Achieve Device Trust & Passwordless Security
With SecureW2, making sure only trusted users and devices access systems is easy. Our Cloud Managed PKI, RADIUS, and Security services can be set up in under an hour, providing a comprehensive package to enable passwordless authentication. Improve security and lower IT expenses and cyber insurance with SecureW2.
Trusted by 1,000+ Global Organizations to Make Their Networks Simpler, Faster, and More Secure.
Certificate Lifecycle Management & Automation Platform
A turnkey managed Cloud PKI platform designed to automate certificate lifecycle management using Cloud Identities like Azure, Okta, Jamf, Intune, and more.
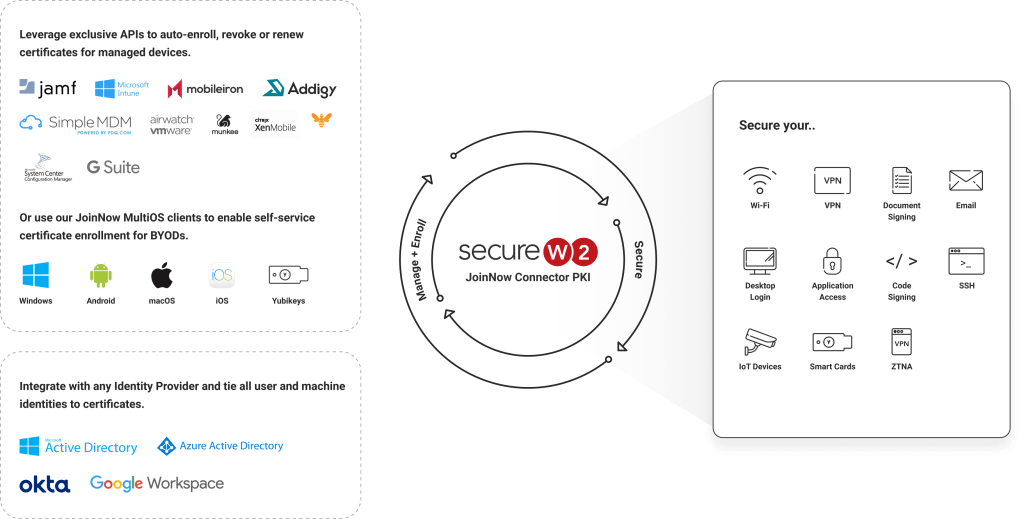
Certificate Lifecycle Management Designed for Your Cloud Environment
- Search for users/devices and easily view all their digital certificate lifecycles and authentication events in one place for easy troubleshooting and management
- Simple and secure, backed by HSM (Hardware Security)
- Integrate with ease to nearly every device management system or with BYODs/unmanaged devices
- Automate certificate enrollment and revocation to all your managed devices through our APIs
- Total cost of ownership (TCO) is less than a third of comparable on-premise Active Directory (AD CS) solution.
We’ve Helped Many Businesses Like Yours
Certificate Lifecycle Automation for Managed Devices
Enrolling your organization’s diverse array of devices - from company-owned laptops to unmanaged smartphones - for certificates doesn’t have to be a daunting task. Our managed device gateway APIs can configure the managed devices on your network for certificate-based authentication with no end-user input.
- Automatically configure and enroll managed company-owned devices through our managed device gateway APIs.
- Connect devices to networks and provide reporting, device analytics, and remote troubleshooting data.
- Push configuration profiles to IoTs, ensuring all devices are using secure certificate-based authentication.
Easy Self-Service BYOD Certificate Enrollment
Potential misconfiguration can be a huge window for human error - and a liability for your security. Our JoinNow MultiOS onboarding solution takes human error out of the equation by providing intuitive self-service software for enrolling unmanaged devices with digital certificates.
- Automatic self-service digital certificate enrollment software compatible with every OS, which includes guided user flow where necessary.
- Configure for device or user certificates.
- From start to finish, configuration takes only a minute or two.
- Configure devices for 802.1x, certificate-based network authentication.
- Support for iOS, Windows, macOS, Android, ChromeOS, Linux, and Kindle.
Frequently Asked Questions
JoinNow Connector PKI is a complete certificate management solution that allows organizations to easily manage the lifecycle of their digital certificates. It provides an intuitive management portal, automation software, and APIs that all combine to make the entire certificate lifecycle easy to manage. Managing certificates is an incredibly complex process that requires highly educated security professionals.
Solutions like SecureW2 work to automate many facets of certificate lifecycle management with security best practices. Enrolling a device for a digital certificate has never been easier. Our Gateway APIs use protocols like SCEP, JSON, and OAuth to both enroll and renew certificates with no-end user interaction required. This allows the JoinNow Connector Public Key Infrastructure to constantly assess whether a user or device should have a certificate, and leverage existing security policies to determine what type of certificate they have and what level of access it should grant.
Most Certificate Lifecycle Management solutions are designed to work with an existing Public Key Infrastructure (PKI), usually Active Directory Certificate Services, and provides a simple framework for automation with a Graphical User Interface (GUI).
The JoinNow Connector PKI rethinks Certificate Management by providing a platform that is designed to be an extension of an organization’s existing identity infrastructure. It constantly communicates with cloud identities like Azure, Okta, Intune, and Jamf so a user or device only has a valid certificate if it is still active, has the right permissions, or is compliant. This ensures that no systems have expired certificates when they shouldn’t, uncompliant devices or inactive users can’t access sensitive data, and your organization remains secure.
The benefit of Certificate Management Systems, and using a digital certificate for authentication in general, is enabling passwordless authentication with the use of digital certificates, which greatly improves an organization’s security. It’s no secret that passwords are a vulnerability, with organizations like Microsoft recommending that you move away from password-based PEAP-MSCHAPv2 to passwordless protocols like EAP-TLS. Digital certificates can be used to secure a range of resources, including your wired & wireless network, VPN, applications, desktop logins, and much more. Additionally, there are benefits for your end-users. With digital certificates, employees no longer have to deal with frustrating password reset policies and disconnects due to password changes.
A Certificate Lifecycle Management Solution with good automation capabilities makes sure that digital certificates remain in the hands of devices/users that deserve them, and are constantly using an array of data sources to automate certificate management with real-time data. It only takes one expired certificate, just like credentials, to break into a system. This is how the Equifax breach happened. A modern certificate management system prevents expired certificate issues like web servers going down, SSL / TLS certificates failing to encrypt traffic.
Many organizations see the benefits of going passwordless, but think that they can reduce the cost of doing so by building their own PKI infrastructure. Unfortunately, this often ends up being a costlier venture in terms of finances and time spent. Building a PKI requires expertise, space for the servers, and regular maintenance. Additionally, certificate management - from issuance to renewal to revocation - is time-consuming.
Certificate Management solutions like our JoinNow Connector PKI can save you the resources you would otherwise spend on building and maintaining your own. What’s more, since our PKI infrastructure is cloud-based, your administrators can access it from anywhere without having to replicate it at every office location. On average, the JoinNow Connector PKI’s total cost of ownership is less than ⅓ of your standard AD CS implementation.
When it comes to revocation, our cloud-based PKI can revoke certificates in a few different ways. Certificate revocation can be achieved manually through our certificate management portal, and through automatic revocation with some MDMs such as Jamf and Intune. Our PKI as a service also includes customizable policies you can create, such as non-utilization, which means certificates that aren’t used for a definable period of time (such as 60 days) are automatically revoked.
When certificates are revoked, they are added to a Certificate Revocation List (CRL). Each CA that is created in the JoinNow Connector PKI contains a Base Certificate Revocation List and a Delta Certificate Revocation List, which allows servers to quickly receive certificate revocation updates in a computing-efficient fashion.
All private keys are stored in hardware, never in software or sent over the air. Many certificate lifecycle solutions take shortcuts and install certificates in software. This leads to easily compromised certificates, causing more security issues than they solve.
With our JoinNow MultiOS Onboarding software, unmanaged devices will generate the have their private key configured as non-exportable, further increasing security. After the private key is generated, MultiOS will send the Certificate Request and device information to the JoinNow Connector PKI, which will use that to create the Certificate and Public Key for the device to go along with the private key.
Our PKI makes renewal simple, too. For managed devices, certificate renewal typically happens on an automatic basis a month or two before the certificate’s expiration. For BYODs, administrators can set a customizable notification email to go out to end-users at a customizable time interval before the certificate is set to expire, encouraging them to renew their certificate before it is set to expire.
Our PKI allows you to create a private certificate authority (CA) only. JoinNow Connector PKI was designed to be used for internal applications, like Application Security and Wi-Fi, so a private certificate authority is the best solution. So it is not a publicly trusted CA, like the Public Key Infrastructures that create SSL certificates for web browsing.
However, you can create as many private CAs as you need. Our customers commonly build multiple CAs for different groups of people to enable role-based access control, such as having multiple CAs for their HR and DevOps teams. It’s also very easy to create both root CAs and Intermediate CAs as well.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Pricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.