You Don’t Need LDAP for 802.1X Anymore
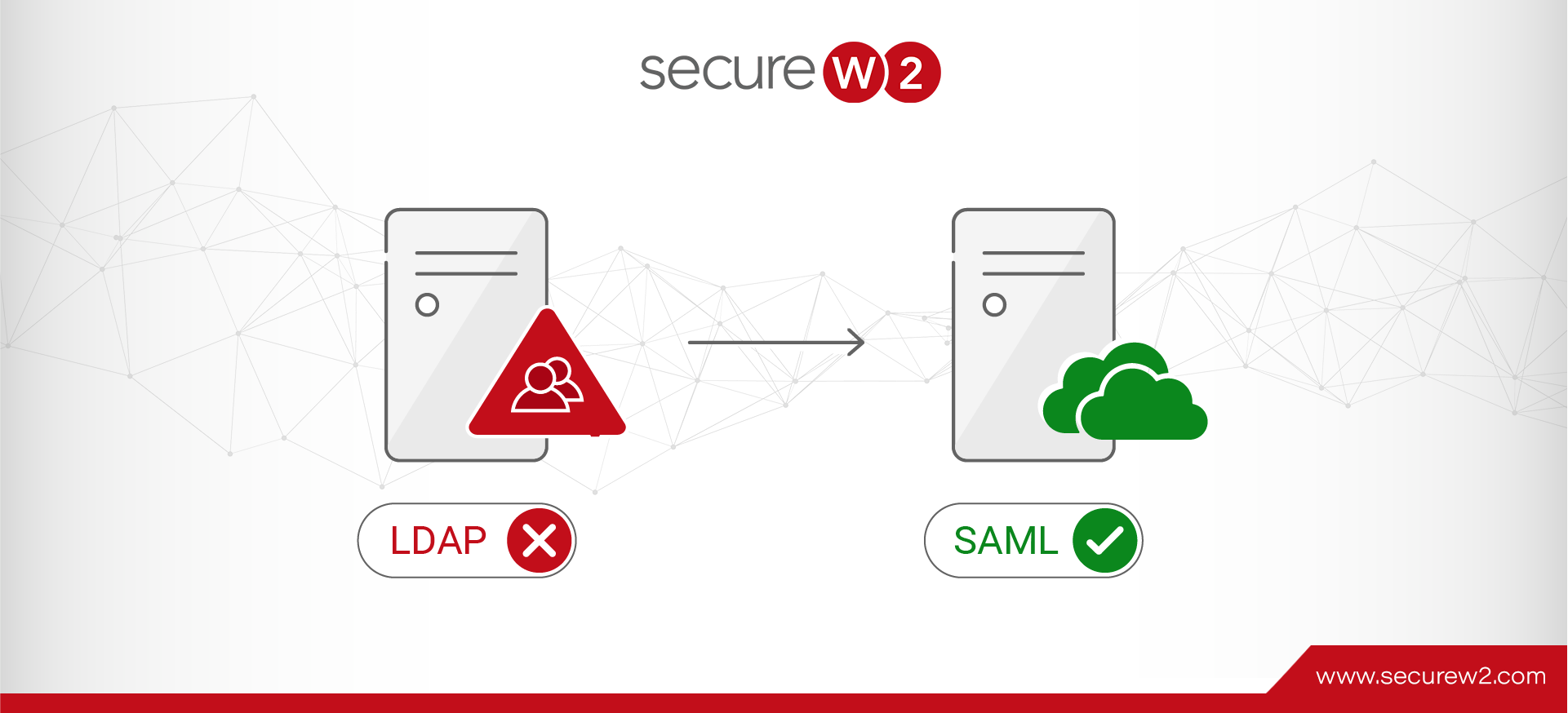
Without protection, your organization’s network is vulnerable to cyber attacks. The 802.1X protocol heightens network security by introducing RADIUS servers for authentication, and Lightweight Directory Access Protocol (LDAP) has commonly been used alongside RADIUS due to its ability to quickly ... Read More