Key Points
- Device authentication checks a device's identity, while attestation verifies its trustworthiness. Authentication alone is insufficient.
- Include authentication and attestation in your security plan to protect your systems against unwanted access and untrusted devices.
Device security is more important than ever. Just one compromised device can give attackers access to your whole network.
Because of this, security professionals depend on device attestation and authentication. Although they might sound similar, these two ideas have very different applications. Understanding the differences can help you strengthen your security posture.
What do they mean, how do they operate, and why should you be concerned about them?
What is Device Authentication?
Device authentication means verifying a device’s identity before granting it access to a network, system, or service. It is similar to verifying your identity at an airport security checkpoint — before letting you through to the terminals, you must authenticate your identity.
How Device Authentication Works
Device authentication frequently employs cryptographic methods such as passwords, digital certificates, and key pairs. These methods help verify a device’s identification before accessing a network or system.
Once authenticated, the device is permitted access to the system. This process guarantees that only recognized and authorized devices can connect.
Common Use Cases of Device Authentication
Corporate settings are among the most popular use cases for device authentication. When employees attempt to access corporate systems remotely, the network determines if the device seeking to connect is registered and recognized. Before allowing access to corporate resources, like shared files or email servers, a work laptop would be required to authenticate itself using a digital certificate. This helps prevent unauthorized access from devices, like those with stolen login credentials.
Device authentication can also be used outside workplace settings, like securing cloud services, verifying devices in VPN configurations, and managing access to distant desktops and mobile apps. Although it is a fundamental component of many security systems, it does not assess the device’s security or compromise. This is the role of device attestation.
What is Device Attestation?
Device attestation adds another layer to authentication. Attestation checks if a device is accurate, safe, and untampered with, instead of just verifying identity.
While device authentication could be thought of as a security checkpoint, device attestation would be like a customs officer inspecting your bags for illegal items and verifying your passport.
How Device Attestation Works
Device attestation usually depends on hardware-based security elements, including:
- Trusted Platform Module (TPM)/Secure Enclave – A secure chip that contains cryptographic keys and integrity proofs.
- Hardware Security Modules (HSMs) – specialized hardware used in secure cryptography operations.
- Remote Attestation—A method where a trusted authority, often a server, checks a device’s integrity before granting access.
Device attestation offers excellent confidence that a device has not been compromised by viruses, illegal changes, or counterfeit parts using cryptographic proofs.
A simple example –
To bring this to life, consider how Apple’s Managed Device Attestation (MDA) works in workplace settings:
- A request is issued – An Apple device (such as an iPhone or MacBook) attempts to enter a secure system, such as a business Wi-Fi network or VPN.
- Secure Enclave kicks in – The device’s built-in Secure Enclave (Apple’s TPM counterpart) generates cryptographic verification of its identification.
- Talks to Apple Servers – It securely communicates with Apple’s attestation servers to provide this proof.
- Validation occurs – Apple’s servers validate the request and respond with validated information.
- This is an actual Apple device.
- It has not been tampered with.
- It has a distinct, hardware-bound identity.
- Access decisions are made – Using this information, the enterprise (via its MDM or security system) determines whether to let the device onto the network.
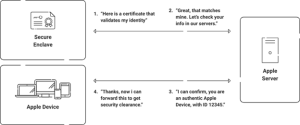
This degree of gadget trust is really strong. Even if a device is cloned or credentials are stolen, the cryptographic evidence associated with the original hardware cannot be faked.Common Use Cases of Device Attestation
Enterprises use device attestation to check endpoint integrity before allowing access to sensitive systems. Attestation may verify that a corporate laptop is running approved software, not jailbroken or rooted, and not infected with malware before an employee connects it to a secure network. Even with correct credentials, the device is denied access if these tests fail.
Organizations employ attestation to secure firmware updates across their hardware. IT departments may check firmware signatures and trustworthiness before updating thousands of devices to prevent malicious software from sneaking in.
Attestation ensures that vital systems employ trusted, untampered hardware in highly regulated domains, including banking, healthcare, and government. This adds security to infrastructure components, including servers, routers, and endpoints, by preventing hardware or OS compromise.
Key Differences Between Device Authentication and Device Attestation
Feature Device Authentication Device Attestation Purpose Verifies a device’s identity Verifies a device’s integrity and trustworthiness Method Uses passwords, certificates, or cryptographic keys Uses cryptographic proofs or hardware-based security Jobs Confirms “who” the device is Confirms whether the device is secure and unaltered Common Use Cases Network access, cloud services, MFA IoT security, firmware validation, and critical infrastructure protection While authentication ensures only recognized devices gain access, attestation adds an extra layer of security by checking whether the device has been compromised.
Why are they both important?
Device authentication and attestation are not competing security practices; they function best together. Here’s why:
- Authentication alone is insufficient – A hacked device with authorized credentials might still constitute a security threat.
- Attestation improves security – It ensures that even if a hacker gets authentication credentials, they cannot gain access through a compromised device.
- Essential for IoT and business security – With billions of linked devices, integrating authentication and attestation protects against unwanted access and device manipulation.
For example, in the corporate environment, device authentication guarantees that only registered devices of employees can connect to internal systems. However, if an attacker accesses a device, attestation can prevent it from accessing essential data by ensuring its integrity.
Conclusion: Putting Authentication and Attestation into Practice
Device authentication and attestation are essential for safeguarding modern corporate environments. While authentication ensures that only allowed devices may access systems, attestation verifies that such devices have not been hacked. When put together, they form an effective defense against today’s increasing cyber threats.
Here’s how to get started:
- Authenticate the device’s identification with a certificate.
- Choose security methods that enable device attestation or integrity checks.
- Deny access to devices that fail security or compliance checks.
- Require attestation support when sourcing IoT devices or hardware.
- Regularly audit your setup to keep ahead of emerging hazards.