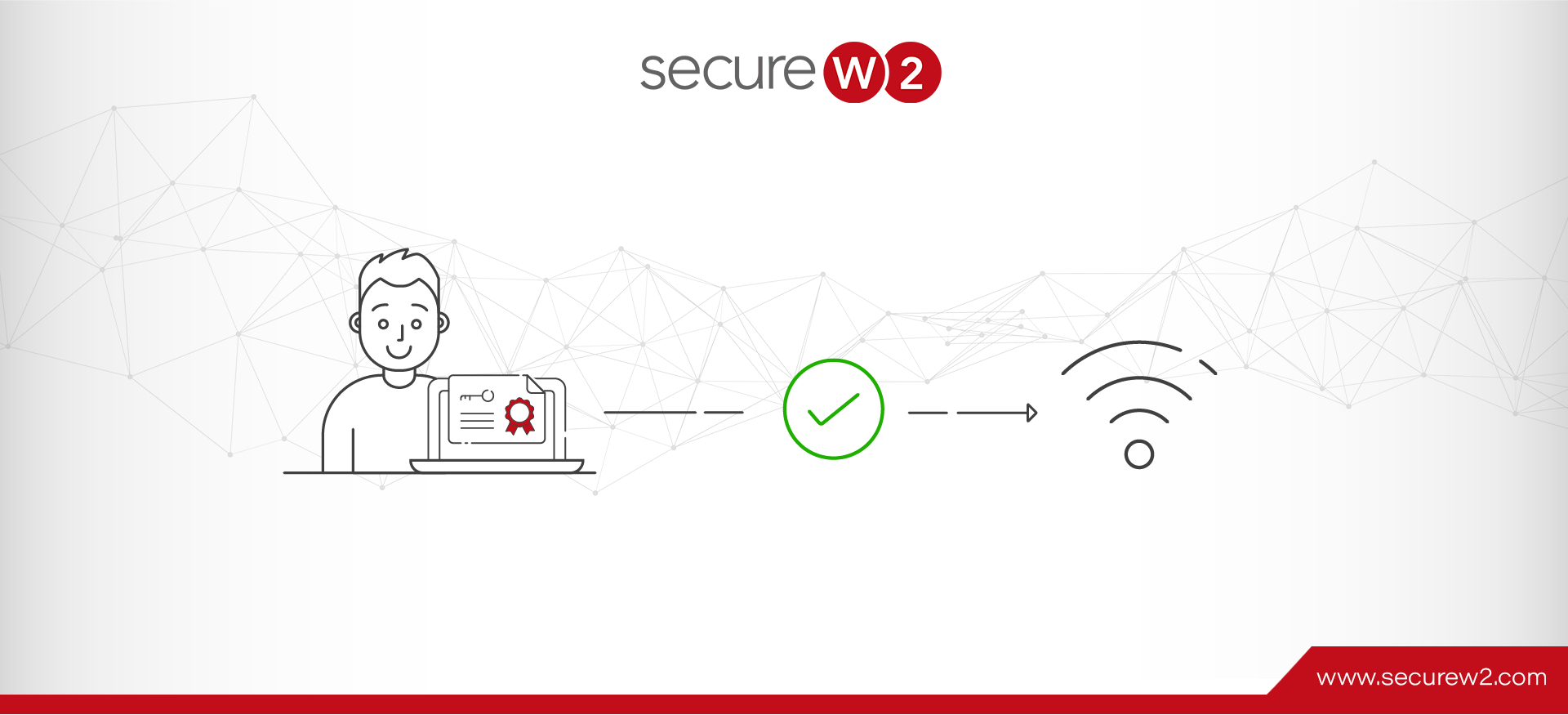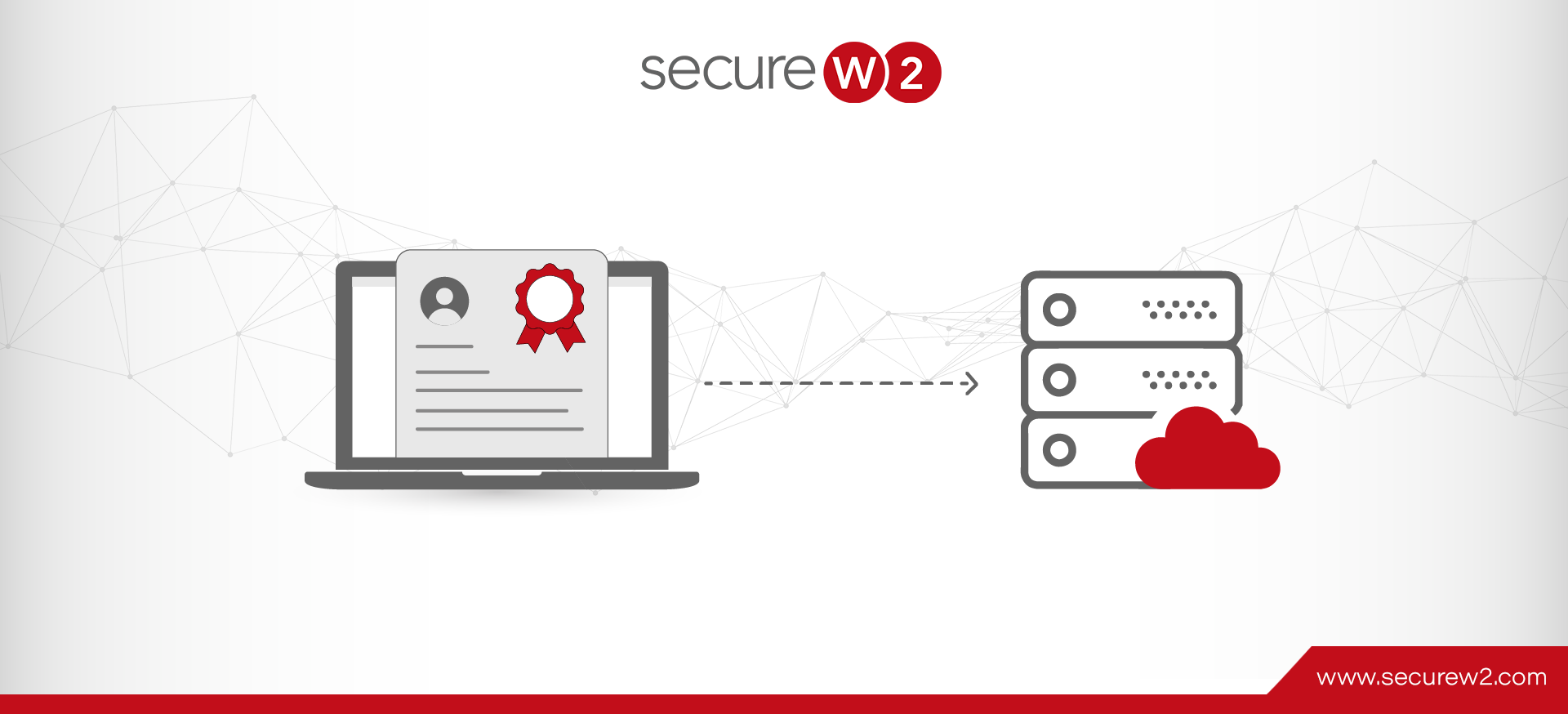
What Is RADIUS Certificate-Based Authentication?
As cyber security risks increase and secure access to network resources is required, organizations are adopting different authentication methods. RADIUS certificate-based authentication is one of those methods that increase the security level of the RADIUS protocol. 80% of breaches in ... Read More