Key Points
- The EAP-TLS authentication flow involves a secure exchange of certificates between the user's device and the authentication server, ensuring a trusted connection.
- Compared to other EAP methods, EAP-TLS provides faster and more secure authentication, making it ideal for high-traffic networks.
- SecureW2's PKI and RADIUS service takes it a step further by validating the user/device in the IDP/MDM after the standard EAP-TLS certificate validation takes place.
For many organizations, the IEEE 802.1X authentication mechanism for Port-Based Network Access Control is the first line of defense against outside attack. It’s also one of the most commonly targeted attack vectors, which makes it a security priority.
One of the most common authentication methods used to send client information over-the-air via 802.1X is the Extensible Authentication Protocol (EAP). There are multiple EAP methods, and while each one utilizes the EAP tunnel to send information through an encrypted channel, only EAP-TLS supports certificate-based authentication, the gold standard of authentication.
Below we will detail the steps involved in the 802.1X EAP-TLS authentication flow and how it results in a secured network connection.
What’s Involved in EAP-TLS?
EAP-TLS authentication involves 3 parties, the supplicant (user’s device), the authenticator (switch or controller), and the authentication server (RADIUS server). The authentication process can first be broken down into 4 broad categories: initialization, initiation, negotiation, and authentication.
- Initialization – the authenticator detects a supplicant seeking to authenticate to the secure network.
- Initiation – essentially a process of saying hello between the supplicant, authenticator, and authentication server.
- Negotiation – the supplicant and authentication server exchange identifying information to determine whether the user should be authenticated to the network.
- Authentication – the process is completed, opening a port for the confirmed user to connect to the 802.1X network and browse securely.
EAP-TLS authentication is typically faster than credential-based authentication, and it occurs automatically without involvement from the user. When the device is in range of the secure network, it will initiate and complete the connection on its own. But what are the actual steps involved?
802.1X Flow Broken Down
Pictured here is a step-by-step image showing the 802.1X EAP-TLS authentication method broken down.
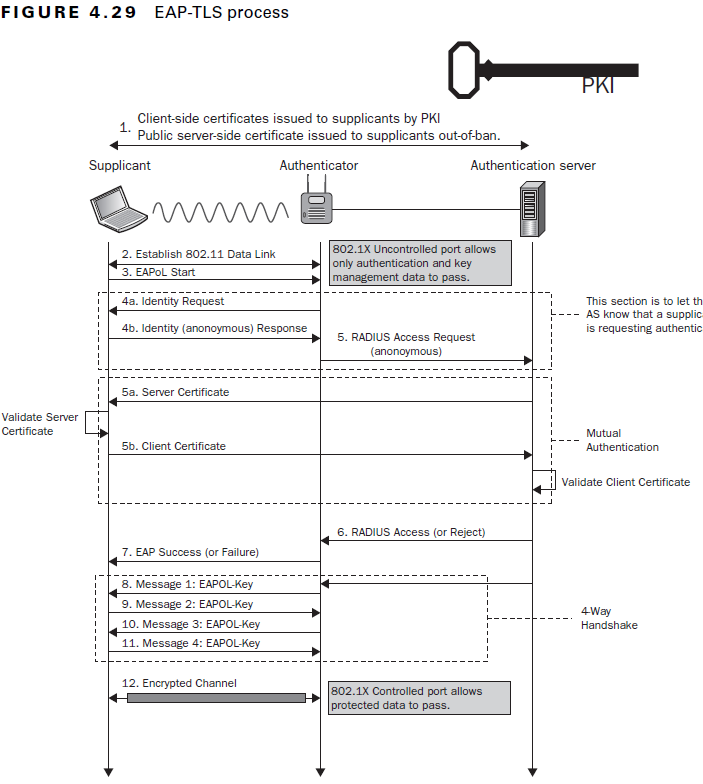
- Client-side certificates issued to supplicants by PKI, Public server-side certificate issued to supplicants out-of-band
- The supplicant and the authentication server begin by saying “hello” and prepare their certificates for authentication to establish a trusted connection.
- Establish 802.11 Data Link
- The supplicant establishes a connection to the authenticator. This will allow for a secure exchange of information between the two parties.
- EAPoL Start
- EAPoL (Extensible Authentication Protocol over LAN) indicates that information can be exchanged between all three parties over a secured LAN channel. Additionally, this is where the authentication method is determined – in this case, EAP-TLS.
- Identity Section
- 4a. Identity Request
- The supplicant requests the identity of the authenticator to ensure it is sending the client certificate to the correct place.
- 4b. Identity (anonymous) Response
- The authenticator requests that the supplicant identify itself.
- 4a. Identity Request
- RADIUS Access Request (anonymous)
- The information that identifies the supplicant and authenticator is sent to the RADIUS to confirm their identity and allow for authenticating information to be sent.
- 5a. Server Certificate
- The RADIUS sends its server certificate to confirm its identity through server certificate validation
- 5b. Client Certificate
- The supplicant validates the identity of the authentication server certificate. After validation, the supplicant sends its client certificate.
- RADIUS Access (or Reject)
- The RADIUS authentication server receives the client certificate and authenticates its identity as an approved network user. Depending on the user’s certificate, the RADIUS sends an Access or Reject message to the authenticator.
- EAP Success (or Failure)
- Based on the RADIUS Access or Reject message, the authenticator sends a Success or Failure message to the supplicant to indicate whether they have been approved or denied network access. If the message is Success, the switch port is opened for direct network communication between the supplicant and authentication server.
- Message 1: EAPOL-Key
- Message 2: EAPOL-Key
- Message 3: EAPOL-Key
- Message 4: EAPOL-Key
- The next step is a series of messages known as the EAPOL-Key exchange. It is a 4 step handshake between the authenticator and supplicant that generates encryption keys. These keys are used to encrypt information that will be sent over the wireless connection and ensures that all ongoing network communications are encrypted and cannot be read by outside parties.
- Linked here is a detailed list of keys that are generated during this handshake.
- Encrypted Channel
- The end result of EAP-TLS authentication is an encrypted channel of communication. The user is ready to access the secure network and utilize all resources available to them.
How to Implement EAP-TLS for 802.1X
Overall, the 802.1X EAP-TLS authentication process is extremely fast. The entire 12 steps occurs faster than human comprehension, and when compared to other methods such as PEAP-MSCHAPv2 and EAP-TTLS/PAP, the difference is still considerable. In high-traffic networks, EAP-TLS’ simpler authentication flow can prevent congestion at peak times.
If strong network security and a rapid, user-friendly authentication process are your cybersecurity goals, 802.1X is the answer. SecureW2 provides all the tools to configure 802.1X and simplify the distribution and management of digital certificates.
Check out our pricing page to see if your organization should have a certificate-based future.