
How Safe Is The EMF Exposure From Wi-fi?
Most people use Wi-Fi, which emits electronic and magnetic fields (EMF). But are the EMFs from Wi-Fi dangerous? The short answer is no, but we'll dig into the question further.
Stay informed with expert insights, best practices, and the latest developments in network security, identity management, and SecureW2 product updates.

Most people use Wi-Fi, which emits electronic and magnetic fields (EMF). But are the EMFs from Wi-Fi dangerous? The short answer is no, but we'll dig into the question further.

Server security is critical in today’s digitally driven environment. The server certificate, a digital document that verifies the identification of a website or server, is fundamental to Internet communication security. Server certificates enable encrypted connections, guaranteeing the confidentiality and integrity ... Read More
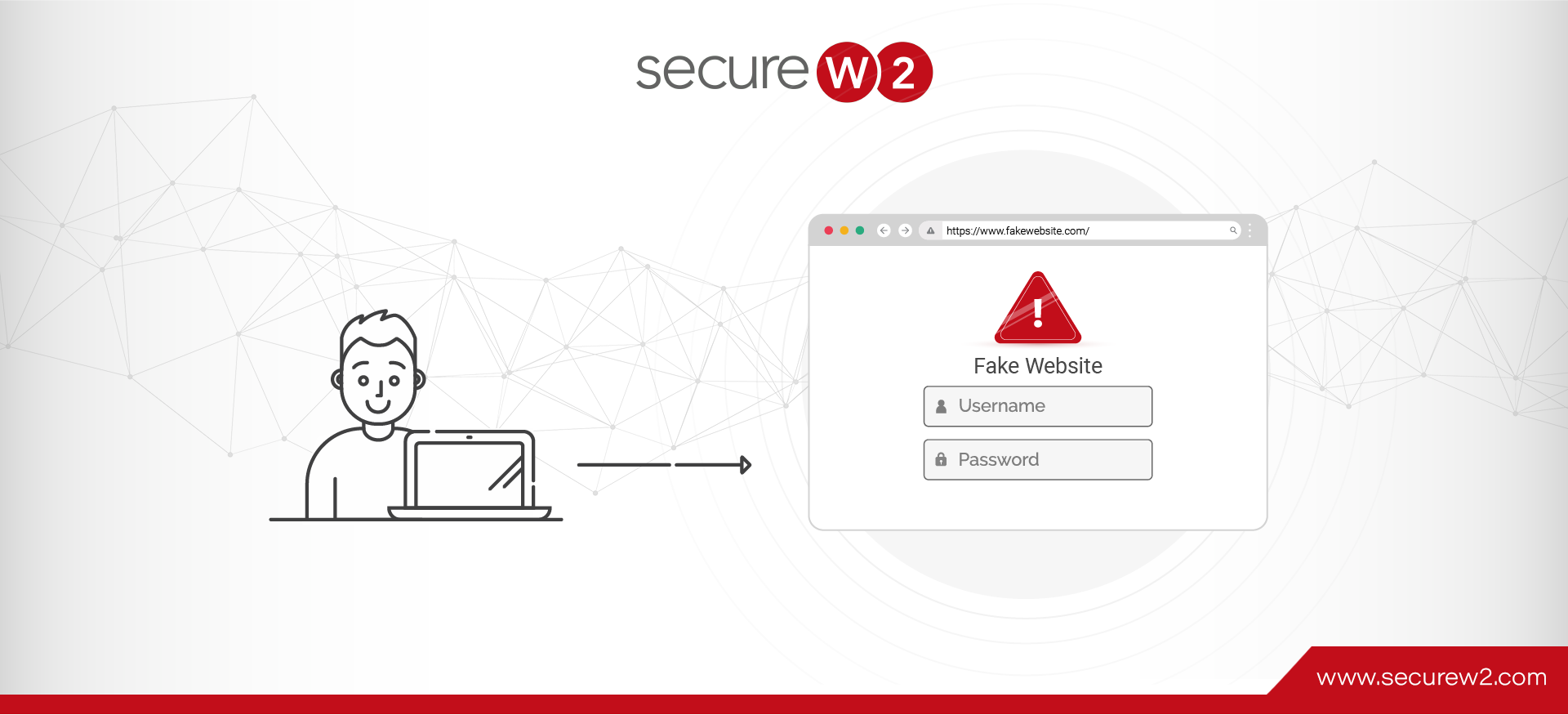
As we increasingly rely on the internet for both personal and professional activities, understanding the potential threats to our online security becomes essential. A prevalent and significant risk is DNS Poisoning, a cyber attack that manipulates and exploits vulnerabilities in ... Read More

Wi-Fi access has evolved from the manual selection of Service Set Identifiers (SSIDs) to the automated, secure connectivity of Passpoint. Initially, users had to browse a list of available SSIDs, select a network, and manually enter credentials—an often cumbersome and ... Read More

We are living in a time where wireless security is imperative because private data and personal information are uploaded online. As the amount of online data increases, so does the monetary cost of cybercrime. Cyber crime is now the most ... Read More
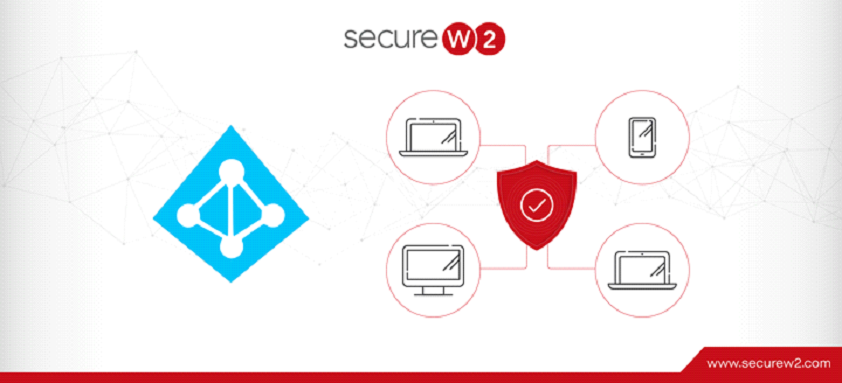
Organizations want different technologies to work well together and integrate smoothly so they can be used more efficiently. The combination of Microsoft Azure and Network Policy Server (NPS) frequently generates interest and confusion simultaneously. While both are effective tools in ... Read More

It’s imperative for organizations to fully switch from SHA-1 to SHA-2. The National Institute of Standards and Technology (NIST) stated SHA-1 should not be trusted, PCI Compliance scanners no longer accept SHA-1 certificates, and Google has deprecated the SHA-1 algorithm. ... Read More
S/MIME stands for “Secure/Multipurpose Internet Mail Extensions”. It’s an IETF standard for public key encryption and creating a digital signature for MIME data. In essence, S/MIME uses a PKI to enroll an email client for certificates (sometimes more than one). ... Read More

Wireless networks are omnipresent. You may have access to many wireless networks, whether in a neighborhood coffee shop, a school, or home. However, it’s hard to tell which ones are secure. Looking closely at Wi Fi security settings can often ... Read More
RadSec is an 802.11x protocol designed to securely transfer information from a RADIUS through TCP (Transmission Control Protocol) and TLS (Transport Layer Security) for protected communications. At a basic level, it protects RADIUS packets sent through public networks. When a ... Read More

Organizations that leverage Microsoft Active Directory (AD) often want to connect their core user identities to their Wi-Fi network. The goal is to enable users to authenticate uniquely to the network in order to increase security. The best practice for ... Read More

What is a Certificate Revocation List? A certificate revocation list, more commonly called a CRL, is exactly what it sounds like: a list of digital certificates that have been revoked. A CRL is an important component of a public key ... Read More