
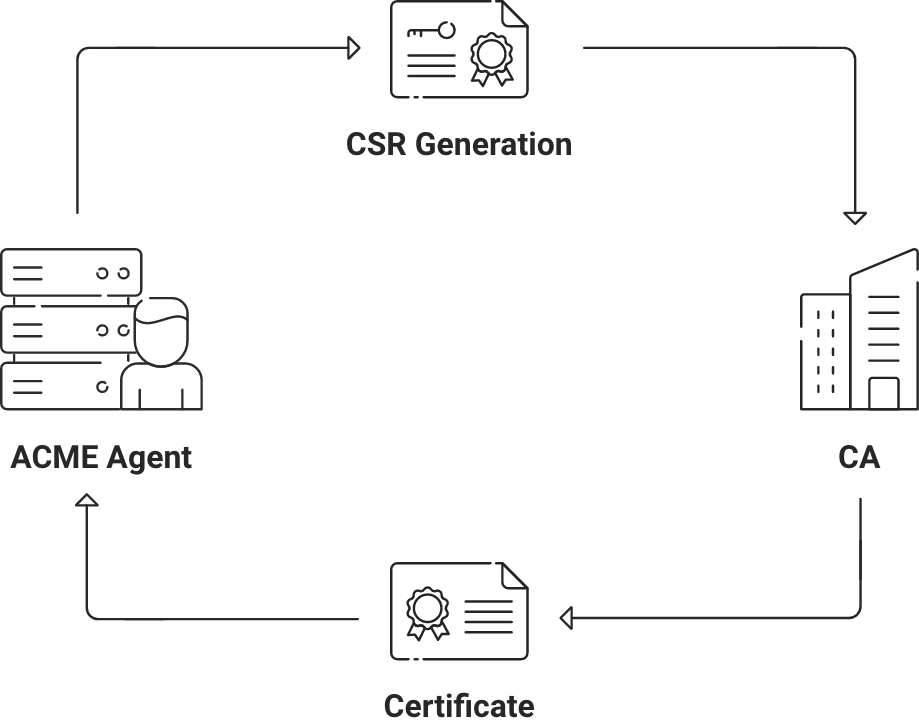
To begin, a certificate management agent is installed on the web server. There is a validation process that any organization or domain will have to undergo with the installed agent. Once the validation process is complete, the agent can request the issuance, renewal, and revocation of certificates. Let’s look at a brief overview of how the process works.
The agent generates a pair of keys that is shared with the CA at the time of the validation. Once validation is complete, the agent is established as the valid owner of the key pair. The key can now be used to digitally sign the Certificate Signing Requests (CSR) and send it to the CA through HTTPS requests. The CA can use the CSR, in conjunction with its associated public key, for issuing the certificate and sending it back to the agent, after which the agent can download and install the certificate and inform the assigned contact about it.
You can automate the agent to check the CA at a defined interval to rotate certificates and keys without human involvement or interference. You can install ACME agents on any server using X.509 certificates and manage multiple domains on the same server or install it on the domain by domain basis.
ACME allows you to reduce almost all of the manual work otherwise involved in managing digital certificates, thus eliminating the following:
- Outages related to expired certificates
- Security risks incurred by unmonitored certificates
- Human Error
History of ACME
ACME was initially designed by the Internet Security Research Group (ISRG) to be used for its open-source CA Let’s Encrypt. ISRG is a non-profit corporation based out of California concentrating on Internet security. Let’s Encrypt provides domain-validated (DV) certificates free of cost.
Let’s Encrypt issues 90-day domain-validated SSL certificates. Facilitated by ACME, the certificates issued can be renewed and replaced automatically without any action needed from the website owners.
The protocol facilitates users to operate the Certificate Authorities of their choice as long as that CA supports it. ACME v2, published in March of 2018, added the ability to issue Wildcard SSL/TLS certificates.
ACME protocol was published as an Internet standard (RFC 8555) in March 2019. With commercial CAs starting to support it as recently as last year, ACME is gaining support among PKI vendors, CAs, and browsers supporting various X.509 certificates.
How Does the ACME Protocol Work?
If you have installed an SSL/TLS certificate in the past, you are aware that it is a tedious process that involves a lot of manual steps. On a high level, you begin by:
- Creating a Certificate Signing Request (CSR) that involves generating a server-side request that has to be copied and pasted into a field for your CA.
- You then run domain validation manually and wait for the certificate to get issued.
- Next, you get the certificate on to the server that it’s being installed at.
- Lastly, install the certificate and check to confirm it is configured accurately.
This manual process requires considerable time and resources, and the outcome can be affected by human errors that may occur during this process.
ACME automates the whole process of certificate management by installing an open-source agent and authorizing the agent to perform certificate management activities at scheduled intervals making the whole process more efficient, as well as time and cost-effective. With ACME, you can organize and automate domain ownership verification, CSR generation, issuance, and installation of certificates. ACME protocol allows you to provision SSL/TLS certificates for any server with an ACME agent installed, including non-Microsoft machines.
Traditionally, ACME is primarily used for generating domain-validated (DV) certificates as they just need to validate that the domain exists, a process that does not require human interaction. When implemented with additional support mechanisms, ACME protocols can generate high-value certificates like extended validation (EV) and organization validation (OV).
ACME protocol sets up an HTTPS server to automate the issuance and life cycle management of trusted certificates and eliminate manual transactions. An ACME client and ACME server are prerequisites to using this protocol. They communicate through a secure HTTPS connection using JSON messages.
How to Set up & Validate ACME?
The steps that help you configure the ACME agent to initiate requisitioning and installing certificates are as follows:
- Select an agent that is compatible and appoint the domain that you want it to manage.
- Select a CA that the agent is compatible with.
- The agent communicates with the assigned CA to generate a key authorization pair that will be used for the validation process.
- To prove its control over the domain it is managing, and the agent will have to solve the DNS/HTTPS ‘challenges’ issued by the CA. The agent will either publish a web page that includes the token provided by the ACME server or publish a DNS record that includes the token.
- To verify the endpoint’s access to the private key, CA will generate a random number called “nonce”. The agent signs this using the private key and sends it back to the CA for verification. The CA will check if it has the correct hash to confirm that the agent is valid and has access to the private key.
- Once the domain and private key ownership are confirmed by the CA, the agent is authorized to execute functions on the web server on behalf of the domain, thus completing the setup.
Certificate Issuance & Renewal of Certificates
Once the ACME agent has been set up and verified, you can automate the certificate operations. For issuance of a new certificate, the agent will generate a CSR for the domain that needs the certificate and send it to the CA via HTTPS. The steps are as follows:
- A CSR will be generated by the agent for the domain
- The public key generated with the CSR will be signed by the agent using the corresponding private key.
- The agent signs the whole CSR with its private key that was generated at the time of the initial configuration
- The CA issues the certificate to the domain after verifying both signatures.
- Lastly, the agent receives the certificate and installs it on the appropriate domain.
The process of renewal is similar to issuance. For renewal, you will have to configure the agent to ping the CA routine requests at pre-defined intervals. This allows it to rotate keys or switch to a new certificate as the admin prefers. The entire process is executed at the back end, eliminating the need for manual processing.
Revocation of Certificates
To revoke a certificate, the agent will need to sign a revocation request with its key so that the CA can verify the signature to confirm if it is a valid request. Once CA revokes the certificate, it publishes the information to the relevant Certificate Revocations Lists (CRLs). The steps that are followed are given below.
- A revocation request is generated by the agent for the concerned SSL/TLS certificate.
- The agent uses its private key to sign the revocation request.
- The CA verifies the signature to confirm the validity of the request.
- The CA revokes the requested certificate.
- The certificate’s revocation status is published to the relevant CRLs.
An admin can initiate a revocation request. However, the revocation process after the request is placed is entirely automatic.
Now let us perform an in-depth analysis of the ACME workflow to understand each step in greater detail.
A High-Level Insight into ACME Protocol Workflow
- As seen in the last section, the device first obtains ACME payload (by MDM or manual .mobileconfig download).
- Then, MDM or unmanaged solutions decide to enroll the given device for client certificates.
- MDM provides the device with a URL pointing to our PKI with a one-time token that identifies the given device along with the enrollment.
- Device contacts SecureW2 ACME services.
- Device request enrollment for “permanent-identifier” requests device attestation-based authentication.
- ACME service returns an attestation challenge to the device.
- It also requests Secure-Enclave for private key storage and device attestation.
- The device generates a key in Secure Enclave.
- The device provides information to the Apple attestation server that allows for the creation of a key attestation.
- Factors to be verified in ACME Protocol
- For Both MDM and BYOD
- Proof whether a private key is stored in Secure Enclave(for Apple devices)
- Proof of the authenticity of devices trying to enroll from the Apple attestation server(for example, serial number, IP address, etc.)
- Verify whether the device to issued certificate is not tampered with and the Secure Enclave is working properly.
- Only For MDMs
- Verify whether the respective MDMs manage the device.
- Verify whether the enrollment attempt was initiated for the respective device. (Optional)
- For Both MDM and BYOD
- Factors to be verified in ACME Protocol
- After receiving the proof and nonce, the ACME server contacts the policy engines of the given PKI server along with the Attestation Verification Server.
- It verifies the serial number and attestation with the MDM again and confirms the enrollment attempt was valid before issuing the certificate.
- Finally, the certificate is issued by the CA.
What is Apple’s Secure Enclave?
Apple’s Secure Enclave is a specialized security feature featured in iPhones, iPads, and Mac computers. It is intended to provide a high level of security for sensitive data while also ensuring secure device operations. It contains almost all the information related to a device’s serial number and provides cryptographic proof with the key that was given by Apple, which is exclusive and not extractable.
Consider the Secure Enclave to be small, dedicated hardware within your Apple iPhone that handles all security-related functions. It has its own CPU and memory, independent from the device’s primary processor. This separation is critical because it offers a safe and isolated environment in which sensitive data may be stored and processed without being easily accessible to other portions of the device or external threats.
One of Apple’s Secure Enclave’s basic functions is storing and managing encryption keys securely. Encryption keys function similarly to secret codes, scrambling and unscrambling data to ensure that only authorized individuals can access it. The Secure Enclave creates and stores these keys, ensuring their safety from unauthorized access.
What is Device Attestation in Apple Devices?
Device Attestation in Apple devices is cryptographic proof of the validity of device attributes based on the Secure Enclave’s and Apple’s attestation servers’ security. These high-assurance IDs may be used to authenticate Wi-Fi, MDMs, VPNs, Kerberos, and other services.
Device attestation basically contains a cryptographically signed document or pseudo certificate that confirms that a key was given to it by APPLE and has proof of that, such as a serial number and newly generated key as well. The key that it is using for certificate enrollment is tied to the same Secure Enclave residing on the device.
Benefits of ACME Protocol
This protocol’s rapid increase in popularity is due to several benefits that make it a favorable choice. Here are some of the key benefits that the ACME protocol offers.
- Better visibility of the entire certificate lifecycle
- Standardization of certificates issuance and request
- Improve the efficiency of the certification process as a whole
- Minimize configuration error due to human interference
- Quick CA and key migration for disaster management
- Overall cost saving
ACME vs. SCEP
SCEP, or Simple Certificate Enrollment Protocol, is an open-source certificate management protocol to automate certificate issuance. SCEP enables devices to enroll for certificates using a URL and a shared secret for communication with a PKI, thus automating the process of information exchange which is otherwise a manual activity that admins have to perform. Mobile Device Management (MDM) software uses SCEP to push payload containing the URL and shared secret for managed devices.
It is similar to ACME in that it enables certificate enrollment and issuance. However, ACME automates certificate management and includes revocation as well. SCEP has been in use for much longer (it was originally developed by Verisign for Cisco as a lighter option to Certificate Management) than ACME, which was developed recently in comparison.
SecureW2 solutions enable you to use either of the protocols for the internet of things (IoT) devices, BYOD, and managed devices. With SecureW2’s managed PKI, you can generate your own certificates and enroll all types of devices for certificates.
ACME Certificate Management and Authentication with SecureW2
Automating certificate management comes with multiple benefits, from eliminating human error to an overall reduction in cost involving manpower, resources, and time. With ACME, certificate issuance, renewal, and revocation become a seamless process with end-to-end automation.
SecureW2 can help you enjoy the benefits of ACME protocols even further with our industry-leading solutions. We offer solutions that configure and auto-enroll managed devices for certificate-based authentication with the ability to deploy certificates to any MDM via API Gateways. We provide easy integration with MDM services like Jamf, Intune, and Google Workspace. Talk to our experts to learn how we can help you implement ACME with our solutions to improve your certificate management experience.