Key Points
- RADIUS server authentication ensures that only authorized users and devices can access your network, preventing unauthorized entry.
- Users can authenticate through passwords or more secure digital certificates, with certificate-based authentication offering stronger protection against modern threats.
- RadSec, or RADIUS over TLS, strengthens RADIUS security by encrypting communications between the RADIUS server and access points, especially in roaming environments.
- SecureW2’s Cloud RADIUS offers an easy-to-deploy, cost-effective solution for organizations, eliminating the need for complex on-premise setups.
Your Wi-Fi or VPN wouldn’t exactly be secure if anyone could access them whenever they wanted. This is why authentication protocols are used, including the RADIUS protocol: to safeguard your network and prevent unauthorized access.
RADIUS servers are a crucial component of an 802.1X network, which is the gold standard for network security – a standard we’ve helped many customers reach. RADIUS server authentication provides the certainty you need that only legitimate parties are accessing your resources, but how does this authentication actually work?
In this guide, we’ll take an in-depth look at precisely how RADIUS works to safeguard your network, and why it matters.
What is the RADIUS Protocol?
Developed in the 90’s, RADIUS is an acronym that stands for Remote Authentication Dial-In User Service, although it is also often known as an AAA (Authentication, Authorization, and Accounting) server. The latter name provides a nice summary of what RADIUS servers do: granting/denying access to your network, providing varying levels of authorization to users, and keeping a record of all attempts to establish a network connection.
The easiest way to imagine where RADIUS fits into your network is to picture a bouncer at the door to a club. When someone tries to connect to your Wi-Fi or VPN, the RADIUS confirms that they should have access first by checking their credentials (username and password) or certificate. Then, the RADIUS rejects or accepts the user accordingly.
RADIUS Components
What do you need to deploy RADIUS in your own organization? Luckily, the answer is “not too much.” All you’ll need is the following:
- Server space
- A network connection/network access server
- Clients/supplicants
The server space is to establish and configure the RADIUS itself. You’ll also need a way to get users onto the network, which is what the network access server is for. Finally, you’ll require devices and users with supplicants to request network access. A supplicant is a piece of software installed in the network stack. Fortunately, almost all devices we might expect to connect to a wireless network have a supplicant built-in.
Of course, you’ll also need the expertise to set up and maintain a RADIUS server, which can be difficult; this is why it’s often simpler to use a managed RADIUS service such as Cloud RADIUS. Rather than build your own RADIUS server from scratch, Cloud RADIUS provides you a truly plug-and-play experience that integrates seamlessly with any of your existing infrastructure.
How Does RADIUS Server Authentication Work?
RADIUS server authentication can verify users or devices through two different methods: X.509 digital certificates or credentials. The actual RADIUS authentication procedure varies a bit depending on which method is used.
RADIUS Credential Authentication Flow
If you’re using credentials, RADIUS can confirm your username and password by referencing your directory (Identity Provider or IDP). The problem is that passwords are vulnerable in the modern cybersecurity landscape; over 60% of people reuse their passwords, and simple social engineering methods like phishing – which allow hackers with little to no technical knowledge to farm passwords – are on the rise.
RADIUS Certificate Authentication Flow
Digital certificates are a much more secure alternative. RADIUS server authentication with digital certificates is also a different, multi-step process.
First, your RADIUS server confirms that the certificate isn’t expired. If it’s unexpired, the RADIUS will then check the Certificate Revocation List (CRL) to ensure that the certificate has not been previously revoked.
Generally, as long as the certificate is neither expired nor revoked, the client is then granted access. However, RADIUS servers that support Identity Lookup such as Cloud RADIUS have an additional step they take for extra security. During the identity lookup stage of RADIUS server authentication, the RADIUS communicates with your directory, using information contained in the certificate to look up the user in your directory
At this point of RADIUS server authentication, it can determine what level of authorization you have based on what group you’re in in the IDP. For example, if you’re in your organization’s financial department, your organization may have granted you access to different resources and systems from someone in the HR department. This is called role-based access control, a cornerstone of Zero Trust Network Access (ZTNA).
Is RADIUS server authentication encrypted?
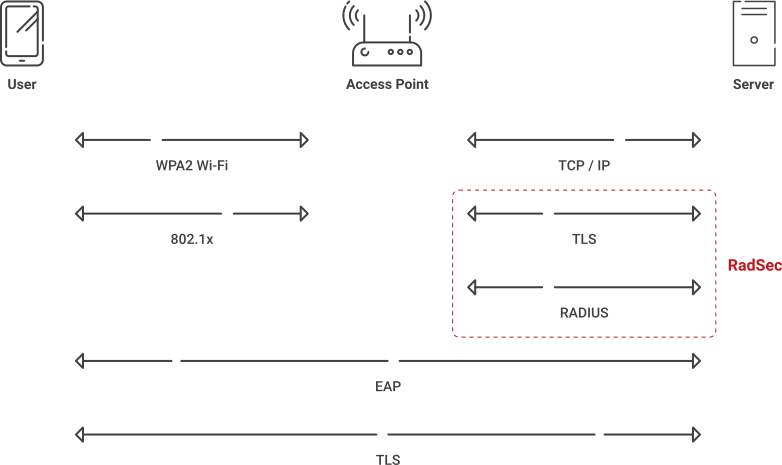
RADIUS certainly boosts the security of your network, but it’s not a one-stop solution for authentication security. The RADIUS protocol relies on the encryption of the credentials themselves when communicating them over the air. In some scenarios, that’s not sufficient.
That’s where RadSec, also known as RADIUS over TLS, comes in. RadSec is an 802.11x protocol for transporting RADIUS packets through TCP (Transmission Control Protocol) and TLS (Transport Layer Security). In a nutshell, it increases the security of RADIUS even further by encrypting the communication between the RADIUS server and the access point (or switch).
This is especially useful in roaming environments. It means that, no matter where you are, when you authenticate to the RADIUS server, your communication with it will be shielded from the view of malicious third parties. Check out our introduction to RadSec to learn more.
How to Set up RADIUS Server Authentication
In the past, opting to use RADIUS server authentication meant that you had to build your own on-premise server. This can be inconvenient for a number of reasons:
- It requires expertise and experience with the RADIUS protocol.
- If you didn’t have the expertise, you may need to hire additional personnel.
- You need both equipment (physical servers) and space for that equipment.
- Setting up the server takes time initially, and maintaining it costs time perpetually
Some organizations still use on-premise RADIUS servers, but nowadays, there are also other options. Thanks to managed RADIUS services like Cloud RADIUS, the process is much simpler and more cost-effective.
Of course, the process of setting up a wireless RADIUS server varies based on your Wi-Fi provider, but the general process with SecureW2’s Cloud RADIUS is outlined below:
- Create a RADIUS profile in your wireless controller.
- Navigate to AAA management, then AAA configuration in the SecureW2 Management Portal.
- Note the Primary IP Address, Port, and Shared Secret.
- Input this information into the RADIUS profile you created.
- Save the new RADIUS profile.
You can learn more about configuring RADIUS with an AP in one of our integration guides.
Cloud RADIUS: RADIUS Server Authentication, Simplified
It’s vital that you ensure only authorized users access your network, and a RADIUS server is inarguably the best solution. In addition to preventing unauthorized access, RADIUS makes it possible for you to utilize the information already contained in your IDP for role-based access control and other policy enforcement options.
And if you’re worried that this sounds complicated to set up, we have good news for you: the security offered by RADIUS server authentication doesn’t have to be difficult to achieve, thanks to Cloud RADIUS. Check out our pricing to see how affordable and simple RADIUS security can be for your organization.