Key Points
- AD Conditional Access combined with 802.1X enforces policy-driven, secure network access.
- Without Conditional Access, networks risk unauthorized access and lack granular device or user control.
- Integrating 802.1X with Azure AD Conditional Access ensures only compliant devices and verified users gain access to the network.
The post-pandemic world is witnessing an exponential surge in cloud-based network solutions as many businesses transition into digital mode. Interestingly, many cutting-edge wireless technologies like 5G, virtual reality, and AI are also changing the pattern of data consumption with each passing day. This trend is expected to continue into the future, considering the superiority of cloud technologies.
Most organizations are making this shift to assist their bolstered remote workforce with the help of cloud platforms like Azure AD (Microsoft Entra ID). However, these developments come with an increased risk of cyberattacks and other security threats, forcing organizations around the globe to strengthen their network security.
In this article, we will explain the conditional access policies of Azure AD and how they can help you enhance the security of your organization.
What is Azure AD (Azure Active Directory)?
Azure AD is a multi-tenant, cloud-based identity and access management (IAM) service used exclusively to support cloud infrastructure. It uses REST APIs to pass data from one system to other cloud-based applications and systems that support REST.
Azure AD is a live database that stores clients’ accounts and their credentials, shared files, security groups, permissions, and more. It enables users to access external resources such as Microsoft 365, the Azure portal, and various other SaaS applications. It also empowers users to access internal resources of their respective organizations like local networks and intranet.
Furthermore, Azure AD Multi-Factor Authentication (MFA) enables users to choose additional layers of authentication, such as OTPs or phone calls. This feature reduces users’ dependency of users on redundant secondary authentication like a hardware token. It also facilitates unblocking locked accounts and password resets without any involvement of the helpdesk.
Difference between Azure AD (Microsoft Entra ID) and Windows AD
- Windows AD uses LDAP to pass queries between clients and servers, while Azure AD uses REST APIs to communicate to various web-based applications and services.
- Windows AD uses Kerberos and NTLM protocols to authenticate user credentials, while Azure AD uses cloud-based protocols like OAuth2 and SAML for user authentication.
- An on-premise server management system governs servers in Windows AD, while Azure AD uses Azure AD Domain Services to manage the servers present in the cloud.
- While AD does not manage mobile devices without external third-party solutions, Azure AD uses Mobile Device Management (MDM) solutions like Microsoft Endpoint Manager (MEM Intune) to manage mobile devices.
- Windows AD enables Windows devices to join the domain using Group Policy (GPO) or external third-party vendors. In contrast, Azure AD smoothly enables them by Microsoft Intune or conditional access policy.
What is Azure AD Conditional Access?
Azure AD Conditional Access is the set of policies within Azure AD that ensures security in the cloud by practicing optimized decisions by bringing various signals together.
You can envision a conditional access policy as an “if-then” statement in a programming loop to repudiate or grant control to your organizational resources. You can configure various attributes as a part of these policies to restrict access to suspicious external users. Conditional access policies are not intended to be a primary authentication factor but are effective as a secondary defense mechanism.
As a network admin, you can secure access to your network by implementing different conditional access policies such as multi-factor authentication (MFA), role-based access control, attribute-based access control, and more. Also, you can customize a different set of rules applied only to specific apps on compliant devices.
General Conditional Signals and Decisions
There are many standard signals admins use to implement conditional access policies, such as:
- IP Ranges
- User’s Location
- Group/ User Membership
- Office Apps
- Microsoft Defender
- Real-Time Risk Detection
These signals form the basis for common decisions, such as multifactor authentication, so you can easily customize the level of security for sensitive applications. You can easily create policies using these signals, especially if you sense a suspicious user or device based on its IP address, login, or location.
To plan a successful conditional access deployment, all you need to do is define a policy in the Azure Portal and block or restrict suspicious users/devices based on these common signals.
How to Build a Conditional Access Policy in Azure AD
As we have seen, the Conditional Access Policy consists of building blocks of if-then statements combined to form a cohesive network access policy within the Azure framework. We can classify these building blocks into two main categories:
- Assignments
- Access Controls
Assignments
As the name suggests, Assignments are basically the who’s who of the Conditional Access Policies. In assignments, you can choose users, groups, and apps in your organization and assign policies based on their specific roles before allowing them access to organizational resources.
In Assignments, you can define the ultimate policies by combining multiple policies based on signals such as sign-in, device location, operating system, client application, etc. You can also assign specific access to particular cloud apps, including various Office products.
Access Controls
Just like the last section, Access Controls is also self-explanatory. As an admin, you grant or block access based on the policies already defined in the Assignments.
Grant Access
Here you simply grant access to the desired users, groups, devices, applications, etc., based on the existing policies in Conditional Access. There are many access options, such as requiring MFA, password resets, using Intune, and so on.
You can either use the “AND” logic to require all controls to be satisfied, or you can use the “OR” logic so that any one of the controls would suffice to give access to the entity.
Block Access
Like Grant Access, you simply block access to the desired users, groups, devices, applications, etc., based on the existing policies in Conditional Access. It is one of the critical control methods you can practice as a network admin to deter suspicious users, devices, or applications.
Security Threats in Azure AD
Although Azure AD facilitates the transition of businesses to the cloud without much hassle, it still has vulnerabilities in the form of login passwords. Although cloud technologies are generally more secure than on-premise alternatives because of resiliency and redundancy, bad actors progress in this arms race at an equal pace. They usually target the weakest link in the system, which is credential-based logins, using various methods like malware, phishing, ransomware, and much more.
There are efforts to mitigate the dangers posed by credentials, such as using additional forms of authentication like Azure AD MFA. Still, users chafe at friction in the authentication process and often neglect guidelines, eventually becoming victims of cyber-attacks.
There are a few other vulnerabilities in Azure AD Connect, which synchronizes Azure AD with the on-prem Windows AD using pass-through authentication methods. Attackers can register as guest users to gain initial access, then penetrate further into the network.. Some organizations also allow the PEAP-MSCHAPv2 protocol to be used for authentication, which has known vulnerabilities.
Using Azure AD Conditional Access with 802.1X
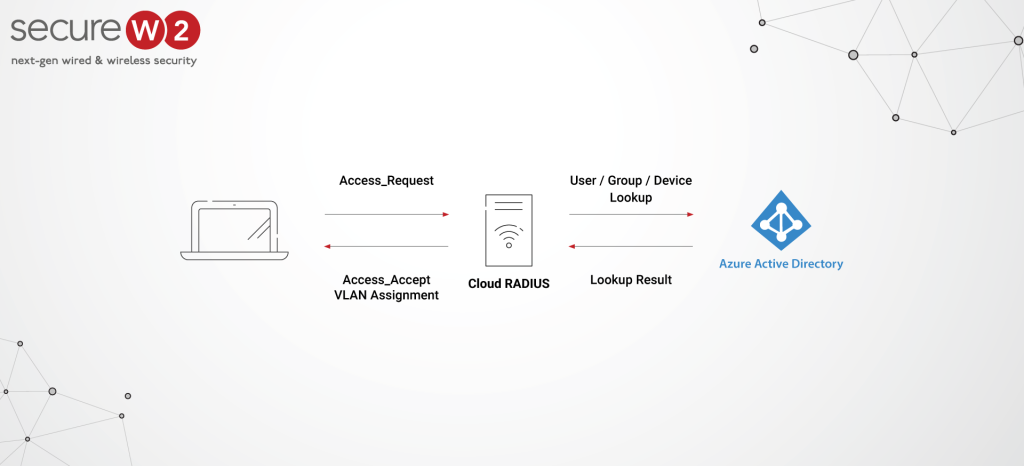 You can use Azure AD with 802.1x either by syncing it with the LDAP server (which uses Active Directory for an on-premise environment) or by creating a SAML application in the Azure portal for enrolling X.509 certificates in your network infrastructure.
You can use Azure AD with 802.1x either by syncing it with the LDAP server (which uses Active Directory for an on-premise environment) or by creating a SAML application in the Azure portal for enrolling X.509 certificates in your network infrastructure.
The first method comes in handy when you are not willing to migrate from your on-premises directory and want to use your existing infrastructure for network authentication. Although on-premise is far less secure and convenient than the cloud, we understand that it might not be easy for some organizations to migrate to the cloud all at once. Click here to see how we helped a customer deploy certificate-based authentication while maintaining support for legacy PEAP authentication.
The second option of using Azure AD for issuing certificates is much more secure as it eliminates almost all the on-premise and credential-based threats we already discussed above. For those out of the know, a digital certificate is a vastly more secure type of credential than passwords because it uses public-private key pairs as proof of ownership to perform asymmetric cryptography.
A Public Key Infrastructure (PKI) is required to issue and manage certificates, which has historically been considered tedious by many admins due to the complex configuration and integration. For successful certificate distribution, you need foolproof onboarding software for managed and unmanaged devices.
This is where SecureW2 comes to the rescue with user-friendly and robust Managed PKI Services that can manage the entire lifecycle of certificates via an intuitive single-pane management interface. Our GUI interface simplifies the distribution of certificate templates compared to AD CS by eliminating the need for certificate duplication with minimal steps.
Our policy engines are capable of enhancing the feature of Azure’s Conditional Access by empowering the admin to implement numerous access policies using many attributes. Also, we have a world-class Cloud RADIUS that provides native integration with Azure AD for enhanced access control, such that you can leverage all your existing policies for ultra-secure network authentication.
Additionally, with a certificate revocation list (CRL), our Cloud RADIUS servers can easily view every certificate that has been revoked and determine which certificates are permitted network access. As an admin, we assist you in downloading the CRL list, and you can easily view this list by downloading it periodically.
Interestingly for Microsoft Intune users, we also provide an enhancement feature that enables auto-revocation of digital certificates on expiry. This feature makes certificate revocation much simpler such that the instant there are any changes to your organization, such as people leaving the company, our PKI can work with Intune to ensure network access is updated instantly.
Enhancing Azure AD Conditional Access with SecureW2
Azure AD is the fulcrum of identity management in cloud-based Microsoft environments, and Conditional Access is the heart of its access management capabilities. Whether you are dealing with unmanaged devices or managed devices, we at SecureW2 have solutions that natively integrate with both.
Integrating with Securew2 gives you more customization for conditional access as well as many innovative features like Azure MFA auth, Intune auto revocation, windows hello for business login, and many more. Our managed PKI and RADIUS services can be set up quickly, costs a fraction of what on-prem solutions do, and has no infrastructure costs because it is all in the cloud.
Here’s our budget-friendly pricing and a one-stop gateway for your perfect onboarding solutions.