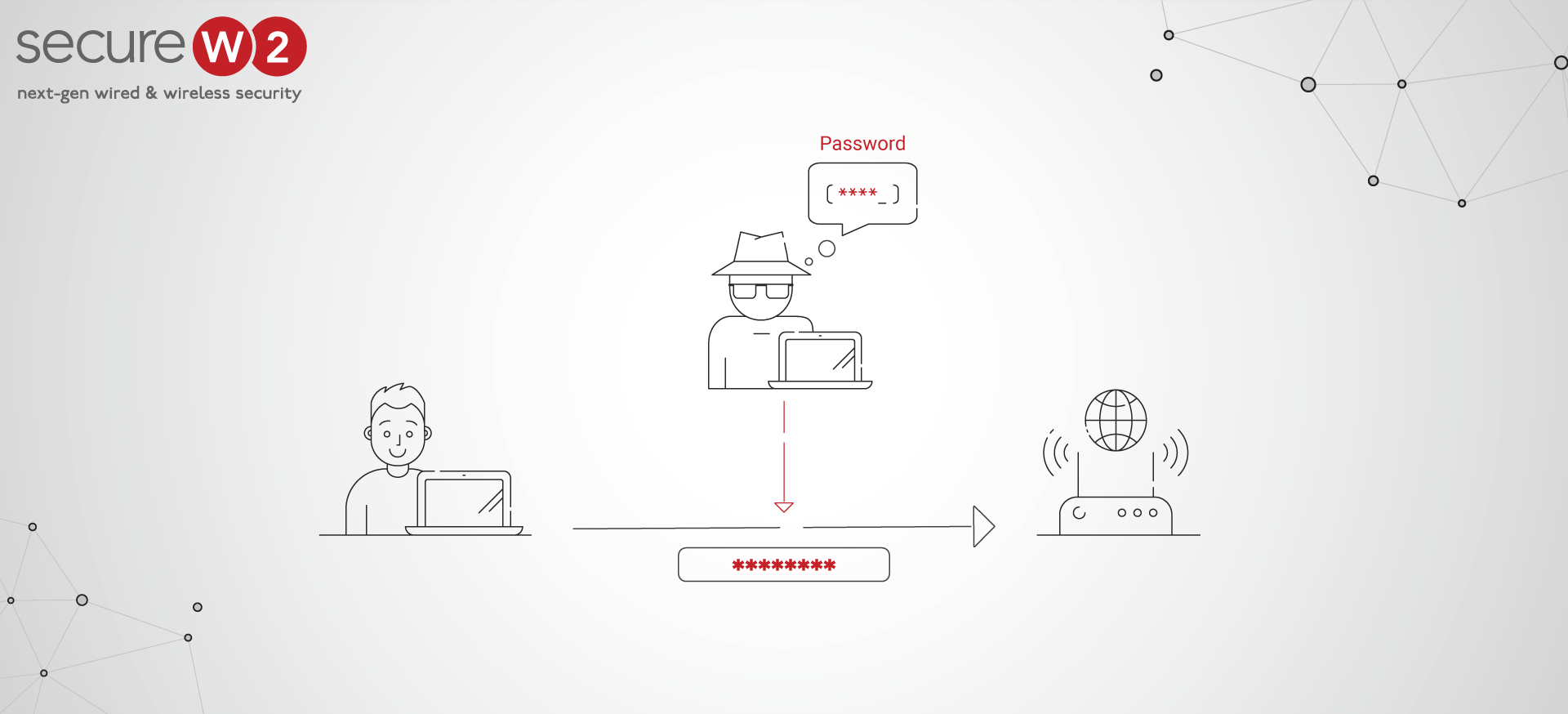
When designing a new network, there are countless features to consider that significantly impact the organization at large. Few functions of the network impact users more than the authentication method chosen by decision-makers.
If an organization seeks the best network security, it turns to WPA2-Enterprise with 802.1X authentication. Each time users connect to the network, their credentials are susceptible to over-the-air credential theft, so the process must be rigidly protected. However, authentication methods are not created equal, and some are more secure than others. Networks operating with an EAP-TTLS/PAP authentication method draw attention to themselves as targets for hackers because of the flawed systems under which EAP-TTLS/PAP operates. Many believe that EAP-TTLS/PAP should be avoided because glaring flaws exist in how it operates and newer authentication methods fill the security holes it leaves open.
What is EAP-Based Authentication?
EAP-based authentication is any authentication method that uses an EAP protocol to verify connections to a wireless network. The term doesn’t refer to the authentication mechanism itself (IE, usernames or passwords), and EAP is compatible with numerous different authentication mechanisms in use today.
However, some EAP protocols are more secure than others, which we’ll touch on in more detail later.
WHAT DOES EAP STAND FOR?
EAP stands for “extensible authentication protocol.” There are several different types of EAP methods used today for authenticating to wireless networks.
What’s Wrong with EAP-TTLS/PAP?
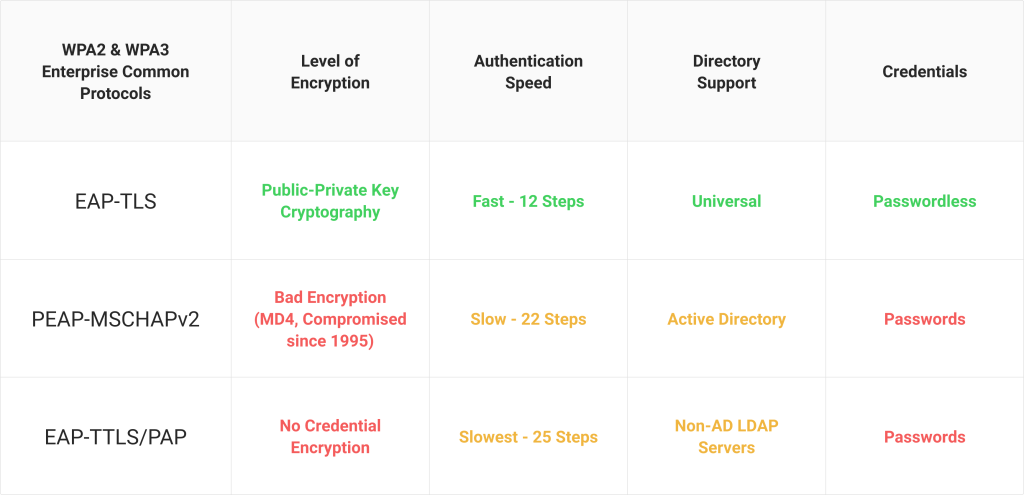
EAP-TTLS/PAP is a simple WPA2-Enterprise Wi-Fi authentication method that has been a system standard for many years. When a user wants to connect to the network, the device initiates communication with the network and confirms that it is the correct network by identifying the server certificate. Server certificate validation is one of the most important mechanisms to prevent over-the-air credential theft.
If the device can confirm the server certificate belongs to the known network, the user’s credentials are sent in an encrypted EAP tunnel. This sounds like a well-protected system for authenticating network users. The tunnel in which credentials are sent is encrypted and the user only sends credentials to a network that is confirmed by the device. Where does EAP-TTLS/PAP expose its weaknesses?
The process to configure a Windows device for a WPA2-Enterprise with server certificate validation enabled.
For the average network user, configuring their devices for EAP-TTLS/PAP can be a challenging process. It involves high-level IT knowledge to understand the steps involved, leading some to incorrectly configure the settings even if they’re provided a configuration guide. If just one device is misconfigured, the security benefits are thrown out the window because the user is sending their username through the air outside of the encrypted EAP tunnel.
Click here to read about how a global fintech leader eliminated their security vulnerabilities by upgrading to EAP-TLS certificate authentication with SecureW2.
Vulnerabilities of EAP-TTLS/PAP
There are simple credential theft tactics that anyone can perform against a network to steal this information, and if the attacker has obtained the private key of the RADIUS, they can decrypt SSL traffic and steal other credentials sent for authentication.
The primary attack method that exposes EAP-TTLS/PAP is a Man-In-The-Middle (MITM) attack. It is usually perpetrated by a user within the physical vicinity of the network or in a common area frequented by organization members, such as a coffee shop or bar. The attacker will configure an Evil Twin Access Point (AP) and RADIUS server for 802.1X authentication. Once configured, the next step is to spoof the desired SSID and push out a strong signal to fool users into unwittingly connecting to a hostile SSID. For authenticity, some may go as far as spoofing the legitimate MAC Address.
With the spoofed SSID in place, the attacker is ready to begin farming credentials. Users may attempt to connect to the spoofed network, or their device might automatically connect without the user knowing. Most devices are designed to seek out the network with the strongest signal, so the key for the hostile user to is to simply project a powerful signal. The device will attempt to connect and the SSID seems legitimate, but unbeknownst to the user, it’s a hostile SSID that’s farming stolen credentials.
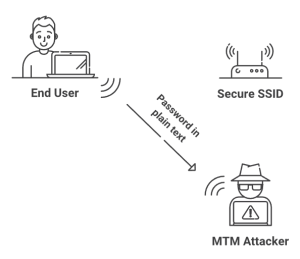
Visualization of a Man-In-The-Middle attack, which can be exceptionally harmful due to EAP-TTLS/PAP sending credentials in cleartext.
A major flaw with EAP-TTLS/PAP is that credentials are sent over-the-air in “cleartext”, meaning they are not encrypted and can be read plainly. If a user is not configured correctly for server certificate validation, anyone that farms credentials from a network using EAP-TTLS/PAP strikes gold; each set of credentials comes to them in cleartext and is ready to be reused for their purposes.
When someone steals encrypted credentials, they require additional tools and time to get them into a usable state. Although an experienced hacker would have the necessary tools and know how, this slowdown in the process could be key to giving time to discover the leak.
When credentials are sent in cleartext, calamity could strike from something as simple as an error in the EAP encryption process caused by a misconfiguration by one user. If this situation should occur, credentials would be flying through the air in cleartext, ready for anyone intercept. This flagrant weakness in EAP-TTLS/PAP could spell doom from the slightest hiccup in network security.
Underlying this problem is the fact that many people recycle their passwords. By stealing one credential, attackers could essentially be stealing the keys to your kingdom, allowing them to extend their access even further into your network. Unfortunately, implementing sophisticated password requirements has the drawback of irritating your end-users. So, where is the balance between end-user satisfaction and security?
Better Alternatives to EAP-TTLS/PAP
SecureW2 began as an open-source supplicant for Windows 7 devices to support EAP-TTLS/PAP, but the misuse of the protocol became unavoidable to the point that we now recommend against its use. The method is often misconfigured by allowing users to self-configure, and overall is a weak form of authentication. For stronger security, none are better than an EAP-TLS, certificate-based authentication method.
First and foremost, EAP-TLS as an authentication method is highly secure and prepared to thwart any ill-advised attacks on the network. Information sent over-the-air is protected in an encrypted EAP tunnel, but for added protection, all information sent through the tunnel is itself encrypted. If a MITM attack is launched, the data obtained is encrypted and unusable in that state.
Certificate-based EAP-TLS ties certificates to specific devices that cannot be shared between multiple users like passwords. The benefit to this is heightened network visibility. Since certificates can’t be shared, you can be sure that each device on your network is what it says it is.
To protect even further against attacks, it’s highly recommended that the network be configured for server certificate validation. This security measure requires each connecting user to authenticate the RADIUS server certificate to ensure that information is only ever sent to the correct SSID. Both the device and network are accurately identified by their certificates, negating the possibility that anything is sent to an illegitimate SSID.
Historically, certificates were not deployed mainstream because of the high-level configuration process. But because of their value to security, onboarding software has been developed to simplify the process; specifically, SecureW2’s onboarding solution. Users that seek network access connect and are prompted to complete an onboarding procedure with a few, easy steps. Once completed, their identity is confirmed, and they are issued a certificate. The user now has unfettered, secure network access for the life of the certificate. You can see what your network authentication could potentially look like with the diagram above.
Don’t Compromise Your Network with EAP-TTLS/PAP
The method of authentication used for the network has an enormous impact on the overall security of your organization. Each day, network users are going to reconnect to the network and require a reliable and secure method of authentication. If the process to connect to the secure SSID is susceptible to outside attacks, the security measures of the entire network can be compromised.
Just one set of credentials is needed to access the network, so it’s vital to deploy a foolproof authentication process. SecureW2 offers affordable options for organizations of all shapes and sizes, including a managed PKI and Cloud RADIUS server designed from the ground up for passwordless authentication. Click here to inquire about pricing.[/vc_column_text][/vc_column][/vc_row]