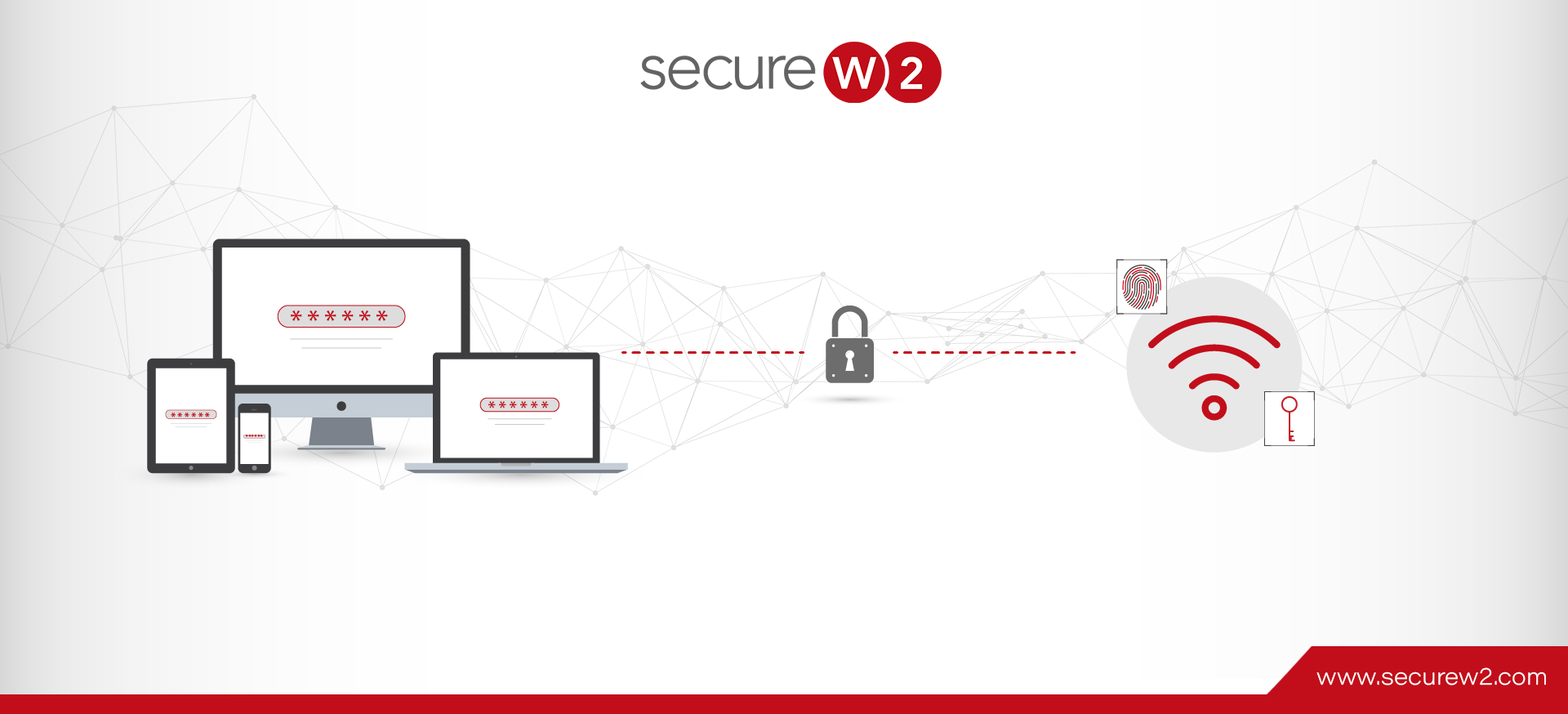
Should WPA2-Enterprise Be Used For My Home Network?
Securing home wireless networks has never been as important. An increase in remote work requires more people to handle sensitive business data at home. On top of this, our lives, in general, are becoming increasingly digital, conducted through services such ... Read More