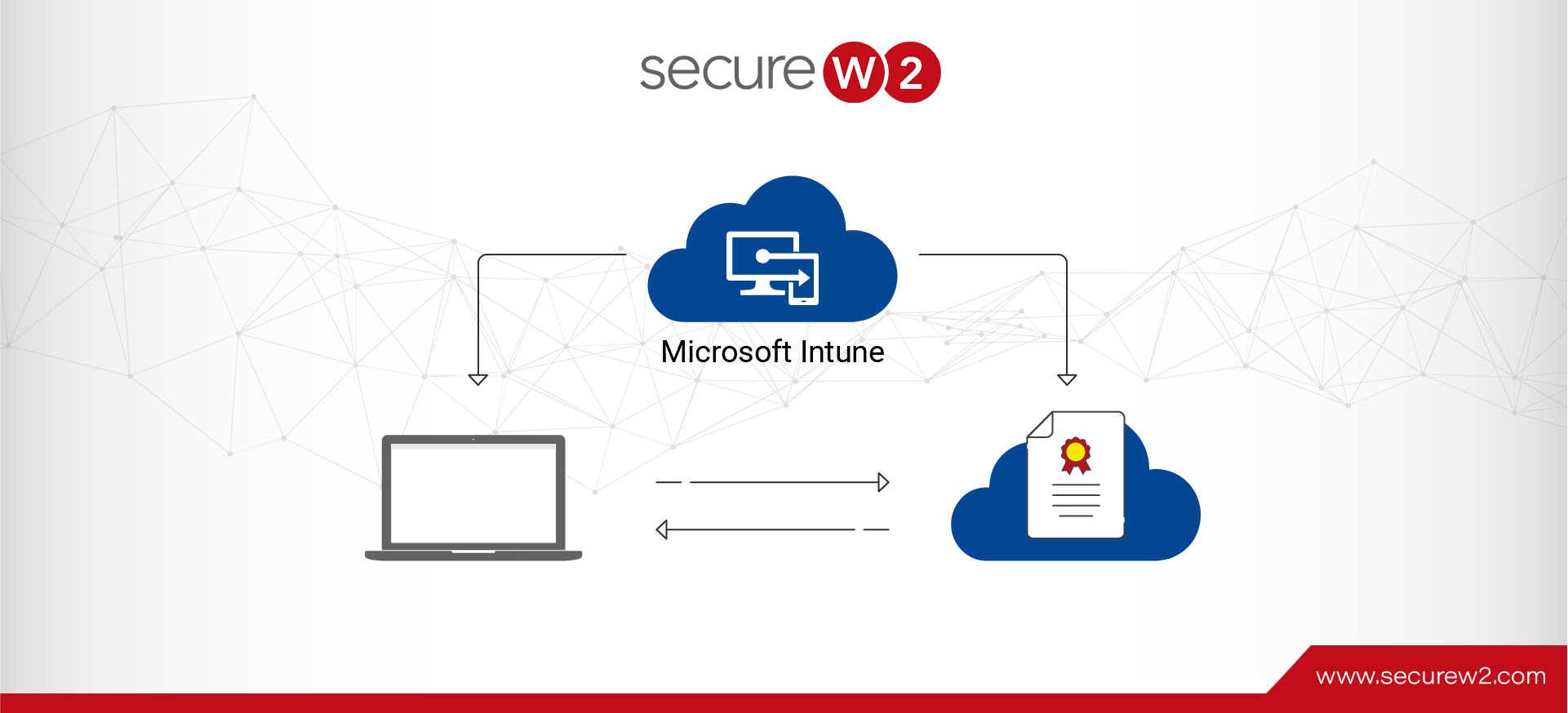
Configuration Guide For WPA2-Enterprise On Operating Systems
Automation is critical for a positive user experience; the faster a monotonous task can be finished, the more time users can focus on important activities. Network authentication can operate the same way as long as you have the right tools. ... Read More