Key Points
- In hybrid work environments, iOS devices must be securely connected to networks utilizing 802.1X authentication with digital x.509 certificates.
- Understanding the role of the RADIUS server and adopting suitable authentication protocols like EAP-TLS helps improve security by reducing credential-based authentication issues.
- Trusted and safe 802.1X authentication requires iOS device root and intermediate Certificate Authorities (CAs) installation and certification.
Securely connecting iOS devices to a network can be a difficult task, especially since the Covid-19 pandemic sped up the inevitable rise of hybrid work environments. Network security must be a top priority and a best practice is configuring IEEE 802.1x authentication, which provides authentication protocols for onboarding clients.
802.1X Authentication: How it Works
802.1X is a network authentication protocol that opens ports for network access when an organization authenticates a user’s identity and authorizes them for access to the network. The user’s identity is determined based on their credentials or certificate, which is confirmed by the RADIUS server. The RADIUS server is able to do this by communicating with the organization’s directory, typically over the LDAP or SAML protocol.
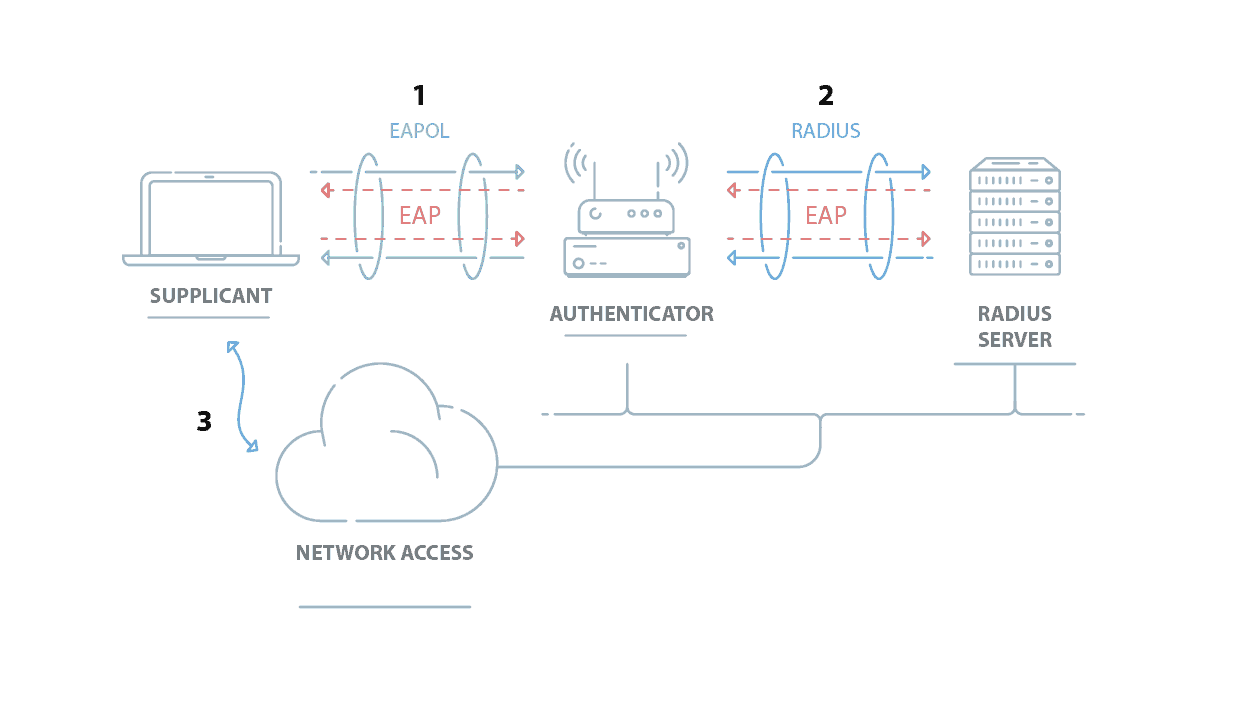
- The supplicant or end-user connects to the authenticator and sends over its credentials or a digital certificate.
- The authenticator sends the identifying information to the RADIUS server, which can check if the supplicant is approved for network use.
- The RADIUS server sends an ‘Access_Accept’ or ‘Access_Denied’ back to the authenticator, which relays it to the supplicant.
- If the supplicant receives an ‘Access_Accept’ message, they are granted network access.
The RADIUS server can authenticate the end-user by verifying their login credentials or checking the user certificate. The RADIUS server is an integral part of the RADIUS protocol, performing both authentication and authentication. It will check the client’s verification in the network and determine what level the client is allowed access based on groups through role-based access control.
How to Configure 802.1X on iOS
Listed below are the 802.1X authentication requirements for 802.1X:
- A wireless access point capable of supporting 802.1X.
- RADIUS Server setup for AAA capabilities
- Devices must have a RADIUS configuration
- Choose EAP Method
- Choose authentication form
- A deep understanding of 802.1X, especially the RADIUS protocol
Which 802.1X Authentication Protocol Should You Use for iOS?
There are different types of authentication protocols and network administrators can pick which one based on how they want to authenticate their users. How can they identify their users in the system and grant them access to the right resources? Some protocols involve a username-password mechanism that the user must enter for access while others rely on a digital certificate.
PEAP-MSCHAPv2
PEAP’s primary vulnerability is its requirement to use credentials to authenticate users. Credentials do not give a clear picture of who is connected to a network because they can be stolen or given to another user.
An ill-intentioned user on the network can operate without being properly identified if they have obtained a valid set of credentials. There are several methods that can be used to obtain credentials. One such way is to use a Man-In-The-Middle attack to intercept credentials while they are being sent for authentication.
This can be frighteningly effective as common passwords, patterns in human behavior, and cooperation among hackers have resulted in sophisticated programs and lists of passwords to attempt when conducting a brute-force attack. What’s worse is that PEAP-MSCHAPv2 has been in use for many years and is revealing vulnerabilities that can be exploited.
EAP-TLS
Certificate Authentication prevents many of the attacks other authentication methods are vulnerable to because it eliminates the need for credentials. Certificates can’t be duplicated, transferred, or stolen off a device, eliminating the risks of many phishing and over-the-air attacks. Credentials can be repurposed and used on any device, but a certificate is explicitly tied to the identity of a particular person and device.
When observing the certificate authentication process, it becomes apparent that the user has minimal involvement. The certificate-equipped device auto-detects the secure network and is automatically authenticated for access. For the entire life of the certificate, the only time the user should have to interact with the certificate is during configuration, which is recommended to supplement with onboarding software that correctly configures every device.
How to Install Certificate Authorities on iOS Devices
In order for the devices to be network trusted in 802.1X, the root and intermediate CAs must be installed. This can be performed by enrolling each iOS device with a certificate.
- Share a link with the trusted certificate to the iOS devices
- Open the link and click ‘Install’ when prompted to download the certificate.
- Input the login credentials.
- Click ‘Done’ when the certificate is installed.
- Follow these directions to Trusted the Root CA
- Settings → General → About → Certificate Trust Settings
- You will find a list of trusted certificates Click enable on the one just installed.
- Settings → General → About → Certificate Trust Settings
Installing certificates onto the device bolsters security measures significantly over credentials. However, the best security practice enables the client to authenticate the RADIUS server with a server certificate.
Enabling Server Certificate Validation on iOS Devices
A major security benefit when using certificate and EAP-TLS for authentication is server certificate validation. It’s an additional security check incorporated into the client-server connection allowing the client to verify the identity of the authenticating RADIUS server.
A certificate must be installed on the RADIUS server so the client can easily verify that it’s the authentication server. The RADIUS server certificate and the client certificate can establish trust if they were signed by the same trusted root CA, which creates a certificate chain of trust.
Unfortunately, it isn’t possible to manually configure server certificate validation for iOS devices because there’s no option to enter server name details. Network administrators will need to download a mobile configuration profile configured to enable it.
SecureW2’s Cloud Connector allows admins to create a configuration file with RADIUS server certificate validation enabled. SecureW2 can integrate with your Jamf MDM or provide a BYOD onboarding service for iOS devices connecting to Windows networks.
Configuring Jamf iOS Devices for 802.1X
To efficiently equip your Jamf iOS devices with certificates, the best option is to utilize a SCEP Gateway. Once a SCEP payload is sent out, devices do not need to be manually configured for certificates; they have enrolled automatically through the SCEP Gateway with no end-user interaction required.
- Configure SCEP Enrollment in SecureW2
- SecureW2 recommends having a new intermediate CA for JoinNow SCEP Gateway integration with Jamf.
- Setup Certificate Enrollment with SCEP on Jamf
- Upload the trusted CA into the Jamf portal and begin the process of enrolling iOS devices with certificates.
- Use PKI Certificate Assistant for Certificate Enrollment
- This process involves uploading the CA signing certificate onto the Jamf portal and establishing the certificate chain of trust.
- Set Up Jamf Configuration Profiles for Jamf iOS devices
- Admins can create a Jamf configuration profile that authenticates the device and enables RADIUS server certificate validation.
- Connect RADIUS with Certificate Payloads
- Set up the certificate payload to validate your RADIUS server. If your RADIUS server certificate also has one or more intermediate CA certificates as part of the certificate chain, you can add those certificates (Root and Intermediate) in this payload.
The JoinNow Cloud Connector offers strong SCEP Gateway APIs, allowing admins to easily enroll every Jamf iOS device. Admins can use JoinNow Cloud Connector to create a mobile configuration file that enables server certificate validation and ensures your iOS devices will always connect to the right RADIUS server.
Addressing iOS 14 Mac Address Randomization Issue
MAC address randomization is when your device’s operating system creates a random MAC address and uses it instead of the original one when connecting to a network. The point of MAC address randomization is to protect devices from being tracked by network providers.
Hotspot 2.0, or Passpoint, is one potential solution to the MAC randomization issue. The purpose is to allow users to roam between different Wi-Fi networks when traveling and transition from network to network without interruptions or switching to cellular data.
By installing a Passpoint User Profile onto a device, you can now tie user information (email address, job title) with a network connection. This eliminates the reliance on the MAC Address being the sole source of identifiable information, as every network connection will have an email address associated with it.
How to find the Wi-Fi Certificate on iOS Devices
The Wi-fi Certificate can be found in your device settings. Finding it is relatively easy, just follow this quick guide:
Settings → General → About → Certificate Trust Settings
This is also where you can interchange root certificates downloaded onto your device.
Best Practices for Securely Onboarding iOS Devices
Configuring WPA2-Enterprise Wi-Fi on your Network
The importance of wireless security cannot be understated as the threat of data theft continues to rise. WPA2-Enterprise networks are the first line of defense – they’ve been proven time and again to keep networks secure by protecting against over-the-air attacks and preventing credential theft.
Onboarding BYOD Devices with Certificate Enrollment
Windows networks are notorious for making it difficult to onboard non-Windows devices and iOS doesn’t have the option to enable server certificate validation. The best solution is onboarding software that automatically configures iOS devices for network access. SecureW2’s Cloud Connector allows admins to distribute a mobile configuration. Additionally, our JoinNow MultiOS is vendor-neutral and allows users on any operating system to self-configure their own devices in a matter of minutes.
Cloud RADIUS Authentication
Thousands of customers are moving away from implementing and managing their own RADIUS server for a cloud-based option. Cloud-based RADIUS solutions succeed where their on-prem and FreeRADIUS counterparts fail by offering easy implementation, cost-effectiveness, and strong security measures.
Securing iOS Devices with 802.1X Authentication
Manually configuring iOS devices creates too much risk in the device onboarding process, both for the organization and the end-user. Most end users are not properly trained to do manual configuration, so it saves time, money, and significant risk to automate the configuration and authentication process. SecurrW2’s software allows admins to use the 802.1X protocol with certificate authentication. Check out our low-cost solutions and add certificate authentication to your network.