Key Points
- Eduroam is more secure with EAP-TLS certificates, replacing passwords and reducing risks like credential theft and evil twin attacks.
- Certificates simplify connectivity, enable seamless cross-campus roaming, and reduce IT maintenance compared to PEAP.
- Deploy EAP-TLS with automated certificate onboarding via SecureW2 to ensure scalable, secure, and fast Wi-Fi authentication.
Eduroam has become crucial for colleges worldwide, providing students and staff with seamless, cross-campus Wi-Fi connectivity. However, as more institutions use Eduroam as their principal Wi-Fi network, security and accessibility problems emerge, particularly for networks that use the Protected Extensible Authentication Protocol (PEAP) for authentication. Using PEAP credentials can expose users to various risks, including credential theft and “evil twin” attacks, in which hackers build false networks to intercept login information. This vulnerability demonstrates the need for a more secure strategy.
Switching to EAP-TLS, which uses digital certificates instead of passwords, provides a more secure alternative. Unlike PEAP, system certificates eliminate the need for human credential input, reduce disconnection concerns, and enhance the user experience by assuring automated re-authentication. For universities looking to protect user data while simplifying connectivity, certificate-based authentication is the clear choice for a secure and efficient Eduroam network.
Read this case study to see how a leading research institution used SecureW2’s certificate-based authentication to boost Wi-Fi security and connection.
What is Eduroam?
Eduroam (Education Roaming) is a global Wi-Fi network service specially designed for the educational and research communities. It enables students, faculty, and staff from participating institutions to connect to Wi-Fi on campuses worldwide securely. Eduroam is powered by a federated authentication system dependent on the credentials of the user’s primary institution. Users can access Wi-Fi at a participating institution by logging in with their registration information from their home institution without additional accounts or credentials.
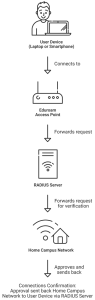
The following is a detailed description of the Eduroam authentication procedure, as depicted in the diagram:
Here’s a breakdown of how it works:
- When a user (e.g., “JP”) from Institution A visits Institution B, they select the Eduroam SSID on their device.
- The Eduroam network infrastructure transmits the user credentials to their home institution’s RADIUS server for verification.
- Institution A confirms that JP is an active member authorized for access, verifies their identity, and receives the credentials.
- Institution A subsequently sends a confirmation back to Institution B through Eduroam, indicating that JP has been verified.
- Institution B grants JP access to the network through this verification, ensuring secure and seamless connectivity.
This process simplifies the secure connection between campuses, thereby reducing the need for insecure public networks and improving data security through 802.1X authentication, which enables encrypted communication.
What is PEAP, and How Does it Work with Eduroam?
One popular authentication technique for safe Wi-Fi connection is PEAP (Protected Extensible Authentication Protocol). PEAP encrypts login credentials, usually a password and user name, and transmits them to a RADIUS server via a secure channel for validation.
PEAP offers a layer of protection between the access point and authentication server, but has drawbacks, primarily because it still uses password-based authentication. It’s especially vulnerable if users have to input their credentials repeatedly or if their passwords are old or weak. PEAP is also vulnerable to man-in-the-middle attacks, making it a less secure option for massive, dynamic networks like Eduroam, where many users join from different places.
EAP-TLS and Eduroam
One of Eduroam’s best features is its cross-campus accessibility, which also puts users at risk for security issues. Hackers may easily trick users into joining by creating “evil twin” networks, which imitate Eduroam and steal their PEAP credentials. Sensitive data may be accessed using these credentials after they are hacked.
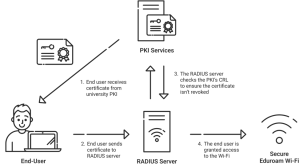
A more secure authentication technique is required because PEAP does not have strong defenses against such attacks. By doing away with the need for passwords, certificate-based authentication—such as EAP-TLS—reduces these risks. They rely on valid certificates, such as client certificates, to considerably limit the risk of credential theft and provide Eduroam users with a secure connection.
PEAP Authentication Vulnerabilities
Typical PEAP Authentication Issues
PEAP has limitations when used with Eduroam, notably in terms of user disconnects and authentication problems. For authentication, PEAP requires user credentials, which include a username and password. Users risk losing access to Eduroam until they upgrade their devices since these credentials change or expire regularly. Additionally, users frequently encounter disconnections and annoying reconfiguration stages if a client device is misconfigured, such as when credentials are entered in the incorrect format. These problems overwhelm IT support for large organizations with many Eduroam users, as users find it challenging to keep a steady connection.
PEAP and Vulnerability to Evil Twin Attacks
The vulnerability of PEAP-based Eduroam authentication to “evil twin” attacks poses a severe security issue. In these attacks, hackers fabricate a phony network with the same SSID, fooling victims into connecting and unintentionally disclosing their login information. Attackers can readily get this information and exploit it to access secure resources on the institution’s network because PEAP depends on passwords for verification. PEAP is a troubling option for sensitive settings like colleges because of Eduroam’s large user base and numerous access points, which raise the possibility of evil twin attacks.
PEAP’s Technical Limitations and Drawbacks
PEAP’s dependency on credentials creates technical issues for Eduroam network administrators. If RADIUS servers are not set up correctly to support the particular credential format Eduroam needs, such as the User Principal Name (UPN) instead of the sAMAccountName, frequent disconnections may happen. Users who regularly switch between networks may experience delays and frustration due to these incompatibilities, which may affect roaming capabilities and result in authentication issues. Additionally, frequent re-authentication is necessary for credential-based systems like PEAP, which can impede network performance and cause congestion in busy places like campuses. This emphasizes the necessity of a more effective and safe authentication technique that eliminates these problems, such as EAP-TLS.
Benefits of Using EAP-TLS with Eduroam
The Security Advantages of Certificates
Strong security measures offered by certificate-based EAP-TLS significantly improve Eduroam’s security. Since EAP-TLS uses digital certificates instead of passwords, it is far more secure against impersonation and “evil twin” attacks than PEAP. Only devices that have been authenticated can access the network since each certificate is exclusive to a user’s device. Additionally, because X.509 certificates eliminate the requirement for password-based validation, they provide a secure, encrypted connection that keeps hackers from intercepting credentials over the air. By doing this, the possibility of stolen credentials is eliminated, and the chance of unwanted access is substantially reduced.
How Certificates Make the User Experience Better
Comparing system certificates to PEAP, end users find the former much easier and more seamless. Password expiration interruptions are eliminated with EAP-TLS as it removes the need for frequent password resets. Without any additional steps, a user’s device with a certificate will automatically connect to Eduroam anytime it is within range. This makes the process more seamless and intuitive by lowering the technical challenges and aggravation frequently connected to manual reconfiguration. Certificates enable connectivity almost instantaneous for employees and students who travel between Eduroam networks or campuses, enhancing the network’s general usage.
Technical Efficacy of Certificates Compared to PEAP
Additionally, valid certificates improve the technological efficiency of Eduroam networks. Particularly in high-density settings, EAP-TLS reduces the requirement for the intricate handshakes and re-authentication procedures that PEAP demands. Without requiring numerous back-and-forth verification processes that credential-based systems need, devices may authenticate rapidly when employing certificates. This guarantees quicker, more reliable connections even during periods of high demand by drastically lowering latency. Due to the simplified design of certificate-based authentication, Eduroam can manage more simultaneous connections while still delivering peak performance in busy campus settings. EAP-TLS is a long-term, scalable solution that improves the university’s end-user satisfaction and network security.
| Feature | PEAP | EAP-TLS |
| Authentication Method | Password-based | Certificate-based |
| Security Level | Moderate (vulnerable to impersonation and “evil twin” attacks) | High (strong protection against impersonation and credential theft) |
| Susceptibility to Attacks | Susceptible to credential-based attacks. | Resistant to credential-based attacks due to certificate security. |
| User Experience | Requires frequent password resets and re-authentication. | Seamless, passwordless; requires no regular user input after setup. |
| Roaming Efficiency | Often experiences issues with disconnects due to credential format mismatches. | Smooth and automatic; certificates enable easy cross-campus roaming. |
| Configuration Complexity | Users often need to manually configure credentials. | One-time configuration with onboarding software; less room for user error. |
| Connection Speed | Slower due to frequent challenge-response handshakes. | Faster with minimal re-authentication steps, even in high-density areas. |
| IT Maintenance | High maintenance due to password resets and misconfiguration issues. | Low maintenance; certificates only need re-issuance every few years. |
| Scalability | Challenging in large environments with frequent disconnects. | Highly scalable and stable in large campus networks. |
| Best for | Short-term, smaller deployments with basic security needs. | Long-term, high-security networks with many users and frequent roaming. |
This comparison chart (Eduroam PEAP vs TLS) shows that EAP-TLS is the best option for Eduroam setups where security, usability, and scalability are top objectives, even if PEAP could function well for smaller networks with less stringent security needs.
How do you Transition from PEAP to EAP-TLS?
The transition from PEAP (Protected Extensible Authentication Protocol) to EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) can greatly improve network security and user experience. EAP-TLS, a certificate-based authentication mechanism, substitutes passwords with digital certificates, lowering the risk of attacks such as password theft and eliminating the need for regular password resets.
SecureW2 offers solutions that facilitate this transition, notably its JoinNow onboarding software. JoinNow automates certificate deployment, simplifying the process for end users and reducing the need for human configuration. This program walks users through a brief, guided onboarding process that installs the relevant certificates on their devices, allowing for smooth, password-free network access. This simplified approach enhances user experience and saves IT burdens by lowering the frequency of password-related support inquiries.
Organizations might take a progressive approach to make the transition easier, enabling PEAP and EAP-TLS on the identical SSID. Existing users can continue using PEAP, while new users or selected test groups will utilize EAP-TLS. SecureW2’s JoinNow software also offers a variety of onboarding options, including QR codes, vanity URLs (e.g., “Wifi.domain”), and an SSID devoted entirely to onboarding, making setup easy for users on unmanaged devices. SecureW2’s interaction with Mobile Device Management (MDM) solutions allows for automatic certificate enrollment on controlled devices without requiring user participation.
Using SecureW2’s solutions, organizations may transition smoothly to EAP-TLS, resulting in a more secure, scalable, and user-friendly network authentication experience.
Transforming Eduroam with Secure, Seamless Authentication
The transition from PEAP credentials to certificate-based EAP-TLS authentication is a significant upgrade for Eduroam networks, particularly in university settings where security and seamless connectivity are crucial. Moving away from credential-based vulnerabilities improves both network security and user experience. With certificate-based authentication, Eduroam becomes a more reliable and flexible service, enabling cross-campus connection and decreasing the demand for IT support.
Ready to improve the security of your Eduroam network?
Contact us and learn how we can help your university create a seamless, certificate-based solution for a safer, smarter campus network.