Key Points
- Microsoft Defender for Cloud Apps provides real-time control over app access and sessions to prevent unauthorized access.
- Conditional Access App Control lets you enforce security policies based on factors like user, device, and location.
- Improve security by integrating certificate-based authentication through SecureW2’s PKI for passwordless application security.
The way we work is radically changing, with globally dispersed teams gaining more popularity. Especially post-pandemic, there has been a significant rise in employees working from home or connecting to the company networks from BYOD machines. This has made the already complex networking ecosystem even more complicated. Monitoring activity after the fact is no longer a viable option. To protect your cloud assets, you need to have better control over your cloud environment in real-time to prevent any data leak or breach, whether intentional or not.
In this article, we will demonstrate how Microsoft Defender for Cloud Apps, when integrated with any identity provider (IdP), can help you gain better control and visibility over your network. Let’s first look at what Microsoft Defender for Cloud is.
What is Microsoft Defender for Cloud Apps?
Microsoft Defender for Cloud Apps portal is a Cloud Access Security Broker (CASB) designed to mitigate the security gaps in a modern network architecture that is a complex ecosystem of managed and unmanaged devices. It helps you get complete visibility and real-time control over your entire network from a centralized location for better protection against cyber threats.
Operating on multiple clouds, when used in conjunction with your IdP, like Azure AD (Microsoft Entra ID) Conditional Access, the CASB platform enables security admins to execute their security tasks in one centralized location. Managing and monitoring security across your Microsoft identities, data, devices, apps, and infrastructure becomes much easier with Microsoft Defender. Along with providing excellent visibility and control over data movement, Microsoft Defender also gives you sophisticated analytics that helps you recognize and manage cyber threats across all your cloud services.
How does Microsoft Defender work?
Microsoft Defender for Conditional Access App Control integrates with your IdP to operate a reverse proxy architecture to enforce access regulations and session controls on your organization’s apps, based on conditions determined by your company’s network policies.
You can quickly achieve this with Conditional Access App Control by defining conditions like:
- Who has access? It can be a user with super access or a group(s) of users with similar roles.
- What Apps do they have access to? An HR employee might have access to cloud apps with payroll information.
- Where do they access from? A particular app may need to be accessible for employees from a specific location, or some apps might only be accessible on specific networks or machines.
Once you have defined the conditions, you can route users to Defender for accessing Cloud Apps for better control over access and sessions. Access and session policies will allow you to safeguard your network through Conditional Access App Control by applying real-time controls on app access and the sessions of each user. You can further refine your filters for access and session policies in the Defender for Cloud Apps portal to define specific actions that include:
- Access Blocking: You can set conditions to block access for specific apps and users to mitigate identified risk factors. For example, as a form of device management, you can block a user when they log in from a BYOD machine.
- Blocking Custom Activities: Some apps carry risks due to the unique scenarios that they have, for example, apps like Slack or Microsoft Teams that allow you to transfer data via messages. You can scan the messages in real-time and block any if it violates company policies.
- Monitoring User Sessions for Compliance: You can monitor the sessions of risky users to review their activities on apps they sign in to. This helps you to both investigate and analyze user behavior and get a better understanding of under what conditions and where to apply session policies in the future.
- Protection on Download: You can provision filters to label and encrypt documents that contain highly sensitive information by integrating with Microsoft Purview Information Protection. This enables you to protect the document by restricting user access in a potentially risky session instead of blocking the download altogether.
- Preventing Data Exfiltration: This will allow you to block access to downloading, printing, copying, and cutting sensitive documents when a user is logged in from an unmanaged device to prevent unauthorized data transfer.
- Asking Authentication Context: Allows you to review Azure AD Conditional Access policies for a user or a machine when a sensitive action occurs in a session. For example, directing a user to complete multi-factor authentication before downloading a highly confidential file.
- Control Uploading of Unlabeled Files: It’s best practice to label sensitive files as per your company policies before they are uploaded and distributed to be used by other users. The filters allow you to block uploads of any file that is not labeled to classify the content as per company policies.
- Scanning to Block Potential Malware: Microsoft Threat Intelligence scans any file before it is uploaded for malware and blocks upload immediately if any potential threats are detected. Blocking the upload of potentially malicious files will help you protect your network from potential threats.
How does Session Control Work?
Session policy, when created with Conditional Access App Control, gives your better control over user sessions by redirecting users through a reverse proxy. This means when a user is connecting to the network, instead of directly taking them to the app, all user requests and responses will now be directed via Defender for Cloud. Redirecting users through proxy doesn’t need additional installation on the device, thus allowing you to monitor or control sessions from unmanaged devices or partner users with much greater ease.
A session protected by proxy will replace all the functional cookies and URLs by Defender for Cloud Apps. For example, if an app gives a user links for domains ending with yourapp.com, the link’s domain will now be suffixed with something like *.mcas.ms. The sample is shown below.
| APP URL | URL when routed through Reverse Proxy |
| yourapp.com | yourapp.com.mcas.ms |
Identification of Managed Devices
With Conditional Access App Control, you can create separate policies for managed and unmanaged devices, thus allowing you to create different access and session policies for different machines. It allows you to identify the type of device by configuring access and session policies that look for
- Devices that are Microsoft Intune Compliant (with Azure AD only)
- Azure AD joined hybrid devices (with Azure AD only)
- Devices authenticated with client-certificates
With Azure AD Conditional Access all your Intune compliant and Hybrid Azure AD Joined devices’ information is transmitted to Defender for Cloud Apps directly. You can easily define an access or a session policy from there.
You can request authentication from relevant devices using client certificates through the device identification mechanism. For managed devices, you can use already deployed client certificates or issue new client certificates. These certificates can be used for context to define access and session policies.
For SSL client certificates (that need to be verified via a trust chain), you can upload an X.509 root or intermediate certificate authority (CA) that contains the public key of the CA. This key will be used to sign the client certificates during each session. Once the certificates are uploaded, access and session policies can be created based on the Valid client certificate and Device tag.
Limitations of Microsoft Defender for Cloud Conditional Access App Control
Microsoft Defender for Cloud Conditional Access App Control has some great features that can help elevate network security. Real-time session control and a centralized platform give you better control over your network, irrespective of the types of devices.
However, the use of passwords for authentication can still leave your network vulnerable. Credential-based authentication is not secure. No matter how robust a platform you use, the use of passwords leaves your network vulnerable to all the popular cyber threats like phishing and man-in-the-middle attacks that password-based authentication carries with it.
Multi-factor authentication (MFA) adds multiple layers of security that can make it difficult for hackers to infiltrate the network and, compared to single-factor authentication, is considered more secure. However, the use of credentials with MFA still carries all the risks of passwords, as was witnessed in the recent Uber MFA attacks.
One of the most significant drawbacks of password authentication is reliance on humans to maintain the standards of safe password policies. The average user is often not well-versed in the best practices of network security and unwilling to self-inflict the inconveniences of correct password management. Users often use easy-to-remember passwords with parts of their names with birth and anniversary dates or the same password for multiple accounts that may be easy to crack for a hacker.
According to a report published by Microsoft, the 802.1x authentication protocol, PEAP-MSCHAPv2 can be exploited by hackers to access the credential information of any machine that has not been configured correctly. One of the biggest vulnerabilities of PEAP-MSCHAPv2 is the encryption method used to transmit packets. When intercepted by an attacker, hackers can decrypt the packets easily. Suppose a machine is not configured correctly to connect to its respective trusted RADIUS server. In that case, hackers can intercept it by imitating to appear like the valid SSID a user is trying to connect, making the machine attempt to auto-authenticate by transmitting encrypted packets containing the user’s login credentials to the spoofed network. This can leave your network vulnerable to attacks.
This is why industry titans like Microsoft have recommended moving away from PEAP-MSCHAPv2 and password-based authentication. Microsoft, on their official site, states, “If you are using Wi-Fi and VPN endpoints that are based on MSCHAPv2, they are subject to …attacks, Microsoft recommends that organizations move to certificate-based authentication… like EAP-TLS.”
Certificates Authentication for Microsoft Defender
The use of certificates to authenticate users when deploying Microsoft Defender can mitigate the risks associated with password authentication. Unlike passwords, certificates cannot be stolen or replicated, nor does it require human interaction at the time of authenticating. Certificates are also provide better context for identity-based access management with Microsoft Defender since certificates positively identify who or which machine is connecting to your network.
Digital certificates do not need to be reset every 90 days like passwords, improving the end-user experience and reducing IT support tickets. The validity of certificates can be set to a specific number of months or years, depending upon your company policy and business requirements. Using certificates to authenticate is also cost-effective as it does away with the issues the IT department usually has to handle, like password reset, password retrieval, or account-locked tickets.
Certificates are protected by public key cryptography, an encryption mechanism that uses two pairs of keys, a public key and a private key. It eliminates issues like eavesdropping, making deciphering messages impossible even if someone manages to listen in to the conversation. This is the core technology of a Public Key Infrastructure (PKI) that manages the public keys that the network uses for public key encryption, identity management, and certificate lifecycle management.
A PKI can be tailored to t fit your company’s needs. Depending on your network security requirements and the vendors you use, SecureW2’s PKI can be customized for Wi-Fi authentication, VPN, email security, or web application authentication, to name a few.
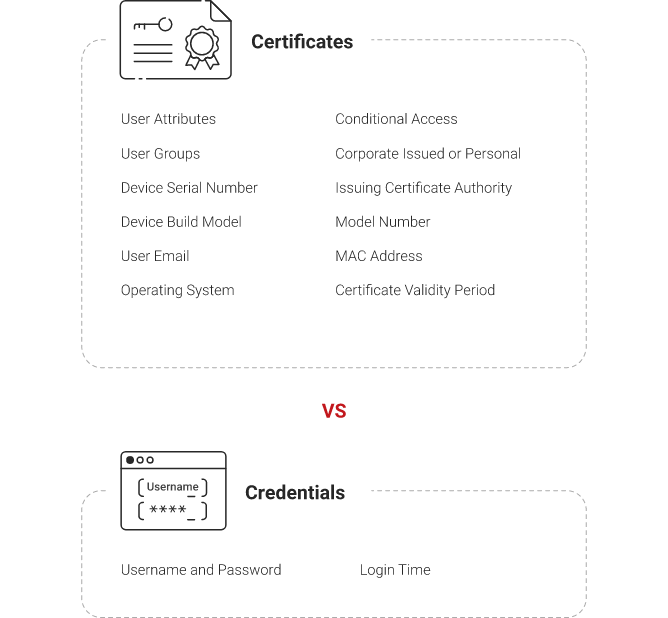
SecureW2 Managed PKI for Microsoft Defender for Cloud Conditional Access App Control
The world is moving to cloud computing, and there is a need for a more comprehensive solution that can help you manage your network security better. Microsoft Defender, when integrated with any IdP, helps you get better, real-time control over your network and all the devices that connect to your network by giving you the flexibility to define conditional access with features like access and session control policies. Configuring certificates to authenticate users will dramatically improve network security, making it nearly impenetrable.
We at SecureW2 can help you integrate Microsoft Defender with our Managed Cloud PKI to issue certificates and manage the certificate lifecycle seamlessly. Our onboarding solutions can help you automate the entire cycle of enrolling and managing certificates for any type of device, BYOD or managed, by installing a user profile on every device. .
Click here to see our pricing and begin implementing passwordless conditional access on your network.