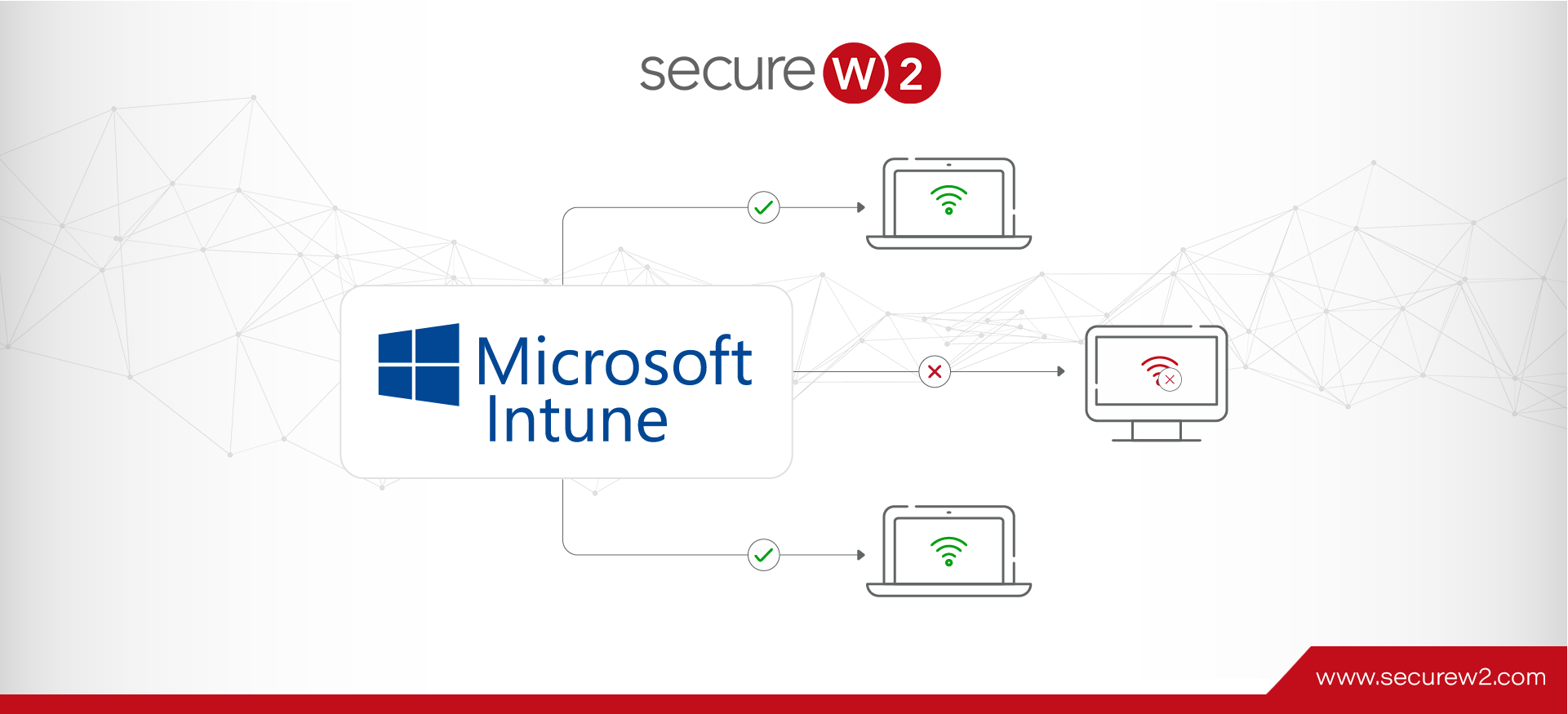
Configure Microsoft GPO with RADIUS Authentication
Integrating Microsoft’s Group Policy Object (GPO) with RADIUS authentication effectively improves network security and access control. GPO enables administrators to apply policy settings for specific user groups, ensuring that individuals only have access to the required resources, preventing unauthorized access, ... Read More