LDAP (Lightweight Directory Access Protocol) authentication can confirm user identities across a network. It uses a centralized directory system for user authorization and authentication. On the other hand, Microsoft offers a cloud-based identity and access management solution called Azure Active Directory (Azure AD, also known as Entra ID). It provides single sign-on, multi-factor authentication, and user provisioning features.
The relevance of LDAP Authentication with Azure AD arises from its ability to expand its capabilities to legacy applications and systems that use a secure LDAP connection for authentication. This integration improves security, productivity, and the user experience for businesses using hybrid IT infrastructures by facilitating easy access to resources in both conventional on-premises and contemporary cloud settings.
What is LDAP (Lightweight Directory Access Protocol)?
Lightweight Directory Access Protocol (LDAP) is a software protocol that allows an entity to retrieve data stored on a server. The “data” may contain user, device, or organization-specific information kept in directories. Servers communicate with on-premise directories via the LDAP protocol.
To facilitate administrator navigation of their directories, the ability to locate particular data, and user access management, data is organized into a hierarchical structure known as a Directory Information Tree (DIT).
How Does the LDAP Protocol Work?
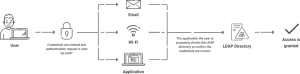
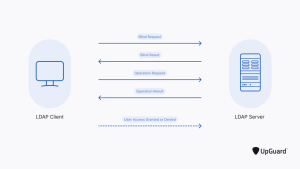
To put it briefly, the LDAP client sends the user credentials that were input into the LDAP server for user authentication. The server determines whether to accept or reject the user’s request to log in once these credentials have been checked against the data in the directory service.
Why is LDAP Important?
Given the rising number of threats to credentials, including more complex attack routes, it is critical to safeguard them in every manner and prevent hackers from accessing critical resources.. LDAP does the following:
- Keeps your passwords safe.
- Confirms the identity of the requester seeking private information.
- Deletes sensitive data when it is no longer needed.
- Stores Important File Backups
Credential storage, or storing usernames and passwords are the primary functions of the LDAP directory. It also provides many other additional services and applications that authenticate users. One example is using LDAP authentication with Docker, Jenkins, and Kubernetes to validate user data. LDAP additionally uses servers and different system administrators to maintain a secure environment within the organization.
The function of the LDAP directory may also be seen in other applications and in the binding of various actions that help LDAP delete distinct entries or search for and compare them with other commands. It also facilitates entry extension, unbinding operations, and entry modification for pre-existing entries.
Risks of the LDAP Authentication Protocol
LDAP poses a cybersecurity concern since it facilitates access to private network resources, and hackers have gradually found ways to exploit weaknesses in LDAP authentication. The most dangerous of these vulnerabilities is LDAP injection. An LDAP injection is a type of cyberattack where malicious code is injected into a web application to get access to confidential data held in LDAP directories. The implanted code uses LDAP metacharacters to change legitimate requests from LDAP clients to achieve malicious objectives. An LDAP injection might result in a data breach, account takeover, or an increase in user privileges. Cyberattackers can easily interact with LDAP and cause LDAP injections when the authentication server fails to confirm the validity of LDAP client queries.
What is Azure Active Directory?
Microsoft Windows Azure AD (Windows Azure AD or Entra ID) is a cloud service that allows administrators to control end-user identities and access rights. Some of its services include identity protection, access control, and a core directory. As its name suggests, Azure AD DS is a Microsoft Azure public cloud computing platform component.
Administrators may decide which data will remain in the cloud and who can access or manage it. They can also decide which services or apps can access it and which end users can access it, thanks to the flexibility offered by the service. Azure AD may assist in enabling single sign-on (SSO), eliminating the need for end users to input passwords to access cloud apps repeatedly.
How Does Azure Active Directory Work?
Azure Active Directory is an identity and access management (IAM) cloud-based solution. It belongs to the identity as a service (IDaaS) category and is a safe online authentication repository for individual and group user accounts. Azure AD controls access to servers and cloud-based apps that leverage contemporary authentication protocols like OpenID Connect, WS-Federation, SAML 2.0, and OAuth 2.0.
Azure AD uses accounts secured by a password and a username to control any access. It is possible to group users into distinct groups, each of which may be given varying access rights for certain apps. To provide users access, identities can also be made for cloud apps, which can come from Microsoft or other software (SaaS) providers.
Azure Active Directory connects users to SaaS apps using single sign-on. As a result, users may utilize the whole set of apps for which they are authorized without constantly logging in. Access tokens generated by Azure AD are saved locally on staff devices and may have expiration dates. Microsoft Azure AD may demand multifactor authentication (MFA) for critical corporate resources.
Azure Active Directory Vs. LDAP: What Are the Differences?
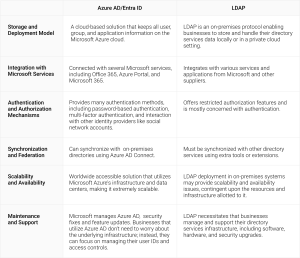
LDAP and Azure Active Directory (Azure AD) are two widely used identity and access management solutions with distinct functions. While LDAP is a protocol used to access and manage directory services data, Azure AD is a cloud-based directory service offered by Microsoft.
Does Azure AD Support LDAP?
Azure AD can only accept LDAP via a connection or sync; it cannot support LDAP directly. According to Microsoft, Azure AD (Entra ID) needs to sync with an LDAP server like Active Directory rather than using LDAP itself. You may use Azure Networking to enable an Active Directory Domain Services (AD DS) instance on your Azure AD tenancy with appropriately configured network security groups to obtain an LDAP connection.
Let’s examine how to use Active Directory Domain Services to link Azure AD to LDAP resources.
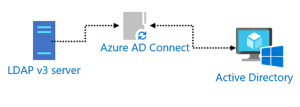
Active Directory Domain Services
Microsoft’s managed domain solution, Active Directory Domain Services (AD DS), may help with LDAP authentication for resources inside the AD domain. AD DS connects the LDAP resource and Azure AD in this scenario. AD Connect and Azure AD offer one-way synchronization from AD, against which the LDAP resource may subsequently authenticate.
This paradigm adds more stages to the authentication process. Therefore, it’s not straightforward to integrate Azure AD with LDAP resources. Every link or stage in an IT process, in general, has the potential to fail, meaning the complexity and risk of this multi-step process is increased. This approach depends more on third parties and can be more unstable and constrictive than a straight LDAP connection.
Challenges of Transitioning LDAP to Cloud Environments
AD is one of the most widely used online directory services because it’s been around for so long, but that may just be its downfall.. To use LDAP for internal applications, organizations must use legacy servers with their Active Directory, meaning they cannot invest in cloud-based software.
It is possible to configure AD connectors, but hosting your directory in the cloud while maintaining duplicate servers on-premise is simply not a long-term solution.
Luckily, many admins were excited to see Azure AD being rolled out to help migrate their AD instances into the cloud and advance network capabilities, but that’s not exactly the case.
Transitioning from LDAP to Certificate-Based Authentication in Azure AD
LDAP is the language AD uses to communicate with other servers and devices. LDAP is able to store data and query it in a way that is easily searchable. With LDAP, servers can easily search for a user in a database, find all the policies attributed to them, and grant them access. LDAP provides network security group levels for WPA2-Enterprise operations. Without LDAP, users will need to be validated for every page or application that they interact with.
Unfortunately, Azure AD doesn’t support LDAP. Azure AD primarily uses the SAML and OAuth protocols to communicate with applications. So, what can you do?
Well, for one, you could leave secure LDAP authentication for more secure certificate-based authentication with EAP-TLS. As the most secure authentication protocol, EAP-TLS uses digital certificates for user authentication, and the connection sessions are encrypted, eliminating the threat of over-the-air credential theft. Credential-based authentication relies on LDAP, but as technology has progressed, the security of credentials is no match for digital certificates. Certificates allow you to use SAML instead of LDAP, making supporting network authentication with Azure easy. So, how can you deploy digital certificates on every single network device?
Supporting Certificate-Based Authentication with Azure AD
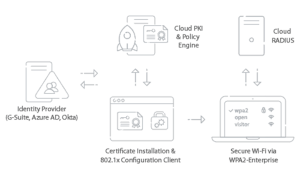
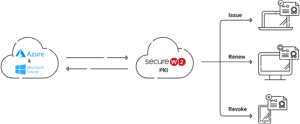
Digital certificates require a Public Key Infrastructure (PKI), but many administrators may fear it is too difficult to implement a PKI. Luckily, that’s not the case because, by integrating Azure AD with our Managed Cloud PKI, admins can get it up and running in no time and start issuing certificates to all network users. We provide gateway APIs for managed devices that automatically issue certificates and a self-service onboarding application for unmanaged devices/BYODs.
Our Cloud PKI is built to authenticate with EAP-TLS for secure Wi-Fi access, the strongest and only certificate-based 802.1x authentication protocol. It’s stronger than any other protocol because EAP-TLS requires both the server and the client to be equipped with certificates, making them both easy to validate. Server Certificate Validation ensures that the client is connecting to the right network server and not a malicious actor impersonating a legitimate server.
For a more in-depth guide, check out our article on configuring WPA2-Enterprise with Azure AD.
Secure User Authentication for Azure AD with SecureW2
Ensuring safe user authentication becomes critical as more and more enterprises rely on Azure Active Directory (Azure AD) for identity and access management. Although many organizations have relied on LDAP for authentication, it’s important to recognize that cybersecurity threats are always changing.
Switching from LDAP to more updated authentication methods, like Azure AD with SecureW2’s Managed Cloud PKI, has several advantages. It resolves the security flaws in legacy LDAP systems and offers enterprises moving from on-premises Active Directory to cloud-based architectures a smooth and safe transition.
Organizations may improve their security posture, reduce the risk of authentication vulnerabilities, and expedite identity and access management procedures by utilizing SecureW2’s Managed Cloud PKI.
Contact us now to see how SecureW2 can help your organization’s identity and access management strategy using Azure AD.