Key Points
- Differentiating between device-based and user-based RADIUS lookups is critical for successful Zero Trust security, particularly in mixed-device scenarios.
- Cloud RADIUS improves authentication security by dynamically comparing user and device IDs to a directory during authentication.
- SecureW2's JoinNow platform includes everything you need to dynamically look up both users and devices in your cloud Identity Infrastructure, including our powerful Cloud RADIUS and managed PKi services.
If all the users in your network fit into one single group, RADIUS authentication would be simple. Alas, things aren’t that easy; administrators often find themselves needing to specifically distinguish between devices and users, especially in an organization with both BYOD/unmanaged devices and managed devices. That’s why most organizations rely on certificate-based RADIUS authentication. The certificate is locked on the hardware of a device, confirming Device Trust and establishing a connection with an identity. The RADIUS server can verify the identity by performing a lookup in the directory during authentication.
Cloud RADIUS is a RADIUS service that is capable of performing both device-based and user-based lookups at the moment of authentication. The end result is that it can apply policy changes the moment you update a user’s or device’s information in your directory.
But how, exactly, does RADIUS lookup differentiate between users and devices, and why does it matter?
What is RADIUS Lookup?
In a nutshell, RADIUS lookup simply means that the RADIUS is actively looking up the user or device in your Identity Provider (IDP)/directory. Lookup can occur either during or after authentication depending on the type of credentials you’re using.
RADIUS Lookup with Certificates vs Passwords
When you’re using password-based credentials, the lookup step is already baked into the authentication. This is because, in order to authenticate in the first place, the account status must be checked every time the username and password are entered. Should the account no longer exist or the password be invalid, the password authentication itself will fail.
Cloud RADIUS, however, was designed specifically for use with digital certificates, which are more secure than passwords. With digital certificates, lookup technically occurs after authentication is completed. In other words, once Cloud RADIUS has verified the certificate isn’t on the Certificate Revocation List (CRL), it goes the extra mile by checking the user or device in your IDP.
It’s essentially an extra step added to heighten the security of your certificates. This latter definition – that RADIUS lookup occurs post-authentication – is what we’ll be working with for the purposes of this article.
Device-Based vs User-Based RADIUS Lookup
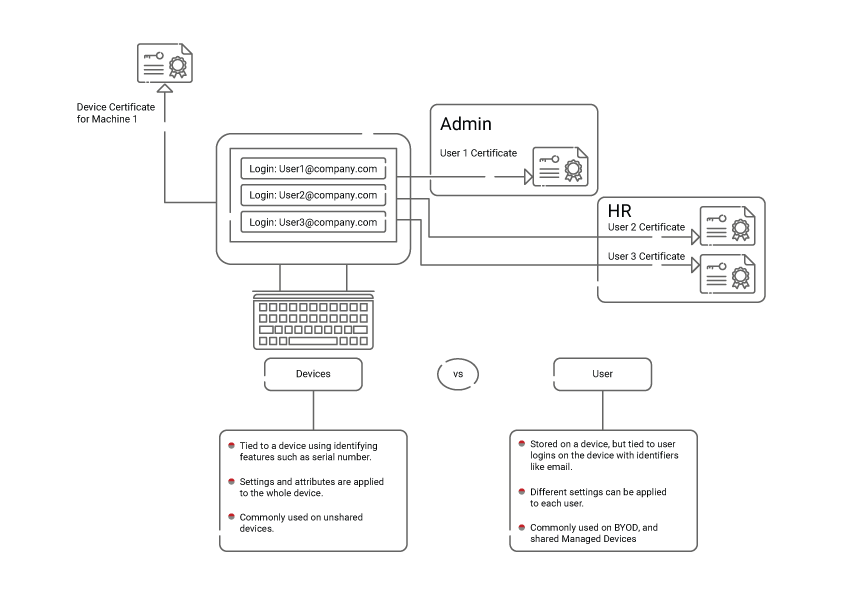
User vs Device Certificates
There are two different types of lookup the RADIUS can perform: user or device. Which type of lookup is performed mostly depends on the directory/IDP and MDM your organization uses.
Some IDPs are designed to store information tailored to users or devices. Examples include the following:
- Okta, which specifically stores user objects.
- Azure Active Directory can store both user and device objects.
- Google generally stores only user objects, but can store device objects in Chromebook environments.
- Active Directory stores both user and device objects together.
So, whether user or device lookup will occur depends on a handful of factors:
- What information is stored, and where it’s stored in your directory.
- Whether the information is accessible.
- If the RADIUS service in question supports the type of lookup.
With that being said, let’s take a closer look at user-based RADIUS lookup and device-based RADIUS lookup individually.
User Lookup
The type of lookup is primarily determined by the identifiers the RADIUS uses to verify the user or device.
Cloud RADIUS was designed from the ground up for use with certificates, which can be issued to both users and devices. It can look up both user and device certificates in your IDP, regardless of whether your IDP is more user-centric or device-centric. This is because our PKI, JoinNow Connector PKI, allows you to encode a user value onto a machine certificate and vice versa.
The main difference in these types of lookups is which identifier the RADIUS will take from the user’s or device’s certificate to compare with what’s in the IDP.
For user certificates, we recommend using any of the following attributes supported by Cloud RADIUS to verify a user’s identity:
- Username
- Common Name
- SAN-UPN
- SAN-Email
Device Lookup
On the other hand, for device certificates, SecureW2 keeps track of the Client ID and Computer Identity by storing them in our Policy database. This information is pulled up during the RADIUS lookup and then compared with whatever is in your IDP for that Client ID or Computer Identity.
For device/machine certificates, we recommend using any of the following attributes supported by Cloud RADIUS to verify a device’s identity:
- Client ID
- Computer Identity
That being said, there are some situations where you want to do a User Lookup, on a device/machine certificate. Okta, for example, is an IDP that focuses on user identifiers. Because the JoinNow Connector PKI allows you to infinitely customize certificate templates, you can issue device/machine certificates with user attributes (email, username) encoded in them. This allows you to do a user-based RADIUS lookup on a device/machine-issued certificate.
RADIUS Lookup Policies and Why They Matter
Typically, with certificate-based authentication (CBA), RADIUS servers authenticate a certificate by simply checking whether the certificate is on the Certificate Revocation List. The RADIUS isn’t able to get much information from the CRL – just if a certificate has been revoked.
With lookup, the RADIUS is able to access much more in-depth information about each user or device attempting to access your resources. This allows the RADIUS to dynamically apply different policies based on the data contained in your IDP.
Cloud RADIUS gives administrators a wide array of policies to create and apply during lookup. For example, you can choose to accept or deny users and devices based on the time of day. You can also accept or deny access based on the type of device, such as not allowing BYODs access to the network. Or, if you need to be more specific, you can only allow devices with a particular operating system.
Effortlessly Issue and Authenticate User or Device Certificates with SecureW2
Ensuring users and devices are segmented into proper groups is paramount to implementing Zero Trust; not only does this help with organization, but it also empowers administrators to create group and network access control policies. Issuing certificates to identify both users and devices provides critical identity context around each connection, and SecureW2 can help you get there with our JoinNow suite.
Our JoinNow Connector PKI will give you all the tools you need to manage user and device certificates, but that’s only the part of the equation. Once your certificates are deployed, you can authenticate them with Cloud RADIUS, a vendor-neutral RADIUS service that can dynamically look up both user and device certificates in your IDP at the moment of authentication.
No matter what your infrastructure consists of, our PKI and RADIUS can fit in, keeping you from having to make inconvenient forklift upgrades. Schedule a demo with us to see firsthand the solutions we have for you.