Key Points
- Azure AD lacks built-in support for passwordless, certificate-based authentication, so integrating a managed cloud PKI like SecureW2 enables secure x.509 certificate usage across Wi-Fi, VPN, and web applications.
- SecureW2 automates certificate enrollment via user-friendly onboarding tools (like BYOD JoinNow apps) and gateway APIs, eliminating manual configuration and reducing misconfiguration risks.
- The included Dynamic Cloud RADIUS enhances security by combining certificate authentication with real-time directory checks and policy enforcement, all without needing on-prem infrastructure.
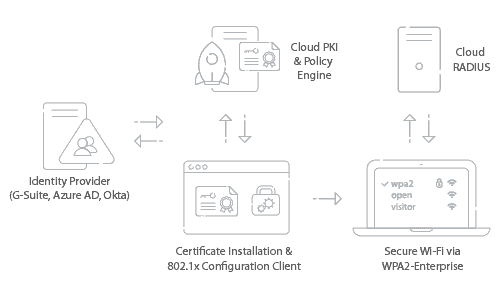
Azure AD (Microsoft Entra ID) customers can ditch password-based authentication and switch to x.509 certificate-based authentication. Digital certificates offer vast improvements to network security, efficiency, and user experience. But in order to deploy certificates, organizations will need to implement a Public Key Infrastructure (PKI).
Improve Azure Security with an Azure PKI
Although they provide a multitude of services, PKIs are most often used with Azure for authenticating users for Wi-Fi, VPN, and web applications. PKIs enable admins to use public-key cryptography, or asymmetric encryption and create a public-private key pair for each user. Public keys are stored in digital certificates for secure exchange, while private keys can be securely stored in the software.
Certificates can contain a bevy of identifying information: MAC Address, email, username, and any other attribute that is contained in your Identity Provider. This gives IT high assurance that the user logging in with the device is who they say they are.
The process of manually enrolling certificates Azure to network devices is complex and mistake-prone, especially if end users are left to complete the configuration. Misconfigured devices are a common vector for cyberattacks, so it’s imperative to correctly configure devices the first time.
Certificates can be easily used for Wi-Fi and VPN authentication. Using certificates for authentication instead of passwords significantly reduces the risk of VPN phishing attacks. With SecureW2’s PKI, you can easily get VPN certificates on to every device on your network with our BYOD Certificate Installation software and our Gateway APIs for managed device certificate auto-enrollment.
Best Practices for 802.1x Authentication with Azure AD (Microsoft Entra ID)
The first 802.1x protocol Microsoft Admins consider deploying is usually PEAP-MSCHAPv2. However, it’s not a great choice since it has well-known vulnerabilities that can be leveraged by attackers to harvest credentials.
PEAP leaves the user vulnerable to Evil Twin and Man-In-The-Middle (MITM) attacks where a malicious user could set up a phony Access Point (AP) that imitates the genuine AP to trick users’ devices into connecting and entering their credentials. This form of attack can be performed using minimum tools, in some cases only a laptop. A user who is unknowingly tricked could accidentally give up their credentials and put the safety of the network at risk.
To defend against over-the-air attacks, a RADIUS server can be configured for server certificate validation. Server cert validation configures the device to validate the identity of the RADIUS and confirm that it is the correct network, but often networks are not configured for server certificate validation due to lack of information and difficulty configuring it without a configuration guide.
The authentication method that is most highly recommended is the EAP-TLS protocol. This top-notch authentication method authenticates a device’s certificate or credentials in an EAP tunnel, protecting it from over-the-air attacks. When using the EAP-TLS authentication method, server certificate validation is a mandatory layer of added security. Once a user is successfully onboarded to the network, they never have to be concerned about connecting to an illegitimate network.
Dynamic Cloud RADIUS for Azure AD
SecureW2’s PKI also comes with our Dynamic Cloud RADIUS server which is built to support Azure networks. In fact, Cloud RADIUS offers an industry-first passwordless Azure solution by leveraging certificates for network security, while still providing LDAP security features like User Lookup. It’s the only solution that provides admins with all the tools necessary to deploy certificate-based 802.1x authentication.
Dynamic Cloud RADIUS operates in fundamentally the same way as regular RADIUS, but it has one extra step that makes a world of difference – it asks the directory if a user is active or not.
This functionality is similar to the user lookup feature sometimes employed by networks with LDAP-AD infrastructure. It allows the RADIUS server to reference an entity’s directory entry, both to confirm that the entity is authorized for access and to read any other useful information there.
Here are just some of the advantages Dynamic Cloud RADIUS brings:
- Reduces reliance on manual certificate management
- Introduced security redundancies
- Runtime-level policy enforcement
- One RADIUS server for multiple networks
Instead of certificates storing the information necessary for policy enforcement, that data can be stored in the directory. Dynamic RADIUS can then check the directory and make policy decisions regarding user privileges, a method that is more secure and easier to manage.
Configuring an Onboarding Service for Azure AD User Enrollment
Device Onboarding software has become a standard for large organizations in recent years, and it’s easy to understand why. Each new cohort of students brings with them an ever-growing number of internet-connected devices – each of which needs to be configured properly to maintain the integrity of a secure network.
For instance, in higher education, the average university student has 7 internet-connected devices, all of which need to be reconfigured every 60-90 days due to password reset policies. Certificates eliminate this need – and typically only need to be configured once during a device’s lifetime.
Onboarding software like SecureW2’s JoinNow allows end-users to easily configure their own BYOD devices, which reduces the burden on IT support and provides convenience for users. Paired with Wi-Fi certificates, it can vastly improve the user experience by eliminating password-related disconnects.
While Wi-Fi certificates are highly recommended for improving BYOD device onboarding, they can be challenging to configure for regular network users. This is why customers love the pairing of our onboarding software with our PKI services. Our software makes it incredibly easy to replace credentials with certificates, so universities can enjoy all the benefits of certificates without drawbacks.
Cloud PKI Built for Azure AD
If our sales and support engineers have told us anything, it’s that many Azure and Active Directory (AD) admins are having difficulties when attempting to migrate their environments to the cloud. For starters, AD requires an on-prem connection and isn’t designed for cloud computing. AD CS, Microsoft’s solution for a homebrew PKI, is similarly tied to on-prem networks.
With that restriction, many admins have chosen to build their own PKI on-premise. But by doing so, they are signing themselves up for an incredibly laborious project that will cost their organizations hundreds of thousands of dollars. On-premise PKIs require weeks or even months of configuration in order to get up and running. Admins spend countless hours trying to figure out what they need, what they don’t need, how to connect the things they do need, and how to connect that with their AD directory.
With the on-prem option, Azure customers are stuck with legacy servers that aren’t well-equipped to handle modern cyber threats – leaving their systems vulnerable to over-the-air credential theft. Plus, the software world is quickly migrating to the cloud, and networks with legacy environments are left behind.
So how can you deploy a cloud PKI that works with Azure? Read on to find out, or if you’d like more context, here’s everything you need to know about Windows PKI servers.
Integrating Azure with a Cloud PKI Solution
Many admins may fear it too difficult to implement a PKI for their Azure environment, but that’s not the case at all. By integrating Azure with our Managed Cloud PKI, admins can get it up and running in no time and start issuing certificates to all network users.
Below, we’ll cover a quick overview of how to set up Azure and AD with SecureW2’s PKI to deploy WPA2-Enterprise with 802.1x EAP-TLS.
Configure Azure as an IDP in a SAML Application.
Enable users to self-configure their devices for WPA2-Enterprise, equip their device with a certificate for life after integrating Azure SAML with SecureW2.
Add Users to the Azure SAML Application and/or Integrate Active Directory
Once integrated, the network can quickly determine who’s an approved network user during the authentication process.
Configure Attribute Mapping and Policies in the SecureW2 Management Portal
Encode user attributes to certificates to provide Identity Context and easily assign VLANs, which is valuable for user groups and policies.
For a more in-depth guide, check out our article on configuring WPA2-Enterprise with Azure and Azure AD.
Managing PKI Certificates in Azure
Apart from getting a certificate onto every device, managing every certificate seems like a tall order for your typical sysadmin. Not to worry, our PKI solution covers every aspect of certificate lifecycle management, from issuance to expiration.
Certificate Issuance
Azure customers are able to use SecureW2’s PKI to deliver certificates to all network devices. For BYODs, admins can use our onboarding software and for managed devices, they can use Gateway APIs.
Users can download our JoinNow App and, in just a few clicks, configure their devices with 802.1x settings and are enrolled with a certificate. Admins can send out configuration payloads containing 802.1x configuration settings and devices will then automatically request a certificate. Once their credentials are approved, a certificate will be administered to the device and set for life.
CRLs
Our Cloud RADIUS server is able to view all certificates that have been revoked by periodically downloading a Certificate Revocation List (CRL). When authenticating devices, Cloud RADIUS can refer to the CRL to ensure that the user’s certificate has not recently been revoked.
Cloud RADIUS gives Azure admins the ability to adjust download intervals so the CRL can be updated more or less frequently to balance security needs and request resources.
Managed Device Gateways APIs
For Azure customers that also use an MDM, such as Intune, admins are able to build powerful Gateway APIs to easily provision every device with a certificate.
SecureW2 offers industry-first native integration with MS-GPO, giving admins the ability to customize certificates for users based on their network policies and access levels.
Event Logs
The data contained within a RADIUS event log varies depending on the deployment, but there are some common fields that you’re likely to find no matter your RADIUS provider.
- Date
- Time
- Name
- Client Type
- Record Type
- Authentication Type
RADIUS vendors with a robust management and reporting suite, like Cloud RADIUS, have the ability to add and remove data fields from event logs. Custom RADIUS event logs can be particularly useful for compliance audits.
In addition to event logs for authentication and authorization requests, RADIUS servers usually also log other event types like server startups, shutdowns, or interruptions of service. These make up a small fraction of the overall logs but are particularly useful for investigating outages and the like.
Not only can admins easily view RADIUS events, but they can also see device connectivity issues and certificate enrollment status all in one place. Admins don’t need to manually search through logs, everything needed to troubleshoot issues is available in our easy-to-use Cloud Management Portal.
Implement a Secure Cloud-based PKI for Azure
By integrating their environments with SecureW2’s Managed PKI and Cloud RADIUS, Azure admins are able deploy secure certificate-based authentication and leave passwords behind. Our software works natively with Azure and admins can use our onboarding software and powerful gateway APIs to auto-enroll all network devices.
Go passwordless with Azure today! We have affordable options for organizations of all prices, click here to see our prices.