Key Points
- Wi-Fi encryption has evolved from WEP to WPA3, with WPA3 offering stronger protections like individualized encryption, resistance to offline attacks, and support for modern security standards
- EAP-TLS with certificates provides superior authentication compared to passwords by ensuring mutual verification, dynamic encryption, and eliminating credential theft risks.
- SecureW2’s Managed PKI and Cloud RADIUS simplify certificate deployment and enable passwordless, policy-driven authentication across enterprise networks.
One key component of wireless security is encryption, which is the process of encoding data before it is transmitted over the air. Only authorized parties with the correct decryption key can read the data, preventing unauthorized access. Common encryption standards for wireless networks include WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), and WPA2, with WPA3 being the latest and most secure standard.
You’ve likely seen these terms if you’ve ever looked at the settings in your router or access point. In this guide, we’ll explain what all those terms mean, compare their security strengths, and explain how you can make your wireless networks even more secure.
What is Wireless Security?
Wireless security refers to the protection of wireless networks and the devices that connect to them from unauthorized access, misuse, or theft. As wireless networks transmit data over the air using radio waves, they are inherently more vulnerable to security threats than wired networks. Without proper security measures, sensitive information transmitted over a wireless network can be intercepted, modified, or blocked by unauthorized parties. Wireless security encompasses a set of technologies, protocols, and practices designed to protect the network and its users from such threats.
Why is Securing Wireless Networks Important?
The ubiquity of wireless networks has made them a prime target for cybercriminals. As these networks transmit sensitive information such as personal details, financial data, and corporate secrets through wireless networks, they are inherently vulnerable to eavesdropping and interception. Without robust security measures, this information can fall into the wrong hands, leading to identity theft, financial fraud, and breaches of privacy.
Wireless security is crucial for maintaining the integrity and availability of network resources. Attacks such as Denial of Service (DoS) can render a network inoperative, disrupting personal communication, business operations, and even critical infrastructure. Implementing strong wireless security protocols helps to prevent such attacks, ensuring that networks are reliable and available when users need them.
Regulatory compliance mandates that businesses and organizations protect sensitive data. Industries such as healthcare, finance, and government have strict guidelines for securing electronic information. Failure to implement adequate wireless security measures can result in legal penalties, fines, and loss of reputation.
The Role of WPA EAP in Wi-Fi Security
The Role of Wi-Fi Protected Access (WPA) EAP in Wi-Fi Security is pivotal in enhancing the authentication process within wireless networks, particularly in environments requiring robust security measures like corporate and public networks. WPA employs EAP, a wireless security protocol, to provide a flexible framework for strong authentication of users and devices. Key aspects include:
- Flexibility: EAP supports multiple authentication methods, including passwords, digital certificates, and smart cards. This flexibility allows organizations to choose the most appropriate authentication method for their security requirements.
- Enhanced Security: By using EAP, WPA can authenticate network users more securely compared to traditional, less secure methods. EAP provides a mechanism for two-factor authentication, significantly reducing the risk of unauthorized network access.
- Dynamic Key Generation: EAP contributes to the dynamic generation of encryption keys, which are unique for each session. This ensures that even if one session key is compromised, other sessions remain secure.
Wi-Fi Encryption Types: WEP, WPA, and WPA2
Wi-Fi encryption types such as WEP, WPA, and WPA2 play a crucial role in protecting data on wireless networks. Initially, WEP was introduced to provide a basic level of Wi-Fi security. However, its vulnerabilities soon became apparent, leading to the development of WPA.
WPA offered improved security features, including Temporal Key Integrity Protocol (TKIP) for better encryption of data. Despite these enhancements, as threats evolved, the need for even stronger security measures led to the creation of WPA2, which includes Advanced Encryption Standard (AES) support, providing stronger data protection.
WPA2 has been the standard for secure Wi-Fi networks, offering significant improvements over its predecessors. Each successive encryption standard was developed to address the weaknesses of the former, ensuring that networks remain safeguarded against unauthorized access and data breaches. The evolution from WEP to WPA3 reflects the ongoing efforts to enhance wireless security in response to emerging threats.
What is WEP Encryption?
Introduced in 1997, WEP (Wired Equivalent Privacy) was the first attempt at securing Wi-Fi networks. Its goal was admirable: to provide wireless networks with a level of security comparable to that of wired networks.
While groundbreaking at the time, WEP’s fixed key approach made it susceptible to various attacks. WEP encryption utilizes a combination of user-supplied keys and system-generated values to encrypt data packets before they’re transmitted over the air. However, its reliance on a static encryption key, which doesn’t change, made it vulnerable to decryption by persistent hackers. Due to its flaws, including the ability for hackers to intercept and crack WEP keys in minutes, WEP encryption has become largely obsolete. Its vulnerabilities highlighted the need for a more secure protocol, leading to the development of WPA.
What is WPA Encryption?
Wi-Fi Protected Access (WPA) was introduced as a temporary solution to address WEP’s shortcomings. It offered enhanced security features, such as TKIP (Temporal Key Integrity Protocol), which dynamically changed keys to prevent the types of attacks that plagued WEP. WPA acted as a crucial stepping stone, bridging the gap between WEP and the more secure WPA2. It demonstrated the Wi-Fi Alliance’s commitment to evolving Wi-Fi security and set the groundwork for the stronger protections offered by WPA2.
The Enhancements of WPA: TKIP and Improved Security
TKIP was a significant advancement, providing a new encryption key for each data packet. This, combined with a message integrity check, greatly improved Wi-Fi security. However, like any technology, attackers eventually found vulnerabilities within WPA, pushing the Wi-Fi Alliance to develop an even more secure standard: WPA2.
What is the WPA2 Standard?
With its introduction in 2004, WPA2 became the gold standard for Wi-Fi security, incorporating the Advanced Encryption Standard (AES) and Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) for encryption. Its robust framework was designed to rectify the vulnerabilities present in its predecessors, offering a far more secure wireless network environment.
WPA2’s use of AES, a sophisticated encryption algorithm, and CCMP, a protocol that enhances data confidentiality, integrity, and authenticity, marked a significant leap in wireless security. This combination ensures that each piece of data is individually encrypted and authenticated, providing a stronghold against potential attacks. WPA2’s reliability, backed by its widespread acceptance and implementation across devices and wireless routers, makes it the preferred choice for securing wireless communications.
What about WPA3?
WPA3 (Wi-Fi Protected Access 3) represents the latest advancement in Wi-Fi encryption and security protocols, succeeding WPA2. Introduced to address the vulnerabilities and limitations of WPA2, WPA3 provides several enhancements that significantly improve the security of wireless networks. One of the critical features of WPA3 is the use of Simultaneous Authentication of Equals (SAE), a robust initial key exchange protocol that replaces the Pre-Shared Key (PSK) exchange mechanism. This change enhances protection against offline dictionary attacks, where attackers attempt to guess the network password by trying various combinations outside of the network environment.
WPA3 improves the security of devices connected to public networks through individualized data encryption. This means that the data transmitted by each device on a public Wi-Fi network is individually encrypted, providing protection against eavesdropping even on open networks without strong passwords. WPA3 also includes measures to simplify the process of connecting devices without displays to a Wi-Fi network securely and introduces a 192-bit security suite aligned with the Commercial National Security Algorithm (CNSA) guidelines for higher security demands.
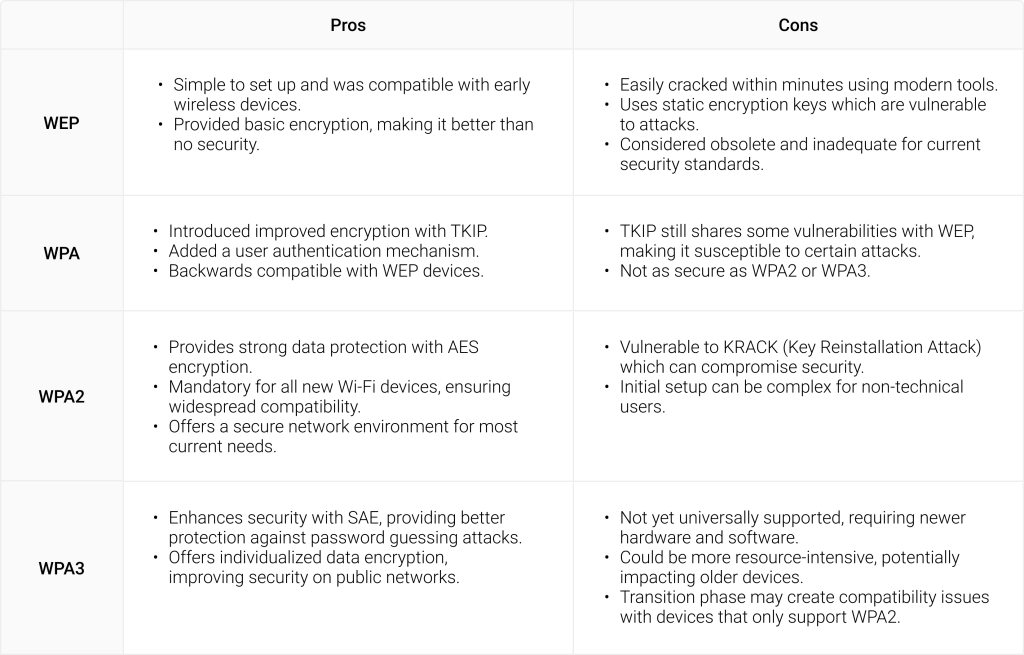
Pros and Cons: WEP, WPA, and WPA2
Here is a summary of the pros and cons for WEP, WPA, and WPA2:
Wi-Fi Encryption Tools
Wi-Fi encryption tools play a vital role in securing wireless networks by encoding data transmitted between devices and access points. Beyond the built-in encryption standards such as WEP, WPA, WPA2, and WPA3, there are additional tools and software that enhance Wi-Fi security. These include:
VPN Services
Virtual Private Networks encrypt all internet traffic from a device, offering an extra layer of security, especially on public Wi-Fi networks. VPNs are crucial for remote workers and those frequently using unsecured networks.
Wireless Intrusion Prevention Systems (WIPS)
These systems monitor a wireless network for malicious activities or policy violations, automatically taking action to prevent or mitigate security threats. WIPS are essential for detecting unauthorized access points or rogue devices.
Wi-Fi Security Scanners
Tools like Aircrack-ng and Wireshark analyze Wi-Fi networks for vulnerabilities, such as weak encryption methods or poorly configured networks. These scanners can help administrators identify and rectify security flaws.
Network Encryption Software
Beyond standard Wi-Fi encryption, additional software solutions provide end-to-end encryption for data sent over the network, ensuring that even if traffic is intercepted, it cannot be easily deciphered.
Enhancing Enterprise Wi-Fi Security with EAP-TLS
The evolution from WEP to WPA3 underscores the continuous effort to protect data from unauthorized access and ensure secure network communication. Among the myriad of tools and protocols aimed at strengthening wireless network security, SecureW2 emerges as a sophisticated solution that significantly enhances network protection.
SecureW2’s managed Public Key Infrastructure (PKI) platform plays a pivotal role in transitioning from traditional password-based authentication to a more secure, certificate-based approach. This is particularly relevant in environments that leverage EAP, especially EAP-TLS, which is renowned for its robust security features.
EAP-TLS stands out for its use of mutual authentication, where both the client and the server authenticate each other using certificates. This method is superior to password-based authentication in several ways:
- Eliminates the Risks Associated with Password Theft: By using digital certificates instead of passwords, EAP-TLS removes the most common vector for network breaches – the theft of password credentials.
- Dynamic Encryption: The use of certificates facilitates the dynamic generation of encryption keys, ensuring that each session is securely encrypted with unique keys.
- Enhanced Authentication: EAP-TLS provides a more secure framework for authenticating devices and users, significantly reducing the possibility of unauthorized access.
SecureW2’s Managed PKI: A Certificate-Based Authentication Solution
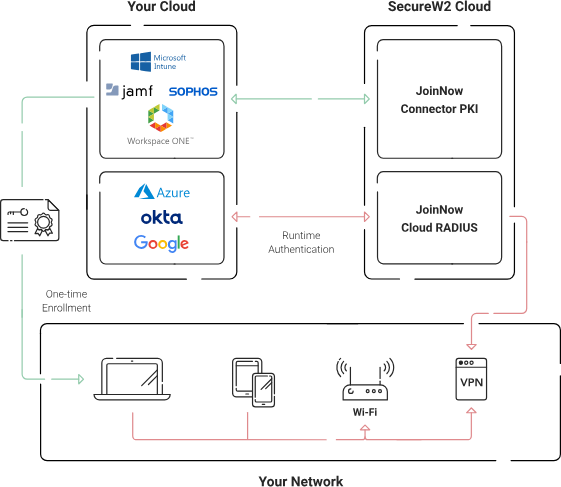
SecureW2’s platform simplifies the deployment and management of these certificates, making it feasible for organizations of any size to implement certificate-based authentication without the complex infrastructure traditionally associated with PKI. Our PKI was also designed with vendor-neutrality in mind, allowing it to integrate with your existing identity and device management infrastructure. We even provide the technology you need to easily distribute certificates to your endpoints, including gateway APIs for managed device certificate enrollment and a dissolvable self-service onboarding application for BYODs.
Additionally, SecureW2 offers a RADIUS server platform designed to facilitate passwordless authentication. This platform not only verifies each network access request but also ensures that the most current network policies are applied by communicating in real-time with cloud identity providers such as Entra ID (Azure AD), Google, Okta, and OneLogin.
Contact us today and see how SecureW2 can fortify your defenses against Wi-Fi vulnerabilities and unauthorized users.
