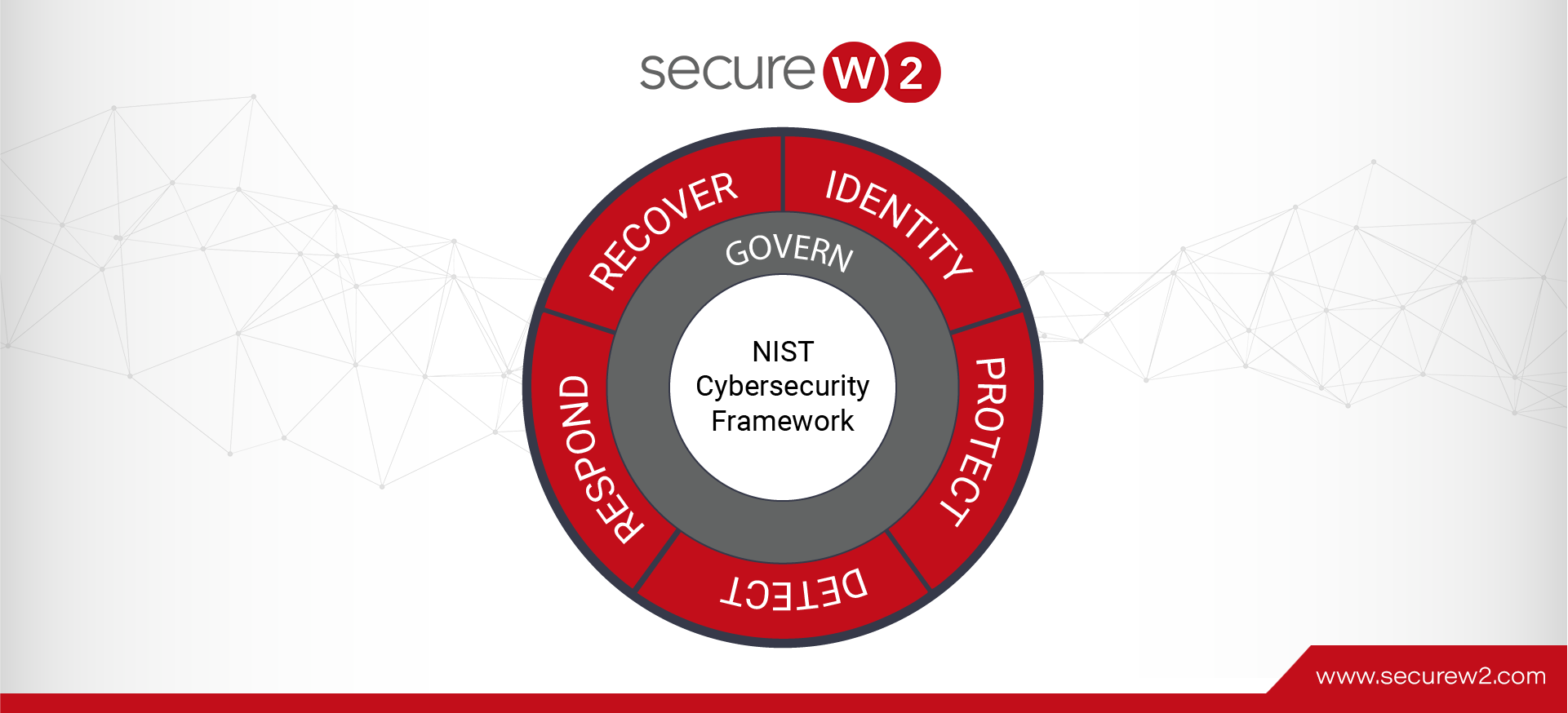
Why Does Certificate Lifecycle Management Automation Need Continuous Authentication?
Enterprises are relying more on automated solutions to manage the lifecycle of digital certificates. Certificate Lifecycle Management (CLM) has evolved from a manual, error-prone process to an automated, API-driven workflow optimized for speed and scalability. However, this shift introduces a ... Read More