Key Points
- LDAP injection attacks exploit vulnerable applications that fail to properly sanitize user input, allowing attackers to manipulate LDAP queries
- The primary defense for LDAP attacks is to implement rigorous input validation and sanitization at the application layer to prevent malicious characters from ever reaching the LDAP query.
- SecureW2 offers a solution for this transition by providing an all-in-one platform for adopting certificate-based authentication
LDAP also known as Lightweight Directory Access Protocol, is an essential utility in network settings that facilitates getting hold of data about organizations, individuals, and resources. LDAP is commonly used for centralized authentication, providing an efficient method for validating users across different applications and services. Although LDAP is widely used, it is not resistant to flaws. This article will focus on a particular type of vulnerability known as LDAP injection attacks.
The true challenge is in understanding the inherent LDAP injection vulnerabilities. This article aims to explain the complexities of an LDAP injection attack, examining possible repercussions and offering guidance on how to prevent them.
What Is the LDAP Protocol?
Companies use directories to store usernames and passwords, email addresses, printer connections, and other static data. LDAP is an open, vendor-neutral application protocol for obtaining and managing such data. LDAP can also manage authentication, allowing users to sign on once and access several files on the server.
Because LDAP is a protocol, it does not dictate how directory programs operate. Instead, it is a language that lets users rapidly discover the required information.
Because LDAP is vendor-neutral, it may be used with a wide range of directory programs. A directory typically contains data that is:
⦁ Descriptive – An asset is defined by combining many elements, such as its location and name.
⦁ Static – The information seldom changes; when it does, the changes are subtle.
⦁ Valuable – Data kept in the directory is crucial to fundamental business processes and is frequently accessed.
LDAP is sometimes used in conjunction with other systems throughout the workday. Your employees, for example, may use LDAP to connect to printers or validate credentials. These workers may then use Google for email, which does not rely on LDAP.
How Do LDAP Authentication, Authorization, and Access Control Work?
Authentication with LDAP validates a user’s password against a directory or LDAP server such as Active Directory and Open LDAP. Which groups does a user belong to? Only users in the detective group should be able to access the clues application; when someone tries to log in, make sure they are in the correct group before providing access, and so on.
But how can you access sensitive information from all of those records? From a flow standpoint, the process is relatively simple:
⦁ A session starts when a client connects to an LDAP server (DSA, Directory System Agent).
⦁ The client then sends an operation request (typically a search or comparison request) to the server, requesting specific information.
⦁ The server then executes the LDAP query and responds.
⦁ After receiving the response, the client unbinds and analyzes the data.
What Is an LDAP Query?
An LDAP query is a structured request to search, retrieve, or alter data within a directory. Such queries use specified parameters to explore the directory structure, allowing quick data retrieval. While LDAP queries are required for authentication and directory management, they must also be secured to avoid exploitation, as evidenced by threats like LDAP injection attacks.
The LDAP Process
The average employee uses LDAP dozens, if not hundreds, of times daily. That user may need to realize the connection occurred even though the methods to fulfill LDAP queries are advanced and complex.
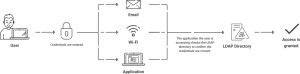
An LDAP query generally includes the following steps:
⦁ Session Connection – The user establishes a connection to the server using an LDAP port.
⦁ Request – The user sends a query to the LDAP server, such as an email lookup.
⦁ Response – The LDAP protocol searches the LDAP directories for information and returns it to the user.
⦁ Completion – The user unplugs from the LDAP port.
The search appears easy, but it requires quite a lot of coding. Developers must establish the search’s size limit, the amount of time the server can spend processing it, the number of variables that may be included in a search, and other factors.
A person moving from company to company may do LDAP searches in each location. However, depending on how the LDAP is set up, the way the searches work and function might vary considerably.
What Is an LDAP Injection Attack?
LDAP injections are a security attack that disrupts some websites’ authentication processes. This attack targets websites that generate an LDAP statement from user data.
For example, an LDAP directory may contain listings of the organization’s users’ various usernames, passwords, and email addresses. An attacker can add malicious code to user input forms, obtain unauthorized access to the directory, and read or modify usernames and passwords if an LDAP directory is utilized for website authentication.
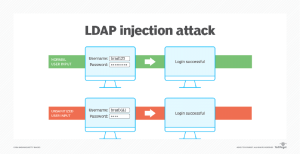
Security experts believe that the significant reason LDAP attacks and similar vulnerabilities occur is that security is frequently inadequate throughout the application development phase. Experts advocate adopting a cleaning procedure to regulate the types and quantity of characters allowed by input boxes and utilizing multifactor authentication for public-facing web apps to secure the integrity of websites that use forms.
How Does an LDAP Injection Work?
LDAP attacks may be carried out by hackers when web-based applications fail to rigorously verify user input, thereby introducing a vulnerability that allows for unauthorized modifications to LDAP statements.
A successful LDAP injection attack occurs when an attacker leverages a security flaw that permits unsanitized input using a local proxy. As a result, they can get access to the LDAP tree and execute unauthorized commands to perform unauthorized searches or change information.
Attackers can manipulate the meaning of a query by using metacharacters such as brackets, asterisks, ampersands, and quotations. If they supply such input, they can update the query unauthorizedly to achieve their purpose. The newly passed parameters can modify the search, addition, and modification functions.
The injection problems with LDAP provide a severe security risk. If adequately implemented, they can give attackers sensitive data such as passwords, roles, permissions, and more. Furthermore, this attack frequently leads to user authentication bypasses, data damage, or denial of service (DoS), destroying the attacking server.
Why Are LDAP Injection Attacks Dangerous?
LDAP injection attacks create a significant risk to system security and integrity, and knowing their possible repercussions is critical for creating effective defense methods. When an attacker successfully conducts LDAP injections, they gain unauthorized access to a system’s directory services. Thanks to this unauthorized access, they can change, analyze, or extract confidential information stored in the directory, such as usernames and passwords, personal data, and access permissions.
An LDAP injection attack has implications that go beyond unauthorized access. Attackers can use these LDAP injection flaws to edit or destroy vital data within the directory, resulting in data corruption and system instability.
Furthermore, because LDAP is frequently used with authentication processes, a successful LDAP attack can compromise the authentication system, allowing attackers to impersonate genuine users or acquire higher rights. This jeopardizes the confidentiality of sensitive data and allows for additional exploitation and unauthorized acts within the plagued system.
An LDAP injection attack can have far-reaching consequences for an organization besides the apparent impact on data security and system operation. Compromised user credentials can be used for more elaborate attacks, such as lateral network movement or the commencement of further phishing operations.
Additionally, the reputational harm caused by successful LDAP injections might erode user and stakeholder trust. As a result, organizations must be aware of the possible consequences of LDAP injection attacks and proactively develop processes to avoid, detect, and mitigate such risks.
How Do You Prevent LDAP Injection Attacks?
LDAP injection attacks can gain unauthorized access to sensitive data, modify LDAP data, or even seize control of an LDAP-enabled system through a simple LDAP query. As a result, it is critical to take precautions to safeguard the system against these threats. Like any injection-based attack, the best way to prevent LDAP injection attacks is to sanitize untrusted input and LDAP queries by using adequate input validation.
Application developers should properly encode and sanitize all information at the application layer. The following practices make this possible:
Input validation (allowlisting)
Allowlisting entails only accepting known good input, such as establishing an anticipated length or numeric range for a particular input field.
Getting rid of all variables
This instructs the computer to disregard metacharacter special functions, such as ampersands, which hackers might exploit to modify LDAP queries. Some querying frameworks, such as LINQtoLDAP, automatically escape while creating malicious queries.
Indexing fields containing sensitive information
This raises the number of LDAP filters an attacker must defeat or alter to access sensitive information.
Analysis tools for static source code
These allow developers to test and debug an LDAP application before it runs.
Sanitization in LDAP Security
In LDAP security, sanitization is a critical process of cleaning and filtering user input to remove potentially hazardous elements. It involves thoroughly validating and purifying input data to verify that it contains no unauthorized or harmful characters that might be used in an LDAP injection attack.
The objective is to build a secure and regulated input environment by deliberately deleting or neutralizing any aspects that attackers might abuse. Sanitization is a preventative strategy to ensure the integrity of user input and avoid exploiting system vulnerabilities.
Dynamic checks
These allow developers to test and troubleshoot applications while running.
Developers can also opt to limit the rights provided to LDAP accounts so that the impact on the broader system is low if they are hacked. Administrators must also correctly establish LDAP servers and user permissions, especially for mobile and online apps.
Alternatives to LDAP
Exploring alternatives to LDAP becomes essential as organizations strive to strengthen their security mechanisms. One productive approach is the implementation of passwordless authentication, specifically by utilizing certificate-based methods. Moving past LDAP and implementing certificate-based authentication can improve security by reducing the dependency on passwords that are frequently vulnerable to phishing or brute force attacks.
Certificates are a more robust and secure authentication because they use cryptographic keys that are more difficult for malicious user to exploit. Organizations can avoid growing security threats and decrease the risks associated with traditional password-based systems by switching to certificate-based authentication. This action complies with contemporary security best practices and adds to a more resilient and future-proof authentication system.
Passwordless Authentication Beyond LDAP
The security landscape is constantly changing, and staying one step ahead of possible threats requires adopting innovative strategies. Passwordless authentication solves the risks associated with traditional password systems and the rising need for powerful, user-friendly security measures.
If your organization is ready to transition to a more secure authentication paradigm, SecureW2 offers solutions for effortlessly adopting certificate-based authentication. Our experience can help you navigate the change and ensure a seamless and efficient deployment.
Moving beyond LDAP and implementing passwordless authentication is a strategic step toward a more robust and sophisticated cybersecurity system. Contact us for more information on how we can assist your organization in making this shift.