Key Points
- WEP encryption, designed to secure wireless networks, is outdated and vulnerable to various attacks, exposing users to unauthorized access and data breaches.
- WEP's flaws stem from its weak RC4 encryption, limited key space, and static shared keys, which make it susceptible to replay and brute-force attacks.
- WPA2 and WPA3 offer stronger encryption and integrity checks, addressing WEP's vulnerabilities and providing a secure foundation for wireless networks.
- SecureW2’s JoinNow PKI simplifies transitioning to certificate-based security, eliminating password-based risks, while Cloud RADIUS integrates seamlessly with cloud identity providers, enabling passwordless, secure network authentication.
As we all know, wireless networks simplify numerous business procedures while providing trustworthy security. As a result, a user must be familiar with wireless networks and how they might facilitate corporate interactions. The wireless network can transport data (or information) over a large region, making wireless data transfers easily interceptable. Information (or data) is a crucial resource for any organization today.
This might be one reason why cybercriminals are increasing since hackers are constantly looking for new techniques and tools to access your system and steal that information. Ensuring the organization’s devices, networks, and servers are effectively protected is critical. This article will examine how effective Wired Equivalent Privacy encryption is in securing your organization’s wireless networks.
What is WEP (Wired Equivalent Privacy)?
WEP (wired equivalent privacy) is an encryption method introduced by the Institute of Electrical and Electronics Engineers (IEEE) as part of the IEEE 802.11 internet standard, certified in 1997.
WEP (wired equivalent privacy) was designed to protect and maintain data secrecy at the same level as a regular wired network. Wireless connections, by their nature, transfer data via radio waves that can be intercepted. WEP encrypts this data, ensuring that the threat actor cannot decipher its contents, such as via an MITM attack, even if intercepted. This reassures us about the effectiveness of WEP in maintaining data secrecy.
Due to US government limits on cryptographic technology exporting, WEP key sizes were initially restricted to a 40-bit key (known as WEP-40) for the 64-bit WEP protocol. However, as these constraints were loosened, the enhanced 128-bit WEP protocol with a 104-bit key (WEP-104) was launched. This evolution in WEP technology, encrypting data with the RC4 stream cipher and verifying it with the CRC-32 checksum, is a testament to the continuous efforts to enhance the security of wireless networks.
The 64-bit WEP key consists of ten hexadecimal (base 16) alphanumeric characters, each representing four bits, whereas the 128-bit WEP key consists of 26 hexadecimal alphanumeric characters. These characters are either numerals (0–9) or letters A–F. Using WEP, all traffic is encrypted as a single key, which utilizes a static key. This key is used to connect PCs to a wireless-secured network. Computers on this network can exchange encrypted communications.
How Does WEP Work?
The Wired Equivalent Privacy protocol encrypts data delivered over the WLAN, providing security equivalent to that of a wired network. Data encryption secures the fragile wireless link between clients and access points.
After WEP protects wireless data transmissions, various LAN security techniques can protect privacy and secrecy. These include password security, end-to-end encryption, virtual private networks, and authentication.
The basic network security services protocol for wireless networks includes the following:
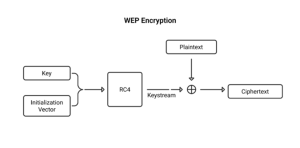
Privacy—WEP secured wireless data using a 64-bit key and the RC4 stream encryption technique. Later protocol versions strengthened security by supporting 128-bit and 256-bit keys. WEP employs a 24-bit initialization vector, yielding effective 40, 104, and 232 key lengths.
Data Integrity—WEP uses the CRC-32 checksum mechanism to ensure that transmitted data is intact at its destination. The sender employs the CRC-32 cyclic redundancy check to build a 32-bit hash value from a data series. Upon receipt, the receiver uses the identical check. If the two values vary, the recipient may request a retransmission.
Authentication – WEP authenticates clients when they initially connect to a wireless network access point. It permits the authentication of wireless clients with the following two mechanisms:
- Open System Authentication – Wi-Fi-connected systems can utilize OSA to connect to any WEP network access point if they use a service set identifier matching the access point’s SSID.
- Shared Key Authentication – Wi-Fi-connected systems employ SKA’s four-step challenge-response process to authenticate.
Drawbacks to WEP
WEP is extensively adopted and deployed, although it has major security flaws. This includes:
- Stream Cipher – When a key is repeated, encryption methods used on data streams, known as stream ciphers, become vulnerable to attack. The protocol’s limited key space makes it hard to avoid recycling keys.
- RC4 Weaknesses—The RC4 algorithm has been scrutinized for cryptographic flaws and is no longer considered safe.
- Optional—The protocol is optional as conceived. Because of this, many users neglect to activate it when installing WEP-enabled devices.
- Shared Key – These systems are configured by default to utilize a single shared key for all users. Individual users cannot be authenticated when they all share the same key.
WEP was smashed by these bugs. Shortly after introducing the Wi-Fi Protected Access (WPA) protocol in 2003, most of the standard committees decided to deprecate the protocol.
Risks Associated with WEP Protocol
WEP security presents substantial risks to enterprises and individuals owing to its vulnerability to unauthorized network access and data breaches. With WEP’s poor encryption mechanisms and vulnerability to numerous attacks, unauthorized users may intercept and decode transmitted data, obtaining unfettered network access. This jeopardizes critical information security and opens the door to harmful actions like eavesdropping, data manipulation, and unauthorized network access. Businesses may suffer significant consequences, including monetary losses, brand harm, and even legal liability, if confidential or user information is stolen.
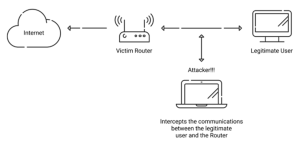
Furthermore, the consequences of using WEP-secured networks go beyond obvious security failures. Businesses may experience operational disruptions and productivity losses due to compromised network integrity. Employees may unwittingly connect to rogue access points or become victims of phishing attempts, aggravating security vulnerabilities. Individuals who use WEP to safeguard their home networks are likewise vulnerable, as hackers increasingly target residential Wi-Fi networks for personal data theft and identity fraud. Finally, the continuous use of WEP security exposes enterprises and people to various avoidable security risks, emphasizing the critical need to shift to stronger and current security standards.
WEP vs. WPA (Wi-Fi Protected Access)
In 1997, the IEEE established Wired Equivalent Privacy as part of the 802.11 wireless networking standard. Five years later, the IEEE suggested WPA as a successor. Throughout WEP’s brief existence, attempts to patch it failed to provide a safe way to access wireless networks. In 2004, WPA2 formally took its place.
WEP variations and enhanced WPA versions comprise the subsequent protocols:
WEP2
Following the discovery of security flaws, the IEEE standards were modified to mandate the use of Kerberos authentication and extend the WEP key length to 128 bits. Nevertheless, WEP was removed from the standard because these modifications were insufficient to increase security.
WEP Plus vs.WEP+
Integrated circuit component manufacturer Agere Systems created this proprietary version. WEP+ removed weak keys from the key space. Still, there were basic problems, and WEP+ was only utilized by Agere Systems Wi-Fi equipment.
WPA
The initial iteration of WPA extended the key length to 128 bits and introduced the Temporal Key Integrity Protocol in place of the CRC-32 integrity check. WPA, however, continues to employ the RC4 encryption technique and has some of WEP’s flaws.
WPA2
Stronger encryption and integrity protection were implemented with this WPA upgrade. It encrypts and verifies the integrity of wireless messages using the Advanced Encryption Standard algorithm using the Counter Mode Cypher Block Chaining Message Authentication Code Protocol. WPA2 is available in the subsequent two modes:
- WPA2 Enterprise – WPA2-Enterprise needs a Remote Authentication Dial-In User Service authentication server to authenticate users.
- WPA2 PSK – WPA2-Pre-Shared Key uses pre-shared keys that are provided to authorized users and are meant for personal usage only.
WPA3
In 2018, the most recent iteration of WPA was made accessible. It offers users of wireless networks far better security. WPA3 enhancements consist of:
- Enhanced encryption for both personal and business use;
- Enhanced personal mode authentication and
- Ideal forward secrecy for communications in private mode.
Transitioning to Robust Network Security
Switching from WEP to more secure choices like WPA2 or WPA3 requires overcoming several obstacles, such as changing network infrastructure and guaranteeing compatibility with current devices. Network migrations may be challenging for individuals and organizations, particularly if the former lacks the resources or technical know-how needed for a successful outcome.
Furthermore, users may be discouraged from adopting newer security protocols due to the possibility of network operations being disrupted during the conversion process. In this sense, programs like JoinNow PKI and Cloud RADIUS provide invaluable support by streamlining the transfer procedure and resolving WEP’s intrinsic shortcomings.
A complete Public-Key Infrastructure (PKI) solution is offered by SecureW2’s JoinNow PKI, making it easier to implement certificate-driven network security. JoinNow PKI removes the need for cumbersome password-based authentication techniques by automating the enrollment and administration of digital certificates. This simplifies the authentication process for desktop login, VPN, and Wi-Fi connections. It improves security while giving organizations useful contextual data on people and devices, allowing them to impose strict access controls and guarantee legal compliance. Furthermore, JoinNow PKI easily connects with current Identity and Device Management systems, enabling businesses to use their current infrastructure and policies to transition smoothly to more robust security measures.
Conversely, SecureW2’s Cloud RADIUS provides a cutting-edge password-free authentication method tailored for cloud identities. Cloud RADIUS improves network security by reducing the need for outdated password-based authentication techniques and reducing the possibility of credential theft. By integrating natively with cloud identity providers like Google, Okta, and Azure AD, Cloud RADIUS allows enterprises to use their current rules and user context for secure network authentication.
In addition, Cloud RADIUS offers instantaneous device removal from the network and real-time intelligence to enforce access regulations, guaranteeing ongoing defense against unwanted access attempts. JoinNow PKI and Cloud RADIUS work together to enable enterprises to confidently move from WEP to more secure choices like WPA2, streamlining the migration process and enhancing network security.
Secure Your Wireless Network
WEP security weaknesses, such as unauthorized network access and data leaks, threaten organizations and individuals. WEP is unsuitable for protecting Wi-Fi networks in the current threat landscape due to its outdated encryption techniques and vulnerability to several attacks. Consequently, people and organizations must understand how important it is to switch to the latest security protocols, like WPA2 and WPA3. By upgrading to these more robust security standards, users can reduce the risks associated with WEP and guarantee the integrity and confidentiality of their wireless connections.
Switching to more secure Wi-Fi protocols has never been simpler thanks to SecureW2’s Join Now PKI, which simplifies certificate-driven network security, and Cloud RADIUS’s cutting-edge passwordless authentication. These solutions offer enhanced features and capabilities to fortify your network’s defenses against cyber attacks, all while streamlining the migration process.
Contact us now to learn how SecureW2 can help your organization achieve reliable and smooth Wi-Fi security.