In a recent cyberattack that involved a password breach at T-Mobile, the personal data of over 37 million T-Mobile customers, including names, dates of birth, Social Security numbers, and driver’s license information, was stolen by hackers. The breach is considered one of the largest in U.S. history, highlighting the ongoing risks of password-based security mechanisms in the face of more sophisticated cyber attackers.
Software giant Microsoft has been at the forefront of promoting passwordless authentication, recognizing that traditional passwords are vulnerable to hacking and pose a security risk for users. Microsoft’s goal is to make it easy for users to move away from passwords and adopt more secure authentication methods, such as biometric authentication and security keys, using its Microsoft Authenticator App.
Let’s look into how Microsoft is leveraging its expertise and resources to create a seamless migration path for its user base. First, we’ll cover precisely what its Authenticator App is.
What Is the Microsoft Authenticator App?
Microsoft Authenticator is a mobile app developed by Microsoft that provides an extra layer of security when logging into your Microsoft account or other online accounts. The app generates a unique, one-time verification code required to access your account and your password. This provides an extra layer of protection against unauthorized access, as the code is only valid for a limited time.
With Microsoft Authenticator, you can also set up two-factor authentication for your Microsoft account, which requires you to provide both your password and a code the app generates to log in. This makes it much more difficult for someone to access your account without your knowledge or consent.
In addition to its advanced security features, Microsoft Authenticator provides a convenient way to manage your online accounts, as you can use the app to log into multiple accounts without remembering different passwords.
Advantages of Passwordless Authentication
There are several reasons why someone would prefer to use passwordless authentication:
- Convenience: With passwordless authentication, users no longer have to remember or reset a complex password if they forget. This can make the passwordless login process faster and more user-friendly.
- Security: Passwords can be vulnerable to hacking and data breaches, but with passwordless authentication, the risk of password-related security breaches is significantly reduced.
- Increased accessibility: For individuals who have difficulty remembering passwords, passwordless authentication provides an alternative solution to improve their experience.
- Better compliance: In specific regulated industries, passwordless authentication can help companies comply with security regulations and standards, as it can provide a more secure authentication process.
Overall, passwordless authentication offers a simple and secure way for users to access their accounts, and it can provide several benefits over traditional password-based authentication.
What Is Microsoft Passwordless Authentication?
Microsoft Passwordless Authentication is a technology that allows users to log into their online accounts without using a password. Instead, it relies on alternative authentication methods, such as biometric recognition, security keys, or one-time codes sent via SMS or email, to confirm a user’s identity.
Passwordless authentication aims to provide a more secure and convenient way of accessing online services, as passwords can be easily forgotten, lost, or hacked. Microsoft’s Passwordless Authentication integrates with the company’s Azure Active Directory service. It can also be used with various Microsoft products, such as Windows 10, Windows Hello, Office 365, Microsoft Outlook, and Microsoft 365.
How Does Microsoft Passwordless Work?
As we know, Microsoft Passwordless is a feature that allows users to access their Microsoft accounts without entering their Microsoft account password.
The process of logging in with Microsoft Passwordless works as follows:
- The user selects the “Sign in with Microsoft” option on a website or app.
- The user is prompted to provide the email address associated with their Microsoft account.
- A notification is sent to the user’s mobile device through the Microsoft Authenticator app.
- The user opens the Microsoft Authenticator app and approves the sign-in request.
- The user is signed in to their Microsoft account without entering a password.
Using different authentication methods adds an extra layer of security since it makes unauthorized access to the user’s account more difficult. Furthermore, eliminating the necessity for a password minimizes the threat of password-related security breaches and makes the sign-in process more user-friendly.
It’s worth noting that Microsoft Passwordless is presently in the initial stage and may not be available to all users. Microsoft is constantly striving to expand and improve the functionality of this feature.
Migrating to Passwordless Microsoft Authentication
Microsoft is working to educate its user base about the benefits of passwordless authentication and the steps they can take to adopt these technologies. The company provides guidance and support to users, such as step-by-step instructions for setting up and using passwordless authentication methods and troubleshooting tips for common issues.
Another way Microsoft is driving the adoption of passwordless authentication is by making it a core feature of its products and services. For example, Microsoft 365 now includes passwordless sign-in capabilities, allowing users to log in using the Microsoft Authenticator app or a Microsoft security key.
In addition, Microsoft has made it a requirement for its employees to use passwordless authentication, setting an example for its user base and showing that the technology is feasible and effective.
Overall, Microsoft’s role in migrating its user base to passwordless authentication is to provide a secure and convenient alternative to passwords that is easy to use and widely available. Through its investment in passwordless technologies and the introduction of CBA (Certificate-based Authentication) in its flagship Azure AD, Microsoft is driving the adoption of a more secure and reliable authentication method that will help protect its users’ digital identities.
Role of Azure AD CBA in Going Passwordless
Azure AD CBA (certificate-based authentication) is a security feature provided by Microsoft in the Azure Active Directory that uses real-time authentication and access policies to protect your organization’s resources.
It helps enable passwordless authentication by allowing users to sign in to their personal Microsoft account without a password, using secure methods such as biometrics or security keys. CBA continuously evaluates the user’s authentication status and enforces access policies based on their risk profile and the sensitivity of the resource they’re trying to access.
In simpler terms, Microsoft has ensured minimizing the dependency on passwords by implementing Azure AD CBA, which basically checks whether a user is who they say they are, using various methods that don’t require a password. Doing so can help keep your organization’s resources safe from unauthorized access.
You can smoothly switch to CBA with Azure AD with the right tools, like a managed PKI. We will explain how you can quickly onboard to certificates using our innovative and user-friendly solutions.
How to Configure Azure AD CBA With SecureW2
Getting Azure AD CBA set up is pretty simple. It only takes a few steps — especially if you’re using an MPKI like the JoinNow Connector PKI and already have an application established for it in Azure AD.
Prerequisites:
- A client certificate enrolled on your device that contains the attribute User Principal Name
- A Root CA and Intermediate CA (we create ours in SecureW2)
- An active Azure environment and Azure AD Subscription, preferably as a Global Administrator.
Overview of the Configuration:
- Export and Create a SecureW2 Certificate Authority
- Upload your CAs and CRL to Azure
- Create a CBA Authentication Policy in Azure
- Issue Client Certificates to Users & Devices
- Test the Certificate
Export and Create a SecureW2 Certificate Authority
To set up Azure AD CBA, you will need a Certificate Authority (CA) to link to your Azure. Our management portal automatically generates a root CA that you can use otherwise, and you are free to create your own in our portal.
Export an Existing Certificate Authority
If you already have a Root and Intermediate CA in SecureW2, here’s how you can export them:
- Log in to the JoinNow Management Portal.
- Go to PKI Management > Certificate Authorities.
- In the Certificate Authorities section:
- Download the Root CA you’d like to use for Azure AD CBA
- Download the respective Intermediate CA
- Click View on each CA to find the respective CRL URLs. Save each Base and Delta CRL for each CA.
Create a New Certificate Authority
If you’d like to create a new Certificate Authority to use for Azure AD CBA, here’s how to do it:
- Go to PKI Management > Certificate Authorities.
- In the Certificate Authorities section, click Add Certificate Authority.
- Create a Root and Intermediate CA, configure settings as desired, and click Save.
- Once it’s been created, navigate to Certificate Authorities, and click View on your newly created CA. Save the Base and Delta CRL.
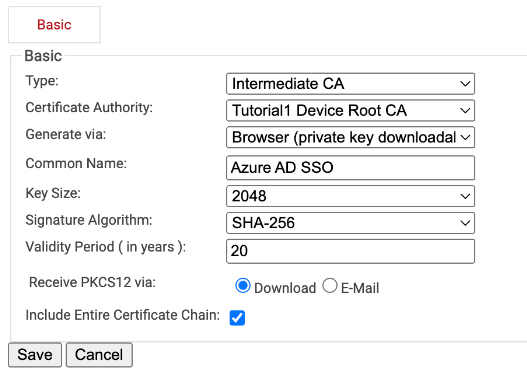
Creating a CA in the SecureW2 Management Portal
Import the Certificate Authorities to Azure
Now that we have our Certificate Authorities handy, we can import them into Azure.
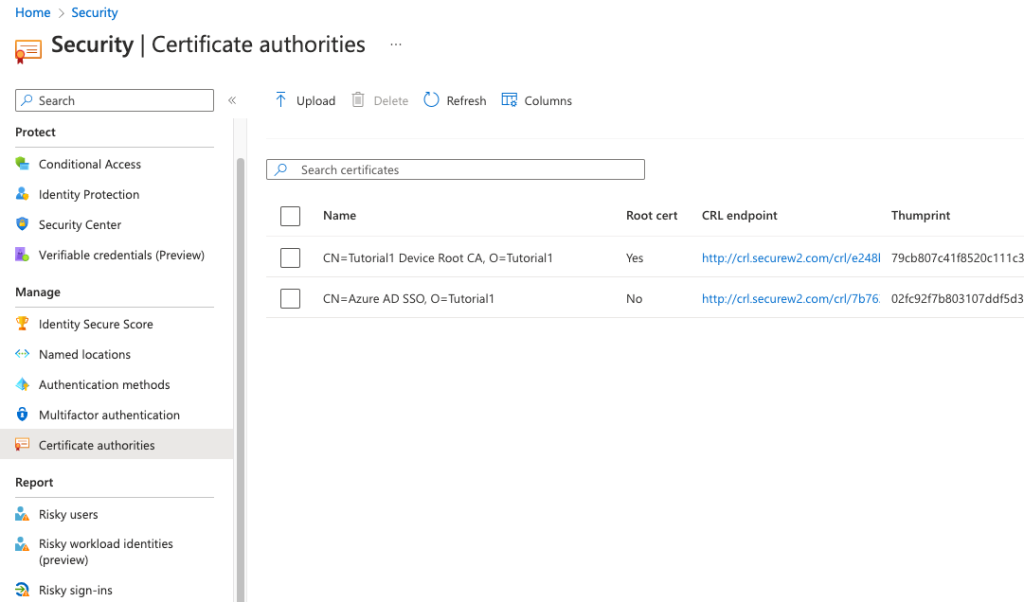
Certificate Authorities in Azure
- Log in to Azure
- Navigate to Security > Manage > Certificate authorities
- Click Upload
- Upload your CA
- Check Yes if it’s a Root CA
- Paste your Base and Delta CRL URLs
- Click Add
Note: The Certificate Revocation List URL is where you upload your Base CRL.
Create a CBA Authentication Policy in Azure
At this point, you need to indicate in Azure itself that you will be using certificates. You can do this in your Azure portal, pictured above.
You can go into Certificate-Based Authentication through the Policies section, add a rule, and choose where the certificates will be coming from.
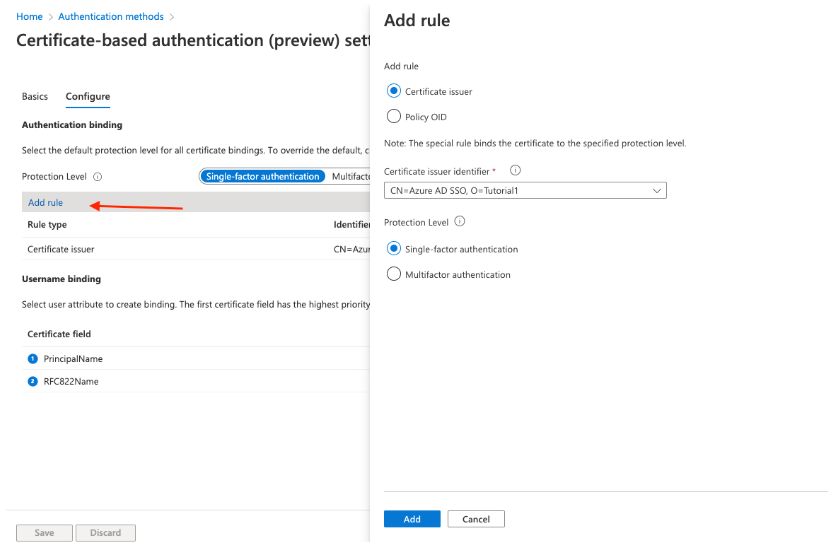
Authentication Binding and MFA
The binding authentication policy helps to determine the strength of authentication to either a single-factor or multi-factor. An admin can change the default value from single-factor to multifactor and configure custom policy rules by mapping to issuer Subject or policy OID fields in the certificate.
- Click Configure to set up Authentication Binding.
- The protection level attribute has a default value of Single-factor authentication. Select Multi-factor authentication to change the default value to MFA.
- Click on Add rule
- You can create a rule using Certificate Issuer or Policy OID.
- Click Single-factor or Multi-factor authentication.
- Click OK to save the custom rule
Username Binding
After creating the binding authentication policy, we need to create a username binding policy to verify the user in the tenant during the authentication.
- Create the username binding by selecting one of the X.509 certificate fields to bind with one of the user attributes.
- The username binding order represents the priority level of the binding. The first one has the highest priority, and so on.
- The authentication fails if the specified X.509 certificate field is found on the certificate, but Azure AD doesn’t find a user object using that value. Azure AD doesn’t try the subsequent binding in the list.
- The next priority is attempted only if the X.509 certificate field is not in the certificate.
- Choose RFC822Name and select userPrincipalName under User Attributes.
- Choose PrincipalName and again select userPrincipalName under User Attributes.
- Click Save to save the changes.
These are high-level steps, and the specific details will depend on your organization’s needs and the configuration of your Azure AD and SecureW2 tenants. It’s recommended to consult Microsoft’s and SecureW2’s documentation or seek the assistance of a qualified consultant for more detailed guidance.
Native Integration of SecureW2 With Microsoft
SecureW2 can natively integrate with Microsoft to provide secure and streamlined access to Microsoft services, including Office 365 and Azure Active Directory. The integration allows users to access Microsoft services using a single sign-on (SSO) experience, eliminating the need for multiple usernames and passwords.
SecureW2 with Your Azure Infrastructure
With SecureW2, administrators can set up Microsoft integration using various authentication methods, such as PEAP-MSCHAPv2, EAP-TLS, and EAP-TTLS/PAP, to ensure secure access to Microsoft services. We also support robust authentication methods, such as multi-factor authentication (MFA), to provide an extra layer of security for Microsoft services.
The native integration between SecureW2 and Microsoft allows organizations to take advantage of Microsoft services while ensuring the security of their network and data. This can help organizations reduce the risk of security breaches and minimize the impact of potential security threats.
Going Passwordless With SecureW2
SecureW2 can play a vital role in enabling passwordless authentication for Microsoft customers. As discussed above, we can easily integrate with Azure Active Directory, allowing users to authenticate using certificate-based methods without relying on passwords. The platform provides various services that make it easy for organizations to implement certificate-based authentication and access policies.
We have extensive experience in automating certificate management, including certificate issuance, renewal, and revocation, reducing the burden on IT administrators. Our access policies provide a way for IT admins to define access policies based on user risk profiles and other factors such as device health, location, or time of day. Access policies can be customized for user groups or resources, providing granular control over who can access what.
We also provide detailed reporting and analytics, helping organizations monitor user authentication activity and detect anomalies. The platform provides real-time access logs, which can be used to track user activity and detect unusual behavior. The reporting and analytics features can also be used to help organizations comply with regulations such as GDPR and HIPAA.
By leveraging SecureW2’s certificate-based authentication and access policies, organizations can significantly reduce the risk of password-related security incidents, such as phishing, credential stuffing, and password spray attacks. If you’d like to see exactly how your network would look with SecureW2, we’d be happy to demonstrate. Set up a free demo with our team to see firsthand how easy passwordless can be.